One of the biggest risks in data security is false confidence. When customers participate in a Microsoft 365 and Copilot Data Risk Assessment, Varonis provides a comprehensive view into current risk within the tenant and how to remediate. The result is true confidence.
An example of this conversion from false confidence to true confidence is the “folder fallacy”. The folder fallacy occurs when a share link (public, direct users, or group) is created for a folder at some point, like the one shown here, and the subsequent files inherit the link exposure. With the passing of time, SharePoint admins and users lose sight of this sharing, and this lack of visibility creates data risk.
Common sharing experience with a SharePoint folder, allowing anyone with a link to edit
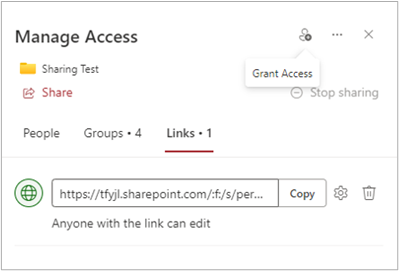
Common sharing experience with a SharePoint folder, allowing anyone with a link to edit
The Folder Fallacy - A Common Scenario
This often occurs during a project with an outside stakeholder or vendor. A project starts, and the folder is shared with a certain group or externally with “Anyone with the link can edit”. Then, at some later point, a SharePoint admin or user may look at an individual file or set of files to view sharing exposure and see a message similar to below.
Example of general user notification in SharePoint for file inherited folder access and potential exposure
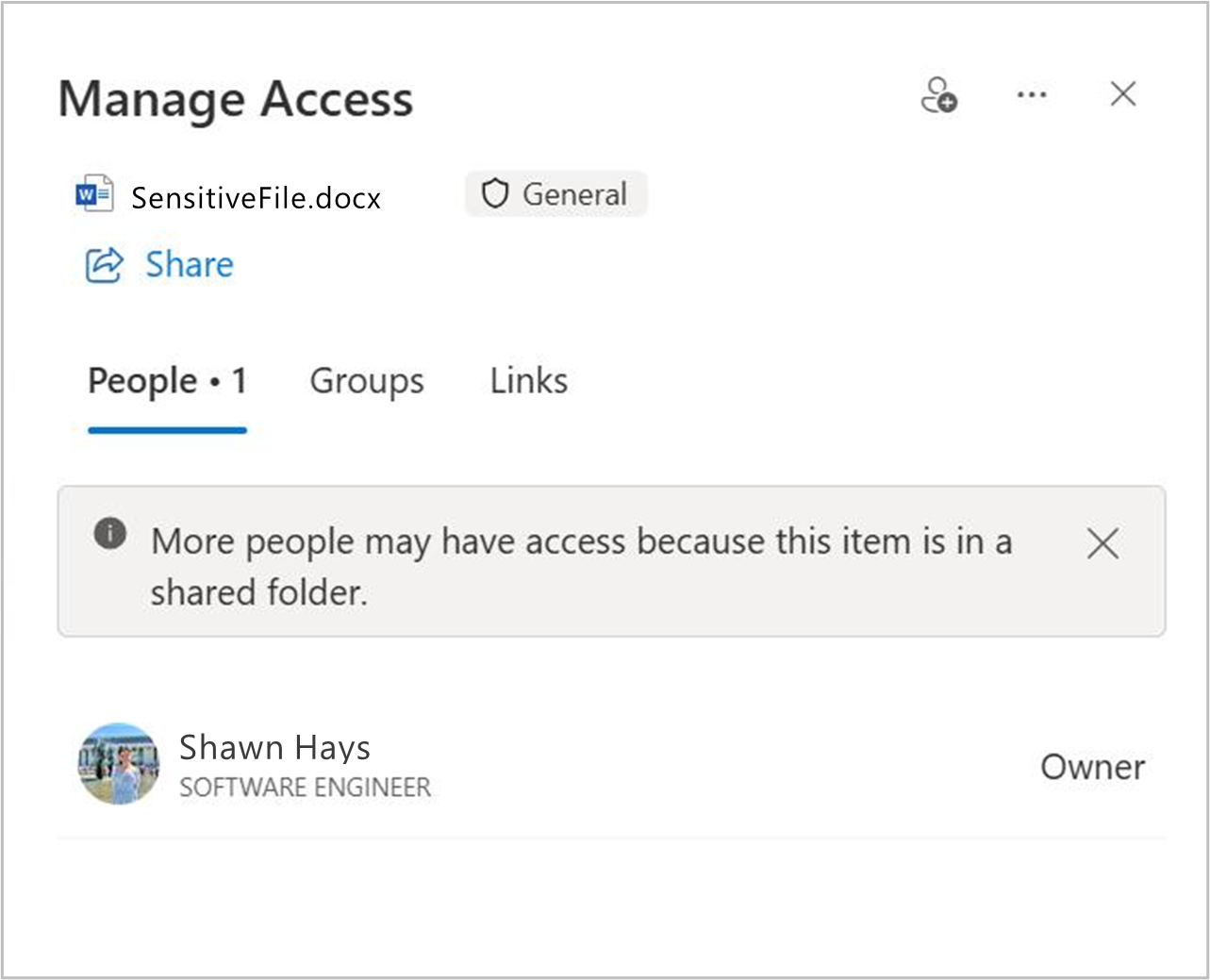
Example of general user notification in SharePoint for file inherited folder access and potential exposure
A nondescript warning is provided to the user that "More people may have access", and the user is left to guess if the file has been shared internally with anyone in the organization, everyone in the organization, or everyone with the link and public access. This ambiguity may lead to false confidence that the file is not shared with anyone or large audiences. Limited visibility also persists in the SharePoint admin center, where, again, the files within the shared folder may not display as publicly shared with link access.
Visibility into Risk
To combat this disconnect and potential blind spot, Varonis can establish true confidence that all public sharing is discovered and addressed. The shown file was never explicitly shared or visualized in the SharePoint admin center as shared, yet Varonis can see the ‘Anyone’ or ‘Organization-wide’ exposure and create an automated data protection policy to remove the access on the parent folder.
Varonis enhanced visibility into SharePoint file exposure due to inherited and unrecognized risks
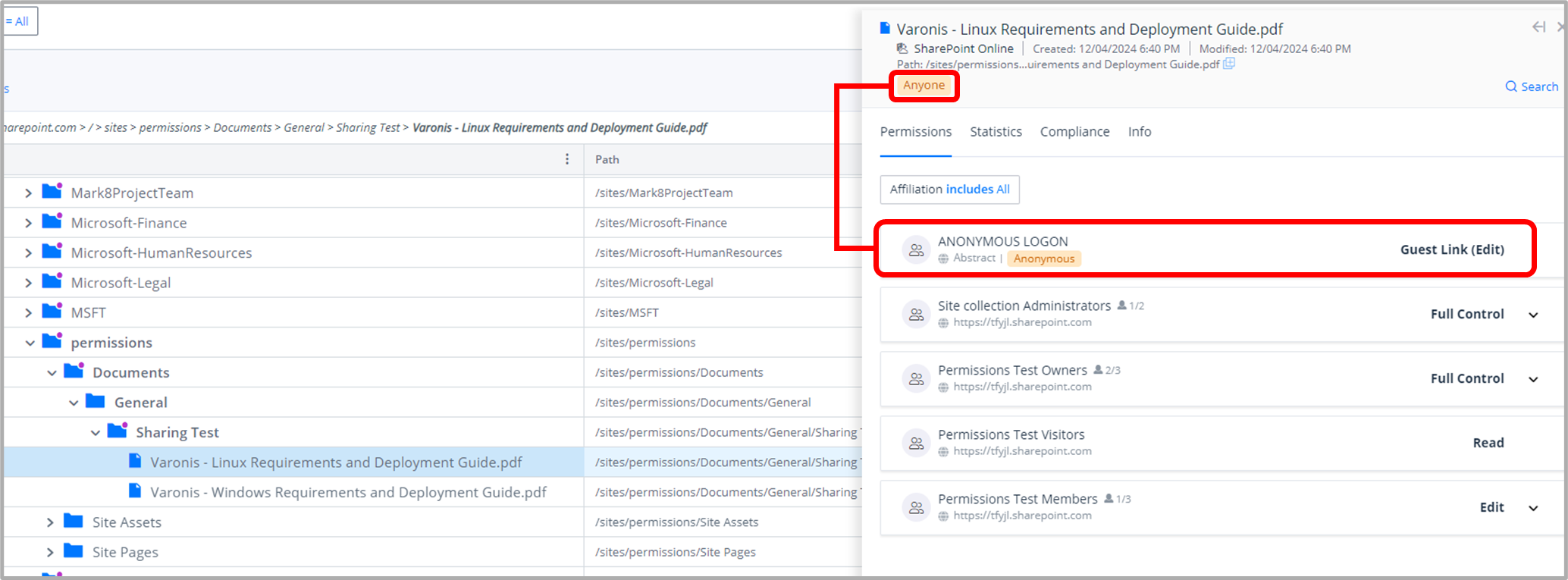
Varonis enhanced visibility into SharePoint file exposure due to inherited and unrecognized risks
Other native solutions can also provide reviews and reports that provide details about sharing links down to the file level from the top 100 sites and the past 28 days from the initiation of the report. Any files within that criteria will be displayed in these reports, including those effected by this ‘folder fallacy’ or other unknown misconfigurations. Then a user can address each access risks file by file.
Three Keys to Modern SharePoint Data Security
- Automation: Unfortunately, time is not on our side, and security teams struggle to address all the risks in their Microsoft 365 environment, let alone the other resources in their data estate. It is difficult to maintain a regular review cycle for exposed links and resources in SharePoint, along with privileged access and entitlements. Organizations desire an automated way to mitigate these risks and others.
Two of the three organizations with the highest marks for their Strength of Offering in the 2025 Forrester Wave: Data Security Platforms have automation as a core component. This most recent Wave analysis and scoring validates what’s seen in other Forrester reports over the last year. One example report focused on building a Cloud Governance Framework stated that “manual policy checks won’t scale and are prone to human error... a good cloud governance framework performs automated audits for rules compliance and uses tooling to flag and remediate any drift.” - Precision at Scale: For many organizations, there’s not a one-size-fits-all approach to managing permissions and access in SharePoint. Unilateral blocking, restricting, or hiding of entire SharePoint sites can be non-conducive to collaboration. Additionally, this approach has been known to cause latency and long wait times for search results, along with deprecating the value of AI agents and solutions like Microsoft 365 Copilot.
Security and governance teams desire a data security approach and platform to enable proper access without compromising the productivity of users. Varonis combines AI classification and sophisticated pattern-matching techniques to produce precise results at scale. This industry-leading accuracy drives intelligent permissions and labeling to folders and files, giving access to the right users where they need it. - Data and Identity Together: Often teams may limit users’ ability to share or create sharing links that are accessible to users outside specified groups (i.e. the Entra security group or Microsoft 365 group “HR Managers”). Individuals could still see the files in search results if they have direct permissions but wouldn’t be able to open the file if they were not in that group.
Managing group memberships and monitoring identities can be effective, though often incomplete. The Varonis Data Security Platform addresses these gaps by detecting outdated users and groups with access to sensitive data. It also identifies unusual behavior to revoke permissions.
Addressing the "folder fallacy" is crucial for maintaining data security in SharePoint environments. By leveraging Varonis' capabilities, organizations can transform false confidence into true confidence by ensuring all public sharing is discovered and remediated. Automation and precision at scale are key to managing permissions and access without compromising productivity. Ultimately, a robust data security approach enables proper access while safeguarding sensitive information.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.








