Databases and data warehouses store vast amounts of sensitive information, making them prime targets for attackers. One of the most effective strategies to mitigate exposure risks and lock down data is data masking, which enables organizations to protect their data by obfuscating it or replacing it with dummy data, rendering it useless to unauthorized users.
Varonis’ Data Security Platform automatically and dynamically masks data in popular databases and data warehouses, such as Amazon Redshift, Google BigQuery, and Snowflake. This capability helps organizations secure critical structured and semi-structured data and reduce the risk of compromise.
With Varonis’ automated data masking capabilities, organizations can:
- Discover and classify sensitive data in databases and data warehouses at scale
- Identify unmasked sensitive columns
- Create, apply, and manage automated masking policies
In this blog, we’ll explore the importance of data masking and how organizations can use Varonis to automatically and intelligently mask their critical data and enforce least privilege access.
What is dynamic data masking?
Dynamic data masking is a process used to temporarily create a structurally similar but inauthentic version of an organization’s data. This technique helps protect sensitive information, ensure least privilege access, and comply with data regulations while retaining the original data’s properties and usability.
By disguising sensitive information, organizations can reduce the risks of data breaches. This is especially crucial when dealing with highly sensitive and regulated information like PII, PCI, PHI, and other sensitive data categories that are prime targets for hackers and subject to regulations.
Data masking is also crucial when developing and training custom AI models. Proper data masking enforcement prevents the unintentional use of regulated data in AI training, which can violate privacy laws and erode customer trust.
The role of accurate data classification in data masking
Accurate data classification serves as the foundation for effective data masking. Organizations need to know where sensitive data resides to implement comprehensive protection strategies.
Proper classification identifies and prioritizes all sensitive information, such as PHI, PCI, PII, and GDPR data, for masking. By accurately mapping the data landscape at scale, security teams can establish targeted masking policies that protect critical data from breaches and help maintain compliance with stringent regulations.
How Varonis dynamic data masking works
Automatically discover and classify sensitive data.
Varonis automatically scans each database instance down to the individual column and row level. Our Data Security Platform uses a combination of AI-powered and rule-based classification to quickly and accurately identify sensitive data at scale.
By doing so, Varonis provides a complete and detailed view of where sensitive data resides within your environment. Classification results appear in an intuitive tree view, which shows where sensitive data is concentrated across database instances, schemas, tables, and columns.
Automatically discover and classify sensitive data at scale.
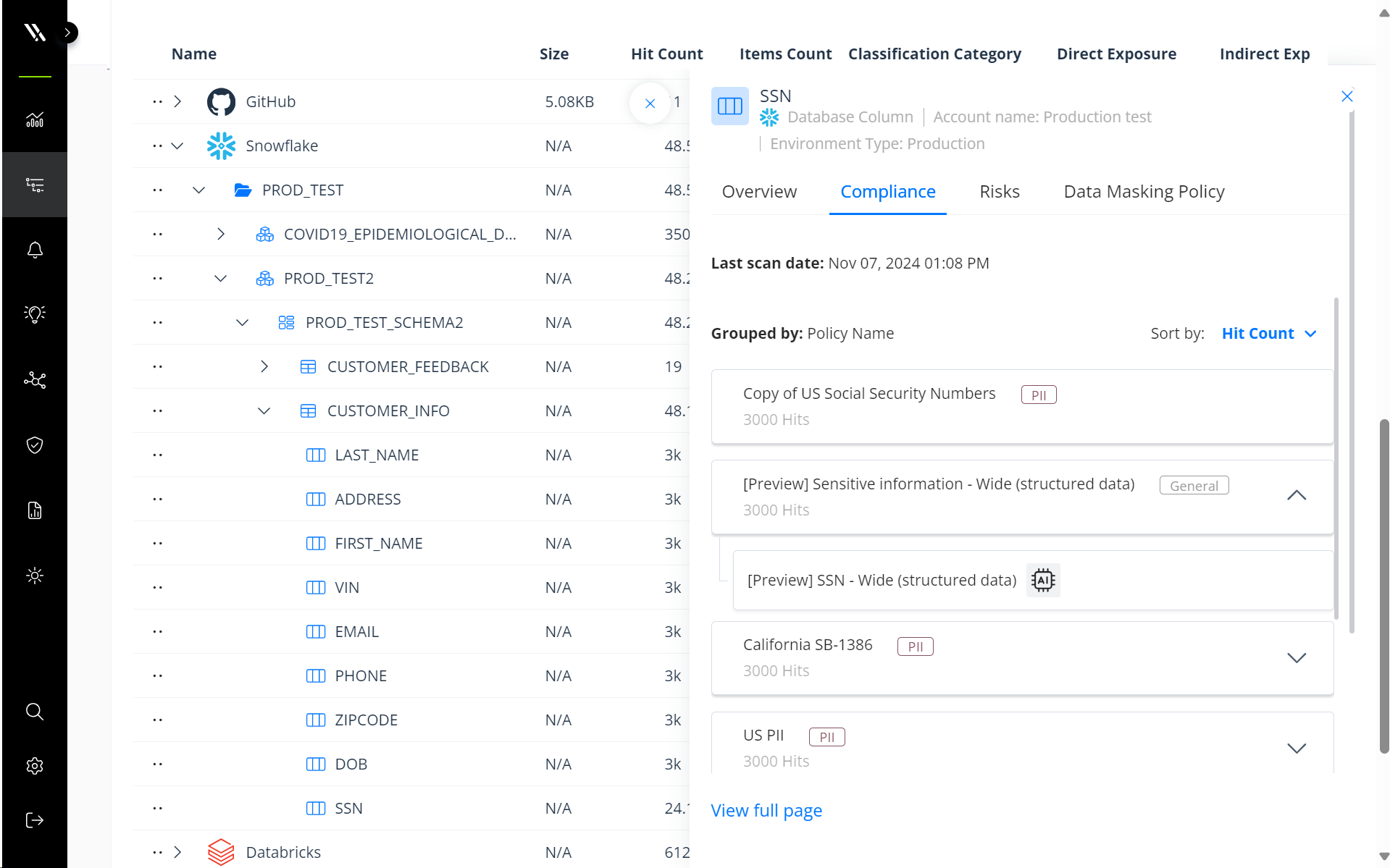
Automatically discover and classify sensitive data at scale.
Identify unmasked sensitive data.
Varonis offers out-of-the-box reports that surface unmasked columns with sensitive data. These reports automatically update as Varonis completes its scans and can be sent to stakeholders regularly for review.
Identify unmasked sensitive columns.
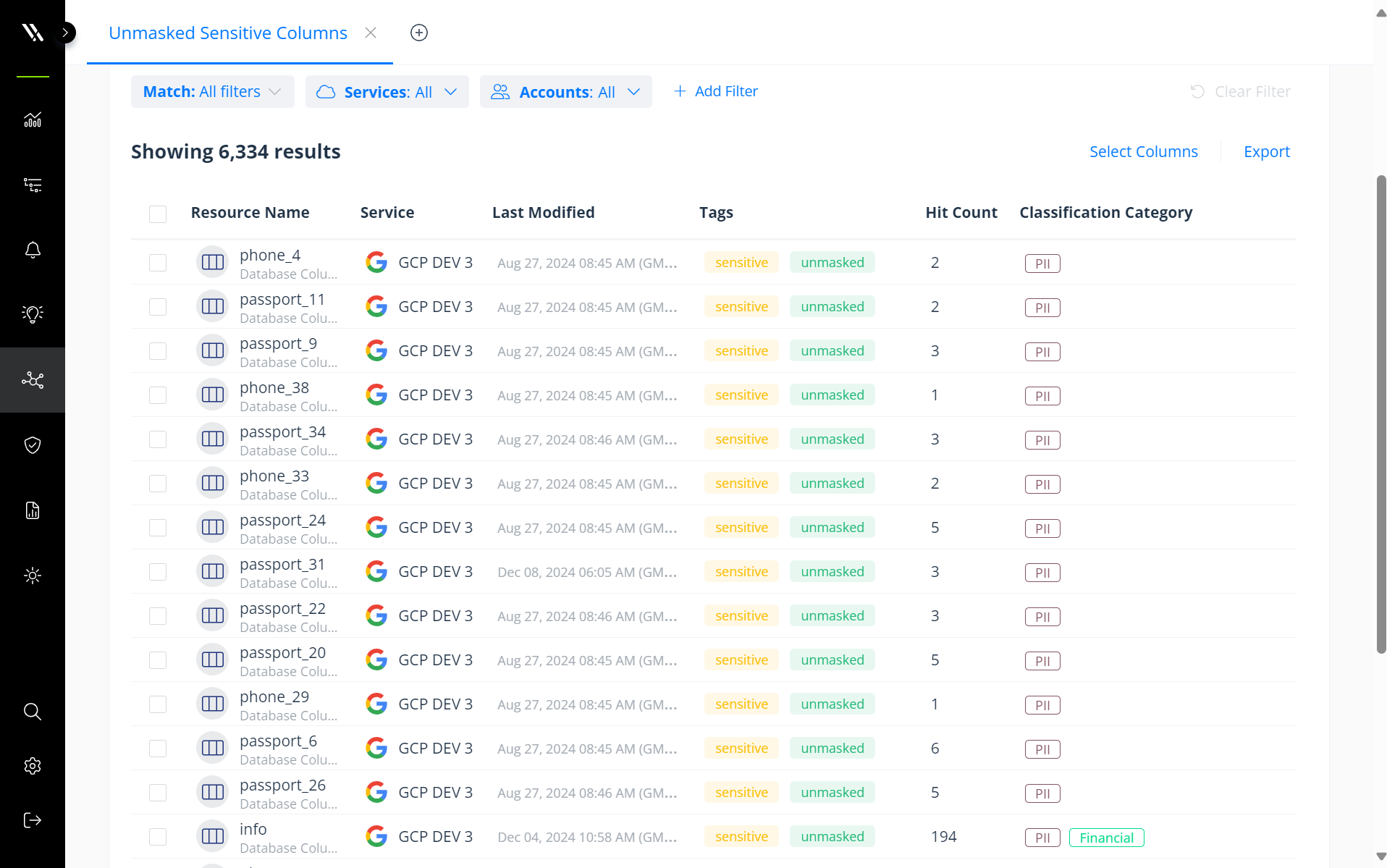
Identify unmasked sensitive columns.
Create and apply automated masking policies.
From the unmasked data report, security teams can use Varonis’ powerful policy engine to create and apply automated dynamic masking policies.
To apply the masking policies, you simply name the policy, select the masking type, and execute it. Varonis will then intelligently apply the masks to all relevant columns, ensuring that when users access this data within the targeted platform, they will only receive the masked information.
These policies can also be configured to exclude roles authorized to view unmasked data. This helps ensure that critical data is locked down and that least privilege is enforced without impeding business operations.
Configure automated masking policies.
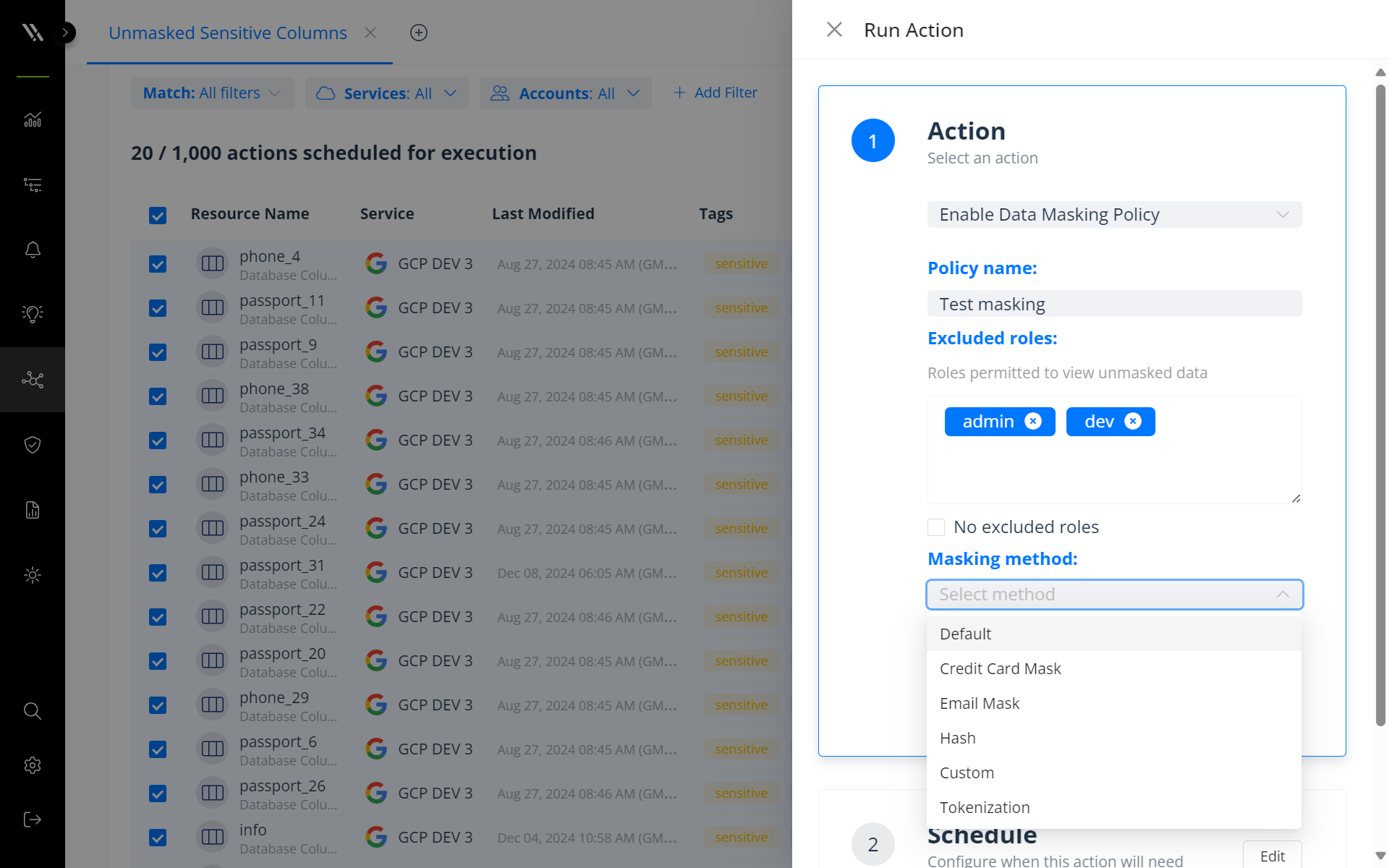
Configure automated masking policies.
Varonis uses intelligent, dynamic masking based on column type and also supports masking methods such as:
- Credit card masking
- Email masking
- Tokenization
- Hashing
You can also create custom masks that replace data with end-user-provided text.
Once you’ve implemented your masking policies, Varonis provides a comprehensive view of all resources protected by each policy and an overview of every masking policy applied to a single schema, table, or column. This view helps you confirm that you’ve correctly applied your masking policies and secured your data.
Review the resources protected by specific masking policies.
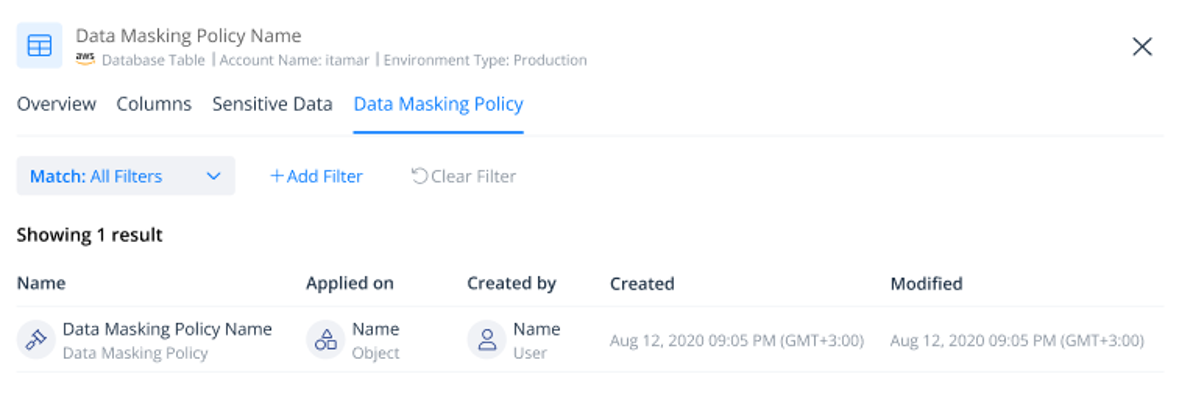
Review the resources protected by specific masking policies.
Removing Varonis-applied data masks
Varonis allows you to remove or modify data masks as needed. You can unmask specific columns automatically or manually or update existing masking policies with new ones. This enables you to manage your data masking policies with flexibility and ease.
Varonis is a dozen security products in one.
Automated data masking is one of many security controls built into the unified Varonis Data Security Platform.
Our industry-leading solution tackles hundreds of use cases, including DSPM, AI security, data-centric UEBA, identity protection, and more, making it the ultimate platform to stop data breaches and ensure compliance, regardless of where data resides.
Ready to secure your most critical data? Try Varonis for free and request a demo today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.