Several powerful features are rolling out for Microsoft 365 customers that can fly under the radar for CISOs and risk management teams.
One such feature, Organizational Messages, was announced in May 2024 as a public preview. Some may recognize the functionality, as it used to be part of Microsoft Intune in a limited capacity. See a helpful demonstration of the new solution by Microsoft MVP Andy Malone.
What are Microsoft 365 Organizational Messages?
M365 Organizational Messages intend to enhance how IT and security teams communicate with users within the organization outside of old-fashioned email that may be largely ignored or lost within inboxes.
Unlike Microsoft Viva Engage or Teams channels, which tend to be used frequently by human resources departments to deliver important messages, “organizational messages” can pop up directly on the desktop screen for Windows devices, Teams, and more.
Below, you can see the various locations or mechanisms for displaying a message to users.
The various locations an organizational message can be displayed
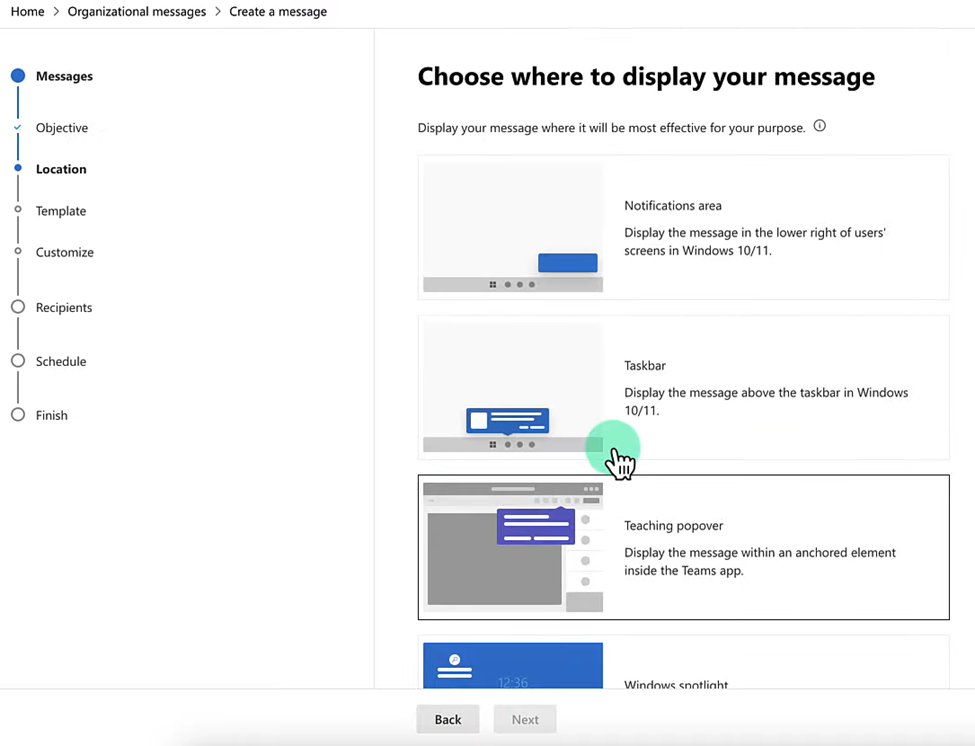
The various locations an organizational message can be displayed
This embedded message can be very effective in notifying users of a recent or upcoming change, prompting them to undergo particular training, or alerting them of an outage.
However, we've found that this solution can also be used for malicious motives.
What can go wrong?
Imagine an administrator’s identity being compromised, a user being given elevated privileges to create an organizational message in the Microsoft 365 admin center, or an admin with appropriate privileges being an insider threat and sending a damaging message company-wide.
All these scenarios could result in a catastrophic incident for organizations if their data and permissions aren't locked down before enabling the feature.
The following image shows how a custom message can be configured to include nefarious content:
- “Your credentials are expiring and must be changed in the next hour. Click here to update your password.”
- “Company XYZ has filed for bankruptcy. All employees will be notified for further instructions and impact.”
- “ABC Application is impacting performance on your device. Please disable by following the linked instructions."
- “Your latest expense report is pending approval. Validate payment details here for final approval.”
Customizing an organizational message in the Microsoft 365 admin center
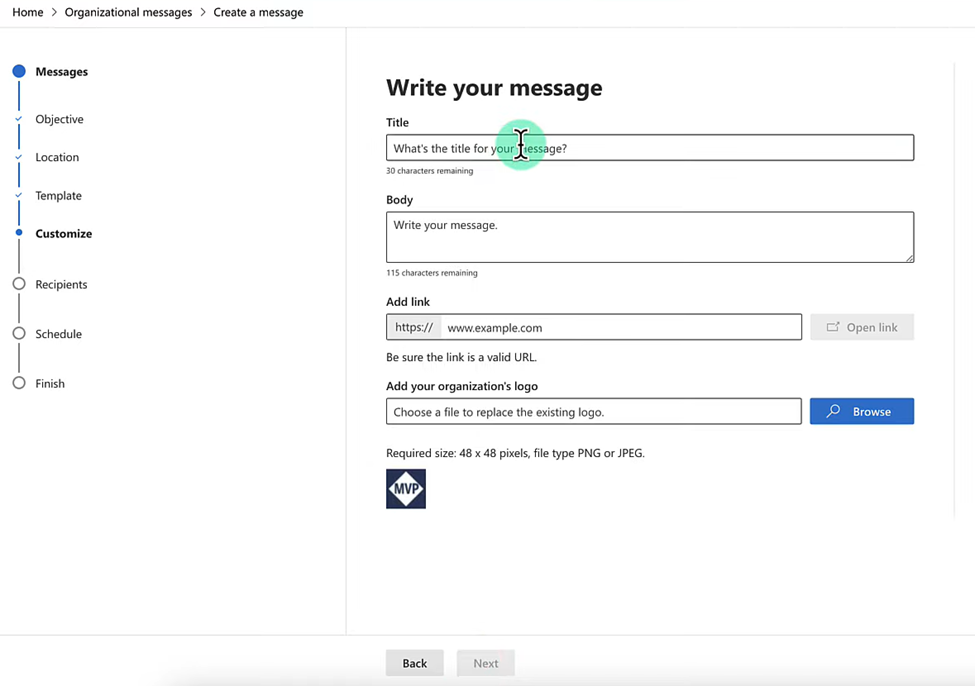
Customizing an organizational message in the Microsoft 365 admin center
Not only can alarming messages cause confusion and turmoil within the business, but the worst-case scenario is when a malicious link is provided, or instructions to run a malicious script or package are given to each user.
The only safeguard against misuse is a default policy requiring the ‘approver’ of an organizational message to be a different user than the ‘writer’ of this message. Regardless, if one identity can be compromised, a second should be fair game to most attackers.
Currently, there is no known feature set to monitor for malicious links or send alerts when organizational messages contain potentially dangerous content.
Mitigate Microsoft 365 risk with Varonis
Following the practices of NIST CSF, it's essential to start with a risk assessment so your organization understands who currently is entitled to write or approve organizational messages. Custom organizational messages can only be authored and approved by users with a Global Administrator, Organizational Messages Writer, and Organizational Messages Approver role.
With Varonis Identity Protection, security teams can accurately understand which users are assigned these roles and consistently monitor events when users are granted one of the roles.
Varonis visibility into relevant Entra ID roles
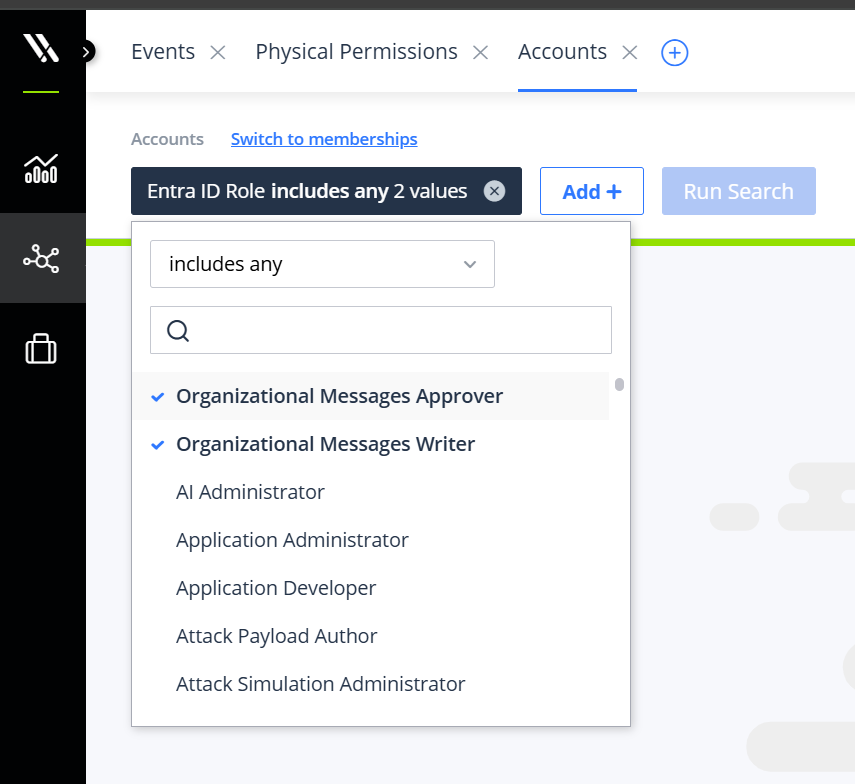
Varonis visibility into relevant Entra ID roles
This is especially important because most default reporting and monitoring is configured on Global Administrators, not these new nuanced "Organizational Messages" roles.
Surfacing key events where relevant roles are added for organizational messages
-1.png)
Surfacing key events where relevant roles are added for organizational messages
We can also go beyond changes to an identity and its entitlements. Varonis provides the full data access picture of a risky identity by actively scanning data access, activity, and permissions. It’s important to also take action when a user authenticates from suspicious locations or performs an event from an unknown device, among other identity signals. Varonis brings identity and data access to the forefront.
Gain visibility and resolution of identity threats with Varonis Identity Protection capabilities
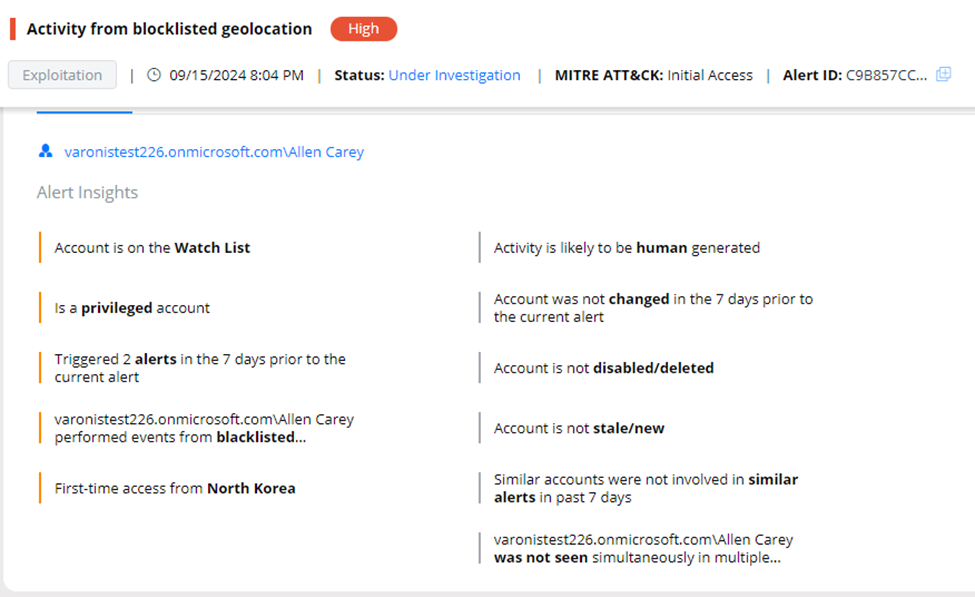
Gain visibility and resolution of identity threats with Varonis Identity Protection capabilities
During an insider risk investigation, breadcrumbs can often be followed to identify if a user is taking measures to damage the organization. Varonis for Microsoft 365 and Insider Risk Management capabilities provide real-time monitoring of file access events, configuration changes, and anomalous behavior.
These variables can be pieced together before an insider threat can exploit a high-impact tool like Microsoft organizational messages for ill intent.
A last line of defense
Without implementing the above solutions or similar from other providers, a bad actor could send out a malicious link through a Microsoft 365 organizational message.
This would go undetected by Microsoft Defender for 365 since the message is not coming through Teams or email via Exchange/Outlook. Thus, one of the last protections in place would be Microsoft Defender SmartScreen, which is only for Edge browsing on Windows endpoints.
Example of Microsoft Defender SmartScreen alerting of a malicious link in Edge
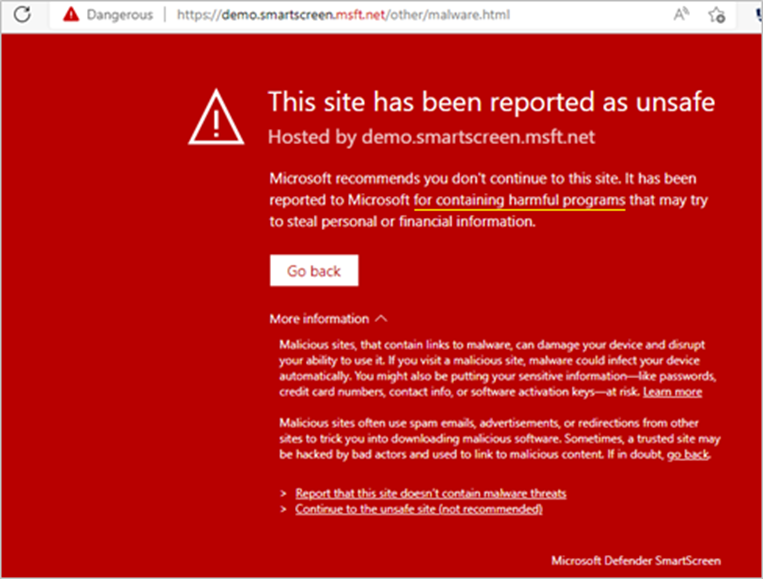
Example of Microsoft Defender SmartScreen alerting of a malicious link in Edge
Assuming that all 1) users are on Windows devices, 2) devices are configured to open new links in Edge, 3) all users have Microsoft Defender for Endpoint Plan 1 or Plan 2, and 4) the site is a known malicious source through Microsoft intelligence — users will be alerted with a red warning page instructing them to turn back. Hopefully, they choose to go back.
Reduce your risk without taking any.
Ready to enable Microsoft Organizational Messages but need to ensure your permissions are in order? Get started with Varonis' free risk assessment.
In less than 24 hours, you’ll have a clear, risk-based view of the data that matters most and a clear path to automated remediation and full access to our cloud-native Data Security Platform during the process.
With a full demo of Varonis, our experts can show you how to identify and fix accounts and configurations that make you vulnerable to password sprays, credential stuffing, and exploitations from compromised identities (like this one).
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.





