-
 Data Security
Data SecurityJun 26, 2017
What is UPnP and why is it Dangerous?
Learn what UPnP (Universal Plug and Play) is and about its potential dangers. Contact us today for all of your cybersecurity needs.

Michael Buckbee
3 min read
-
 Data Security
Data SecurityJun 20, 2017
I Click Therefore I Exist: Disturbing Research On Phishing
Homo sapiens click on links in clunky, non-personalized phish mails. They just do. We’ve seen research suggesting a small percentage are simply wired to click during their online interactions. Until...

Michael Buckbee
3 min read
-
 Data Security
Data SecurityJun 06, 2017
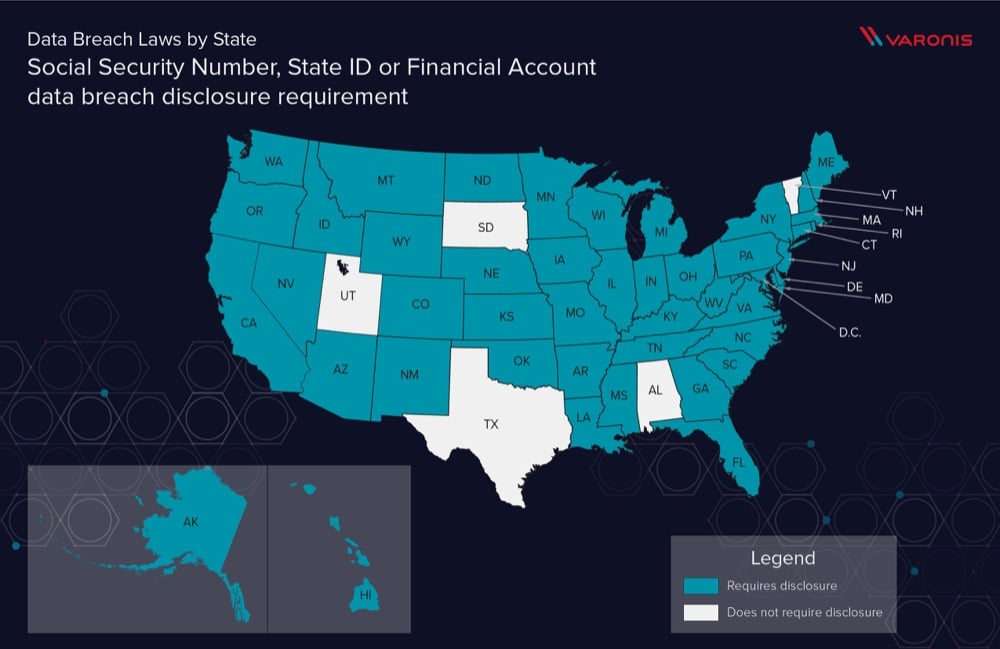
Data Breach Definition by State
State governments are becoming more aware of PII and PHI data breaches, how about your state? See how PII is protected per state with our primer on US State Data Breach Law Definitions.

Michael Buckbee
10 min read
-
 Data Security
Data SecurityMay 26, 2017
Disabling PowerShell and Other Malware Nuisances, Part I
Back in more innocent times, circa 2015, we began to hear about hackers going malware-free and “living off the land.” They used whatever garden-variety IT tools were lying around on...

Michael Buckbee
4 min read
-
 Data Security
Data SecurityMay 20, 2017
EternalRocks leaves backdoor trojan for remote access to infected machines
What we know so far The WannaCry ransomware worm outbreak from last Friday week used just one of the leaked NSA exploit tools, ETERNALBLUE, which exploits vulnerabilities in the SMBv1...

Kieran Laffan
2 min read
-
 Data Security
Data SecurityMay 15, 2017
Why did last Friday's ransomware infection spread globally so fast?
Ransomware is a type of malware that encrypts your data and asks for you to pay a ransom to restore access to your files. Cyber criminals usually request that the...

Kieran Laffan
3 min read
-
 Data Security
Data SecurityMay 12, 2017
🚨 Massive Ransomware Outbreak: What You Need To Know
Remember those NSA exploits that got leaked a few months back? A new variant of ransomware using those exploits is spreading quickly across the world – affecting everyone from the...

Michael Buckbee
2 min read
-
 Data Security
Data SecurityMay 12, 2017
Planet Ransomware
If you were expecting a quiet Friday in terms of cyberattacks, this ain’t it. There are reports of a massive ransomware attack affecting computers on a global scale: in the...

Michael Buckbee
1 min read
-
 Data Security
Data SecurityApr 12, 2017
What is a Data Security Portfolio?
A Data Security Platform (DSP) is a category of security products that replaces traditionally disparate security tools to reduce risk and prevent threats.

Rob Sobers
6 min read
-
 Data Security
Data SecurityMar 08, 2017
Practical PowerShell for IT Security, Part I: File Event Monitoring
Back when I was writing the ultimate penetration testing series to help humankind deal with hackers, I came across some interesting PowerShell cmdlets and techniques. I made the remarkable discovery...

Michael Buckbee
5 min read
-
 Data Security
Data SecurityJan 20, 2017
Connecting Your Data Strategy to Analytics: Eight Questions to Ask
Big data has ushered in a new executive role over the past few years. The chief data officer or CDO now joins the C-level club, tasked with leveraging data science...

Michael Buckbee
3 min read
-
 Data Security
Data SecurityJan 12, 2017
How to setup a SPF record to prevent spam and spear phishing
Some things go together like peanut butter and jelly: delicious, delightful and a good alternative to my dad’s “Thai-Italian Fusion” dinner experiments as a kid. When other things are combined...

Michael Buckbee
6 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital