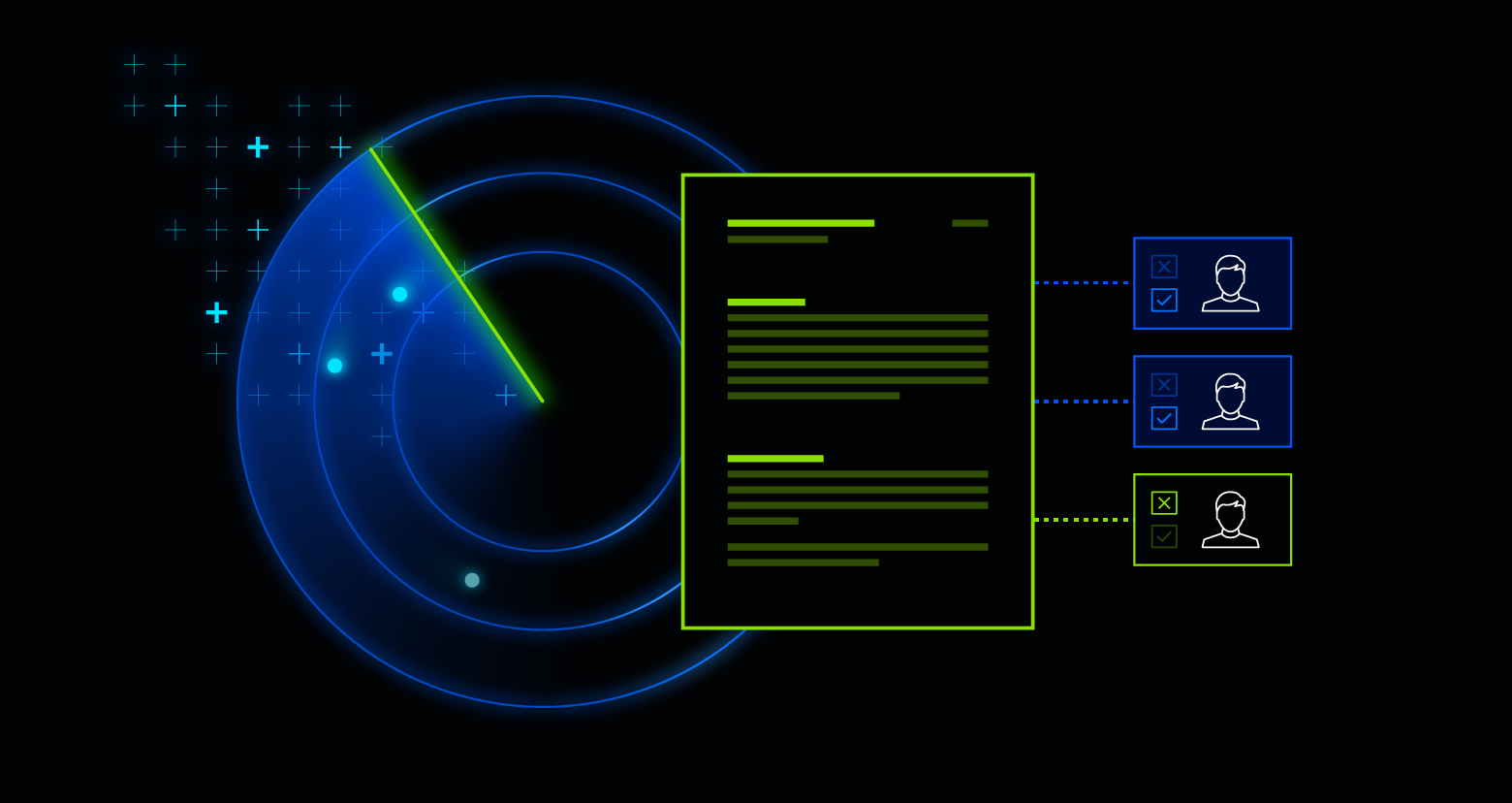
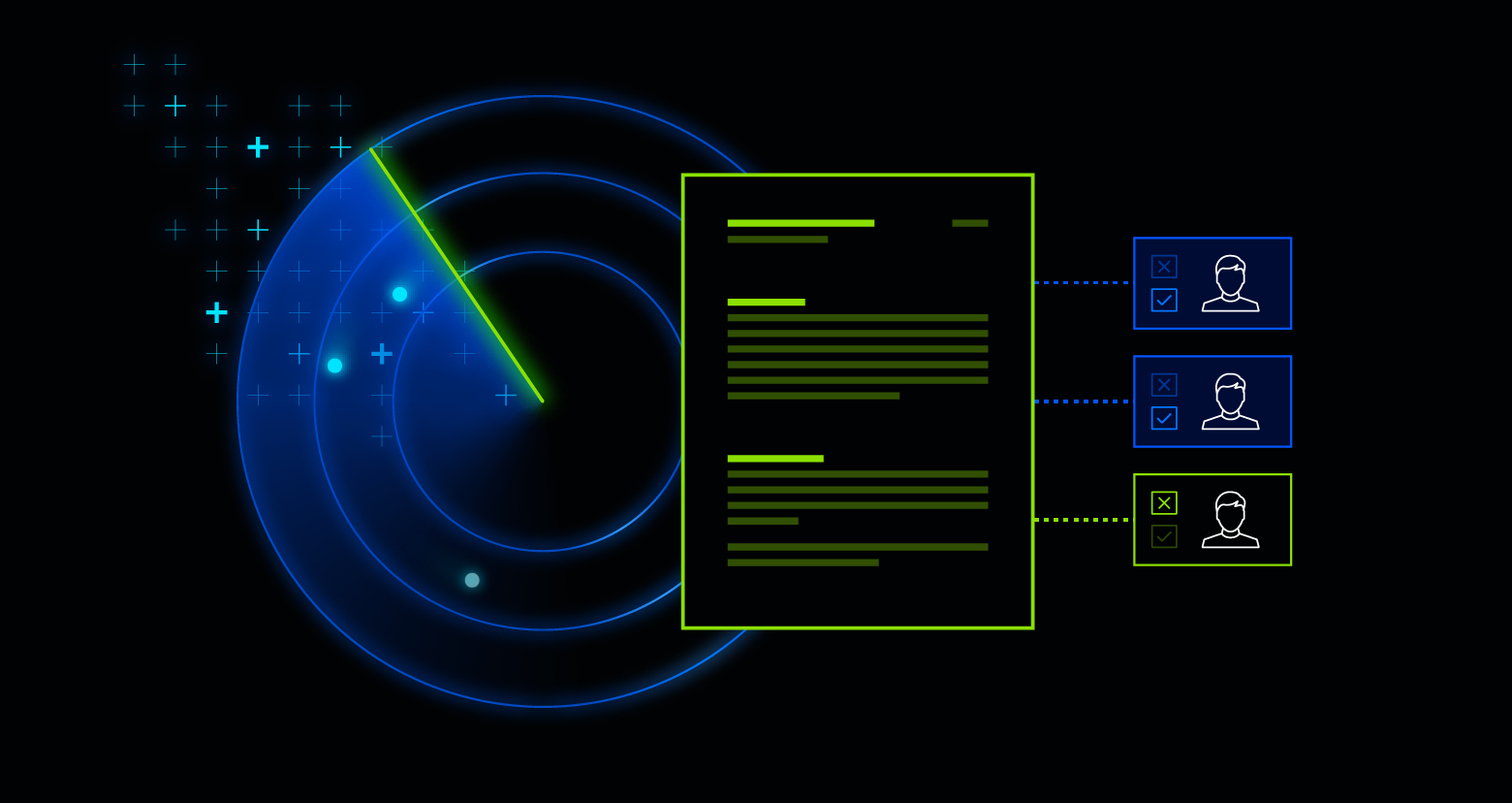
As the name suggests, data loss prevention (DLP) is a framework designed to provide visibility into data use across your organization so that you can implement policies to safeguard against data theft, loss, or misuse. DLP capabilities include classification, encryption, surveillance, and policy enforcement to help prevent data loss.
Traditionally, DLP was focused on on-premises workloads. However, the increase in cloud and hybrid environments has complicated organizations' DLP efforts.
Tried-and-true techniques for on-premises DLP are often unsuitable for cloud-based and hybrid settings. As such, DLP solutions are adapting to address the changing requirements of today's organizations.
In this blog, we’ll explore:
- How DLP works
- The importance of DLP
- The challenges of applying traditional DLP to cloud and hybrid environments
- What sets Varonis’ DLP capabilities apart
How does DLP work?
DLP solutions discover and analyze data to identify sensitivity, monitor activity, and ensure compliance with set policies. If a policy is violated, DLP helps take actions like blocking the activity, encrypting the content, logging the incident, and sending an alert.
Discover and classify data.
A successful DLP must first understand the data it needs to protect, beginning with:
- Discovering sensitive data — where does your sensitive data reside?
- Classifying the data — is it PII, PCI, IP, or HIPAA data?
- Mapping the data to permissions — who can access the data?
- Creating a set of labels that map the data to DLP policies and help guide usage, such as “public,” “internal,” “confidential,” and “restricted.”
Analyze permissions.
With your data classified and your permissions mapped, your DLP solution should analyze the data and its permissions in the context of your organization’s policies and relevant regulations. For example:
- PII, HIPAA, SOX, and IP data will need more stringent protections, like limited sharing permissions and encryption.
- Are there high-risk permissions, like global access to data containing PII? If so, over-permissive access will need to be corrected.
Create your DLP policies.
Next, you’ll need to create your organization’s DLP policies. Certain data within your company is regulated, and policies should ensure compliance with those regulations.
Similarly, critical business data will require tailored DLP policies that align with your organization’s objectives. You must also understand how to enforce business rules and comply with policies — for example, having the ability to return or delete all personal data after the end of services to comply with GDPR.
Monitor data activity.
Finally, your DLP solution monitors data activity. If a policy is triggered — a user tries to copy a sensitive item, for instance — the DLP can take any number of automated actions, including:
- Surfacing the relevant policy information to inform the user
- Blocking the action to prevent theft or loss
- Encrypting the data to prevent the user from accessing or reading the data
- Sending an alert to inform your security team
- Logging the incident for investigation
- Restoring a backup of the lost data to prevent business interruption
Watch our “Catching Success with Cloud DLP” discussion to learn more about data security.
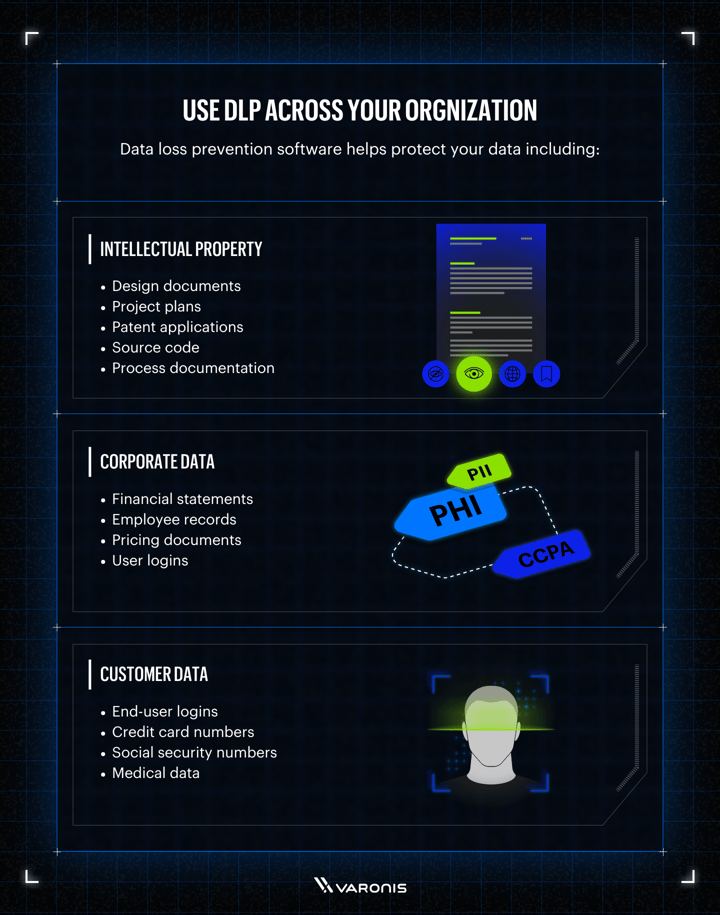
The importance of data loss prevention
Data loss prevention software helps protect your data including:
Intellectual property
- Design documents
- Project plans
- Patent applications
- Source code
- Process documentation
Corporate Data
- Financial statements
- Employee records
- Pricing documents
- User logins
Customer data
- End-user logins
- Credit card number
- Social security numbers
- Medical data
DLP solutions help meet regulatory requirements and prevent data loss that could negatively impact the business. To understand why DLP is essential, let’s imagine a few scenarios:
- A laptop with a spreadsheet of unencrypted HR data is stolen, potentially exposing everything from social security numbers to addresses
- A former employee leaves to a competitor with sensitive customer information
- An unapproved third-party application is leaking sensitive IP outside of the organization
Each of these instances would be a nightmare for any company, potentially resulting in regulatory fines, lawsuits, or the loss of valuable company information that could hurt revenue. Numerous scenarios like these can happen anytime, making DLP an important competency for every organization.
The challenges with DLP
Traditional on-premises DLP solutions struggle to remain viable in cloud and hybrid environments; these tools typically focus on a limited number of egress points, like email.
Cloud environments, on the other hand, present numerous ways for data to leave or leak from an environment. SaaS applications and collaborative workspaces — including Microsoft 365, Salesforce, and Google Workspaces — make moving and sharing data easy. Simple misconfigurations like an unsecured database or an abandoned snapshot can also lead to data loss. There are simply many more ways for data loss to occur in the cloud.
Data discovery is also much more challenging in cloud and hybrid environments. Most enterprises use multiple clouds, and large, sometimes outsourced, dev teams constantly spin up new resources, making it extremely challenging to know what data needs protection.
Finally, many DLP efforts fail because organizations equate DLP with data security. DLP, on its own, however, does not detect or respond to threats and doesn’t remediate issues like overexposure, which is critical for securing data in cloud environments.
What Sets Varonis' DLP Solutions Apart

Varonis takes a holistic approach to data security, combining DLP capabilities with data classification, DSPM, and data-centric threat detection. By doing so, we provide the functionality you need to protect your most sensitive data and support downstream DLP efforts wherever your data resides — whether in the cloud, a hybrid environment, or on-premises.
Varonis automatically discovers and classifies sensitive data at rest, prevents exposure, monitors data activity, and stops data exfiltration through:
- Deep visibility: Varonis discovers and classifies your sensitive data wherever it resides and collects more information on the data than any other solution, including sensitivity, permissions, and activity. This creates the foundation for successful DLP.
- Automated remediation: Varonis can automatically fix the underlying issues that lead to data loss and theft, including revoking excessive access and fixing labels.
- Threat detection: Varonis continually monitors for abnormal behavior and threats that could lead to data loss, using automated threat models and a dedicated team to spot abnormal threats, like ransomware.
While legacy DLP relies on endpoint and network-based agents to detect and stop sensitive data loss, Varonis protects data where it lives with API-based analysis and monitoring.
Data Loss Prevention FAQ
Below are some commonly asked questions about data loss prevention.
Q: What is the difference between DLP and “DLP Endpoint?”
A: “DLP Endpoint” means that an agent is running on a computer and managing some aspects of DLP for that computer.
Q: Are there any known security limitations with DLP?
A: DLP only tracks data movement and doesn’t include context. For example, if a user moves a large volume of data, it triggers a DLP alert. Traditional DLP isn’t sophisticated enough to know that the user is a regular user of this data and that their activity is normal.
Traditional DLP solutions also struggle in cloud environments, where there are numerous potential points of egress and data is constantly cloned and created.
Q: When our users create data, the DLP prompts them to classify it; isn’t that good enough?
A: Do you trust your users to know all the possible classification implications of the data they create? It’s best to have the file scanned by an engine with all the rules enabled.
Q: Is Varonis a DLP?
A: Varonis offers next-gen DLP capabilities as part of our cloud-native Data Security Platform, such as data monitoring and alerting on abnormal behaviors, classification, archival, and
quarantine.
Q: What types of data sources do DLPs help secure?
Every organization will likely have sensitive or valuable data specific to their business. With that said, below is a list of data types typically covered by DLP solutions:
- Corporate data
- Credit card numbers
- Customer data
- Design documents
- Employee records
- End-user logins
- Financial records and statements
- Intellectual property
- Medical data
- Patent applications
- Pricing documents
- Process documentation
- Project plans
- Social security numbers
- Source code
- User logins
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.