In the data management and IT space there have been significant consideration and hand wringing about how the European Union’s General Data Protection Regulation (GDPR) will eventually impact US based businesses or how a future US Federal data breach disclosure law might affect IT operations. What often is the missed in the discussion is that there are significant per state data disclosure notification regulations currently in effect in the USA..
What’s even worse, as laws vary so much state to state, you might not realize that they’re applicable to you until you’re already broken them.
Get the Free Pen Testing Active Directory Environments EBook
What is a Data Breach?
A data breach is the intentional or unintentional release of confidential, private, or secured data to an untrusted entity. Data Breaches result in the release of Personally Identifiable Information (PII), Personal Health Information (PHI) or trade secrets. Credit card numbers, social security numbers, and bank account information are common targets in a data breach. Data breaches are usually theft for monetary gain, but some incidents have been related to international espionage activity.
Data integrity centers around control. Who can access a particular piece of data? Who has rights to modify a file? What accounts can write to a database?
If at any point, for any reason, an organization loses control of a piece of data it’s considered to be a data breach.
From a technical perspective there is a massive difference in the severity of the threat posed by something like the OPM Data breach – which exposed the background investigation files, fingerprints, medical history and Social Security Numbers of 4.2 million people and the forum software on a relatively small website being compromised.
While vastly different in scope and in the type of data that was exposed, it’s important to realize that the analysis, response and notifications that need to be taken are exactly the same.
We are right now living in a world where it’s very likely that what were previously routine attacks or incidents should be reported as a data breach.
Scenarios That Call for a Data Breach Notification Plan
Depending on what state you’re in and exactly what was exposed any of the following scenarios would trigger the need for you to execute on a data breach notification plan:
- A phishing attack that revealed employment data on a half dozen employees.
- A spreadsheet with a list of student emails and if they had peanut allergies
- A forum breach where emails and passwords were taken.
- A cloud based service that you use experiencing a security incident.
A ransomware attack that encrypts files containing PII data is considered a data breach in legal terms as while the data hasn’t left the confines of your network, it’s no longer in your control.
Data Breach Notification: How to Prepare?
Understanding what data is in your possession, who it’s associated with and who is using it are all keys to making breach notification decisions. Use our data breach checklist below to assure you don’t miss any important preparation points.
Data Breach Preparation Checklist
- Properly associate your data with a user.
- Maintain up to date contact information.
- Keep up to date records of which US State a person resides in:
Self reported (shipping or billing address) and when it was last updated
IP address - Classify your data by type.
- First or last name
- Social security number
- State ID numbers (driver license, passport)
- Any financial account information
- Any biometric information (fingerprints, retina scans, etc.)
- DNA (genetic) identifiers
- Electronic signatures
- Employer ID numbers or access codes
- Any financial information (ex: retirement account numbers, investment information)
- Health insurance info (health insurance ID)
- Any medical information
A product like the Data Classification Framework can be very helpful in identifying PII within files on a network.
You Discover a Data Breach, Now What?
First, you should take whatever steps are necessary to prevent further data loss (patch, modify permissions, other remediation). Next:
- Formally note the date you first became aware of the data breach as the clock is ticking.
- Determine the number of people affected.
- Find out exactly what user identifying data attributes were disclosed.
- Investigate to find out exactly what types of application data were affected.
- If you prepared and have per state user information, determine what communication options you have to contact each person (email, sms, mailing address).
Data Breach Notifications: How to Avoid Doing Them?
We’re going to presume that you’re already taking steps to secure your network and applications properly. You may or may not have taken additional steps to structure and monitor your data internally. Doing so both better protects data you’ve been entrusted with and limits the potential that you’ll need to be in a meeting with the CEO, Chief Legal Counsel and the Attorney General of your state.
Have a Data Retention and Purge Plan
Purge unused data (quantities of data matter as different rules are triggered at higher numbers of affected users). Products like Data Transport Engine and others allow you to do do things like remove data based on rules like “File hasn’t been accessed in 6 months”. Other applications like DatAdvantage let you conduct entitlement reviews continuously to limit who has access to what data.
Separate Authentication and Application Data
While this isn’t always possible, having separate higher security user authentication systems that contain users’ email, password (or other auth system) allows for another layer of security.
A great recent example of this is the Unity Forum data-breach. Unity is a framework for developing 3D content like games and virtual reality experiences. They have tens of thousands of developers who ask questions of each other and have discussions around such exciting topics as: “Dynamically Translating/Rotating a NavMeshSurface/NavMesh Agent”.
Users log into the forums via a central UnityID service that also controls access to their asset store, question and answer site, etc. So while their forums were defaced they were able to write:
On April 30, our public forum website was attacked and successfully compromised due to poorly implemented password routines; our investigations show no theft of passwords in this attack, nor impact to any other Unity service.
What’s unsaid is that they also sidestepped most data breach disclosure requirements as in most cases losing control of user passwords is a trigger. This separation helps keep a bad situation from turning into a legal quagmire.
Who to Notify When Data Breach Occurs?
Affected users should be notified that a data breach has occurred. It’s important that they are informed of what has occurred and what steps they should take “without undue delay”.
Do I Need to Notify each State’s Attorney General?
Depending upon the per state breakdown of affected users, each state attorney generals’ office may need to be notified. For example, Hawaii requires that the attorney general be notified if over a 1000 state residents are included in breach, whereas North Data requires notification for more than 250 and New York State if any state residents are affected.
Do I Need to Notify a Nationwide Consumer Credit Reporting Agency (Credit Bureau)?
Similar to the Attorney General notifications, per state requirements govern whether you will need to contact Consumer Credit Reporting Agencies (CCRA). Depending on the type of data that has been compromised you may need to coordinate requesting fraud alerts and freezing credit cards.
- Equifax – www.equifax.com – 1-800-685-1111.
- Experian – www.experian.com – 1-888-EXPERIAN (397-3742)
- TransUnion – www.transunion.com – 1-800-916-8800.
How Should People be Notified of a Data Breach?
For most small scale breaches (defined per state) notifications can be done via email, mail or telephone. It’s recommended to contact people in the most expeditious way possible, which for most organizations likely means you’ll be conducting notifications via email.
In cases where the the cost of notification exceeds a certain limit (most often $200,000), the number of people affected exceeds a threshold (most often 500,000) or in cases where you don’t have sufficient contact information to send individual notifications, mass notification procedures can be used instead.
Typically this comes down to placing a “prominent” notification on your public facing website for a period of time sufficient to inform affected users.
Alternatively, statewide media may be contacted and informed of the data breach. Typically this is considered to mean that you send your breach disclosure information to the newspapers and TV stations operating in the state. This quickly becomes something complex enough that you should not tackle on your own, instead use a Press Release service to distribute your notification. Such as:
- PR Log – https://www.prlog.org
- PR – http://www.pr.com
- PR Newswire – https://www.newswire.com
How can I Figure Out What States My Users Reside In?
By far the easiest method is to ask them and then periodically reconfirm that their information is up to date. If you have ever registered a domain, you’ve likely received an email asking you confirm that your contact information is up to date. If circumstances allow you, you could build something similar into your own application or processes.
Unfortunately, that’s not always an option. A solid fallback is to record the most recently IP address of each user when they reconnect with your service. You may already be recording this for other reasons (rate limiting, load balancing, it’s a default feature of your authorization service, etc).
If needed you can then run the user recorded IP addresses through an IP to location service such as MaxMind, or FreeGeoIP which will return general location information including which US State the IP is located within.
It’s important to keep in mind that all of these services become increasingly inaccurate as the geographic specificity increases. In almost all cases they’ll identify what country a person is connecting from correctly, and in the vast majority of cases (barring VPN use or other network oddities) the state. If you’re relying upon IP state identification, it is probably a good idea to err on the side of caution and presume that you have mis-identified a few user locations if you’re on the cusp of a state notification limit.
What to Include in a Data Breach Notification?
California has the most detailed breach notification requirements in the United States, up to and including specifying the font-size that notifications should be displayed with.
Their requirements (and an excellent guideline for all communication) below:
- Write in plain english.
- Title and Headings should be conspicuously displayed.
- Should be titled: “Notice of Data Breach” with paragraphs covering:
- What happened
- The date of the breach, estimated date or date range
- What information was involved
- What we are doing
- What you (the user) can do
- A place to find more information
- Note: don’t use font smaller than 10pt type
In the case of California (and other states) there are further mandates based around the type of data exposed. For instance, if a social security number or a driver’s license or California identification card number is exposed then the toll free numbers and addresses of the major credit reporting agencies (listed above) need to be included in the communication.
We’ve included a copy of their form for your use below:
Download: California Model Data Breach Disclosure Form
Data Breach Notification Deadlines
It’s important to note that the timing requirements for disclosure are based around when your organization first learned of the data breach. The majority of states require that data breach notifications are sent: “Without undue delay”, most aggressively this is defined as within 30 days of discovery.
The distinction is important as there is often a significant lag between when a breach happens and when it’s discovered (many times by an outside party).
Given the tight timelines, it’s not practical to manually review all the different US State data breach notification laws.
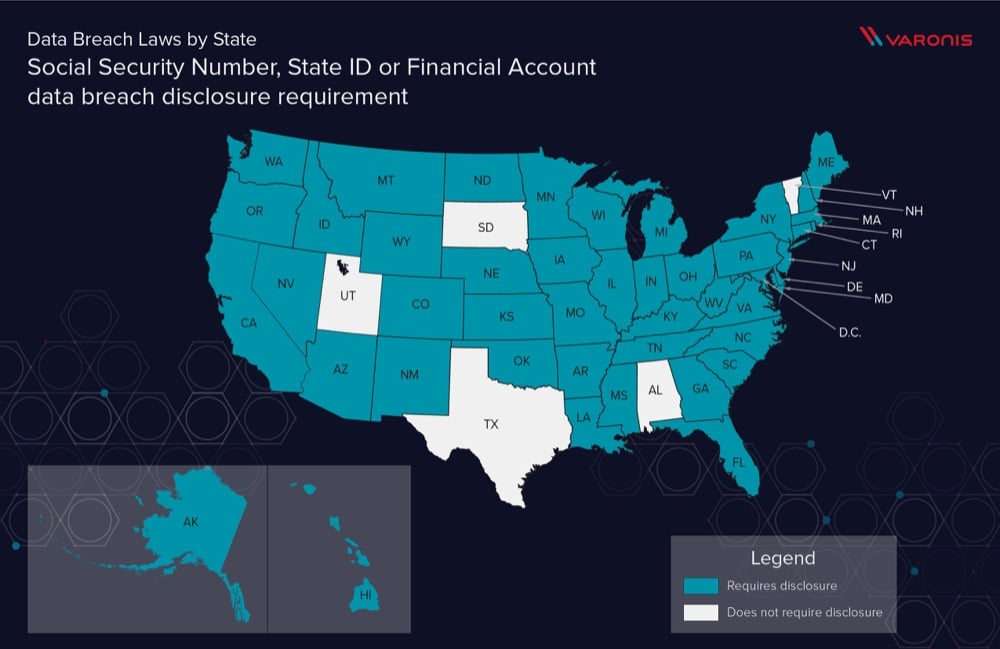
Now that we’ve gone through the importance of understanding what classes of data you have in your control, take a look below to see how PII is protected per state.
We stress this point as it’s easy to get lost in the different numerical conditions around per state data breach disclosure. What’s often not considered is that due to differences in how a state defines Personally Identifiable Information (PII), what may be considered a data breach in North Dakota might not be a data breach in Florida.
Typically “Personal information” does not include publicly available information that is lawfully made available to the general public from federal, state, or local government records.
Also, it’s important to remember that these data points are combinatorial. For example, emailing a spreadsheet of Social Security Numbers that did not include associated first and last names likely wouldn’t be considered sufficient to trigger data breach disclosures in most cases.
All of this results in the need to understand exactly what information was lost in a breach.
What is PII?
PII stands for Personally Identifiable Information. It is legalese for any data that could allow one human to locate or identify another. For example, with just a first and last name it can be difficult to track someone down. But with their social security number or their bank account information it is much simpler. PII definitions vary across jurisdictions, and organizations must understand the PII laws they need to follow.
Almost all states consider a mixture of:
- First Name or Last Name
- Social Security Number
- State ID (Driver License, Passport) – Given that these are per state laws, they are often keenly interested in disclosure of Driver’s License numbers, Passport information, etc.
- Financial Account Information (account code, passcode, password). Typically this is summarized as “any ability to access a financial account” and encompasses anything that might be used for access to bank, credit card, retirement, investment or savings accounts. The definition is broad enough to include things like cryptocurrencies as they’re clearly financial in nature.
With that as the baseline we can then start to consider some more of the outlying criteria. While this may or may not affect you today, the conventional wisdom is that sometime in the not too distant future a comprehensive Federal Data Breach disclosure law is going to be passed. Most likely it will be a roll-up of the different state disclosure laws.
Given this, it’s good to consider this a roadmap of the data that you need to preferentially protect, manage, secure and dispose of to protect your organization from breaking the law.
Data Breach Notification Laws: Account
In large part, mass data breaches are dangerous because consumers often reuse credentials between accounts. It’s not uncommon for someone to use the same email address and password between say their social network, their bank and their preferred shopping site.
This means that a breach in any one of those systems actually compromises them all.
With that in mind, I was pleasantly surprised to find that a handful of states require notification if any kind of username/password is leaked from a service (as it’s quite likely that those passwords would also unlock more sensitive financial or medical accounts)
These statutes are not widely known and potentially affect thousands of tiny one off SAAS services, forums, blogs, companies and other websites.
It’s a big change from the mindset of “We don’t have any valuable information, so it’s not a big deal if we’re hacked.”
Someone who runs a moderately popular WordPress blog with comments enabled is likely not thinking “I need to check Georgia Data Breach Notification laws” when their site gets hacked.
Data Breach Notification Laws: Biometrics
Biometrics are increasingly popular as a means of adding additional factors to authentication or as a user friendly way of securing access. Given this, unsurprisingly, unauthorized access to biometric data is considered to be a leak of personally identifiable information.
Fingerprints, retina/iris scans or any other “unique physical representation” (so presumably facial recognition, palm scans, gait analysis,etc would all fall under this category).
The statutes themselves don’t get into the fine detail of what constitutes biometric storage. They don’t differentiate storing a high definition image of a thumbprint from a system that takes sample points from a thumbprint and stores a hash of the value. Unauthorized disclosure of either would be considered a data breach.
Data Breach Notification Laws: DNA
Currently, only Wisconsin considers a disclosure of your personal genetic makeup to be “Personally Identifying Information”.
Data Breach Notification Laws: Electronic Signature
Somewhat maddeningly, the definitions for what constitutes an electronic signature are quite vague. But it would fairly safe to assume that they include PKI keys as a signatory mechanism.
To me this is interesting as there are lots of cases where a web host might have thousands of vulnerable sites in standalone VPS silo’s. You could imagine some PHP bug that allowed for the contents of them to listed – which would then trigger the disclosure rules.
Data Breach Notification Laws: Medical Data

Generally defined as: “any electronic or physical information about treatment, diagnosis or history”, which extends far beyond a formal medical record as one might have in a hospital.
Consider something like a consent form for a trampoline park (not pregnant or has a history of heart issues) or a checkbox in a form that indicates that someone has a peanut allergy.
Data Breach Notification Laws: Date of Birth
Date of Birth is often used as a security question and inclusion of it as a PII indicator seems forward thinking.
Data Breach Notification Laws: Employer Code
An identification number assigned to the individual by the individual’s employer in combination with any required security code, access code, or password.
Data Breach Notification Laws: Mother’s Maiden Name
Long used as the answer to security questions, disclosure could potentially be used for account recovery attacks.
Data Breach Notification Laws: Health Insurance
This is distinct from any actual medical information, but purely items of information like who is providing coverage and the identification number for the account.
Data Breach Notification Laws: Tax Information
I’m honestly a bit surprised that tax information isn’t more often considered to be a reportable data breach event as it’s so often used as a means of identification.
We hope this underscores the importance of classifying the data on your network to better prepare for a potential data breach.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.