Cyber espionage is the unauthorized use of computer networks and other resources to access or transfer secret, classified, or sensitive information. It’s seen as a growing problem for governments, corporations, and individuals. In this post, we’ll explore the ins and outs of cyber espionage, learn how cyberspies carry out their sophisticated operations and dive into some steps you can take to protect your secret data.
- What is cyber espionage?
- Which factors define a cyber espionage attack?
- What makes a CyberSpy?
- Who’s at risk for cyber espionage?
- Cyber espionage attacker tactics
- How to prevent cyber espionage
- Closing thoughts
What is cyber espionage?
The word espionage for many may conjure up images of globe-trotting secret agents, smoke-filled backrooms filled with mysterious figures, and satellites peering into forbidden spaces from thousands of miles above. In truth, though, today’s intelligence-gathering operations often take place in the digital realm. It may not be as sexy as James Bond outwitting an arms dealer at the baccarat table, but cyber espionage is making a profound global impact politically, culturally, and economically.
Once a novelty, espionage operations in cyberspace are now commonplace, but with very real-world implications. State-sponsored hackers have used digital campaigns to upend the geopolitical order. The digital theft of intellectual property and trade secrets has been called “the greatest transfer of wealth in U.S. history.” And for repressive regimes, social media, smartphones, and search histories have become tools for monitoring and suppressing dissent.
Get the Free Essential Guide to US Data Protection Compliance and Regulations
Which factors define a cyber espionage attack?
Nailing down a precise cyber espionage definition is difficult, as it's an inherently secretive and wide-ranging set of potential activities. It can be carried out at a small or large scale, vary in sophistication, and target anything from a single user to an entire region. However, there are some consistent factors that will often serve to differentiate cyber espionage from other types of cyberattacks:
- An emphasis on covert action: In contrast with other types of attacks like ransomware, cyber espionage generally seeks to remain undetectable throughout the entire lifecycle of the attack. Perpetrators may go to great lengths to conceal their actions, their motives, and their identities. The use of zero-day exploits and custom malware that can’t be identified through signature-based antivirus is common.
- Access or theft of sensitive information or intellectual property: Many types of cybercrime target customer data, financial information such as account numbers, or the digital infrastructure that organizations use to carry out day-to-day operations. Cyber espionage attacks tend to have a different focus, going after the closely guarded secrets of rival nations, intellectual property and advanced technology of corporate competitors, or private communications of dissidents or political adversaries. Interestingly, the type of information targeted in cyber espionage is often not subject to data breach reporting and notification laws, which could mean that such attacks could be underreported in cybersecurity statistics.
- A specific target and/or motive: Many cyberattacks are indiscriminate, victimizing any individual or group unlucky enough to download the wrong app, click the wrong link, or otherwise fall into the crosshairs of the attacker. Cyber espionage targets can vary from individuals to entire populations or governments, but the threat actor almost always has a target defined before beginning a campaign. This is not often a crime of opportunity.
What makes a CyberSpy?
Spycraft used to be an expensive game reserved for the wealthiest of nations. Not all of us can afford our own Quartermaster, after all. But times have changed since the days of Ian Fleming and Gary Powers, and the now ubiquitous use of computer networks — even for highly classified documents and communications — has dramatically lowered the bar to entry for countries, groups, and even individuals to set up their own digital sleuthing operations.
Establishing a cyberespionage program doesn’t require highly trained secret agents, stealthy spy planes, or top-secret eavesdropping equipment. Small or large groups can easily carry out clandestine missions on a global scale using off-the-shelf computer hardware, a cheap network connection, and some programming know-how. While all of the superpowers that long dominated the shadowy cloak-and-dagger world have their own cyber espionage initiatives, the increased accessibility has opened the door to smaller nations, organized crime groups, and even resourceful individuals. For the right price, you can even hire a freelance cyber-espionage group and name your own target.
Who’s at risk for cyber espionage?
Spy vs Spy is so 1961. Espionage and intelligence gathering in the modern era is asymmetrical and non-linear. Nation-states spy on individuals, individuals compromise multinational conglomerates, and even close allies spy on each other. Companies have been caught spying on their own board members, intelligence analysts have abused their positions to snoop on love interests, and data harvesting firms have amassed troves of information on consumers in order to build comprehensive marketing profiles.
Even if we’re not a direct target, the information and data we generate every day can be of interest to adversaries. Something as outwardly innocuous as a fitness tracking app can reveal hidden military installations. All of us — individually and as part of organizations — generate a wealth of digital footprints that make us a potential cyberespionage target.
That’s not to say that certain organizations and individuals aren’t at heightened risk, however. Government and military entities are frequent targets, as are defense contractors, technology companies, and biotech and pharmaceutical companies. Internationally, cyber espionage targets have included human rights activists, political dissidents, and journalists.
Cyber espionage attacker tactics
Since cyber espionage is by its very nature a secretive activity, it's difficult to say with any certainty exactly what tactics are employed and at what scale. What we do know is based on cyber-espionage cases that have been publicly disclosed in the past. Many of the following tactics have been observed, often used in conjunction with each other.
Social engineering
According to Verizon’s 2020 Cyber Espionage report, a deeper break-out of the espionage category in the company’s annual Data Breach Investigations Report (DBIR), social engineering is a go-to tactic for cyberspies. Over 80% of such attacks identified in 2020 leveraged some variety of phishing, for example. Social engineering is highly attractive in a cyber espionage context because it's inexpensive, requires relatively little sophistication on the part of an attacker, and is often both highly effective and difficult to track or attribute.
Real-World Examples: Perhaps the most widely reported cyber-espionage attack so far, the unauthorized access and subsequent leaks of thousands of emails linked to Hillary Clinton’s 2016 Presidential Campaign, began with a simple phishing email. Clinton campaign manager John Podesta received what looked like a security alert from Google stating that someone had logged into his account, and he should change his password immediately:
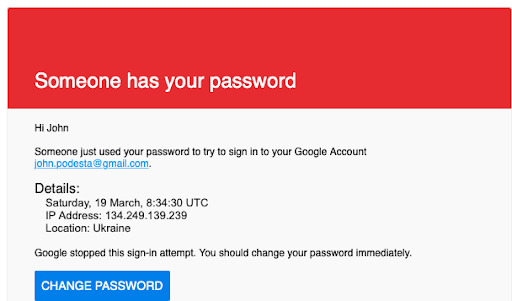
The alert turned out to be phony, and the change password link in the email led to a fake Gmail login page built for the purpose of harvesting credentials. While Podesta thought he was changing his password, he was actually giving it to the attackers. The attackers then used it to log in to the real Gmail and download over 20,000 emails.
Supply chain attacks
Supply chain attacks are becoming an increasingly favored tool of sophisticated cyberespionage groups. In this type of attack, a threat actor will seek to compromise a trusted vendor, partner, or supplier of a target organization. Often, this is accomplished by sneaking backdoor code into a product or service that is already used by the target. This is a highly effective means to bypass even advanced cyber defenses and can be a very difficult attack to detect.
Real-World Examples: In late 2020, news broke of the extraordinary SUNBURST cyber espionage campaign, in which threat actors believed to have ties to the Russian government compromised components in a legitimate network monitoring tool called SolarWinds Orion. By targeting SolarWinds, a supplier to dozens of government organizations as well as most of the Fortune 500, the threat actors were able to gain covert access to sensitive networks within the US Departments of State, Commerce, Homeland Security, Energy, and the Treasury, as well as thousands of others. Other supply chain attacks have leveraged compromised cloud service providers, digital certificate authorities, wireless routers, and accounting software.
Watering hole attacks
In a watering hole attack, the threat actor will compromise a site or service known to be frequented by the target, and then surreptitiously add malware to the site with the hope of compromising the ultimate target. For example, if the threat actor were after a large oil and gas company, they may seek to embed malicious code onto the website of an oil and gas trade publication. In many cases, a watering hole attack is paired with a zero-day exploit cracking open publicly unknown vulnerabilities in a particular browser or operating system. Attackers may also use a bit of social engineering, presenting a fake software update or other prompts to the victim. The result is that a target may visit a website and unknowingly download specially crafted and highly capable malware that’s very unlikely to be caught by anti-virus or other security software.
Real-World Examples: A threat actor known as Evil Eye has been observed using watering hole attacks in several campaigns targeting Uyghurs, an ethnic and religious minority hailing from a region in Northwestern China. Past attacks have victimized the websites of respected international institutions, religious and charity organizations in Asia, and even the US Department of Labor.
Fake or trojan apps
What better way to conduct a cyber espionage campaign than lure targets into bugging their own devices for you? This tactic has been widely used by a variety of threat actors. The attacker will create either a fake app or even embed a backdoor within an otherwise functional program. The target is then convinced to download the app, often through a social engineering campaign. Such rogue apps are often found on third-party app stores, but in some cases have been managed to sneak past the review process required to appear in official app stores. On the desktop side, pirated versions of expensive software like Adobe Photoshop have long contained hidden trojans and other malware.
Real-World Examples: Along with dozens of other types of scams, the global coronavirus pandemic has brought with it a bevy of fake COVID-19-themed apps. Some have been weaponized to steal banking information or capture messages from “secure” messaging apps like Telegram. Another bogus app targeting users in Libya had the ability to spy on users through the phone’s microphone and camera. Other campaigns have masqueraded as popular apps like Netflix, Evernote, Spotify, and even PornHub.
Catfishing
While they could be classified as a type of social engineering attack, catfishing scams have been used frequently enough in cyber espionage campaigns that they deserve their own mention. Catfishing involves the creation of a fake identity — a tactic perhaps as old as espionage itself. Social media platforms and the instant availability of billions of photographs have made this a fairly straightforward process. Some threat actors have been known to build a virtual relationship with their targets for months, often posing as an attractive member of the opposite sex, a professional recruiter in a desirable industry, or a journalist.
Real-World Examples: Due to the low cost and technical complexity required, catfishing has been employed by a variety of threat actors that may lack a top-tier cyber espionage program. Groups with ties to Iran have used the technique to target western defense contractors, Hamas used the technique against Israel Defense Force (IDF) troops, and hackers aligned with the Bashar Al-Assad regime in Syria catfished rebels during the country’s civil war. Chinese spy agencies have also been accused of using the technique to recruit human intelligence sources through services like LinkedIn.
Insider attacks
An insider attack is perhaps the nightmare scenario when it comes to cyber espionage. Some of the most high-profile intelligence failures in the western world, from Kim Philby at the height of the cold war to Edward Snowden in the modern era, have their roots in this type of attack. Digital technology and sloppy access control amplify the inherent risks, potentially giving single individual access to wide swaths of an organization’s sensitive data. While there’s always been some risk of highly trusted individuals going rogue, the potency of an insider attack in the digital age is often amplified by poor access control, lax monitoring, and general organizational apathy towards information security. Not all insider threats are born of malicious intent — a careless or unwitting employee can be the source
Real-World Examples: The Edward Snowden leaks are perhaps the quintessential insider attack story. As a lowly systems administrator that wasn’t even directly employed by the NSA, the then 29-year-old managed to dramatically alter the geopolitical landscape and inspire widespread contemporary debate over privacy, security, and ethics. In the corporate world, companies from Gillette to General Electric have fallen victim to insider cyber espionage attacks.
How to prevent cyber espionage
Routing out cyberspies is one of the most difficult challenges for those tasked with safeguarding attractive targets like government entities, defense contractors, and research institutions. Cyber espionage attacks are often well-funded, highly sophisticated, and incredibly silent on the network. The Verizon Cyber Espionage Report found many cyberespionage examples that compromised their targets in just minutes or even seconds. Victim organizations often take months or years to discover the attack. While some of the general cyber hygiene practices like keeping software up-to-date are helpful, there are some special considerations that go into mitigating the unique risk of cyber espionage:
Look at behavior, action, and anomalies
The cyberespionage tactics we explored earlier are favored by advanced threat actors for a reason. Social engineering, zero-day exploits, and supply chain attacks are all incredibly effective at bypassing traditional defenses like firewalls and signature-based antivirus products. Top cyberspies go to great lengths to avoid detection, using encryption, advanced programming techniques, and other forms of subterfuge to remain hidden for long periods of time. State-sponsored hackers have the resources and technical know-how to invent entirely new types of attacks that no security product has ever seen. Anomalies from a known baseline behavior are sometimes the only clue left from particularly sophisticated cyber espionage attacks.
User and entity behavior analytics (UEBA) solutions like Varonis DatAlert are uniquely suited to spot signs of digital espionage and data theft because they don’t rely on signatures built from previous attacks. Instead, DatAlert uses behavior-based models that learn what’s normal for every user and device and detect potential threats through suspicious or unusual activity. Varonis Edge expands the detection window by adding in VPN, DNS, and web proxy telemetry in order to detect threats such as APT intrusions or data exfiltration attempts.
Utilize strong unique passwords and multi-factor authentication
Credential theft lends itself well to cyber-espionage operations because it often raises few alarms. There was no immediate cause for concern when hackers logged into John Podesta’s Gmail account in 2016 because the hackers had Podesta’s actual username and password. The credentials were authentic, so Google allowed the login attempt. Such cases illustrate the importance of good password practices and the use of Multi-Factor Authentication (MFA). For organizations with sensitive or confidential data, password reuse across multiple sites should be forbidden, and difficult-to-crack passwords are required.
Password lockout policies and account monitoring can foil some of the more rudimentary cyber espionage attempts. Lockout policies will restrict an account after a defined number of failed login attempts within a given period. Account monitoring can spot signs of both failed and successful attacks and can be critical to piecing together an attacker’s moves after the initial compromise.
Access control and the principle of least privilege
Instituting something called the principle of least privilege can also be very effective in thwarting espionage campaigns and data theft. The principle of least privilege dictates that users should have the lowest level of access to resources possible while still being able to carry out their responsibilities within the organization. Picture a marketing employee working for a large beverage company. They should obviously have access to the company’s marketing information, but the recipes, manufacturing processes, and other intellectual property should be strictly off-limits.
Most organizations don’t actually have a clear picture of who can access what on their networks. This lack of visibility, coupled with how time-consuming and disruptive making access changes can be, makes it incredibly difficult to implement effective access control. Varonis can automatically map out the relationships between users and data, show you where sensitive data is concentrated, and automatically remediate overexposure — getting you to least privilege without human intervention. In addition to controlling access to data, the use of administrator accounts should be highly regulated and limited only to situations where required.
Educate your employees and build a culture of security
Technical controls can only do so much to thwart cyber espionage attacks. A comprehensive cybersecurity program has to include a human element in order to be effective. Good security awareness training is often the most effective defense against social engineering attacks. Teaching employees how to spot signs of phishing, pretexting, and catfishing can squash opportunities for espionage agents to gain an initial foothold.
Organizational culture can play a huge role, too. In its Insider Threat Mitigation Guide, the US Cybersecurity and Infrastructure Security Agency (CISA) stresses the importance of educating and engaging employees rather than taking a restrictive and punitive approach. Getting buy-in from key stakeholders, including top executives, is crucial to building a security-aware culture within your organization.
Implement zero-trust
One of the most high-profile cyber-espionage cases of the last several decades, the 2009 Operation Aurora attacks targeting the “crown jewels” of over 30 technology and defense companies, led Google to completely reimagine the way a large enterprise thinks about cybersecurity. The resulting BeyondCorp framework was an early implementation of a new approach called “zero-trust”. In the zero-trust model, every device and user inside an organization is considered potentially compromised by adversaries until proven otherwise. The framework stresses flexible and granular segmentation and authentication.
Zero-trust has been criticized by some as a marketing avenue for security vendors. However, moving towards a zero-trust framework was identified as a priority for U.S. federal agencies in response to the SolarWinds/SUNBURST campaign. Other big names backing the idea include Microsoft, Cisco Systems, and the National Security Agency (NSA).
Closing thoughts
With new attacks challenging the limits of what we thought possible, organizations of all types and sizes have to assume they’ll be cyber-espionage targets at some point. Products like Varonis DatAdvantage and DatAlert can be powerful tools in your counterespionage war chest. We may not all have 007’s arsenal at our disposal, but each of us can take steps to avoid getting snared in the global spy game!
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.