When someone says the word "hacker," you probably imagine one of two things.
You might picture skilled cybercriminals creating malware, running brute-force attacks, or performing SQL injections.
Or maybe you think of the Hollywood cliche of someone in a hoodie sitting in a dark room, hammering away at a keyboard for 30 seconds before proclaiming, "We're in!"
What you probably don't imagine is someone simply pasting a URL into Postman, clicking send, and getting back 11 million customer records.
But that's precisely what can happen to businesses when they aren’t careful, and this highlights the importance of using SaaS security posture management (SSPM) tools in your data security strategy.
Unfortunately, implementing SSPM is not as cut and dry as buying the latest tech tools and hitting “Go.” The issue with most SSPM tools is that they only do half of the job.
They audit the configuration of your SaaS and cloud apps but don't audit the data itself or users. The tools also do nothing to actively resolve the issues they find. This means even if the tools find issues, you've still got to investigate and fix them yourself, which can be time-consuming and expensive.
Varonis approaches SSPM differently, taking a data-first approach and using automation to resolve the issues the platform detects, giving you a clearer view of where there are risks and how they can be mitigated.
In this blog post, we will cover:
- The importance of protecting yourself against misconfiguration risk
- Why most SSPM tools don't provide enough protection
- Why a data-first approach is the best way to stop attacks
- How Varonis safeguards SaaS tools and actively works to protect data
Security incidents caused by misconfiguration
Unfortunately, the Postman example we mentioned above isn't an isolated case. Misconfiguration has caused issues for countless companies.
The Cloud Security Alliance found that nearly half of all organizations reported they had dealt with one or more security incidents because of a SaaS misconfiguration.
The problem is that the bigger your organization is, the more likely mistakes will happen. We’re all flawed humans who sometimes get things wrong or make hasty decisions.
This is especially relevant when you consider the increased reliance on SaaS solutions — such as Google Drive, Microsoft 365, and Salesforce — for collaboration and data storage to carry out essential business processes.
This leaves companies vulnerable in ways that can feel impossible to solve. If you lock things down too tightly, you stunt the productivity of your teams, but the more freedom they have, the higher the risk of something going wrong.
This is why it's so important to use tools that make collaboration easier while actively helping you solve security issues within your company.
SSPM tools help you identify misconfigurations.
SSPM tools are designed to help organizations manage the security posture of their SaaS applications (as the name states) and identify where misconfigurations could put their SaaS environment and the data within at risk.
Most commonly, these tools continuously audit your SaaS applications to identify and alert you to misconfigurations as they occur, providing you with recommendations and necessary steps for remediation.
These misconfigurations can range from not enforcing MFA on GitHub to org-wide default settings exposing records publicly in Salesforce. Something as seemingly innocuous as a mis-checked box when configuring your SaaS application can open your organization up to significant risks.
Continuous monitoring allows you to quickly identify and resolve any issues before a user accidentally exposes critical data — or even worse, a threat exploits those misconfigurations.
But most of these tools are just that — tools, which have a narrow focus and solve only one part of the equation. These tools don't take into account the risk associated with misconfigured identities, sharing rules, and infrastructure.
Using an SSPM tool in isolation will only get you so far. The goal of any security tool or approach is to lower the risk of data leakage or breach. But by focusing solely on SaaS misconfigurations, you're only tackling one piece of the puzzle. The tools themselves will certainly help reduce risks, but you can’t feel confident that the data in those applications is secure with just an SSPM tool.
Instead, you need to look at the posture of not just the configurations but the SaaS data itself. And you do this by combining SSPM with data security posture management (DSPM).
How Varonis secures your SaaS
Instead of only auditing the configuration of your SaaS, Varonis takes a holistic, data-centric approach to tackle the problem, reducing both your attack surface and blast radius as much as possible.
We do this not only by giving you much better visibility of misconfigurations but also by allowing you to analyze your SaaS security at the data level. This includes where your data lives, who can access it, and what they can do with it.
We also use automation to remediate issues we find. This can vary from misconfiguration to remediating the SaaS permissions themselves.
Here are breakdowns of the eight capabilities we use to secure your SaaS apps:
Misconfiguration detection
As we’ve already mentioned, misconfiguration of your SaaS platforms can be a huge factor in the security of your data.
According to the 2021 Gartner report on the Hype Cycle for Cloud Security, between now and 2025, more than 99% of cloud breaches will be avoidable and caused by misconfigurations and end-user mistakes.
This is why it’s so important to pick up on misconfiguration issues automatically.
Varonis continuously scans your SaaS and IaaS apps and identifies security gaps and misconfigurations. We alert you when issues arise, sort them by severity, and clearly and concisely explain how these gaps put your organization at risk to help you prioritize remediation efforts.
Varonis posture dashboard
Along with identifying exposure risks, Varonis’ posture dashboard lets you visualize where your configurations are drifting from best practices set by rules and regulations like NIST, HIPAA, ISO, and CIS, potentially creating compliance issues.
Each alert comes with step-by-step instructions on how to solve the issue, and you can even automatically fix certain misconfigurations with a click of a button.
This gives you the peace of mind that your SaaS platforms are always configured correctly, and you’re not going to be at risk due to user error.
Varonis Threat Labs
Our team of experts continuously updates Varonis’ misconfiguration library with the latest configuration risks and best practices as SaaS and IaaS platforms evolve and add new configuration options.
We employ world-class domain experts in Salesforce, AWS, Google, Okta, and more, so you don’t have to. We develop, test, and automatically push new insight definitions to all customers.
Our elite cybersecurity research team, Varonis Threat Labs (VTL), constantly discovers new attack vectors and ways threat actors abuse misconfigurations in the world’s most critical SaaS apps. Our learnings from VTL create new and unique cloud security insights that keep you safe.
Data access control
Managing your environment’s security posture doesn’t stop at fixing misconfigurations. Ensuring your data access is configured correctly and locked down is just as important, if not more.
This is where you begin to see the value of combining SSPM with DSPM. Varonis not only analyzes the configuration of your apps but also audits the security posture of data stored in SaaS.
You can drill down into any folder or specific piece of data and see who can access it. Varonis makes it quick and easy for you to understand what level of access each person has without having to be an expert in each platform by normalizing permissions into a simple CRUDS labeling system (create, read, update, delete, and share).
You also have a bi-directional view, so in addition to analyzing data, you can look at a user and see all the data they have access to, making it easy to understand the damage they could do if they were to be compromised. We also tell you whether the data has been shared and tagged as org-wide, external, or public so you know exactly how it’s exposed.
User activity auditing
It's all well and good knowing what someone can do, but it's also vital to track what someone has done with your valuable SaaS data. This is why our user and data activity auditing are so important.
Varonis aggregates data activity, authentication events, privilege escalations, group changes, and more, producing a cross-cloud audit trail that's easy to read and analyze.
Varonis can also differentiate between normal and privileged user activity, helping you identify particularly risky activity by users with elevated permissions who could do serious damage if a threat were to compromise their accounts.
Varonis uses these events to provide real-time alerting on any potentially abnormal or risky activity so issues and potential threats are caught, investigated, and resolved quickly.
Sensitive data discovery and classification
We also automatically discover and classify your sensitive SaaS and cloud data and present it in an easy-to-read file tree format, giving you better visibility and making it simple to sort and filter the data.
This includes categories such as PII, security, financial, etc., which you can view at a folder level, or drill down through sub-folders and analyze individual pieces of data.
You can also review individual resources with Varonis’ file analysis capabilities to see exactly where sensitive data lives in the resource and validate classification results.
We’ll show you where this data is exposed internally, externally, and publicly, helping you prioritize risk reduction on your most sensitive data.
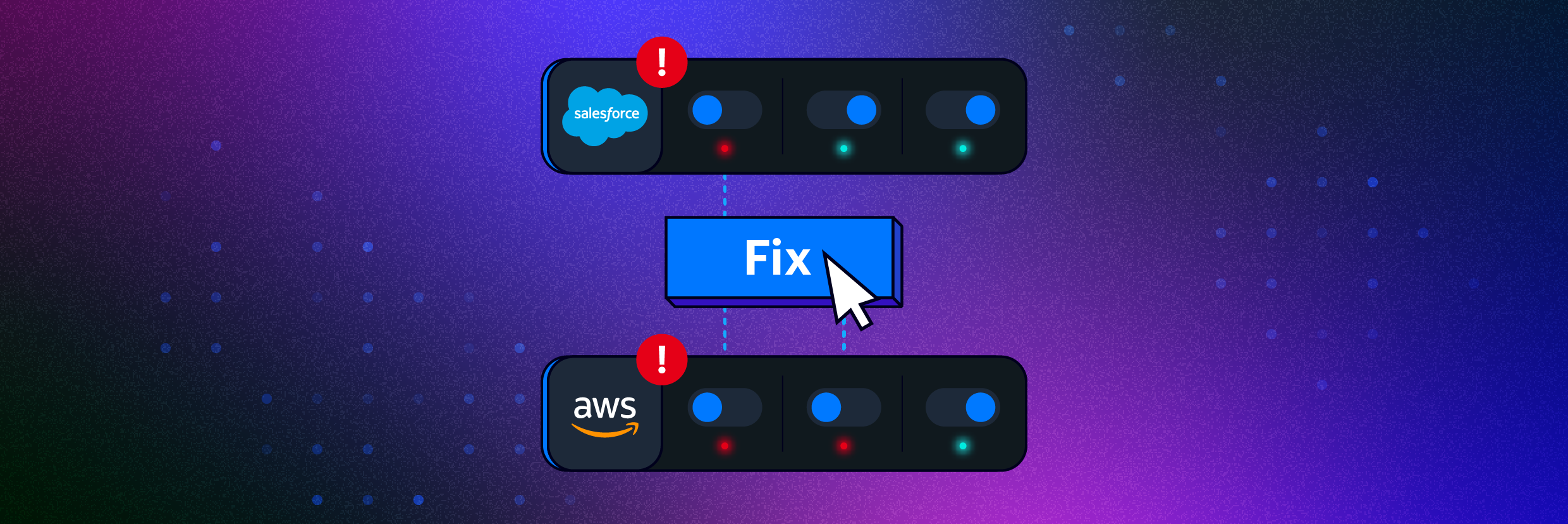
Remediation
Unlike many SSPM solutions, which can open a support ticket or trigger a workflow, Varonis' automated posture management feature can be configured to execute the change in the misconfigured SaaS application instantly.
Enable this feature to fix the flagged issue automatically, saving you time from having to locate and fix the issues yourself manually. With one click, the issue is fixed, and the alert is gone.
This button triggers Varonis to fix the flagged issues automatically, whether it's a misconfiguration or an access issue.
This saves you from having to locate and fix the issues yourself manually. One click and the issue is fixed, and the alert is gone.
Automation
Once you've chosen what to remediate using the feature above, our least privilege automation can also automatically remediate the permissions and access for you.
And it only takes four simple steps:
- Identify the scope of the automation based on your high-priority areas.
- Configure your remediation rule behavior.
- Run rules to review the expected changes.
- Turn the feature on and track the progress.
Once you’ve performed this action, your issues will resolve automatically as they come up.
Varonis in action
When a college in the U.S. was informed someone in their school was storing copyrighted materials in Google Drive for distribution, the school had no way of knowing who it was.
Thousands of students were enrolled, and all the school administrators had was a system log to work from, so identifying the culprit felt like an impossible task.
However, by combining the SSPM and DSPM tools in Varonis, the college officials solved the mystery: They audited the data, including the configuration, permissions, and access logs, helping them quickly identify the drive where the data was stored, and the person responsible for it.
The school enforced least privilege across the college to prevent this from happening again and configured alerts to detect abnormal behavior in the future. Now, they have a clear view of all their data and can proactively stay on top of threats and issues.
If you've ever managed (or tried to manage) permissions in Salesforce, you might appreciate all these features for use with Google Drive or Box, but wonder if these functionalities work within Salesforce. After all, Salesforce holds some of your most valuable data, but it's notoriously complicated.
However, everything we've discussed in this blog post can also be achieved in Salesforce:
- Easily see who can access what records, files, and attachments in a bi-directional view.
- View clear audit logs of who has accessed what and what they did with it.
- Automatically classify all your Salesforce data to identify areas of risk and sensitivity.
- Locate any misconfigurations and fix them with one click of a button.
Read how we also helped one of America's top real estate organizations protect sensitive data in their SaaS apps (including Salesforce) in our case study here.
In closing
If you want to avoid joining the growing list of breached companies, having an effective SSPM tool is vital, but you can’t stop there. Most tools only focus on misconfigurations and leave you with a list of issues to fix.
This leaves you vulnerable to a much larger attack surface and blast radius.
Instead, you should take a data-first approach by combining your SSPM with DSPM. That way, the data in your SaaS and cloud applications will be protected, and your attack surface and blast radius will shrink.
Varonis gives you a complete view of not just how SaaS settings are configured but also what data they hold, who has access to them, and how they are being used. We do this by giving you the tools you need and automating most of the work:
- User activity auditing
- Threat detection
- Misconfiguration detection
- Sensitive data discovery and classification
- Automated remediation
With Varonis, you can rest easy knowing your data is secure, no matter the app where it's stored.
Get started with a free Data Risk Assessment which gives you access to the entire Varonis Data Security Platform to see how secure your data is.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.


/Insights%20Dashboard%20-%201-1.png?width=690&height=268&name=Insights%20Dashboard%20-%201-1.png)