-
 Threat Research
Threat ResearchMar 29, 2022
Defending Your Cloud Environment Against LAPSUS$-style Threats
Varonis breaks down the recent LAPSUS$ hacks and provides best practices for defending your cloud environment against LAPSUS$ style threats

Nathan Coppinger
6 min read
-
 Threat Research
Threat ResearchMar 11, 2022
Is this SID taken? Varonis Threat Labs Discovers Synthetic SID Injection Attack
A technique where threat actors with existing high privileges can inject synthetic SIDs into an ACL creating backdoors and hidden permission grants.

Eric Saraga
3 min read
-
 Threat Research
Threat ResearchMar 04, 2022
ContiLeaks: Ransomware Gang Suffers Data Breach
Conti, a prolific ransomware group, has suffered a leak of both internal chat transcripts and source code being shared by a reported Ukrainian member

Jason Hill
6 min read
-
 Threat Research
Threat ResearchFeb 03, 2022
Ransomware Year in Review 2021
In this post, we dive into six ransomware trends that shaped 2021.

Varonis Threat Labs
10 min read
-
 Threat Research
Threat ResearchFeb 02, 2022
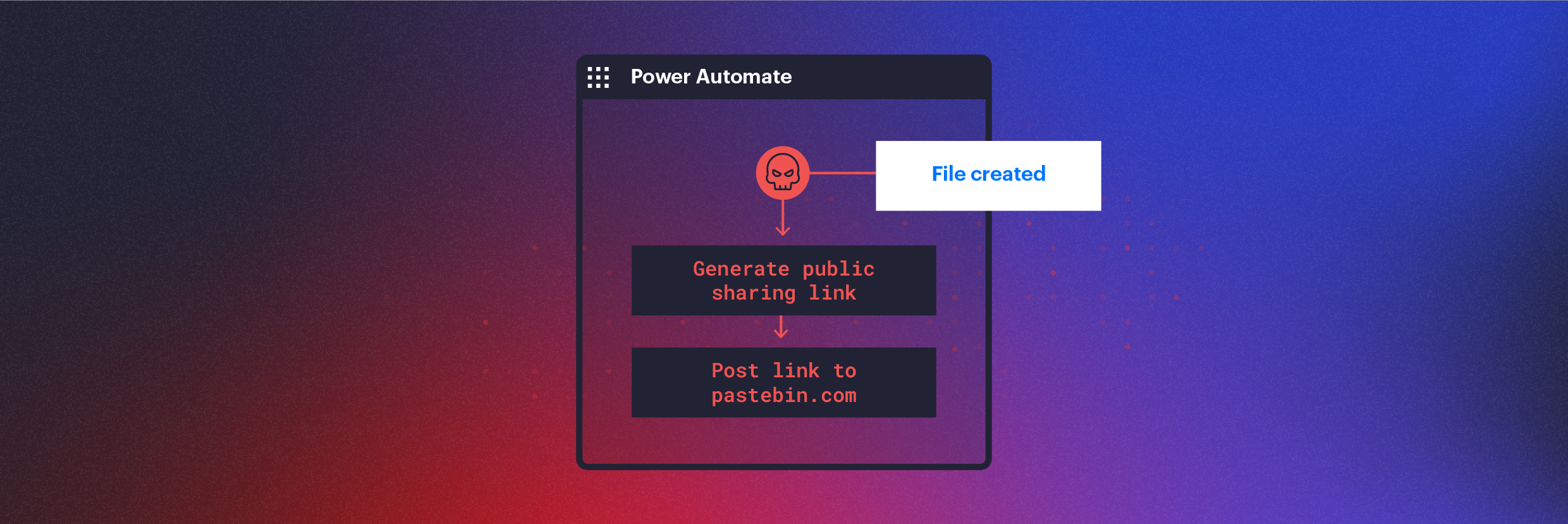
Using Power Automate for Covert Data Exfiltration in Microsoft 365
How threat actors can use Microsoft Power Automate to automate data exfiltration, C2 communication, lateral movement, and evade DLP solutions.

Eric Saraga
5 min read
-
 Threat Research
Threat ResearchJan 26, 2022
BlackCat Ransomware (ALPHV)
Varonis has observed the ALPHV (BlackCat) ransomware, actively recruiting new affiliates and targeting organizations across multiple sectors worldwide.

Jason Hill
9 min read
-
 Threat Research
Threat ResearchJan 18, 2022
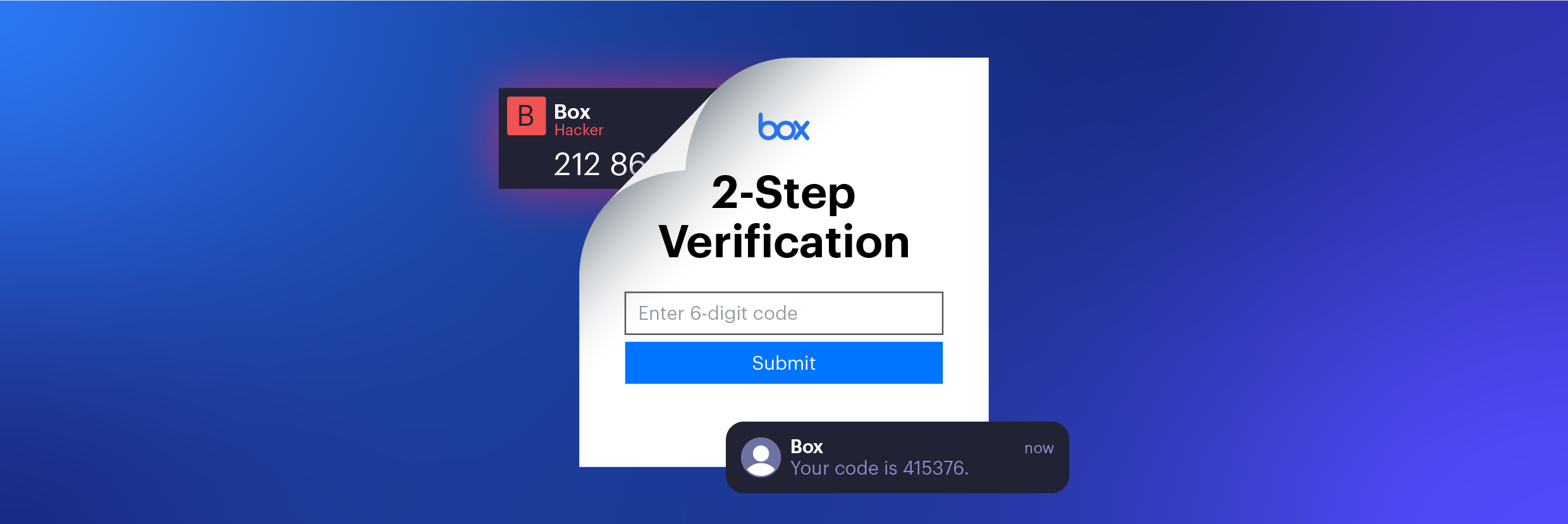
Mixed Messages: Busting Box’s MFA Methods
Varonis Threat Labs discovered a way to bypass multi-factor authentication (MFA) for Box accounts that use an SMS code for login verification.

Tal Peleg
3 min read
-
 Threat Research
Threat ResearchDec 02, 2021
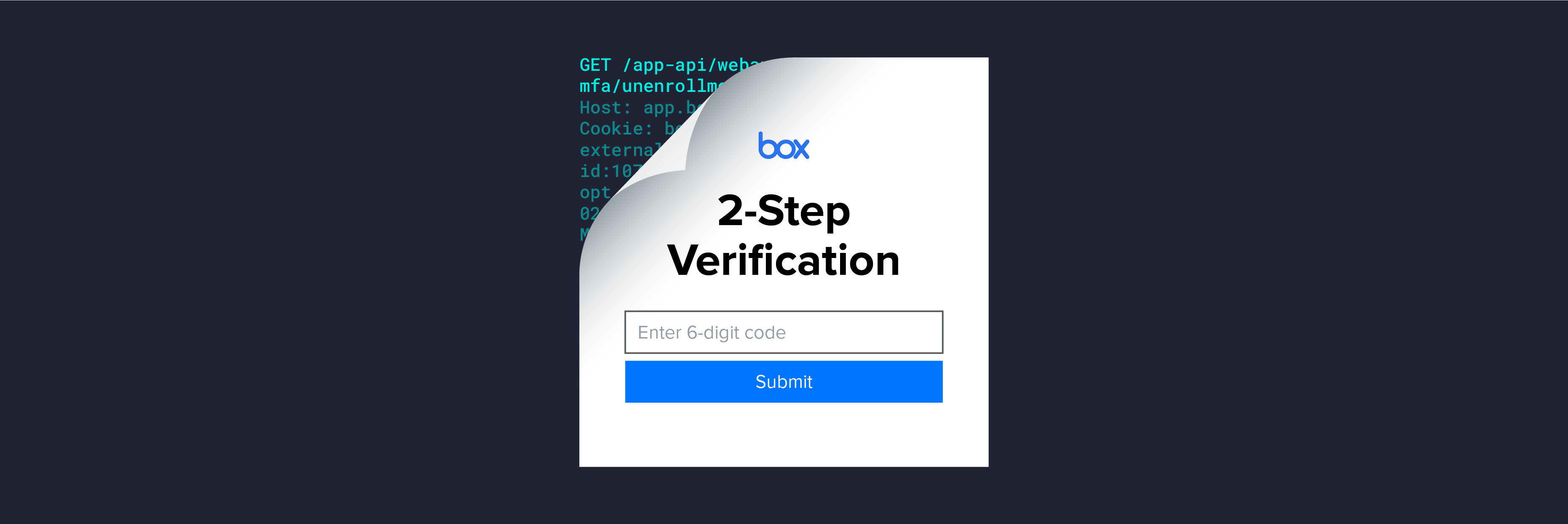
Bypassing Box's Time-based One-Time Password MFA
The Varonis research team discovered a way to bypass Box's Time-based One-Time Password MFA for Box accounts that use authenticator applications.

Tal Peleg
2 min read
-
 Threat Research
Threat ResearchNov 17, 2021
No Time to REST: Check Your Jira Permissions for Leaks
Varonis researchers enumerated a list of 812 subdomains and found 689 accessible Jira instances. We found 3,774 public dashboards, 244 projects, and 75,629 issues containing email addresses, URLs, and IP...

Omri Marom
4 min read
-
 Threat Research
Threat ResearchNov 02, 2021
Einstein's Wormhole: Capturing Outlook & Google Calendars via Salesforce Guest User Bug
If your organization uses Salesforce Communities and Einstein Activity Capture, you might have unknowingly exposed your administrator's Outlook or Google calendar events to the internet due to a bug called...

Nitay Bachrach
3 min read
-
 Threat Research
Threat ResearchNov 02, 2021
BlackMatter Ransomware: In-Depth Analysis & Recommendations
CISA has issued a security bulletin regarding the BlackMatter 'big game hunter' ransomware group following a sharp increase in cases targeting U.S. businesses. To mitigate these attacks, it is recommended...

Dvir Sason
6 min read
-
 Data Security Threat Research
Data Security Threat ResearchOct 21, 2021
Abusing Misconfigured Salesforce Communities for Recon and Data Theft
Our research team has discovered numerous publicly accessible Salesforce Communities that are misconfigured and expose sensitive information.

Nitay Bachrach
10 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital