-
 Data Security
Data SecurityJun 19, 2020
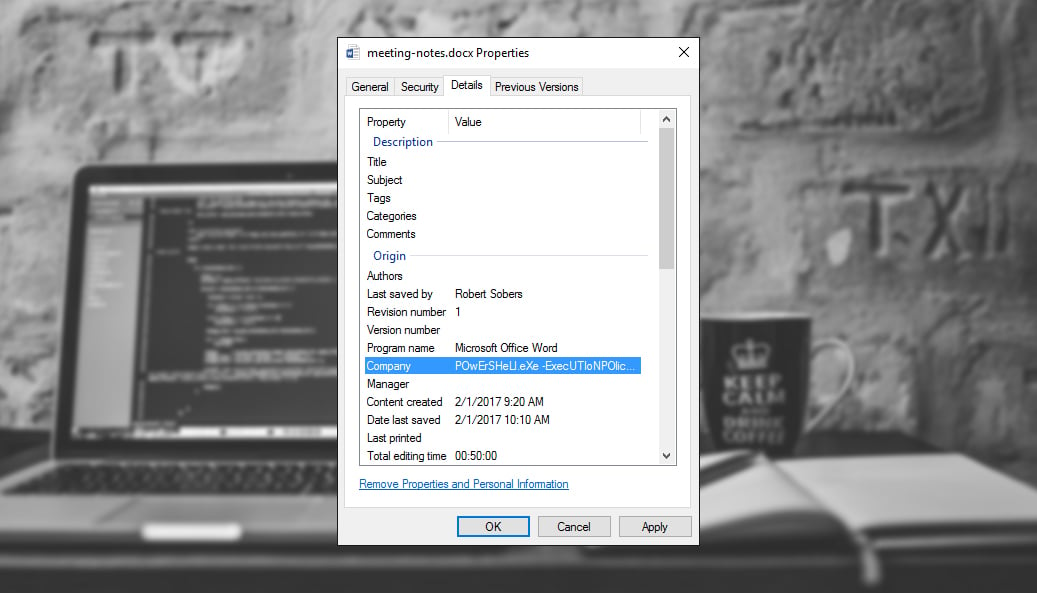
Detecting Malware Payloads in Office Document Metadata
Ever consider document properties like “Company,” “Title,” and “Comments” a vehicle for a malicious payload? Checkout this nifty PowerShell payload in the company metadata: #powershell payload stored in office metadataDocument...

Rob Sobers
1 min read
-
 Data Security
Data SecurityJun 19, 2020
Working With Windows Local Administrator Accounts, Part I
In writing about hackers and their techniques, the issue of Windows local Administrator accounts often comes up. Prior to Windows 7, the Administrator account was created by default with no...

Michael Buckbee
3 min read
-
 Data Security
Data SecurityJun 19, 2020
Defining Deviancy With User Behavior Analytics
For over the last 10 years, security operations centers and analysts have been trading indicators of compromise (IoC), signatures or threshold-based signs of intrusion or attempted intrusion, to try to...

Matt Radolec
4 min read
-
 Data Security PowerShell
Data Security PowerShellJun 19, 2020
PowerShell Obfuscation: Stealth Through Confusion, Part I
To get into the spirit of this post, you should probably skim through the first few slides of this presentation by Daniel Bohannon and Le Holmes given at Black Hat...

Michael Buckbee
3 min read
-
 Data Security PowerShell
Data Security PowerShellJun 19, 2020
How to use PowerShell Objects and Data Piping
This article is a text version of a lesson from our PowerShell and Active Directory Essentials video course (use code ‘blog’ for free access). The course has proven to be...

Michael Buckbee
5 min read
-
 Data Security
Data SecurityJun 19, 2020
More NSA Goodness: Shadow Brokers Release UNITEDRAKE
Looking for some good data security news after the devastating Equifax breach? You won’t find it in this post, although this proposed federal breach notification law could count as a...

Michael Buckbee
2 min read
-
 Data Security
Data SecurityJun 19, 2020
Interview With Wade Baker: Verizon DBIR, Breach Costs, & Selling Boardrooms on Data Security
Wade Baker is best known for creating and leading the Verizon Data Breach Investigations Report (DBIR). Readers of this blog are familiar with the DBIR as our go-to resource for...

Michael Buckbee
14 min read
-
 Data Security
Data SecurityJun 19, 2020
DNSMessenger: 2017's Most Beloved Remote Access Trojan (RAT)
I’ve written a lot about Remote Access Trojans (RATs) over the last few years. So I didn’t think there was that much innovation in this classic hacker software utility. RATs, of...

Michael Buckbee
2 min read
-
 Data Security
Data SecurityJun 17, 2020
How to Protect GDPR Data with Varonis
In the overall data security paradigm, GDPR data isn’t necessarily more important than other sensitive data, but demands specific monitoring, policy, and processing – with significant fines to encourage compliance....

Michael Buckbee
3 min read
-
 Data Security
Data SecurityJun 17, 2020
Adventures in Fileless Malware, Part II: Sneaky VBA Scripts
I’m a fan of the Hybrid Analysis site. It’s kind of a malware zoo where you can safely observe dangerous specimens captured in the wild without getting mauled. The HA...

Michael Buckbee
5 min read
-
 Data Security Privacy & Compliance
Data Security Privacy & ComplianceJun 17, 2020
Wyden’s Consumer Data Protection Act: Preview of US Privacy Law
The General Data Protection Regulation (GDPR) has, for good reason, received enormous coverage in the business and tech press in 2018. But wait, there’s another seismic privacy shift occurring, and...

Michael Buckbee
4 min read
-
 Data Security
Data SecurityJun 17, 2020
Koadic: Security Defense in the Age of LoL Malware, Part IV
One of the advantages of examining the gears inside Koadic is that you gain low-level knowledge into how real-world attacks are accomplished. Pen testing tools allow you to explore how...

Michael Buckbee
5 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital