With the sheer amount of data and users leveraging AWS, it’s easy for misconfigurations to slip through the cracks. One commonly overlooked area is the naming of S3 buckets.
AWS S3 bucket names are global with predictable names that can be exploited by bad actors seeking to access or hijack S3 buckets. This is known as “S3 bucket namesquatting.”
The use of predictable S3 bucket names presents a widespread issue. Thousands of instances on GitHub use the default qualifier, making them prime targets for exploitation.
In this blog, we will examine the occurrence of S3 bucket namesquatting, methods to address the issue, and how Varonis can prevent this and other related data security problems in AWS.
What is S3 bucket squatting?
S3 bucket namesquatting can occur in several ways, but the root cause always depends on predictable naming qualifiers.
For example, when new regions are released, bad actors can preemptively register buckets before the actual owners can claim them by correctly guessing the names. Although AWS Region names aren’t usually made public, they can be deduced by those familiar with qualifiers and region names. If a bad actor knows the timing of a new region release, they can proactively register buckets before the owners can.
S3 bucket namesquatting can also occur when using the AWS Cloud Deployment Kit. The AWS Cloud Deployment Kit creates staging S3 buckets where resources are provisioned to the environment with a predictable naming pattern: cdk-{Qualifier}-assets-{Account-ID}-{Region}. If users don’t customize the names, they are leaving the door open for bad actors.
AWS S3 buckets have predictable naming structures that can be exploited by attackers.
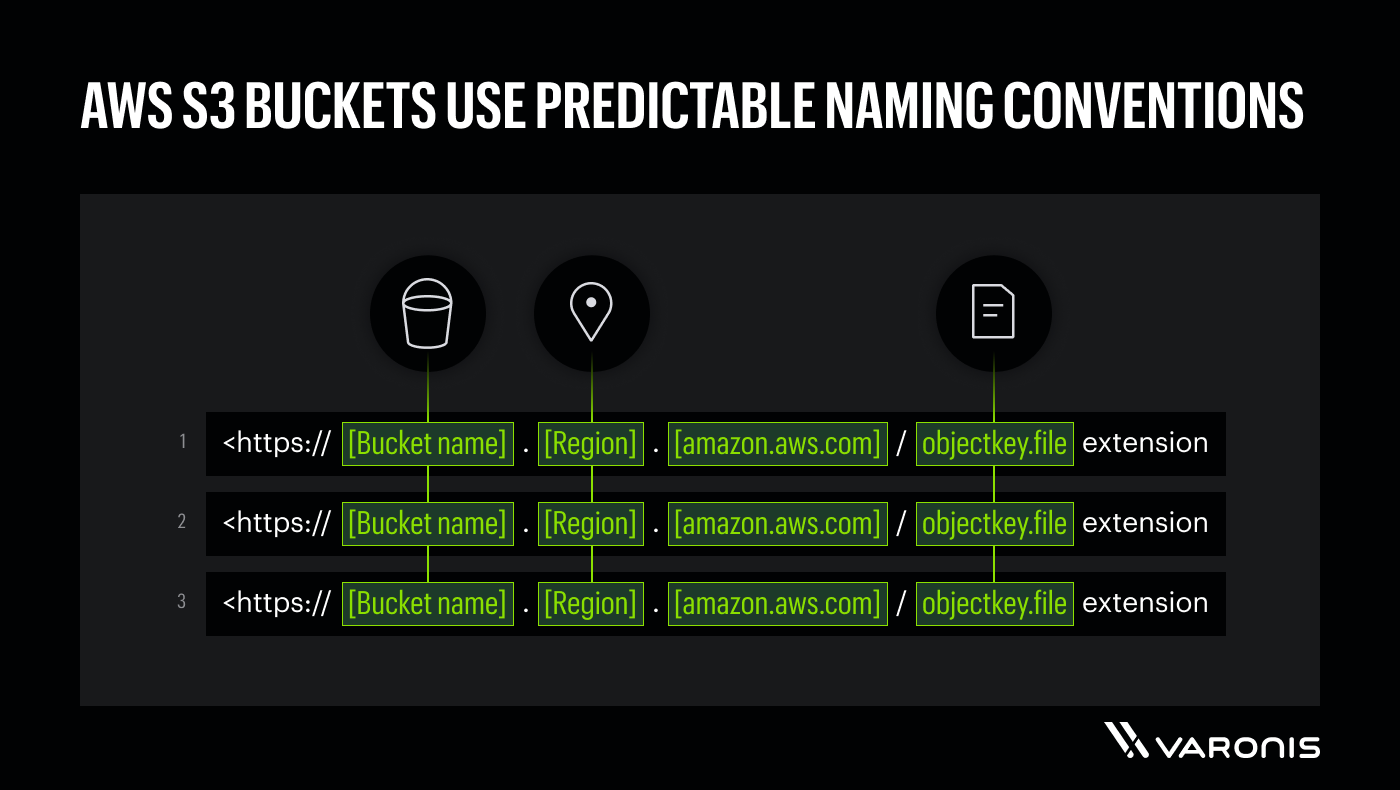
AWS S3 buckets have predictable naming structures that can be exploited by attackers.
Exploiting predictable S3 bucket names can lead to several different attacks. Bad actors can redirect traffic or initiate a denial-of-service (DoS). Moreover, attackers can potentially manipulate cloud formation resources and even create admin accounts.
A highjacked S3 site jeopardizes customer confidence
Varonis recently identified an incident in which a bad actor exploited static S3 buckets and Amazon Route 53 to redirect traffic to a less-than-reputable website. Customers were forcefully redirected, which made it appear as if there had been a hack. This incident had the potential to harm customer confidence and was causing headaches for the security team.
The Varonis Incident Response team diagnosed and helped to remediate the problem. However, S3 bucket namesquatting can easily go unnoticed by many companies, leading to significant issues for customers and even data breaches.
How do you prevent S3 bucket namesquatting?
To prevent S3 bucket namesquatting, make sure that your S3 buckets are locked down. It’s important to understand that the naming conventions can be predicted and to ensure that your S3 buckets are not public. AWS recently updated its documentation to emphasize the importance of customizing S3 bucket names when bootstrapping resources.
“Unlike the other bootstrap resources, Amazon S3 bucket names are global. This means that each bucket name must be unique across all AWS accounts in all AWS Regions within a partition.”
Beyond that, it’s important to identify issues, such as when default bucket names have not been changed on a large scale. AWS allows users to make configurations, and simple misconfigurations or incorrect policies can negatively impact your customers.
If namesquatting is detected, here are some practical steps to take:
- Decommission the domain to prevent further exposure
- Request and confirm that AWS takes down the bucket
- Point DNS records at non-S3 resources until fraudulent DNS records are purged
How Varonis helps prevent S3 bucket namesquatting
When an energy sector company adopted a cloud-first approach, they knew they needed to clean up user permissions and stale data and safeguard its critical data from attacks.
They sought a solution that could secure their cloud data, help them comply with international standards, and detect and mitigate threats in real time, leading them to Varonis.
Read the full case study: How Varonis Helps an Energy Company Safeguard Critical Data in AWS and M365
“S3 buckets are a known target in the hacker world because AWS is so prevalent. S3 buckets are exploited all the time.”
CISO, Energy Sector Company
Varonis provides a comprehensive solution for securing data in AWS. Given the large scale of AWS deployments, misconfigurations are often overlooked. Varonis automates security processes to help teams scale effortlessly.
Varonis automatically discovers and classifies sensitive data across unstructured and structured resources in AWS and flags risk from excessive access and misconfigurations, including potential S3 bucket namesquatting.
Once data risks and misconfigurations are detected, Varonis automatically remediates issues to ensure that your AWS data is secure. For instance, Varonis can automatically apply public access blocks on all S3 buckets containing sensitive data. Additionally, Varonis can help prevent the No. 1 cause of cyberattack — compromised identity — by removing stale users, roles, and access keys, right-sizing access, and alerting you to abnormal behavior.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.







