Varonis Identity Protection
Monitor identities across cloud data stores and applications with the most advanced identity threat detection and response capabilities on the market.
- Coverage
- Visibility
- Automation






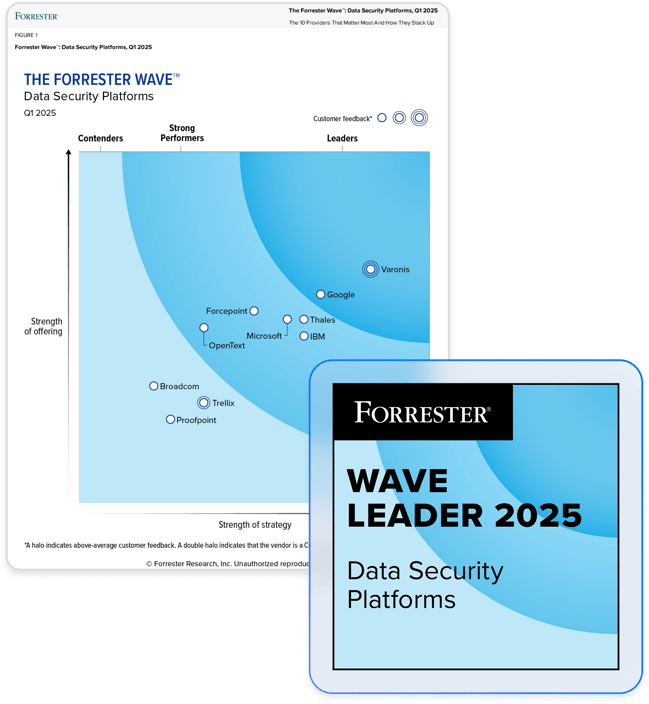
Partner with the leader in data security.
Attackers don’t hack in, they log in.
Identity Resolution
Seamlessly map identities and users across cloud and on-prem environments. Varonis intelligently correlates identity and data activity in easy-to-understand visuals, resulting in IT and security teams spending less time deciphering and more time resolving risks.
Identity Posture
Varonis provides centralized access control, enabling you to easily review, modify, and revoke access while complying with regulations and policies. Effortlessly eliminate stale users, excessive permissions, and misconfigured roles, groups, and policies.
Identity Threat Detection and Response (ITDR)
Our threat models can automatically alert on leading identity threats, such as brute-force methods or logins occurring from an abnormal location. Pinpoint and track threats with a full forensics log of actions, including file access, email activity, permissions changes, and more.
Automated Policies
Organizations need automation to effectively correct org-wide permissions and manage privileges across the data estate. Varonis is able to efficiently identify and fix accounts and configurations that make you vulnerable to password sprays, credential stuffing, and other novel attacks.
MDDR
Varonis uses machine learning to develop behavior profiles and baselines for every user and identity in your environment. Add our Managed Data Detection and Response (MDDR) service to unlock a global team that will investigate and respond to your identity alerts 24x7x365.
.png?width=543&height=416&name=Group%202627%20(4).png)
"Varonis alerts us to authentication anomalies, permission modifications, administrator group changes—anything suspicious that’s happening within our Active Directory."
Security Admin, Major Healthcare Technology Provider
Read case studyVaronis solves modern identity security challenges.
Untangle Microsoft Entra ID and Active Directory permissions.
- Automatically correct org-wide permissions and manage privileges across your data estate.
- Identify and fix accounts and configurations that make you vulnerable to password sprays, credential stuffing, and other brute-force attacks.
- Track all changes to group policies, users, computer accounts, password settings, and more.
Improve security posture in Okta.
- Automatically map users across Okta.
- Identify and fix accounts and misconfigurations that make you vulnerable to account takeover such as missing MFA and excessive enrollments.
- Track users and third-party applications for unusual behavior such as abnormal application assignments, privilege escalation, and more.
Right-size privileges across IaaS and SaaS.
- Automatically map identities, accounts, and users across Salesforce, AWS, and M365.
- Uncover access to data with granular and normalized effective permissions mapping for each identity across buckets, blobs, fields, and more.
- Identify and fix accounts and configurations that make you vulnerable to breaches, including exposed access keys, privileged policies, and missing MFA.
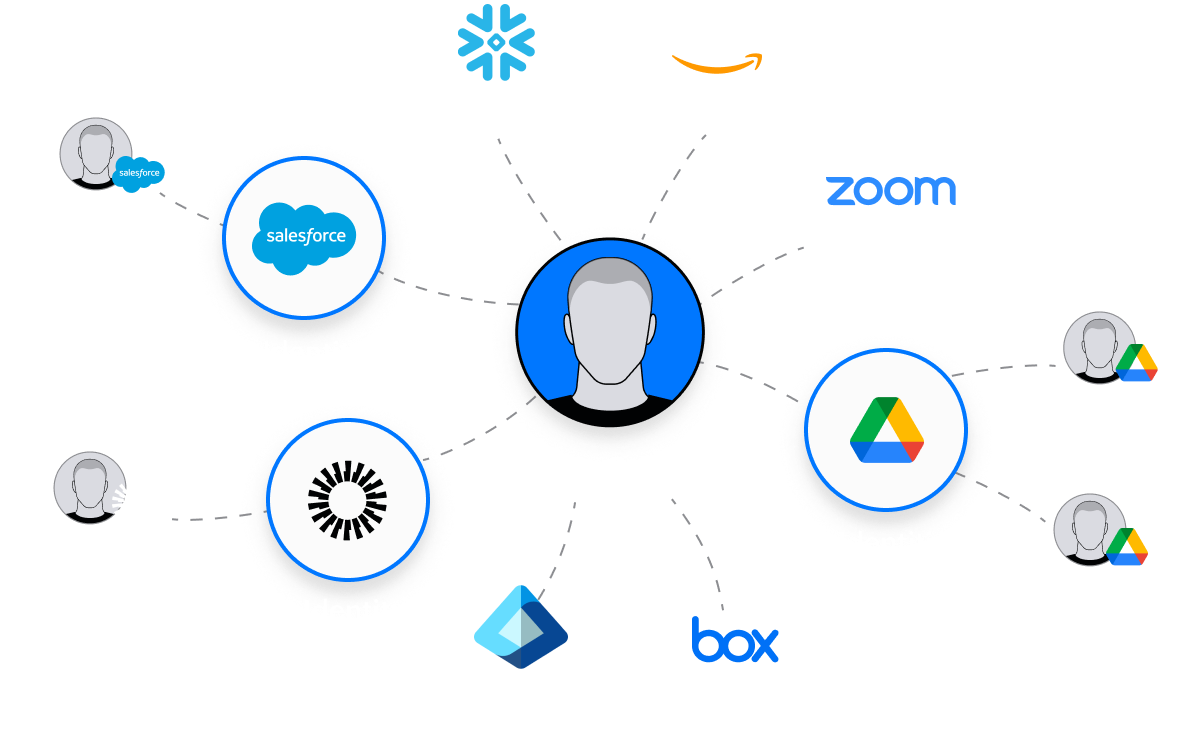
One platform for multi-cloud, SaaS, and on-premises data.
Varonis protects enterprise data where it lives — in the largest and most important data stores and applications across the cloud and behind your firewall.
Identity Protection Resources
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital














