Évaluation des risques liés aux données
Cartographiez les risques liés à vos données sensibles et établissez une stratégie de remédiation claire et hiérarchisée grâce à l’évaluation des risques sur les données la plus avancée du secteur.
- En profondeur
- Exploitable
- Gratuit







Collaborez avec le leader de la sécurité des données.
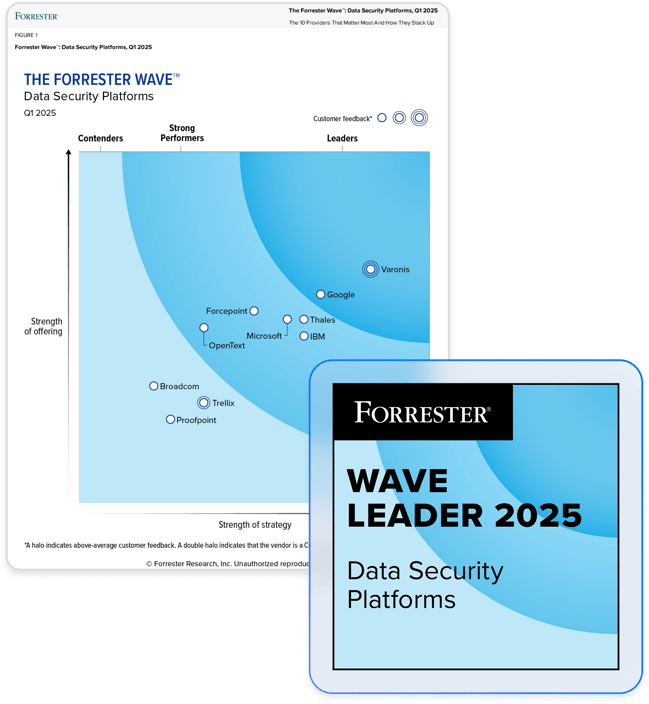
La vérité est toujours bonne à entendre.
Facile à installer
- Cloud-native
- Installation en quelques minutes
- Résultats dans les 24 heures
Complet
- Accès complet à la plateforme
- Analyste de réponse aux incidents dédié
- Rapport de résultats clés
Exploitable
- Analyse approfondie des risques
- Stratégie claire vers la remédiation
- Recommandations exploitables
« J’ai été étonné de la rapidité avec laquelle Varonis a pu classifier les données et détecter leurs expositions potentielles pendant l’évaluation gratuite. »
Michael Smith
RSSI, HKS
« Au cours du processus d’évaluation, nous avons été très surpris de constater que l’ensemble du département pouvait librement accéder à une grande quantité de données contenant des informations sensibles. »
Terrence Slaton
RSSI, gouvernement du comté de Fulton
Principaux risques liés aux données
Mettez en lumière les risques les plus critiques sur vos données avec des détails concrets et exploitables qui vous permettront de prévenir d’éventuelles fuites de données.
Examen complet de la posture de sécurité
Bénéficiez d’une visibilité approfondie sur vos données sensibles et sur les risques associés, quel que soit l’emplacement de vos données les plus critiques, y compris dans le cloud, les applications SaaS et les centres d’hébergement de données.
Détection active des menaces
Au cours de la période d’évaluation, les modèles de menaces basés sur le comportement de Varonis s’entraînent sur des millions d’événements pour apprendre le comportement unique de vos utilisateurs et de vos appareils afin de détecter les comportements anormaux.
Analyse des risques de configuration
Varonis analyse en permanence les configurations des systèmes de vos plateformes Cloud et SaaS afin de déterminer si certains paramètres présentent des risques ou s’ils ne sont pas conformes à l’état souhaité.
Examen des risques liés aux identités
Varonis analyse vos Directory Services cloud et on-premises et détecte les configurations faibles pouvant fournir des voies d’accès aux attaquants au niveau des identités. Cela inclut les erreurs de configuration risquées comme des utilisateurs obsolètes possédant des droits d’administrateur.
Réduisez les risques sans en prendre aucun.
