Varonis Threat Labs found an easily exploitable UI bug (CVE-2023-28299) in Microsoft Visual Studio extension installer that allows an attacker to spoof an extension signature and effectively impersonate any publisher. Microsoft issued a patch for CVE-2023-28299 on April 11, 2023.
Unpatched systems remain vulnerable to threat actors issuing targeted malicious extensions to compromise systems.
Why is this important?
Visual Studio is the second most popular IDE on the market, with over thirty thousand customers and a 26% market share.
What separates Visual Studio from its competitors are the hundreds of extensions that allow users to do anything from integrating GitHub and SQL servers to simple productivity tools like spell checks and code snipping.
The most popular extensions routinely have millions of downloads. With the UI bug found by Varonis Threat Labs, (CVE-2023-28299), a threat actor could impersonate a popular publisher and issue a malicious extension to compromise a targeted system. Malicious extensions have been used to steal sensitive information, silently access and change code, or take full control of a system.
The bug
For security reasons, Visual Studio does not allow newline characters inside an extension's name, and it does so by preventing the user from entering information in the "Product Name" extension property.
This restriction can easily be bypassed by opening the VSIX as a ZIP file and manually adding newline characters to the tag <DisplayName> under the file: "extension.vsixmanifest".
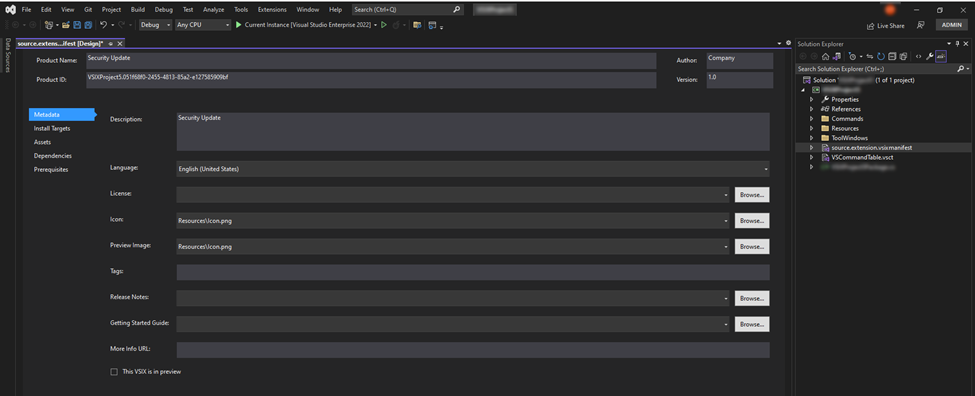
Creating a new C# project and editing its property
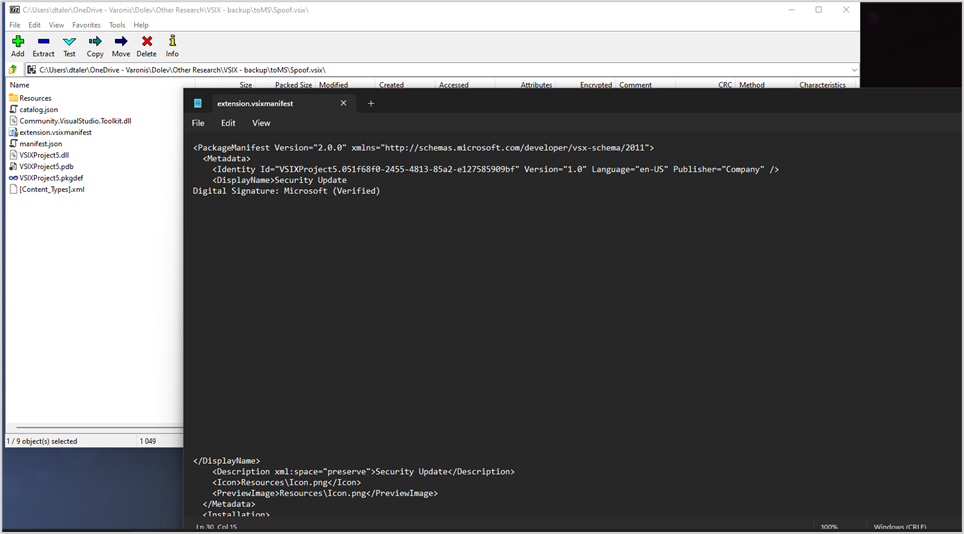
Editing in 7zip
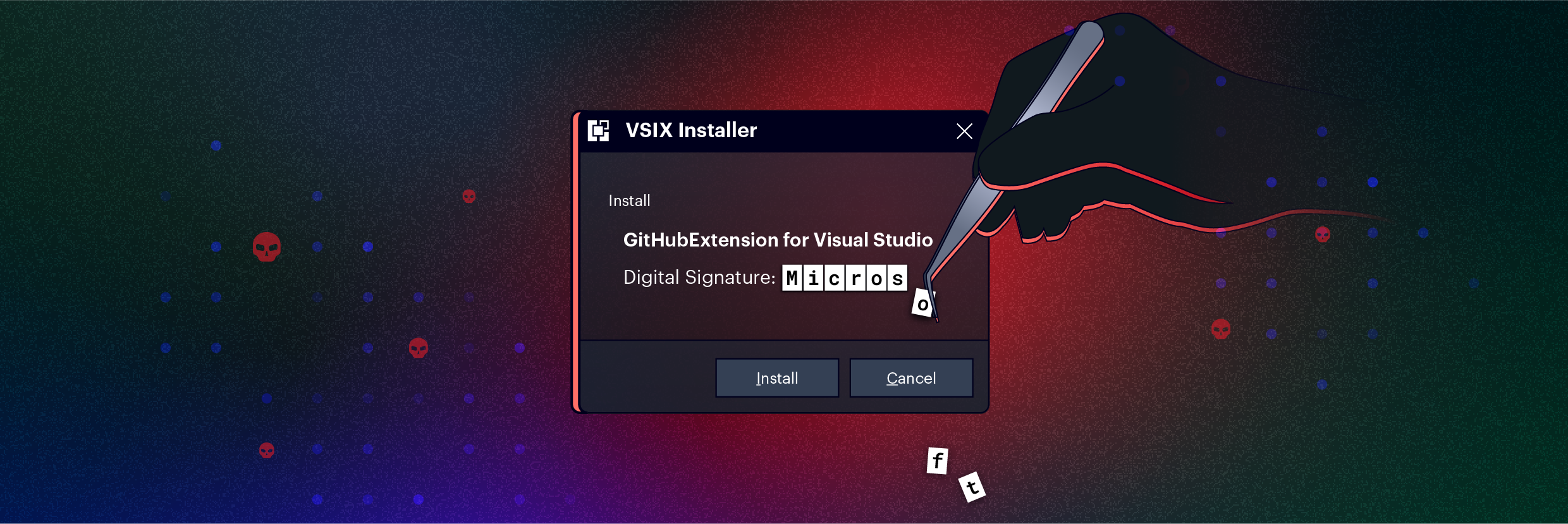
When enough newline characters are added to the extension name,all other text in the Visual Studio installation prompt is pushed down — which effectively hides the warning "Digital Signature: None."
The spoof
Let’s take a moment to review what a normal extension looks like and what the spoofed extension looks like at each stage.
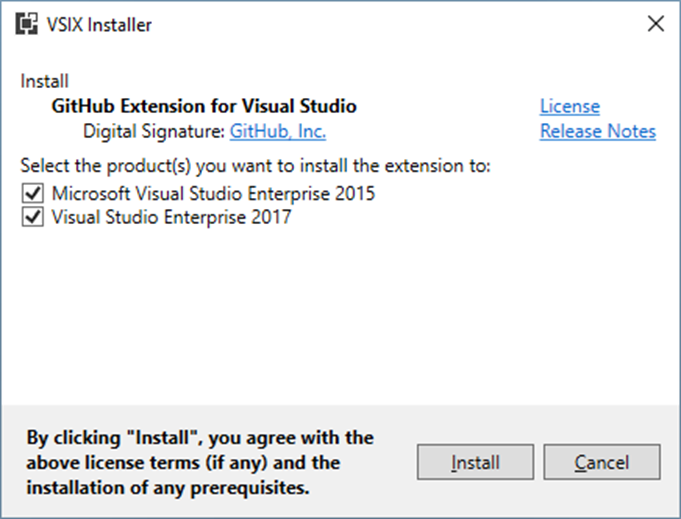
Real extension with digital signature
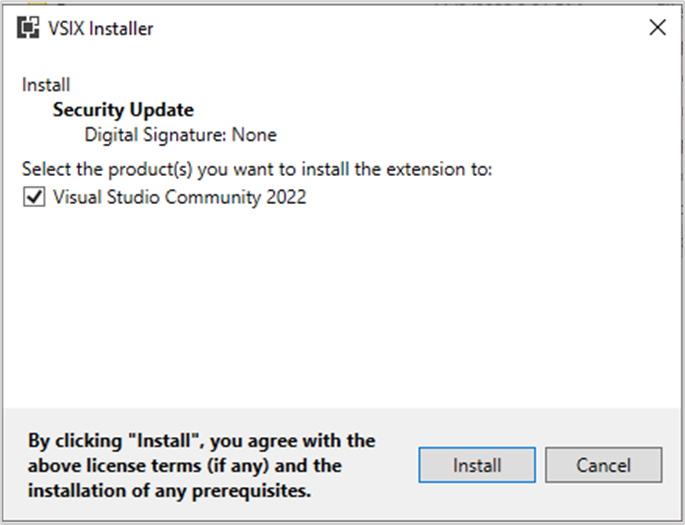
Extension without digital signature
And because a threat actor controls the area under the extension name, they can easily add fake "Digital Signature" text, visible to the user and appearing to be genuine.
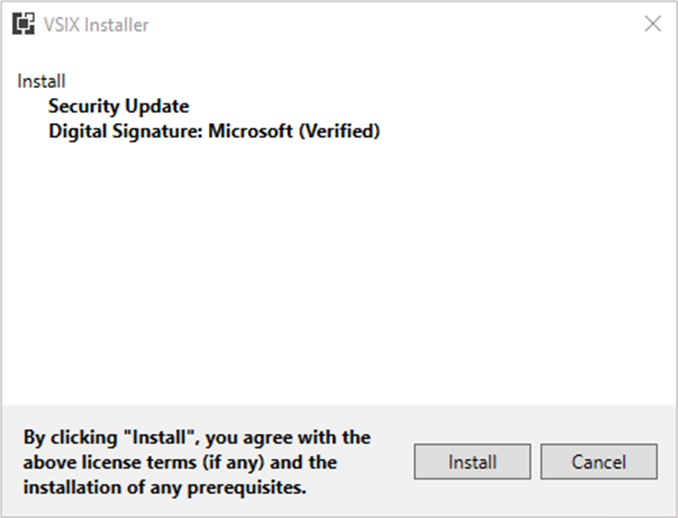
Extension with spoofed signature
The attack scenario
How could an attacker weaponize this exploit?
Primarily by phishing. Imagine the following scenario:
- The attacker sends an email to company developers disguised as a legitimate software update.
- Within the email, the attacker attaches the spoofed VSIX extension that mimics the legitimate one.
- The victim cannot tell the spoofed malicious VSIX from a real, signed update and installs the malicious VSIX.
- After implementing a crafted payload within the extension, the attacker compromises the victim's machine — gaining an initial access footprint to the organization.
- With a foot in the door, the threat actor can continue to perform lateral movement inside the breached organization, potentially allowing the threat actor to steal IP and confidential data, and to further impact the business.
Microsoft response and recommendations
Microsoft recognized this exploit, assigned it the CVE-2023-28299 identifier, and included a fix for it in the April 11, 2023, Patch Tuesday update. Varonis Threat Labs held off on publishing this article until a fix could be issued.
We recommend that all potentially vulnerable systems apply the Microsoft-provided patch and monitor for any suspicious activity.
Summary
CVE-2023-28299 is a UI bug in Microsoft Visual Studio, a leading Integrated Development Environment, that allows for spoofed publisher digital signatures.
The low complexity and privileges required make this exploit easy to weaponize. Threat actors could use this vulnerability to issue spoofed malicious extensions with the intention of compromising systems.
As of April 11, 2023, Microsoft has acknowledged this vulnerability and issued a patch for it as part of their Patch Tuesdays.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.