Shadow databases, like shadow IT, often fly under the radar, unnoticed by security teams. With Varonis’ industry-leading DSPM capabilities, security teams can not only discover shadow databases, but also backups, dumps, and orphaned snapshots. They can then use Varonis to automatically identify if these resources contain sensitive data and quickly see where they are exposed to risk.
Managing unmanaged databases
It’s relatively simple to spin up an unmanaged database on an AWS EC2 instance, but often, these databases are created without the knowledge of security teams.
Because security teams are unaware these databases exist, let alone whether they contain sensitive data or are correctly configured, they create an unnecessarily large attack surface for bad actors to exploit.
With Varonis, security teams can:
- Discover shadow databases across AWS environments
- Classify sensitive data stored in EBS Volumes, unmanaged databases, and snapshots
- Surface orphaned snapshots
- Identify backups and dumps stored in S3 buckets and link them to the relevant database
In this blog, find out how Varonis’ new update enables security teams to discover shadow databases and identify where they expose sensitive data.
Uncover shadow databases.
With Varonis, customers can scan their AWS elastic block store (EBS) volumes to identify where they are attached to EC2 instances running unmanaged database services, such as MySQL, PostgreSQL, and Oracle.
Once scanned, customers can see all their databases, including unmanaged shadow databases, from a single management console.
Get an overview of the databases in your environment from a single console.
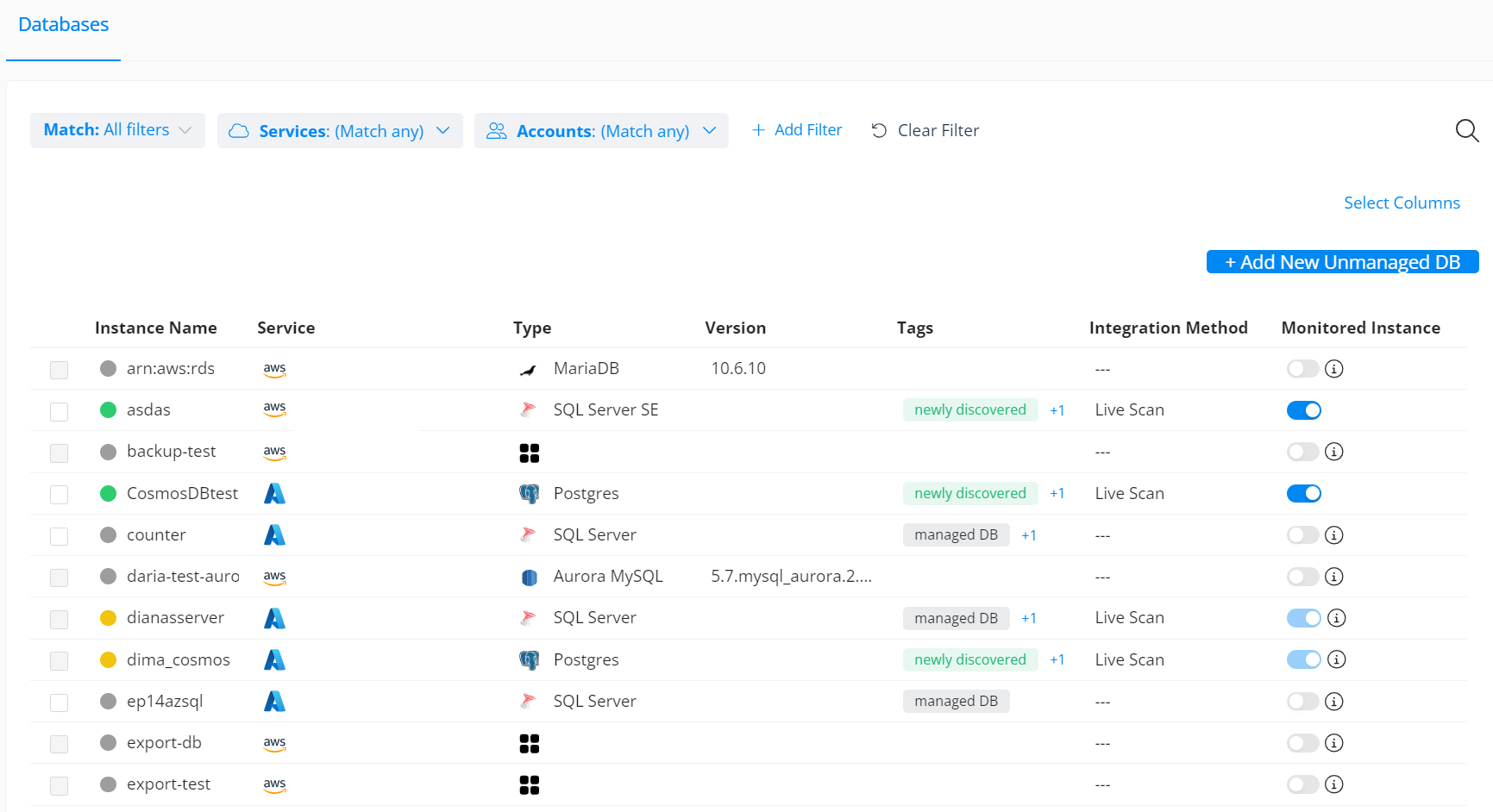
Get an overview of the databases in your environment from a single console.
Discover and classify sensitive data.
Varonis scans the shadow databases and orphaned snapshots it discovers – down to individual columns – to find and classify sensitive data, such as personal information, financial data, health records, and intellectual property.
Review the classification results from your Varonis environment to understand the exact types, concentrations, and locations of sensitive data you have. These results can be used to decide which databases should be monitored or removed from the environment.
Review classification results of shadow databases with an intuitive interface.
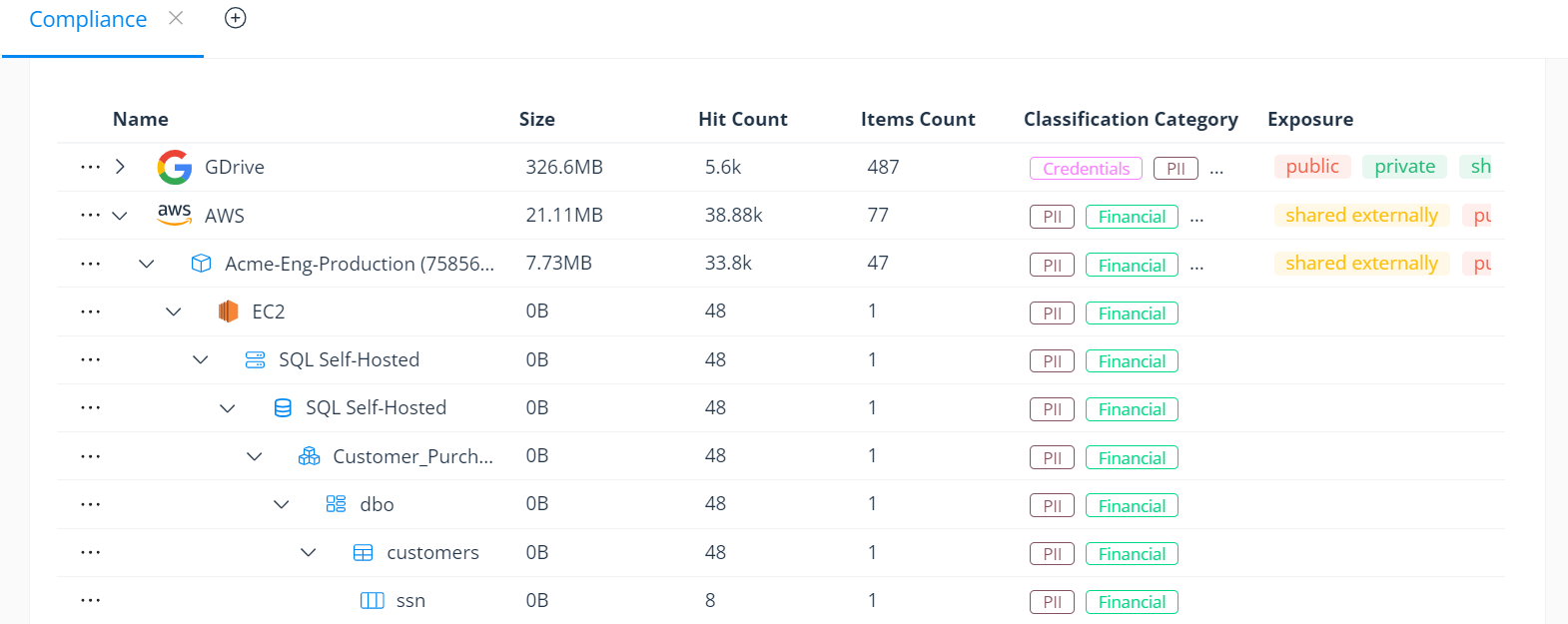
Review classification results of shadow databases with an intuitive interface.
Connect backups and dumps to databases.
Like shadow databases, database backups and dumps in S3 buckets containing sensitive data can fly under the radar of IT and security teams. These backups and dumps may contain outdated or unencrypted data that could be exposed to unauthorized access or leakage.
Varonis can discover database backups and dumps that are stored in S3 buckets. Once discovered, Varonis classifies any sensitive data within, analyzes for exposure, and connects the backups and dumps to the relevant database.
Surface sensitive database backups and dumps in S3 buckets.
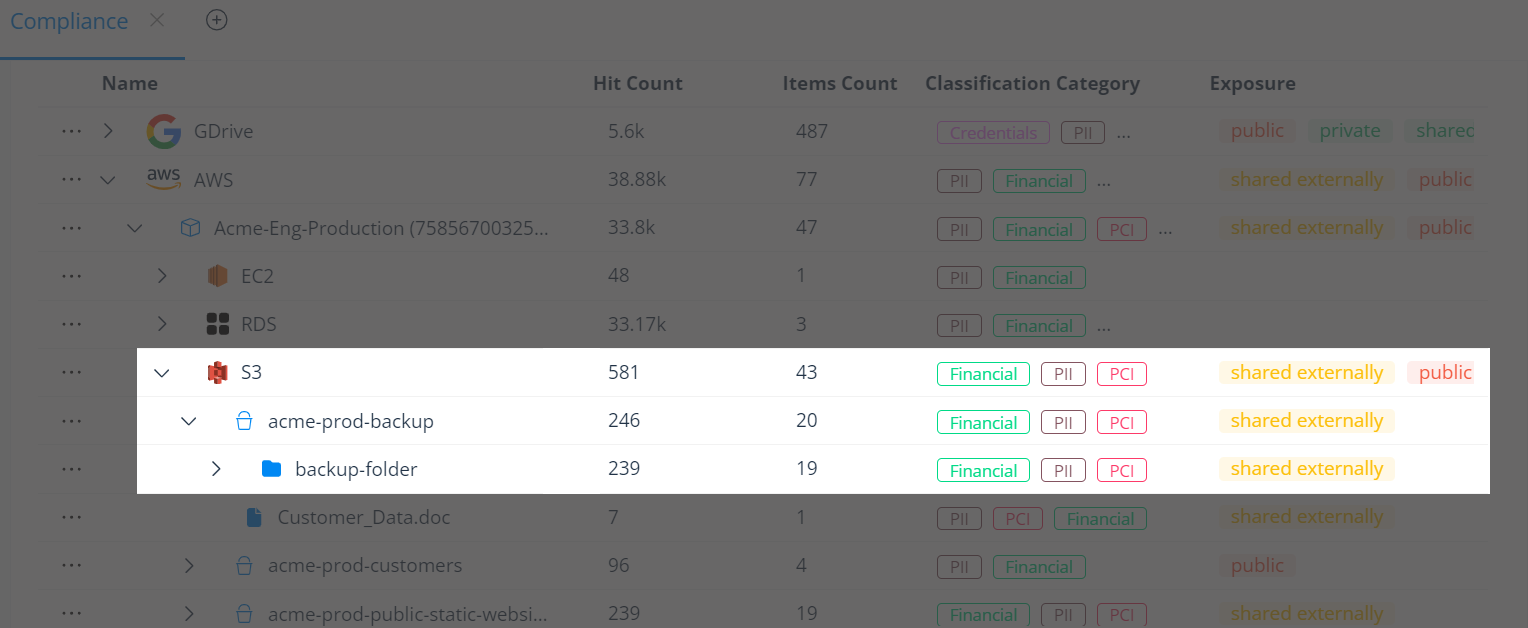
Surface sensitive database backups and dumps in S3 buckets.
Varonis will also alert customers of these backups, identify misconfigurations, and provide recommendations on securing them in case manual remediation is necessary.
Varonis can automatically fix misconfigurations and remediate public exposure — removing the manual effort needed to reduce sensitive data exposure and improve your data security posture.
Orphaned snapshot discovery.
Snapshots serve as a record of database history, which can help with reporting and recovery in case of a disaster. But if snapshots aren’t appropriately linked to databases, they can pose unnecessary risk. For example, if you deleted a database but didn’t find and remove every associated snapshot, all that data could still be accessible.
Varonis can discover every orphaned snapshot in your environment and identify whether it contains sensitive data. This enables IT and security teams to prioritize remediation efforts and ensure any orphaned snapshots are deleted or secured.
Discover and classify orphaned snapshots in your environment.
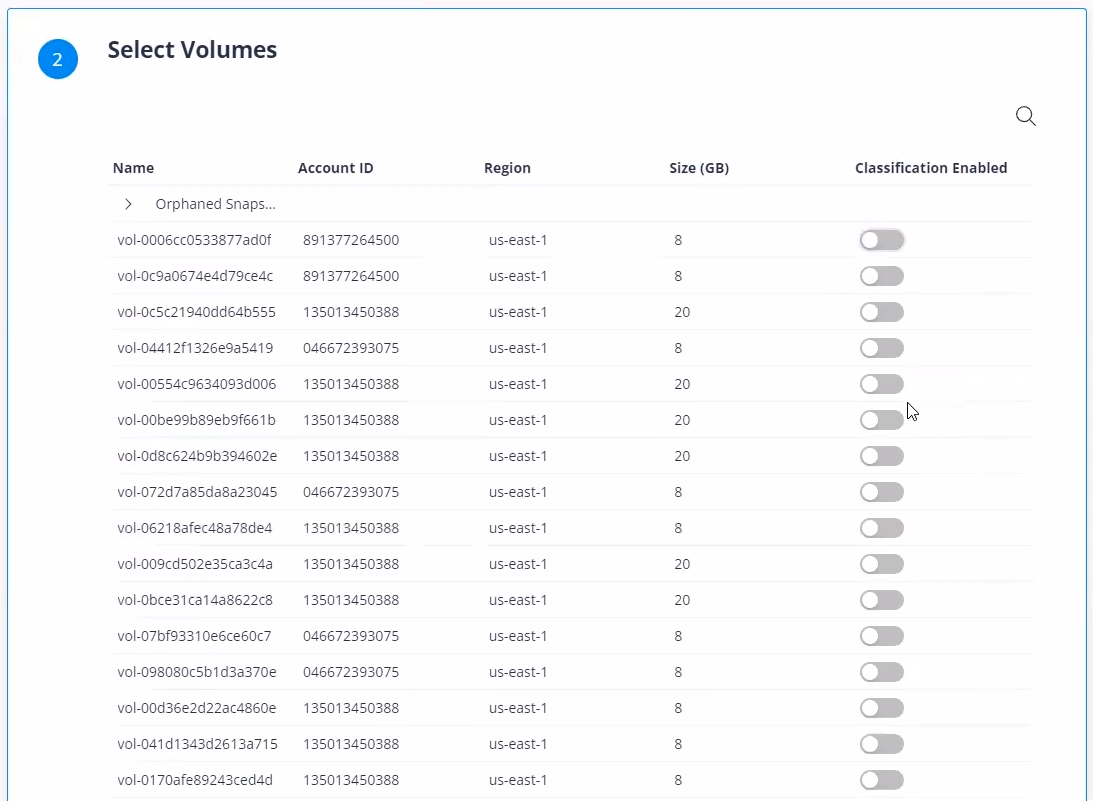
Discover and classify orphaned snapshots in your environment.
Try Varonis for free.
Available on the AWS Marketplace, the Varonis Data Security Platform helps security teams continuously monitor and improve their data security posture in real time with the ability to:- Access a centralized overview of their security posture with customizable DSPM dashboards
- Discover and classify sensitive data stored across structured and unstructured resources
- Identify where sensitive data is exposed, using automation to help enforce least privilege access
- Monitor sensitive data activity and alert you to abnormal behavior
- Maintain a historical, enriched, and human-readable cross-cloud audit trail to facilitate investigations
- Continuously surface misconfigurations, identify configuration drift, and automatically fix issues
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.