Varonis has broadened its structured data support to include Amazon Redshift, offering a complete solution for protecting AWS environments from data exposure, insider threats, and cyberattacks. This allows organizations to secure their vital data warehouses through:
- Scalable data discovery and classification
- Granular permissions and exposure analysis
- Misconfiguration management
- Continuous activity monitoring and sophisticated threat detection
Discover and classify sensitive data at scale.
Varonis automatically maps your cloud data estate, enabling you to surface all of your Redshift database instances, whether they are serverless or provisioned clusters. Varonis then automatically scans your Redshift data warehouse to discover and classify sensitive data across your database instances down to the individual column level.
Hundreds of out-of-the-box classifiers help you understand where you have regulated data and where it’s at risk. This includes intellectual PII, financial data, and other sensitive information that drives your business decisions.
Automatically discover and classify sensitive data stored across the cloud and view results in an intuitive tree format.
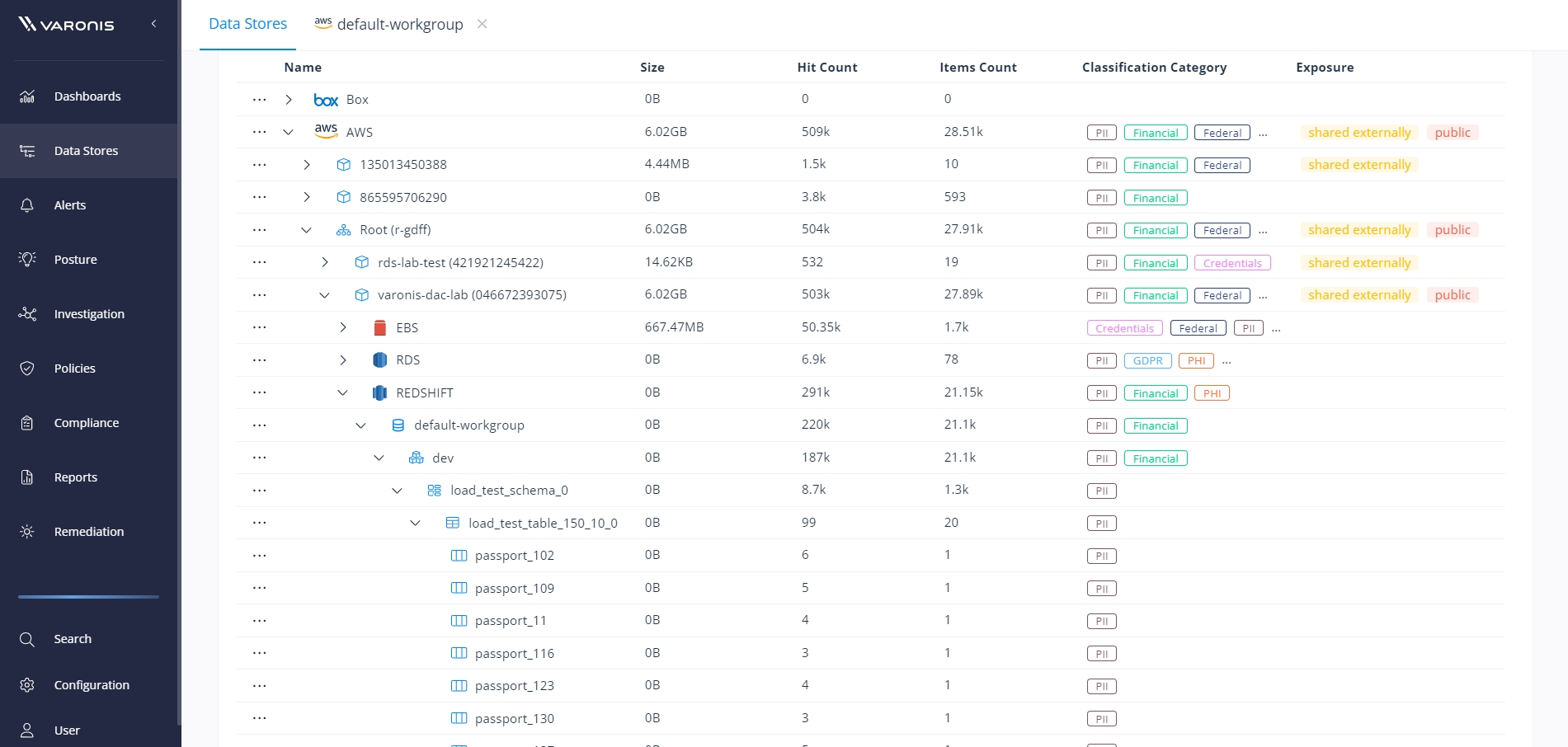
Automatically discover and classify sensitive data stored across the cloud and view results in an intuitive tree format.
Detect and fix configuration drift.
Varonis continuously monitors Amazon Redshift and the broader AWS environment to surface critical misconfigurations that may expose your sensitive data to risk and non-compliance.
We identify misconfigurations across your Redshift workgroups as they occur, such as:
- Clusters missing audit logs
- Clusters missing encryption
- _ssl database parameters disabled on serverless workgroups
- Database ports that are publicly accessible
Varonis then automatically compares your environment’s posture against standard rules and regulations like CIS, ISO, NIST, and HIPPA to detect configuration drift.
The Security Posture dashboard identifies these risks and incorporates findings from the Varonis Threat Labs, which regularly update misconfiguration risks as they are discovered.
When a configuration risk is identified, Varonis can automatically fix the problem, recommend the next steps, and provide detailed instructions on how to manually remediate if such intervention is preferred.
View misconfigurations sorted by severity in the Varonis posture dashboard and identify configuration drift across your cloud environment.
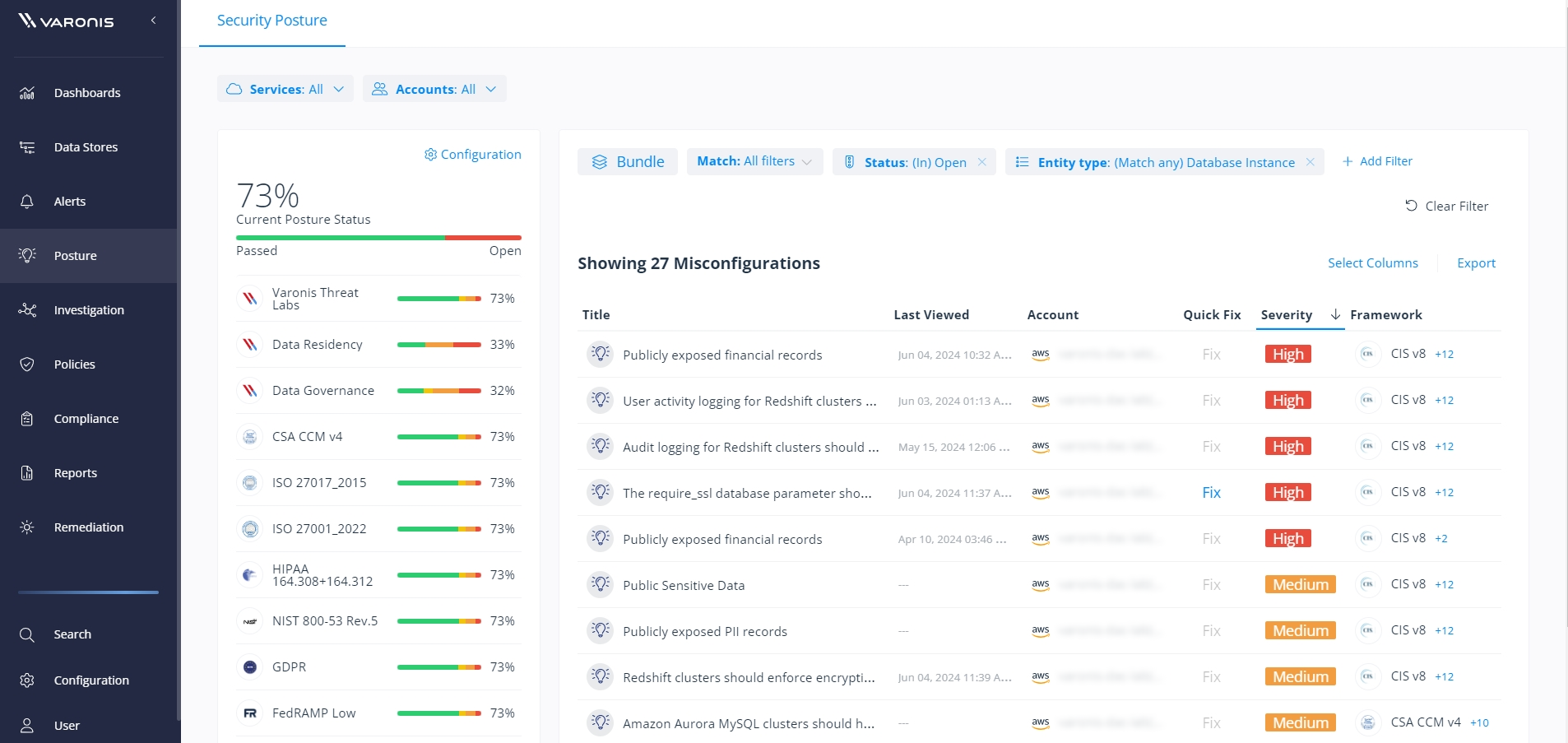
View misconfigurations sorted by severity in the Varonis posture dashboard and identify configuration drift across your cloud environment.
Easily understand and reduce your AWS blast radius.
Varonis analyzes and maps user permissions across Amazon Redshift database instances to identify where sensitive data is at risk through excessive privileges, external access, and public exposure.
Varonis simplifies complicated access policies, keys, and ACLs by normalizing permissions into a simple CRUDS model (create, read, update, delete, and share). You can also visualize each user's permissions through the access reasoning graph, giving you unmatched insight into your AWS blast radius.
Map user and role permissions across your Amazon Redshift warehouse instances.
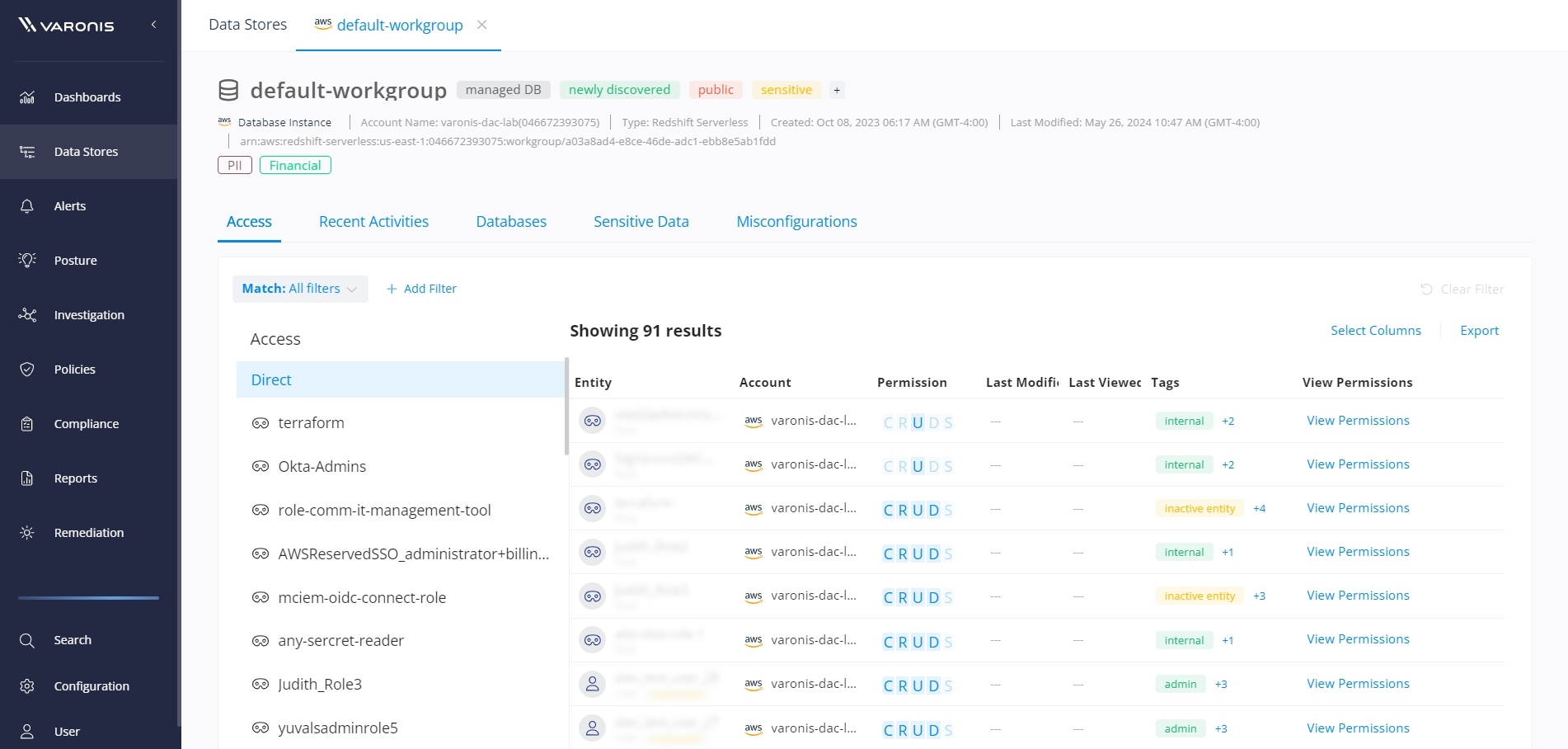
Map user and role permissions across your Amazon Redshift warehouse instances.
Monitor activity and catch threats to your critical Redshift databases.
Varonis continuously monitors your Redshift data warehouse for abnormal or risky activity that could indicate a threat or put your critical databases at risk. We proactively alert you to suspicious activity, including:
- Excessive or abnormal deletion of Redshift databases
- Disabling Redshift cluster logging
- The assignment of privileged inline policies that could expose data
Varonis maps each alert to the relevant MITRE ATT&CK tactics and techniques and provides a granular cross-cloud audit trail of events to help security teams better understand the alert’s context, impact, and phase.
Varonis maintains a complete and normalized audit trail of events that captures granular Redshift activity, such as when users create or delete database instances, modify clusters, or restore database instances from backups.
By filtering the audit trail based on privileged users, sensitivity, or activity type, you can easily investigate threats and see what sensitive data was affected across your Redshift databases and broader cloud environment.
Varonis provides a complete cross-cloud audit trail to facilitate investigations and identify lateral movement.
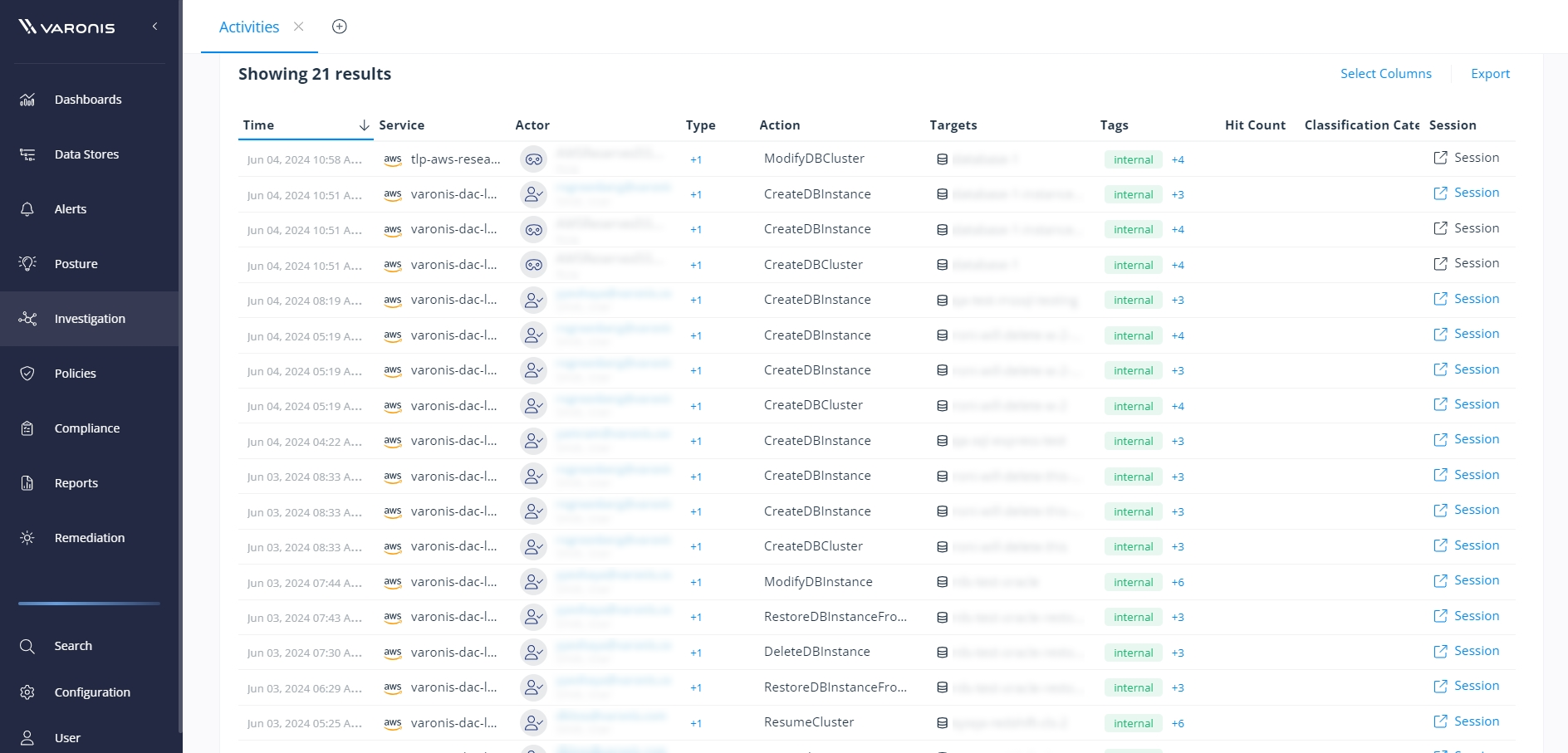
Varonis provides a complete cross-cloud audit trail to facilitate investigations and identify lateral movement.
Try Varonis for AWS for free.
Available on the AWS Marketplace, the Varonis Data Security Platform helps security teams continuously monitor and improve their data security posture in real time with the ability to:
- Access a centralized overview of their security posture with customizable DSPM dashboards
- Discover and classify sensitive data stored across structured and unstructured resources
- Identify where sensitive data is exposed, using automation to help enforce least privilege access
- Monitor sensitive data activity and alert you to abnormal behavior
- Maintain a historical, enriched, and human-readable cross-cloud audit trail to facilitate investigations
- Continuously surface misconfigurations, identify configuration drift, and automatically fix issues
Ready to improve your data security posture and achieve automated outcomes with Varonis’ leading DSPM solution? Request a demo today and visit us at AWS re:Inforce.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.