I’ve already written about the fundamentals of security analytics. To review: it’s the process of aggregating, correlating, and applying other more advanced techniques to raw event data in order to produce an actionable security result. The ideas for my definition were borrowed heavily from Gartner’s wise security thinker, Anton Chuvakin, who has a wonderful presentation on this very subject.
Get the Free Pentesting Active
Directory Environments e-book
Table of Contents
The Limitations of Security Tools
According to Chuvakin, these are the key factors for a security analytics project to be successful:
- Data driven mindset
- Ability to collect data
- Some stats knowledge
- The right tools and people to ask good questions
It’s the last point that often leads IT security teams astray. Sure you can buy individual tools — network monitoring or SIEM — to solve a problem at hand. If you’re aware that these tools are great for answering specific questions — “which app is opening a connection to an unfamiliar IP address? — then you’re not setting yourself up for disappointment later!
The inevitable “gotcha” with specialized security analytics tools is that the IT managers looking at the results will raise questions that can’t be answered by the tool alone: “Why is the PowerShell script that’s connecting to an IP address in a shady domain being run under the account of Trevor in accounting?”
Why indeed! Security analysts may find themselves in a position where they don’t have the technical resources or the time to conduct more comprehensive follow-up. In the case above, the IT admins could kill the rogue PS script and then disable PowerShell or more likely restrict it just to admins on the server. And then perhaps someone else in the security group, when they have the time, can more closely look into Trevor’s activities and learn why he’s periodically logging into a server not normally associated with him.
This may be a satisfactory outcome. But suppose IT management wants more answers, now! Then the IT security team will need to use another tool — say Bloodhound — to study lateral movements of user accounts. And then for the next incident, the security team could cobble together code to dig into the Windows Events log, and watch for non-admin accounts launching script-ware that connects to restricted IP addresses anywhere on the system …
What Is a Security Analytics Platform?
I’m making the obvious point that two or three tools glued together does not a solution make — maybe that’ll replace this legacy expression?
Anyway, the reason for a software platform is that it lets different security functions share a common underlying “backplane” — functions working together within a single application and using the same underlying data structures. The platform can then be applied to many different use cases, unlike a DIY solution.
Security analytics is no different! With a security analytics platform, vendors are also supplying customers with new event collectors and libraries of proven security threat patterns or models (see below). And the platform allows security admins to customize existing threat models or create new ones from scratch to monitor and interpret attacks, all through a consistent interface.
To top it off, the relevant security information is visually displayed in a way that helps lower-level staff, who don’t have a PhD in data analytics, understand what’s important and empowers them to take the most effective actions first — users and devices involved, and practical options for a response.
Security platforms are also scalable. What’s the point of all this capabilities if it can’t efficiently work on large enterprise-size networks?
What I’ve just described has been nicely implemented by a data security company that I happen to know about.
Threat Models and Security Analytics Platforms
As Gartner’s Chuvakin emphasizes, security analytics has to lead to useful security results. It’s not enough to just gather system and security events, and perform some analysis if the information doesn’t give IT staff the relevant security information to do their jobs.
In other words, the analytics algorithms should go beyond an alert that, for example, tells you there’s “a burst of file activity” — perhaps files being copied and renamed. Far more useful is if the analytics informs the incident response team that a ransomware attack is in progress as the files are being quickly replaced with encrypted versions. Or, to take another example, that a user has elevated her privileges by stealing credentials or hashes dumped from LSSAS memory
To provide more relevant security information, researchers came up with the idea of threat models, which are a higher-level or structured view of all the underlying security events. These models are not based on legacy signatures and other indicators of compromise (IOC), but rather on overall system and file activities and behaviors. Thread models give far more meaningful information to security technicians— ransomware, pass the hash, or denial of service (DoS) attack has been detected, instead of a graphic showing a spike in Event 4660s in the log!
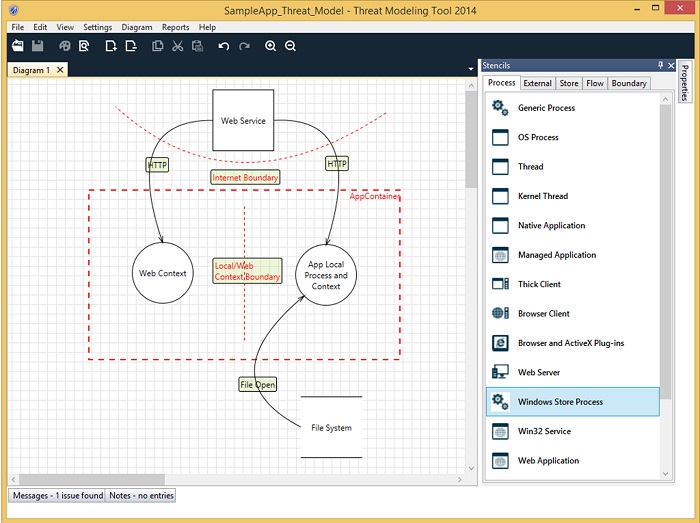
Sure you can do your own threat modeling to work out the details that make up real-world attacks, and there are tools to help you. But it ain’t easy. That’s where a platform vendor can help: bundling proven threat models for many common attacks into the platform, so IT security groups can hit the ground running.
Security Analytic Platform Benefits
To summarize, a security analytics platform has these benefits:
- Many different functions (detection, analytics, mediation) are under a single application roof. The analytics platform makes it easy to share security event information between the various functions. The vendor supports integration with third-parties for specialized features (SIEM, network intrusion, and more).
- The platform is scalable: it can monitor and interpret an enterprise-level volume of security events in near real-time.
- The platform interprets the underlying information as human understandable threat models, and provides higher-level details such as device names, geo location, user account name, and files and folder path names to help admins.
- The platform presents information graphically so than non-specialist technicians can quickly understand the threat and then take actions and remediations from with the interface.
The Big Picture: Security Analytics Platform User Interface
Perhaps the best way to understand what a security analytics platform does is to look at an actual interface. For this, a graphic can be worth its weight in blog verbiage!
Before we delve into a security analytics GUI, it’s educational to see the raw information a good security analytics tool, for example, Event Query Language or EQL, can provide to security admins and analysts.
For your security tools enjoyment, here’s a clip from a video explaining how to craft and run an EQL script to detect typical LoL-malware— in this case, regsvr32. Take a look at the first few minutes:
I’m not saying there’s anything wrong with EQL. In fact, I’ll be exploring this fascinating open-source event monitoring tool in a future post. However, EQL is meant for sophisticated security admins who can develop their own scripts and understand the results from the command-line output.
Contrast the above with the following graphic showing part of the interface for the Varonis Data Security Platform:

Without having to work out threat models or develop their own scripts, a security technician using the Varonis Data Security Platform can quickly see the user, device, and folders that are involved in a threat related to “unusual service behavior access to atypical files”. Notice also there’s context about other recent alerts associated with the user’s device. And if the tech drilled down, he’d discover this particular attack has moved to the exfiltration phase.
The moral of this story: a concise and informative interface, based on event data fed in from multiple sources and analyzed by complex algorithms running under the hood, is not something that can be done with a single-purpose security event tool!
Intrigued? Ask for a demo of the Varonis Data Security Platform today!
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.