Salesforce is often home to your organization's most sensitive data, and while the CRM tool does a lot of the heavy lifting to keep your information secure, companies often forget it’s a shared responsibility to combat cyber threats; in-house security teams and Salesforce admins are also responsible for protecting company data. This includes who has access, how users can access data, and continually monitoring access and activity to data.
As threats evolve, it’s important to know what security risks are most concerning today.
Ryan O’Boyle, Senior Manager of Cloud Architecture and Operations at Varonis, and Christine Marshall, Courses and Community Director at Salesforce Ben, exposed the biggest security risks to your Salesforce org and shared insights into how companies can protect their sensitive data.
The most concerning risks they identified include:
- Data exposure resulting from complex permission models
- Sensitive data living where it doesn’t belong
- API connections that leak information
- Misconfigurations that can expose data publicly
- A disconnect between Salesforce admins and their security teams (CISOs, CIOs, etc.)
Throughout this blog, we’ll highlight how Salesforce professionals and security teams can combat the most concerning risks in Salesforce environments.
Clean up Profiles and Permission Sets.
Salesforce users have stated that the management of profiles within the application can be very complicated. To improve the experience, Salesforce plans to retire permissions on profiles by 2026.
Preparing for this change now will ensure your Salesforce environment is set up for success when the changes take effect and that your data is protected.
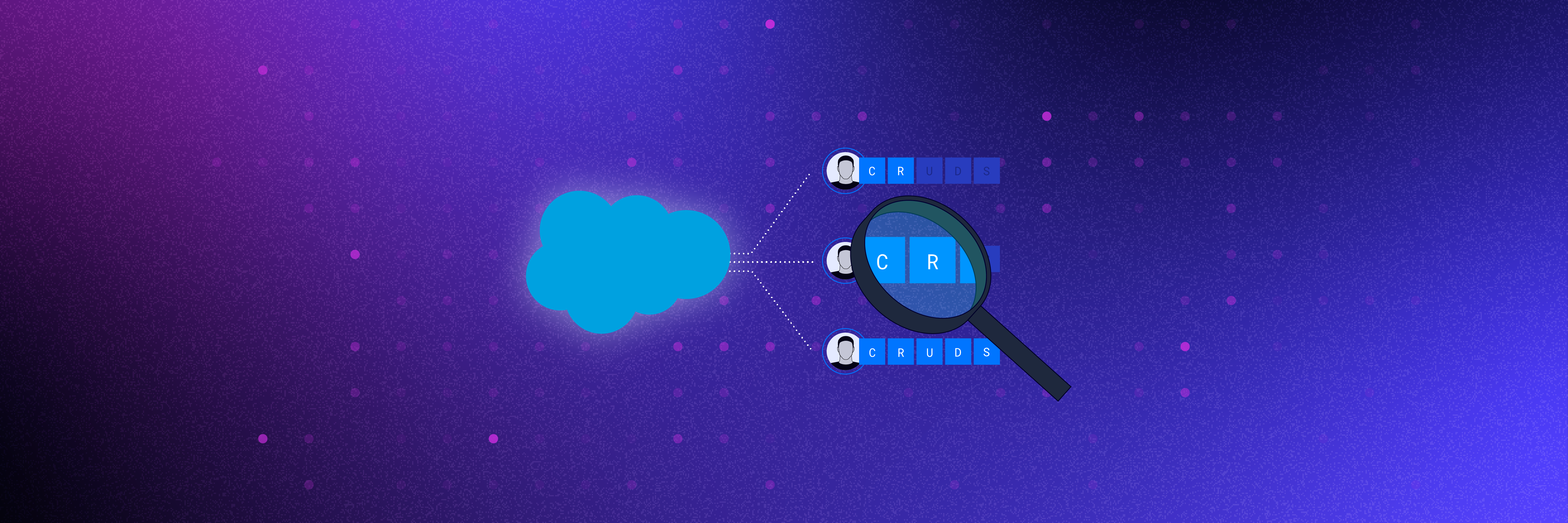
Ryan recommended starting with a baseline of what permissions exist within your profiles and understanding what users can access, converting needed permissions to permission set groups, and then cleaning up left-behind profiles that are stale and unused.
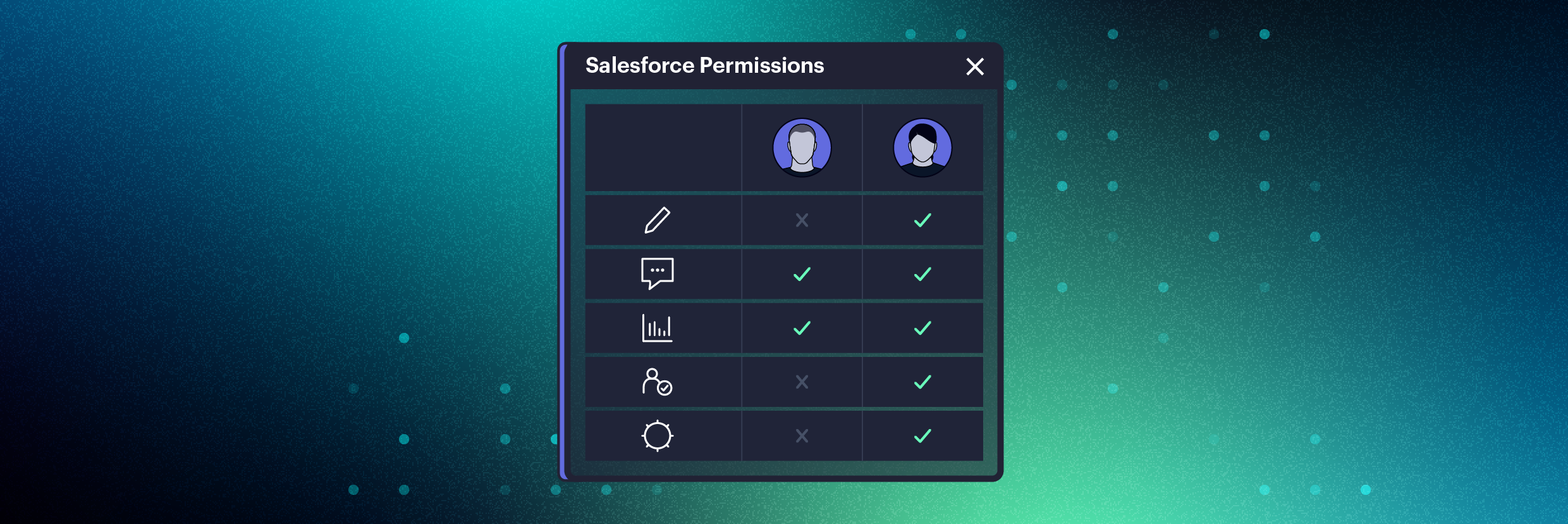
 Varonis simplifies permissions analysis, showing you not only what someone’s effective permissions are but also how they got them — down to the object and field level. In this example, Melissa Donovan can export reports due to her Account Exec profile permissions.
Varonis simplifies permissions analysis, showing you not only what someone’s effective permissions are but also how they got them — down to the object and field level. In this example, Melissa Donovan can export reports due to her Account Exec profile permissions.
“The long-term goal here is increased security and better usability. A more consolidated permission model will help organizations get to a least privilege model and ensure that only the right users in the organization have the right access to the right data sets in the right areas of the environment,” Ryan said.
Christine added that now is a great time to start going through documentation, if available, on why certain profile permissions exist while auditing your processes. By getting ahead of the game, you are limiting the technical debt from your Salesforce environment from increasing.
Read More: 10 Tips to Payback Your Salesforce Technical Debt
“Figure out why you have certain profiles and what they are for, and then start trimming them down and thinking about what could be moved to permission sets, where you’ve got duplicates or unused profiles, and why something was set up. Start doing that recon work now, because it’s going to make it easier for you going forward,” Christine said.
Risks involved with third-party applications
Another area for security teams and admins to analyze and audit is any third-party applications connected to your Salesforce environment.
Whether it be in a sandbox environment or adding an integration, third-party applications are often connected to a Salesforce organization without oversight from the security team, which leads to a lack of communication and visibility into what apps are connected, who uses the apps, and the access these apps could have to your information.
We implement great security policies around our own personal devices, but unfortunately, sometimes we forget to implement those in our corporate environments as well.
In her role at Salesforce Ben, Christine has seen administrators grant third-party applications system admin access, which gives the apps a wide array of access to your Salesforce org and the data residing within.
Ryan and Christine both recommend security teams and Salesforce administrators work together to audit their existing third-party app inventory, reevaluate the access they need, and remove apps that are no longer being used.
She adds that most Salesforce users don’t come from a security background and may not be aware of the implications of their decisions.
“As Salesforce professionals, we need to start building security into our day-to-day job,” Christine said. “These are the things that you should be doing in the same way that you use the health check tool or optimizer; we need to start doing that for the third-party apps as well. Build in that review and be proactive, because so many security issues are reactive, and by then, it's typically too late.”
Being proactive should include running risk assessments of your Salesforce environment weekly, monthly, or quarterly to understand what apps have access to data within the environment and how they obtained access.

Audit which apps are inactive, high-risk, or unverified. In this example, several apps are stale and can be removed because they can access sensitive data.
Locate and remove shadow data in community sites.
In recent years, there's been a push toward being digital first and allowing customers to access self-service support, making Salesforce communities and experience sites rise in popularity. Salesforce communities are a great way to share FAQs, knowledge articles, sales and marketing material, and more.
However, the risk of these community sites exposing data is high, and it’s important for organizations to understand how the permissions of these sites are configured from the data perspective.
One of the ways data can be exposed on these sites is through misconfigured permissions. Somebody uploads a file that gets attached to a record that then ties it into a community site, which then exposes sensitive data to the entire organization, or in some cases, the entire internet.
In addition to misconfigured permissions, our team at Varonis also discovered community sites that were essentially deactivated from a business perspective but hadn’t been deactivated on Salesforce. These abandoned communities, which Varonis Threat Labs dubbed “ghost sites,” still have connections to your environment and the data within them, increasing the possibility of it getting into the wrong hands.
This vulnerability is not a bug or technical issue on the Salesforce side, it's a pure configuration issue when it comes to the permissions within the org itself and can be avoided with proper security reviews of your Salesforce org.
Salesforce link exposure
Some organizations are familiar with sharing links in Microsoft 365 or Google, but did you know that this functionality also exists in Salesforce?
The setting can be enabled within your Salesforce orgs and allow end users to share files and attachments on records through a public URL.
There are some great security measures that can be implemented, but most Salesforce users aren't aware the share settings have been turned on in the first place and that further steps need to be taken.
“The truth of the matter is, unfortunately, many folks don't realize that the settings have even been turned on in the environment or how many users can access or even create these public links,” Ryan said. “This is a big one that we're seeing trending, and it would definitely encourage everybody out there to take a quick look at who can create public links across their Salesforce.”
Be proactive with your Salesforce security.
Even though the risks covered in this blog may differ, one aspect remains constant: Organizations need to dedicate time and create formal security processes to keep their Salesforce environments secure.
Salesforce does so much for us, but the security of our data is our responsibility. I think now is a great opportunity for Salesforce professionals to educate their companies on their role and what it encompasses, and to remind them that things need to be done.
Christine and Ryan both acknowledge that starting with a risk assessment is a great way to gain visibility into the security concerns in your organization. Varonis offers a free risk assessment that gives you concrete steps to prioritize and fix major security risks and compliance issues in your data.
“One of the things that we strive to achieve is making the risk assessment simple and helping make your lives easier when it comes to locking down the data, potential misconfigurations, and integrations, and ensuring that you’re at the highest security posture possible,” Ryan said. “It’s something that you can use internally to educate others within the organization and help increase the efficiency of your team.”
Watch the full session with Ryan and Christine to dive deeper into the security risks to your environment and discover how Varonis for Salesforce can help protect your data.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.
-1.png)