Gestion des risques internes
- Cross-cloud
- En temps réel
- Automatisé






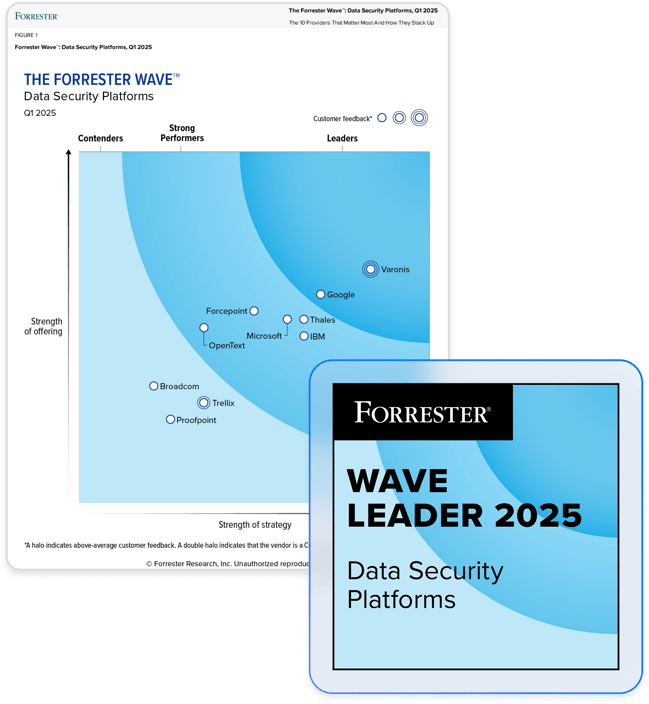
Collaborez avec un leader de la sécurité des données.
Protégez vos données des menaces internes.
Surveillance proactive
- Recevez une alerte en cas de comportement anormal
- Automatisez la réponse à incident
- Bénéficiez d’une assistance MDDR 24 h/24, 7 j/7, 365 j/an
Analyses Forensics consultables
- Répondez aux événements d’accès aux fichiers
- Faites le tri dans les élévations de privilèges
- Analysez les activités suspectes
Remédiation des autorisations
- Identifiez les utilisateurs disposant d’autorisations excessives
- Révoquez les droits risqués à grande échelle
- Minimisez votre rayon d’exposition interne
Varonis a beaucoup apporté à notre entreprise. Il a été en mesure de détecter un incident qui s'est produit dans notre environnement contrairement aux autres outils à notre disposition.
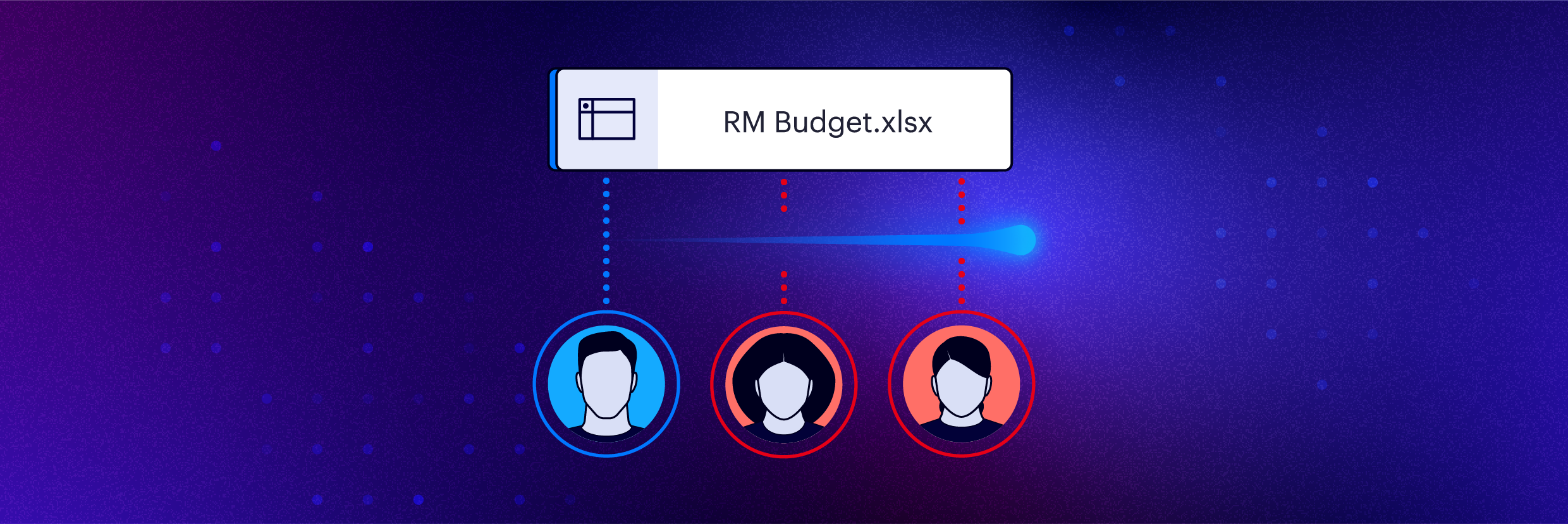
Automatisation du modèle de moindre privilège
La gestion des risques internes, cela commence par prendre des décisions intelligentes concernant les personnes autorisées à accéder aux données ou non. Varonis réduit votre rayon d’exposition en continu, sans intervention humaine, et il automatise la gestion des autorisations à grande échelle.
Audit de l’activité des données
Varonis détecte les menaces internes grâce à une surveillance continue des principaux indicateurs de compromission. Des centaines de modèles de menaces détectent automatiquement les anomalies et vous alertent en cas d’activité anormale (accès inhabituel à des fichiers, modification des autorisations, suppression de labels ou de protections, etc.).
Évaluation continue des risques
Varonis fournit une vue en temps réel de votre posture de sécurité des données, en combinant sensibilité des fichiers, permissions et activité d’utilisation. Depuis les liens partagés jusqu'aux groupes d’autorisations imbriqués, nous évaluons les permissions actives et priorisons les mesures de remédiation en fonction des risques.
Surveillance et enquête proactives
Notre équipe d’experts en cybersécurité surveille vos données à la recherche de menaces, enquête sur les alertes et ne signale que les incidents nécessitant votre attention, permettant à votre équipe de gagner du temps, et renforçant vos défenses de sécurité.
Une seule plateforme pour les données multicloud, SaaS et on-premise.
Varonis protège les données des entreprises là où elles se trouvent, dans les applications et les dépôts de données les plus importants du cloud comme derrière votre pare-feu.
Ressources pour la gestion des risques internes
Allez au-delà de la gestion du risque interne.
Êtes-vous prêt à voir la plateforme de sécurité des données n° 1 en action ?
Êtes-vous prêt à voir la plateforme de sécurité des données n° 1 en action ?
« J'ai été impressionnée de la rapidité avec laquelle Varonis a pu classer les données et détecter les expositions potentielles des données pendant l'évaluation gratuite. »
Michael Smith, CISO, HKS
« Ce que j'aime chez Varonis, c'est qu'ils se concentrent sur les données. D'autres solutions protègent votre infrastructure, mais elles ne font rien pour protéger vos biens les plus précieux : vos données. »
Deborah Haworth, Directeur de la sécurité de l'information, Penguin Random House
« L’assistance apportée par Varonis est sans égal, et son équipe continue d’évoluer et d’améliorer ses produits pour suivre le rythme effréné des avancées du secteur. »
Al Faella, CTO, Prospect Capital