Varonis now integrates with leading EDR providers Microsoft Defender for Endpoint and SentinelOne, expanding our Managed Data Detection and Response (MDDR) visibility to customers’ endpoints.
By integrating with Microsoft Defender for Endpoint and SentinelOne, Varonis MDDR analysts can automatically access a live feed of our customers' EDR alerts and related telemetry directly within the Varonis platform. As a result, our incident responders and forensic analysts detect even more attacks and perform end-to-end investigations with little to no customer or third-party involvement.
Varonis’ new EDR integrations give customers:
- Earlier threat detection: MDDR analysts use EDR alerts to identify and stop threats earlier in the kill chain.
- Swifter and more conclusive investigations: Varonis consolidates telemetry from multiple detection surfaces — data, cloud, identity, network, and endpoint — into a single view for fast and conclusive forensics.
- Higher ROI on EDR tools: By correlating EDR alerts with Varonis' unique data-centric alerts, MDDR analysts spot threats that could go unnoticed in isolation.
How Varonis MDDR uses EDR telemetry
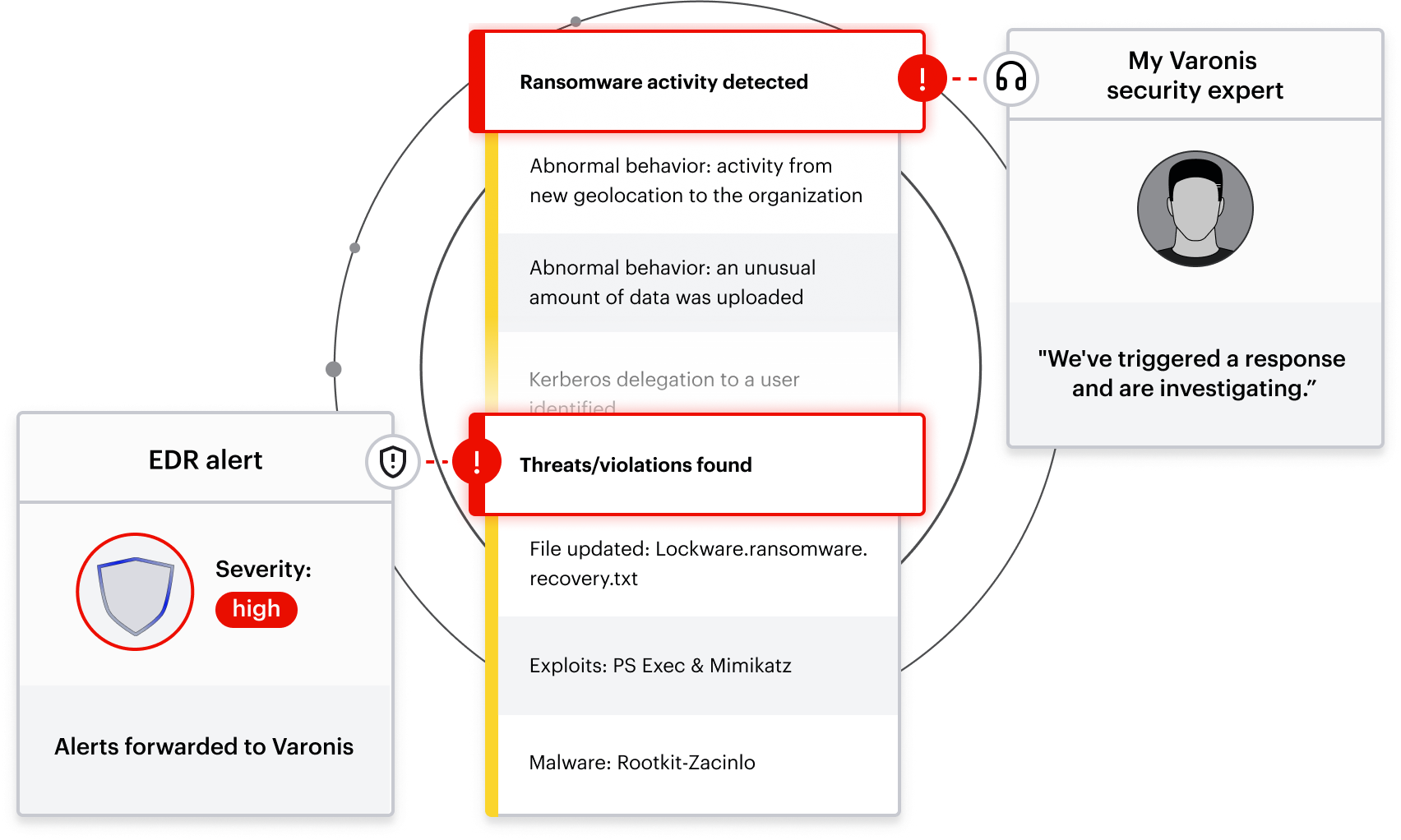
When the Varonis MDDR team receives an alert that a threat requires attention, an MDDR analyst reviews all relevant data about the alert, including the EDR information. With the additional context provided by the EDR integrations, Varonis can detect, investigate, and respond to threats such as:
- Compromised identities: Identify compromised endpoints that serve as attack vectors by collecting malware indicators, unique identifiers, or a machine’s location.
- Ransomware: Stop ransomware attacks faster by confirming the infection with indicators of compromise (IOCs) such as command line activity or registry key file changes.
- Advanced data exfiltration: Detect exfiltration attempts faster by correlating cloud activity with endpoint details such as IP addresses, DNS records, operating systems, and machine types.
- Advanced persistent threats (APTs): Pinpoint the source of intrusions detected by MDDR using EDR alert details such as the alert origin, time, and severity.
Try Varonis for free.
Integrating Varonis with SentinelOne and Microsoft Defender for Endpoint is quick and secure. Varonis analysts will immediately begin to use the EDR telemetry to help protect your sensitive data.
Ready to see how Varonis MDDR can help secure your sensitive data 24x7x365? Contact your Varonis representative or see Varonis in action by scheduling your 30-minute demo.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.