- Correlate data access with edge telemetry
- Detect suspicious VPN, DNS, and web activity
- Stop brute-force, C2, and data exfiltration
Varonis starts at the heart—watching your data—and fans outward to the network edge. By correlating events at each layer, our threat models give you the best chance at fighting APTs and insider threats.
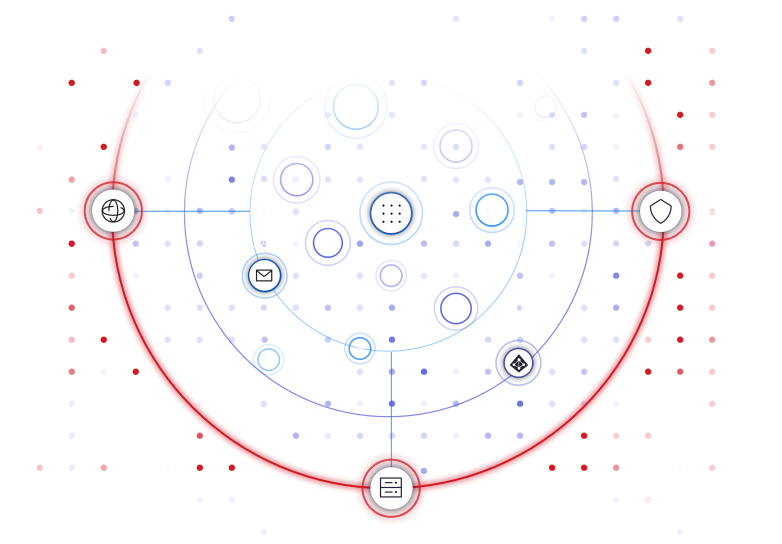
Edge is your canary in the coalmine.
Get real-time awareness of risky configurations and early indicators of compromise. Our threat models continually learn behaviors specific to your organization.

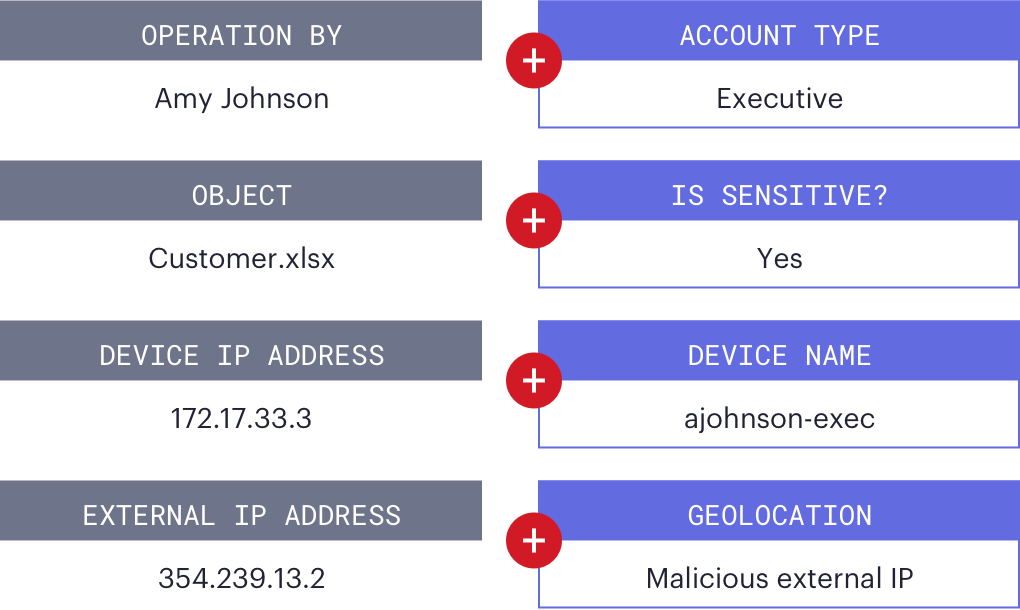
We don’t just copy raw network device logs—we give you clean, human-readable events enriched with valuable context like URL reputation, account type, and data sensitivity.
Trace any incident back to your data.
Filter
See suspicious events at the edge

Isolate
Identify the top-offending user or device

Pivot
Easily answer “what data did they access?”

Filter
See suspicious events at the edge
Isolate
Identify the top-offending user or device
Pivot
Easily answer “what data did they access?”

Varonis Edge was our MVP. Edge directed us to the computers with suspicious DNS requests, correlated them with specific users, and showed us the IPs we needed to block.
Key features
No endpoint agents
Automated responses
Continuous updates
Integrated threat intelligence
Event normalization
SIEM integration
No-cost incident response and forensics team.
