Quick ransomware background
Ransomware is a type of malware that encrypts your data and asks for you to pay a ransom to restore access to your files. Cyber criminals usually request that the ransom be paid in Bitcoins: the #1 cryptocurrency (basically a distributed ledger) which can be used to buy and sell goods. By nature, Bitcoin transactions (e.g. ransom payments) are very difficult to trace.
Historically, most ransomware infections use the attack vector – how they get in – of social engineering (like clickbait from a social media platform – think cute kitty pics on Facebook or Twitter) or email phishing campaigns, which contain attachments or links to a website. The end result is that a malicious payload gets a foothold on a machine inside a corporate network. Unfortunately, all of those next generation perimeter defenses that organizations spend good money on are not that difficult to bypass in order to get inside.
Once inside, most ransomware will scan the internal network to see which servers host file shares, attempts to connect to each share, encrypt its contents, and then demand a ransom be paid to regain access to the now encrypted files. End users can usually access way more data than they should be able to: either through wide open permissions or by accumulating permissions over the course of their employment at their company. Think for a minute just often you’ve stumbled across a folder or files which you know you shouldn’t be able to access. Access controls are out of control. In this case, IT is typically blind because of the sheer complexity of file system permissions.
Good to know, but what was different last week?
Without going too much into the technical details, I can tell you that the code behind the biggest ransomware outbreak in history isn’t actually all that special. It’s a type of cryptoworm: a self-propagating malicious form of malware. That means that once it gets a foothold, it can spread autonomously without the need for someone to remote control it.
Normally, ransomware targets unstructured data hosted on file shares – this ransomware, however, did not discriminate.
In April, several hacking tools created by the NSA were leaked online. These hacking tools exploit vulnerabilities in hardware and software so that they can hack into or move laterally around a computer network.
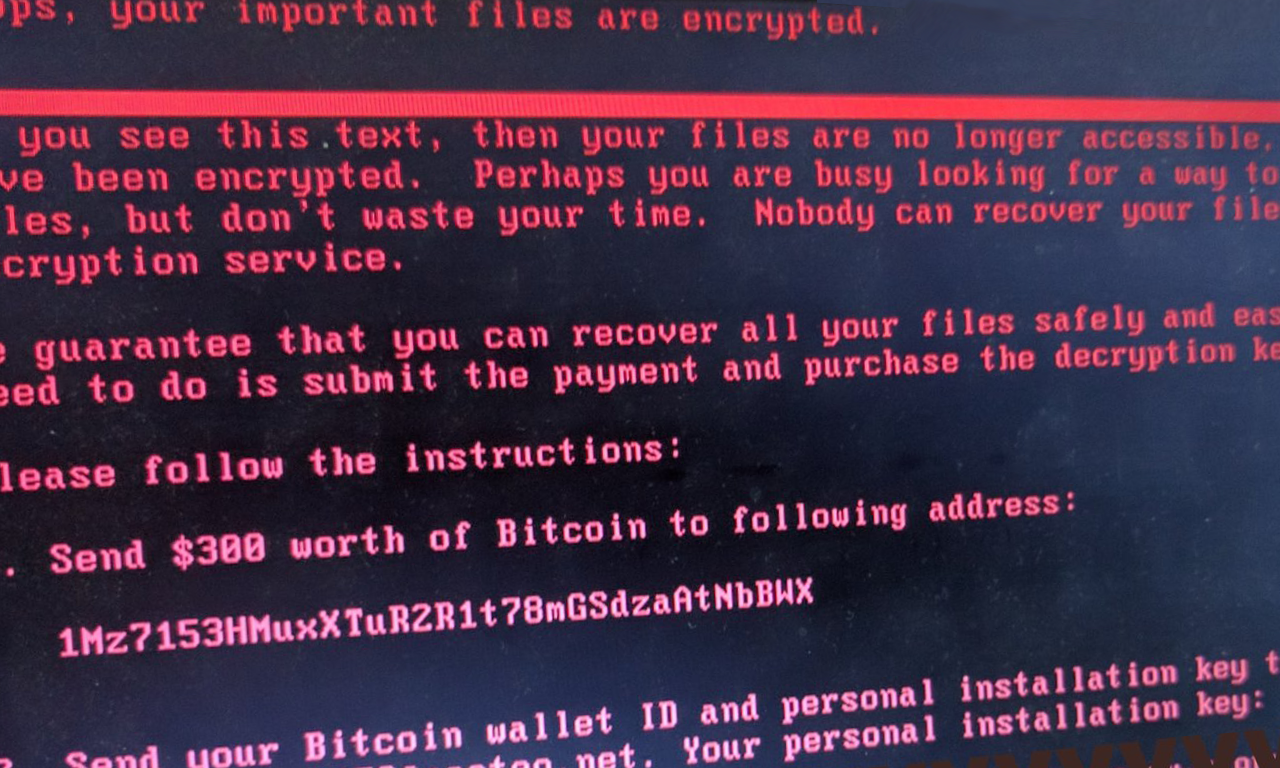
WannaCry ransomware (also known as WCry / WanaCry / WannaCrypt0r / WannaCrypt / Wana Decrypt0r) – the type responsible for last Friday’s attack – went a few steps further: once it got onto even a single machine within a corporate network, it did the following:
- Looped through any open RDP (Remote Desktop) sessions, to encrypt data on the remote machine
- Sought out any vulnerable* Windows machines – endpoints (laptops/desktops/tablets) and servers using Microsoft vulnerabilities
- Used the traditional approach of going after file shares directly from the endpoint
*The particular vulnerability that made the difference last week was in the Microsoft SMBv1 file sharing protocol, which was used to hop from machine to machine encrypting data – like a spider web effect. Most internal servers are separated on internal networks so that end users can’t access them. The cryptoworm would need to hit just one internal server (e.g. a file server) and from there it would target whatever vulnerable servers that file server can access. This allowed it to quickly traverse entire networks, effectively crippling many of them. Like many cryptoworms, it’s self-propagating and so replicates itself and searches out to other vulnerable hosts/computer networks worldwide.
The truth is that the worldwide infection could have been much worse if not for the quick thinking of a security researcher. @MalwareTechBlog spotted that the malware code was connecting out to a nonsensical domain, which was not registered. This call out was hard-coded in case the creator wanted to stop it and likely also to help avoid IDS/IPS sandboxing techniques. If the request comes back showing that the domain is live, the “kill switch” kicks in to stop the malicious part of the code from executing – effectively stopping the malware in its tracks. @MalwareTechBlog, acting on a hunch, registered the domain name and was immediately registering thousands of connections every second. The result was that he stopped what could have been a much wider spread infection.
The bad news is that new versions of the code are already in development: https://www.bleepingcomputer.com/news/security/with-the-success-of-wannacry-imitations-are-quickly-in-development/
Lessons Learned
Microsoft released a patch (software code update to fix vulnerabilities) for this particular SMBv1 vulnerability back in March. The sad truth of the matter is that proper vulnerability patch management processes would mean that most organizations would not have been so badly affected.
That’s not to say that vulnerability patch management processes are enough coverage for ransomware. Nor are backups, since some ransomware will hide in your backups so that after you restore files they will simply attack again.
There is no one stop shop for stopping ransomware infections or any cyber security threat for that matter. Security is all about risk reduction – and requires a layered approach with controls in place at each layer while leveraging solutions to automate processes wherever possible. If any organization says that they’re 100% safe from cyber-attacks, then they’re either delusional or telling you porky pies!
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.