This month, we released new updates designed to help you accelerate security workflows, automate your DSPM efforts, and manage shadow databases.
Our new functionality includes:
- Webhook integration support
- Industry-first AWS remediations
- Shadow database discovery
- Amazon Redshift support
- Salesforce risky permissions remediation
Discover what’s new for Varonis customers in this quick 3-minute video or continue reading for all the details.
Integrate data-centric insights into your security workflows using webhooks.
Security teams can now easily integrate Varonis into their broader security stack by sending Varonis’ enriched, data-centric alerts and security insights to SIEMs and SOARs, communication solutions like Slack, automation platforms like Tines, and more.
Varonis comes with out-of-the-box integrations for Slack and Microsoft Sentinel, but teams can easily integrate Varonis with virtually any platform that accepts webhooks.
With these integrations, security teams can:
- Triage alerts in Microsoft Sentinel for investigation and response
- Automate misconfiguration remediation workflows with Tines
- Notify relevant personnel of incidents with real-time security insights in Slack
Read our blog to learn more.
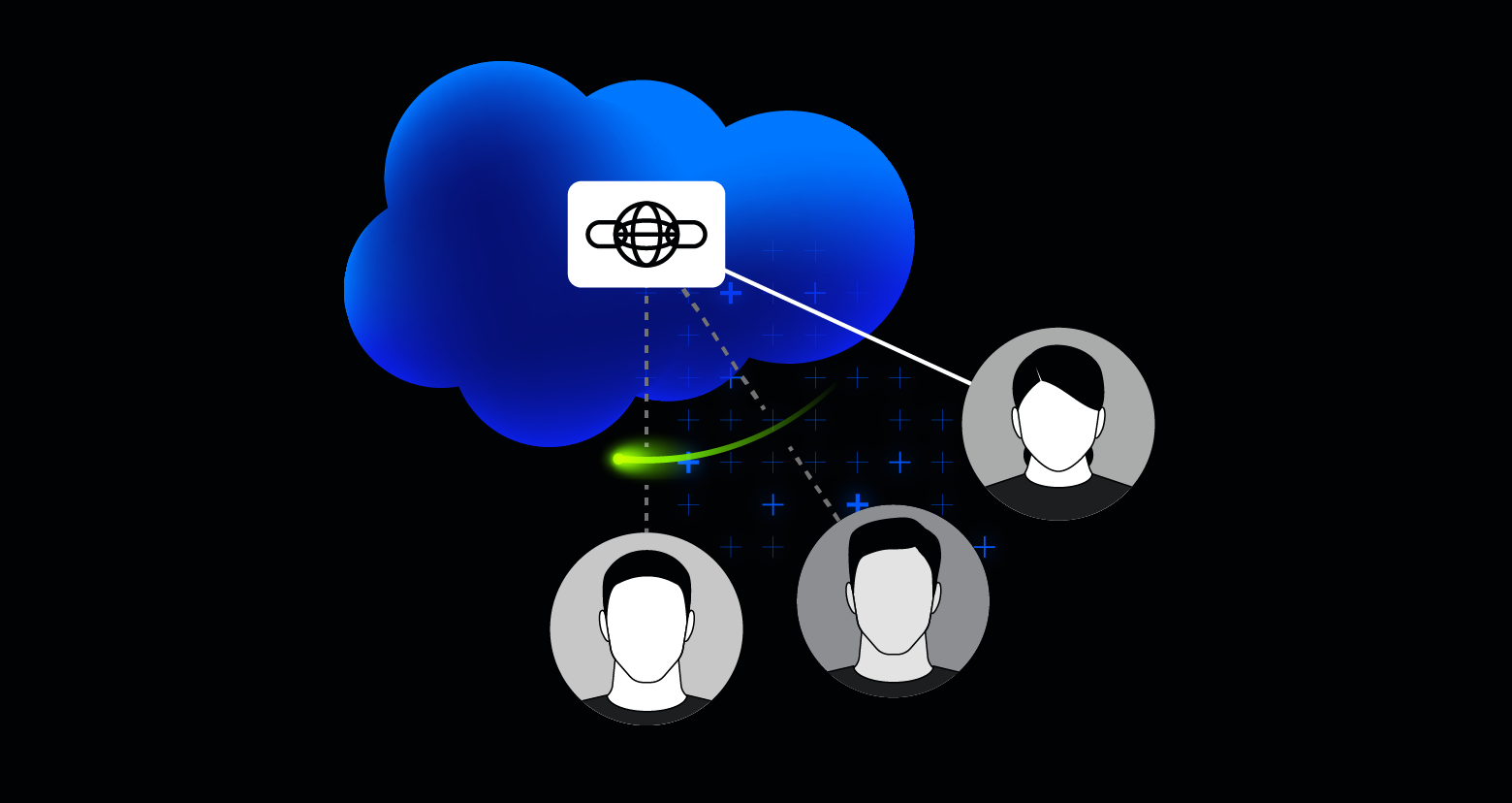
Send Varonis’ enriched data security alerts and insights to Slack or your preferred SIEM, SOAR, or other workflow solutions.
Send Varonis’ enriched data security alerts and insights to Slack or your preferred SIEM, SOAR, or other workflow solutions.
Expanded remediation in AWS
With Varonis’ automated remediation, security teams can automatically apply public access blocks on all S3 buckets containing sensitive data.
You can perform this remediation in bulk, on a schedule, or continuously so that you always stay ahead of new exposures.
A detailed activity audit trail can also help you detect when users make buckets public so you can address risk as soon as it happens.
You can also now use Varonis to remove stale users, roles, and access keys in AWS at scale.
Varonis maintains a complete inventory of users, roles, and access keys in your AWS environment and identifies which are stale based on a customizable inactivity period. Varonis then surfaces the stale entities in the IaaS dashboard, creates reports for easy review, and enables you to promptly eliminate them from your AWS account.
Set up reports to send to your cloud security architects on a regular basis to review and approve entities for removal by Varonis.
Read our blog to learn more.
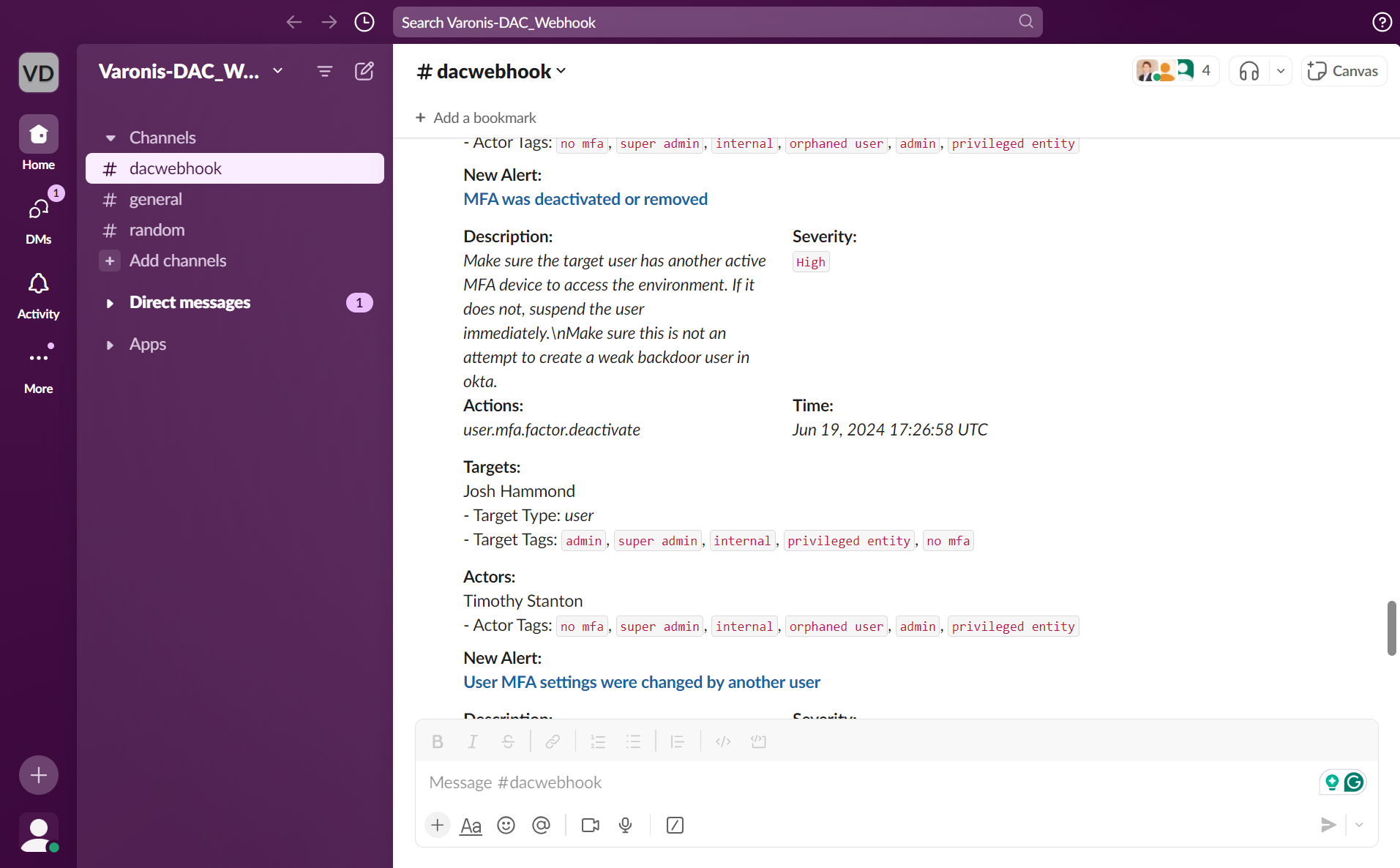
Automatically apply public access blocks to S3 buckets.
Automatically apply public access blocks to S3 buckets.
Shadow database discovery
Varonis has improved its leading data security posture management (DSPM) capabilities by enabling the discovery of shadow databases — unmanaged databases created without the security team’s knowledge — across AWS environments.
With this release, Varonis can:
- Classify sensitive data stored in EBS volumes, unmanaged databases, and snapshots
- Surface orphaned snapshots
- Identify backups and dumps stored in S3 buckets and link them to the relevant database
Security teams now have a clear view of all their databases, including unmanaged shadow databases.
Read our blog to learn more.
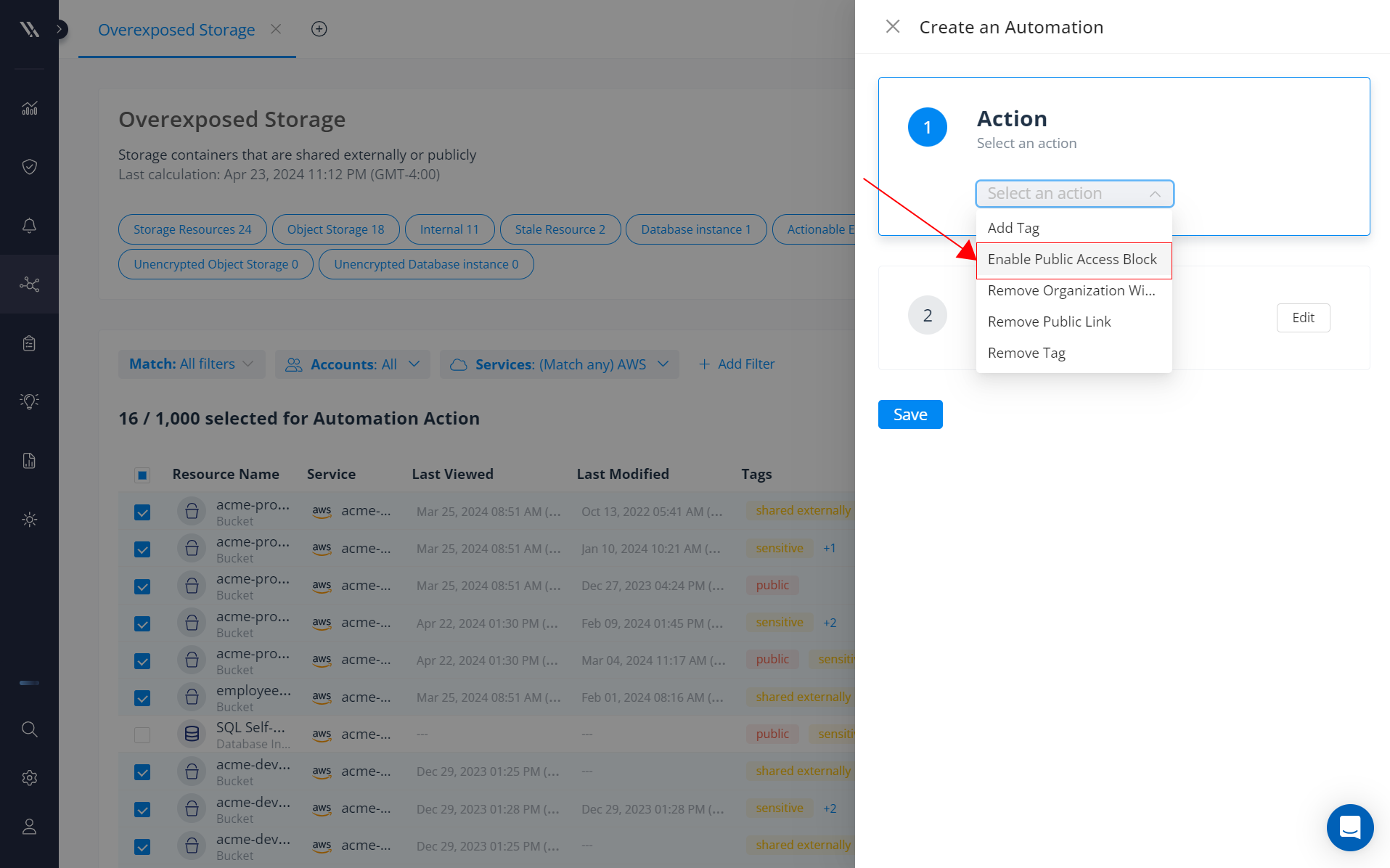
See an overview of the databases in your environment from a single console.
See an overview of the databases in your environment from a single console.
Expanded database coverage — Amazon Redshift support
By expanding Varonis’ support for structured data to AWS Redshift, organizations can be confident their critical data warehouses are secure.
Providing a complete solution for protecting AWS environments from data exposure, insider threats, and cyberattacks, Varonis enables:
- Data discovery and classification
- Permissions and exposure analysis
- Misconfiguration management
- Activity monitoring and threat detection
With user and role permissions mapped across all Amazon Redshift warehouse instances, you can easily understand and reduce your AWS blast radius.
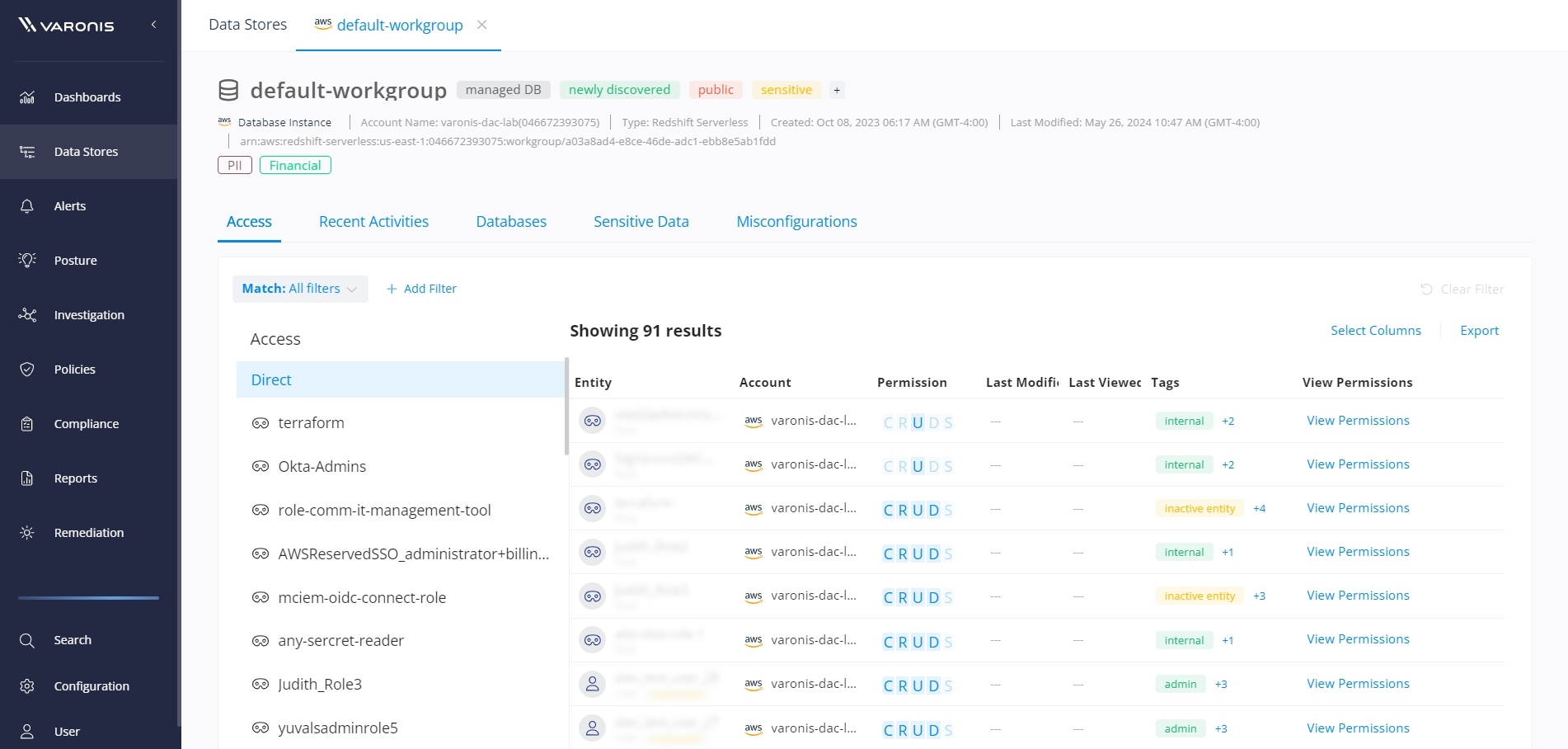
With user and role permissions mapped across all Amazon Redshift warehouse instances, you can easily understand and reduce your AWS blast radius.
Revoke the ability to create Salesforce public links.
The latest update to Varonis for Salesforce gives security teams more control over public links. You can now find and remove the permission to create public links directly from Profiles and Permission Sets.
Use Varonis for Salesforce to automatically identify every Profile and Permission Set that contains the “create public link” permission, the users assigned these entitlements, what sensitive data each entitlement grants access to, and which users are actively creating public links.
It only takes a few clicks from the automated report to revoke the “create public link” permissions from your entitlements and commit the changes to Salesforce.
This new feature builds upon our existing remediation capabilities to find and remove public links in Salesforce, making Varonis the only solution that enables you to both limit the ability to create public links and remove existing links that expose sensitive information.
Revoke the “create public link” permission from entitlements with only a few clicks.
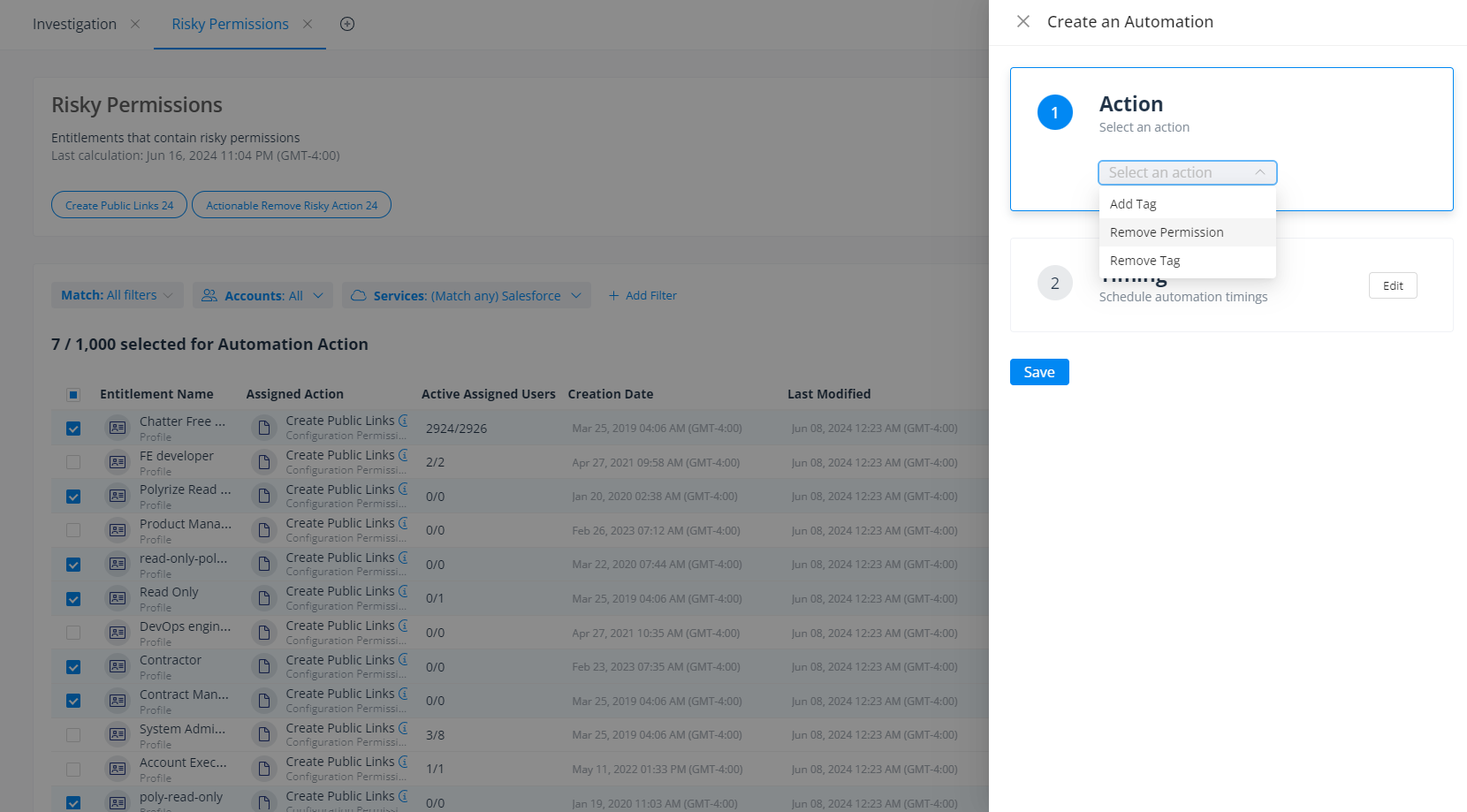
Revoke the “create public link” permission from entitlements with only a few clicks.
Keep up with the latest Varonis product releases.
Varonis’ offerings move fast! Discover product updates you may have missed on our blog.
For more information, including release notes and how-to videos, visit the Varonis Community.
See Varonis in action and request a demo today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.