-
 Data Security
Data SecurityMar 29, 2020
What is an IT Security Audit? The Basics
Security audits are crucial to maintaining effective securilty policies and practices — learn best practices, audit types and what to look for in an audit

Michael Buckbee
5 min read
-
 Data Security
Data SecurityMar 29, 2020
What is DCOM (Distributed Component Object Model)?
DCOM (Distributed Component Object Model) is a programming construct that allows a computer to run programs over the network on a different computer as if the program was running locally. Our guide details everything you need to know and more, check it out!

Michael Buckbee
3 min read
-
 Data Security
Data SecurityMar 29, 2020
Protect Your Data With Super Easy File Security Tricks!
But if you drill down a little in your thinking, it’s easy to see that data security is ultimately protecting a file somewhere on your system—whether desktops or servers. While data security is a good umbrella term, we need to get into more details to understand file security.

Michael Buckbee
6 min read
-
 Data Security
Data SecurityMar 29, 2020
Social Media Security: How Safe is Your Information?
What exactly are social media platforms doing to keep your information safe? We’ve broken down the security initiatives and features to find out!

Rob Sobers
2 min read
-
 Data Security
Data SecurityMar 29, 2020
What is an Advanced Persistent Threat (APT)?
An advanced persistent threat is a long term operation designed to steal as much valuable data as possible. Learn how to protect your organization and more

Michael Buckbee
4 min read
-
 Data Security
Data SecurityMar 29, 2020
10 Secure File Sharing Options, Tips and Solutions
When moving digital data across networks, there is a number of different tools and solutions that will fit various business needs at the enterprise level.

Michael Buckbee
8 min read
-
 Data Security
Data SecurityMar 29, 2020
5 Cybersecurity Concerns of Industry Insiders
We asked professionals attending two of the world’s biggest cybersecurity conferences – RSA in San Francisco and Infosecurity in London – five questions to gauge their opinions and attitudes about current cybersecurity concerns and issues. Read on to discover what we found!

Rachel Hunt
3 min read
-
 Data Security
Data SecurityMar 29, 2020
Zero-Day Vulnerability Explained
Find out how zero-day vulnerabilities become zero-day exploits and zero-day attacks, and how to defend your network from zero-day attacks and exploits.

Michael Buckbee
3 min read
-
 Data Security
Data SecurityMar 29, 2020
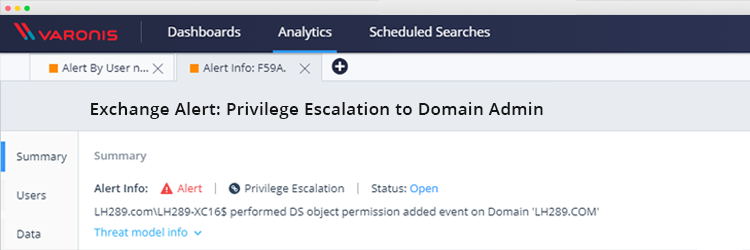
Exchange Vulnerability: How to Detect Domain Admin Privilege Escalation
Researchers recently uncovered a vulnerability in Exchange that allows any domain user to obtain Domain admin privileges that allow them to compromise AD and connected hosts. Here’s how the attack...

Michael Buckbee
1 min read
-
 Data Security
Data SecurityMar 29, 2020
Spotlighting Unstructured Data Access
At Varonis, we sometimes highlight external articles, especially when they provide independent insight into our solution. Dr. Edward G. Amoroso, former Senior Vice President and Chief Security Officer of AT&T,...

Rob Sobers
1 min read
-
 Data Security
Data SecurityMar 29, 2020
What Working in Cybersecurity is Really Like: A Day in the Life
Learn what working in cybersecurity is like from Q&A with experts across various job roles — including which skills you need, resources and expert advice

Rob Sobers
18 min read
-
 Data Security
Data SecurityMar 29, 2020
What Certifications Should I Get for IT?
Elevate your IT knowledge and credentials by using our IT certification flowcharts to find the right certification for your experience level and interests.

Rob Sobers
2 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital