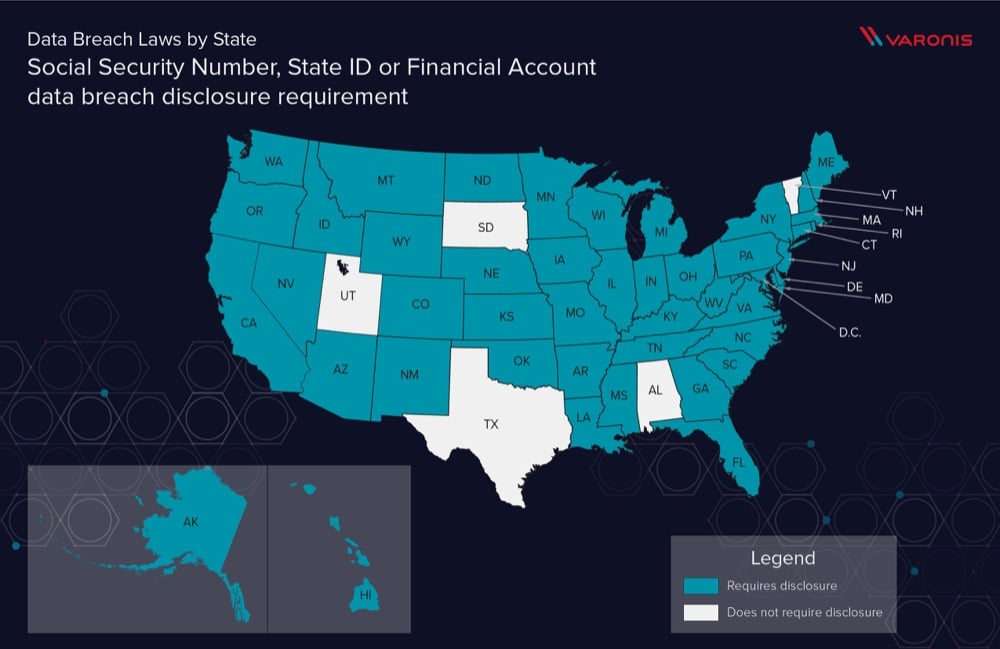
Those of you who have waded through our posts on US state breach notification laws know that there are few very states with rules that reflect our current tech realities. By this I mean there are only a handful that consider personally identifiable information (PII) to include internet-era identifiers, such as email addresses and passwords. And even fewer that would require a notification to state regulators when a ransomware attack occur.
Access Alone, or Access and Acquire, That is the Question!
Remember the loophole in state breach laws with respect to ransomware?
Get the Free Essential Guide to US Data Protection Compliance and Regulations
Just about all state notification laws define a breach to be unauthorized access and acquisition. Since ransomware merely accesses the data — it encrypts it — without copying or exfilitrating, such an attack would not have to be reported under that definition.
I’ve been able to find only three states — though there may more lurking— that consider a breach to be either access or acquisition: New Jersey, Connecticut, and, most recently, North Carolina.
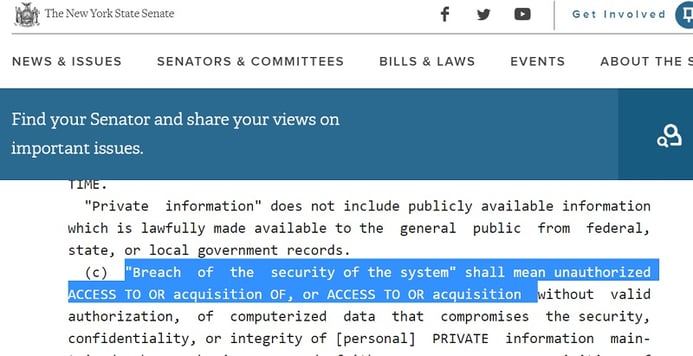
But late last year, New York began making a bid to join this elite club. The NY Attorney General Eric Schneiderman proposed the Stop Hacks and Improve Electronic Data Security Act (SHIELD Act) to “close major gaps in New York’s data security laws, without putting an undue burden on businesses.”
NY’s SHIELD — love that abbreviation — will update the state’s legal definition of a breach to use the “or” word, thereby closing the ransomware gap.
By the way, if you’re wondering whether other federal and international data security laws have ransomware loopholes — they do! — and breach notification legalese brings out your inner attorney, you’ll love our in-depth white paper on this very subject.
Anyway, the AG also proposes to tweak the state’s current PII definition to now encompass user name or email address (along with a password), biometric data, and even HIPAA-style protected health information or PHI.
The Data Empire State
Those who love the wonky details can peruse the SHIELD Act here and review all the changes it will make to the current legal language on the books.
SHIELD will also require something new as well: companies will need “reasonable administrative, technical, and physical safeguards for sensitive data”— the standard boilerplate that we see in many federal laws. This is as non-prescriptive as it gets, so for now this mostly serves as a warning to companies to have some minimal security policies and procedures in place.
SHIELD is just a legislative proposal at this point, and has yet to be finalized and passed by the legislature. We still have a long way to go. But once that happens, I expect we’ll get additional guidance on some of the law’s nuances from the state. We’ll keep you posted.
I’d like to point out that the SHIELD Act covers any company that does business in NYS. This means that it does have a GDPR-like extended territorial scope aspect to it — in this case, the law crosses state boundaries. In other words, if a California-based e-commerce company collects data from NYS residents, then they would be covered by SHIELD, and would have to report, for example, an exposure or access of PII to NYS authorities.
Yeah, there’s some legal questions about whether NYS can assert jurisdiction in other states.
One last wonky point: New York State’s other data security law, its Department of Financial Services (NYSDFS) own cyber regulations, covers banks and financial companies. It also has breach notifications rules, which we wrote about here.
In short: New York’s financial companies are covered by the NYSDFS regs; for everyone else, the SHIELD Act will apply.
With all this data security legal innovation, New York is at the forefront among states in protecting data and setting a bar — although initially low — for security practices for anyone doing business in the Empire State.
Varonis Perspective
With the Facebook hearings just about over, it appears that Congress may legislate at a national level, at least in terms of data privacy. There are many proposed breach notification and data protections laws also kicking around Congress. A much-needed national law may be on the horizon as well.
The data security legal winds are changing! Why wait to be taken by surprise at a later date?
You can start preparing by reviewing existing security plans and procedures, paying particular attention to incident or breach response. In particular, to support NY’s breach rule requiring notification on unauthorized access to PII, you’ll need to be able to classify your file system data, and then alert IT security when specific types of sensitve file data are accessed in an usual way.
Not everyone, ahem, can do this!
You’ll also find that the Varonis site to be an incredibly rich resource for data security wisdom. We have many posts and white papers on existing standards and their controls — PCI DSS, NIST 800 family, SANS Critical Security Controls (CSC) — that will provide ideas and inspiration for meeting New York’s new rules.
And we explain how Varonis can help with our DatAdvantage, DatAlert, and DataPrivilege products.
Need to know more? Click here to request a free risk assessment today!
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.