The U.S. Cybersecurity and Infrastructure Agency (CISA) issued an alert warning Sisense customers of a data breach. The agency advised all Sisense customers to "reset credentials and secrets potentially exposed to, or used to access, Sisense services" and report any suspicious activity.
Sisense's CISO echoed this message, advising customers: “Out of an abundance of caution, and while we continue to investigate, we urge you to promptly rotate any credentials that you use within your Sisense application."
Sisense makes business intelligence products that allow customers to build custom dashboards by connecting to multiple third-party services.
IMPORTANT: The data stolen from Sisense includes credentials, tokens, and access configurations. Therefore, not only is the data stored within Sisense at risk, but data in each connected service may also be at risk. This includes cloud services such as Salesforce, Azure Blob, Amazon S3, Amazon RDS, GitHub, Google, Box, and many others.
Sisense can also establish JDBC and SSH connections to data sources on unmanaged or on-premises servers.
What does this mean for my organization?
If you are a Sisense customer, your Sisense credentials may have been compromised, giving bad actors access to data stored in your Sisense instance. Sisense has not confirmed precisely which data was stolen, and the nature of the data at risk will likely vary from customer to customer, depending on what they use Sisense for. Example dashboards include financial data, PII, customer data, HR data, and more.
Keep in mind that some Sisense integrations use OAuth and app keys to connect to third-party systems while others require a simple username and password.
We advise Sisense customers to:
- Reset credentials used to access Sisense products.
- Reset credentials stored in Sisense for data integrations.
- Limit Sisense access to integrations to Sisense IPs (107.23.195.228 and 54.236.224.46) to lower the risk of data exfiltration.
- For self-hosted databases and SSH tunnels, limit user connections to the above IPs.
- For cloud-hosted data sources (e.g., AWS or Azure), put a policy in place to restrict Sisense's cloud identity to act from the above IPs.
- Search for Sisense integrations and users performing activity from IPs other than 107.23.195.228 and 54.236.224.46 (or other approved internal IPs) in integrated data sources and services including databases and cloud providers.
- Look for anomalous users or resources created by Sisense integration users.
- Review logs from at least a month back in your Sisense products, connected apps, and connected data sources.
- Review actions performed by integration keys and credentials used for Sisense data integrations.
Sisense’s CISO sent an update to customers with a list of suggested actions (source: @marcwrogers):
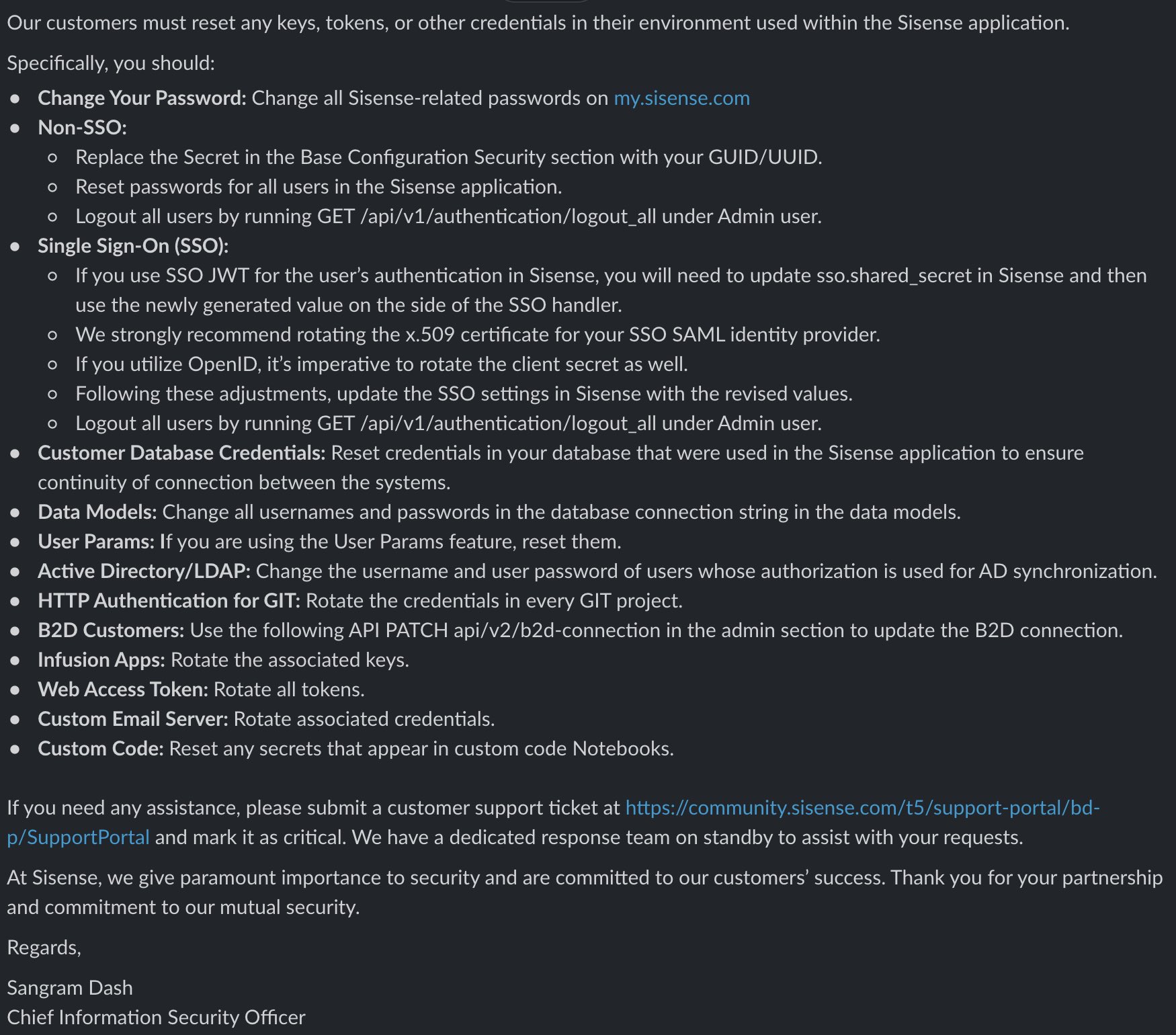
What happened?
There has been no confirmation by Sisense regarding how the breach happened. According to Brian Krebs, trusted sources close to the investigation indicated that the attack flow looked something like this:
- Attacker accessed Sisense’s Gitlab instance
- Found credentials to Sisense’s AWS account in a Gitlab repository
- Accessed Sisense’s AWS account and downloaded multiple terabytes of S3 data including credentials, tokens, and configs
How can Varonis help?
If you are using Varonis to monitor services that are connected to Sisense such as Salesforce, AWS, Azure, Google Workspace, Box, etc., many of our existing threat models will help detect abnormal behavior stemming from malicious use of credentials stored in Sisense:
- Abnormal service account behavior
- Potential ticket harvesting attacks
- Account enumeration
- Abnormal access to sensitive and idle data
- Unusual upload/download activity
These models also apply to customers using Varonis to monitor local resources like Linux servers, Windows machines, and Active Directory.
If you have our network monitoring product and are using Varonis' cloud-hosted offering, our Threat Labs team has already performed a threat hunt, using the Varonis logs to look for communication between your infrastructure and Sisense IP addresses and will reach out if needed.
If you are a Sisense customer and want assistance hunting for IOCs in data sources that are connected to Sisense, please reach out to our team.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.

.png)






