-
 Data Security
Data SecurityMay 25, 2018
What's The Difference Between a Proxy and a VPN?
Comparing a proxy vs VPN? We're taking a look at each to help you understand the benefits, drawbacks and steps to deciding which is right for your company!

Michael Buckbee
4 min read
-
 Data Security
Data SecurityMay 24, 2018
The Malware Hiding in Your Windows System32 Folder: Intro to Regsvr32
In our epic series on Malware-Free Hacking, I wrote about techniques that let you use well-known Microsoft apps and tools to run evil custom scripts. This file-less hack-craft usually involves sneaking...

Michael Buckbee
5 min read
-
 Data Security
Data SecurityMay 21, 2018
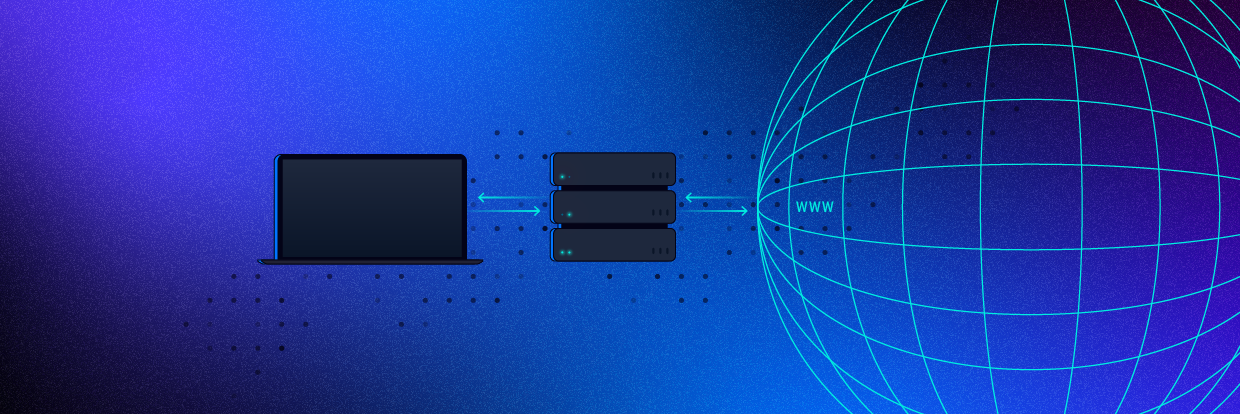
What is a Proxy Server and How Does it Work?
A proxy server acts as a gateway between you and the internet. Learn the basics about proxies with our complete, easy-to-follow guide.

Michael Buckbee
7 min read
-
 Data Security
Data SecurityMay 18, 2018
What is Spear Phishing?
You might be wondering what is spear phishing. Our guide includes all the information you'll need to know including examples and tips for avoiding an attack

Michael Buckbee
3 min read
-
 Data Security
Data SecurityMay 08, 2018
The Anatomy of a Phishing Email
Have you been hooked by a phishing email? We’ve broken out the most common components of a phishing email. Check out our full guide to test your knowledge!

Rob Sobers
3 min read
-
 Data Security
Data SecurityApr 17, 2018
Verizon 2018 DBIR: Phishing, Stolen Passwords, and Other Cheap Tricks
Like the rest of the IT security world last week, I had to stop everything I was doing to delve into the latest Verizon Data Breach Investigations Report. I spent...

Michael Buckbee
4 min read
-
 Data Security
Data SecurityMar 01, 2018
GDPR Data Protection Supervisory Authority Listing
The DPA (Data Protection Authority) is the agency within each European Union country that is responsible for GDPR (General Data Protection Regulation) assistance and enforcement. A Data Protection Authority handles...

Michael Buckbee
5 min read
-
 Data Security
Data SecurityDec 15, 2017
Best of the Inside Out Security Show Podcast
We’ve interviewed many privacy experts, chief data officers, security pros and learned so much about the real world. Because we’ve covered so much, I’ve curated the most popular infosec quotes...

Michael Buckbee
1 min read
-
 Data Security
Data SecurityOct 30, 2017
Why A Honeypot Is Not A Comprehensive Security Solution
A core security principle and perhaps one of the most important lessons you’ll learn as a security pro is AHAT, “always have an audit trail”. Why? If you’re ever faced...

Michael Buckbee
5 min read
-
 Data Security
Data SecurityOct 03, 2017
[Transcript] Ofer Shezaf and Keeping Ahead of the Hackers
Inside Out Security: Today I’m with Ofer Shezaf, who is Varonis’s Cyber Security Director. What does that title mean? Essentially, Ofer’s here to make sure that our products help customers...

Michael Buckbee
11 min read
-
 Data Security
Data SecurityJun 28, 2017
Complete Guide to Windows File System Auditing - Varonis
Windows file auditing is key in a cybersecurity plan. Learn about file system auditing and why you'll need an alternate method to get usable file audit data

Michael Buckbee
7 min read
-
 Data Security
Data SecurityJun 26, 2017
What is UPnP and why is it Dangerous?
Learn what UPnP (Universal Plug and Play) is and about its potential dangers. Contact us today for all of your cybersecurity needs.

Michael Buckbee
3 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital