Data breaches exposed 36 billion records in the first half of 2020. This number continues to increase as more businesses go online, with more knowledge workers working remotely in 2021. As a result, the average organizational spending on cloud and data security measures to protect customer data has also increased tremendously.
If Salesforce is your CRM of choice it’s natural that you’ll want to protect it as it stores not just your customer data, but vital prospect lists, pricing and discounting info, sales pipeline, and often sensitive information shared under an NDA.
- Salesforce Security: The Basics
- Salesforce Data Security: Best Practices
- Salesforce App Development: Best Practices
- Salesforce API and Communities: Best Practices
- Salesforce Security: An Evolving Pursuit
Salesforce Security: The Basics

The Salesforce platform provides the most comprehensive set of controls to secure your Salesforce org, starting with the ability to identify security vulnerabilities across your org, all the way to advanced auditing and encryption features to bolster your implementation. Let’s have a look at these features.
Get a Free Data Risk Assessment
Salesforce Health Check
Salesforce enables you to identify potential security vulnerabilities in your Salesforce org instance through a comprehensive health check utility called Salesforce Health Check. You could run the check as a predetermined Salesforce Baseline or customize it to be as stringent as needed. The assessment would assign a score and provide a detailed rundown of all the settings that you might need to review and remediate as required.
Phishing and Malware
As one of the biggest global SaaS platforms, the Salesforce platform provides a transparent and real-time view on its uptime and security measures on Salesforce Trust. This site offers a slew of practical measures which your Salesforce org can adopt for thwarting phishing and malware attempts, including:
Multi-Factor Authentication (MFA)
Add an extra layer of security to Salesforce user accounts. Salesforce intends to make MFA mandatory for all accounts starting February 1, 2022.
IP Ranges and Session Restrictions
Salesforce enables you to restrict your users to access your org instance only from your corporate network or VPN using IP range restrictions. Use this feature to set up defined hours for usage and session-specific settings for logged-in users, including a high-assurance level of security for sensitive operations like managing certificates, and auth providers.
Salesforce Shield
Suppose you are looking to extend your security threshold and go beyond the standard security measures provided by Salesforce. In that case, you could upgrade to an additional layer of security to strengthen organization-level access with Salesforce Shield. Salesforce Shield consists of 3 main features:
Shield Platform Encryption
Shield Platform Encryption extends on the Classic Encryption standard to 256-bit AES encryption. Use this feature for different encryption schemes depending on your use case and process encrypted data on standard and custom fields.
Event Monitoring
Event Monitoring can track multiple event types within the Salesforce ecosystem and allows you to view, filter, and download event logs through a web app called the Event Log File (ELF) Browser. You could use cURL or Python to sift through the event data or use your monitoring system of choice like Splunk to visualize this data.
Field Audit Trail
Use Field Audit Trail to realize stringent audit requirements for your Salesforce org by tracking a wide variety of standard and custom objects.
You could implement every Salesforce Shield feature with confidence by learning step-by-step on the Shield Learning Map page. We have also curated all the resources you need on this topic in our comprehensive guide to Salesforce Shield.
Salesforce Data Security: Best Practices
The data security model in Salesforce helps you secure data at multiple levels from an org perspective down to an individual record. Using this model provides you the ability to secure the organization data at four levels, namely:
Organization Level Security
Use Org Level security measures like Trusted IP ranges and Salesforce Shield as mentioned above to set up organization-wide security policies.
Object Level Security
Use Profiles on your Salesforce org to enforce access privileges on the object level for a given domain or by provisioning specific accounts on a given profile.
Field Level Security
Use field-level security on a given object to restrict specific fields within particular screens and reports to hide or provide read/write permissions.
Record Level Security
Use Record level security in Salesforce to customize access and share records for each profile depending on specific roles and criteria.
We have curated all the resources you would need to enforce the data security model in your Salesforce org with our guide to Salesforce Data Protection.
Salesforce App Development: Best Practices
The power of the Salesforce platform is enabled by its custom app development capabilities to create Apex and Visualforce pages on its Lightning Platform. But as with all things with great power also comes the responsibility to secure the app and minimize exposure to security risks. There are several aspects that app developers need to be aware of, namely:
Cross-Site Scripting (XSS)
In this scenario, apps using dynamic web page content could potentially open up users to compromise their interactions to security attackers, who can take control of their session and execute malicious code. In addition, XSS requires no authentication and no user action, which makes the app genuinely vulnerable.
Salesforce provides development guidelines to restrict such scenarios during app development in this Visualforce developer guide.
Cross-Site Request Forgery (CSRF)
In this scenario, apps using dynamic web page content can be compromised by attackers, who could then incite a user to perform unintended actions to enable their malicious motives. The primary difference between XSS and CSRF is that the user in a CSRF performs one or multiple actions in this scenario, limiting the damage to the extent of the actions performed. In XSS, in contrast, the user is entirely unaware an attack is occurring.
Salesforce protects against such scenarios by implementing an anti-CSRF token and prevents any script execution until the token is validated every time. All developers looking to safeguard their code in these scenarios should pay attention to these Visualforce guidelines for CSRF.
SOQL Injection
Salesforce implements its database query language in Apex, known as SOQL. The security measures to protect query injection in SOQL are also similar in SQL scenarios. An attacker can modify unvalidated user input in SOQL queries for malicious intent. Hence Apex developers trying to secure their code against SOQL attacks should implement the defense mechanisms explained in these Visualforce guidelines for SOQL Injection.
Salesforce API and Communities: Best Practices
The Salesforce platform is flexible in its ability to open its functionality for developers and social communities alike. This flexibility could also open up possibilities to multiple security incidents outside a well-secured Salesforce instance. Fortunately, Salesforce provides guidelines to secure these external sources as below.
API and Communities Access
- Enable permissions only for specific roles and enforce these permissions as ‘API only’
- Allow only read access unless necessary and enforce password-level policies and location-specific restrictions as with other roles in your Salesforce org
- Whitelist apps on a case-to-case basis and review periodically to revoke access to dormant apps
- Allow users on the least level of privilege and selectively grant higher privileges on a case-to-case basis
- Enforce authenticated access on your communities if possible
Salesforce Security: An Evolving Pursuit
In the words of Louis Pasteur, fortune favors the prepared mind. The Salesforce platform arms you at each level to protect your org instance from security incidents of every nature. Though, like most cloud platforms, Salesforce also adheres to a shared security responsibility model. It is important to understand which security tasks are handled by the CRM and which tasks are handled by you. How you prepare yourself with all these tools and guidelines is your prerogative. Security is hardly a one-and-done event – it requires an evolving pursuit of understanding the state of your current org and pre-empting an incident at each level. Consider setting aside time to put these utilities provided by the platform to work and assessing your org readiness every month. You will find peace of mind knowing that your most valuable data is safe and protected.
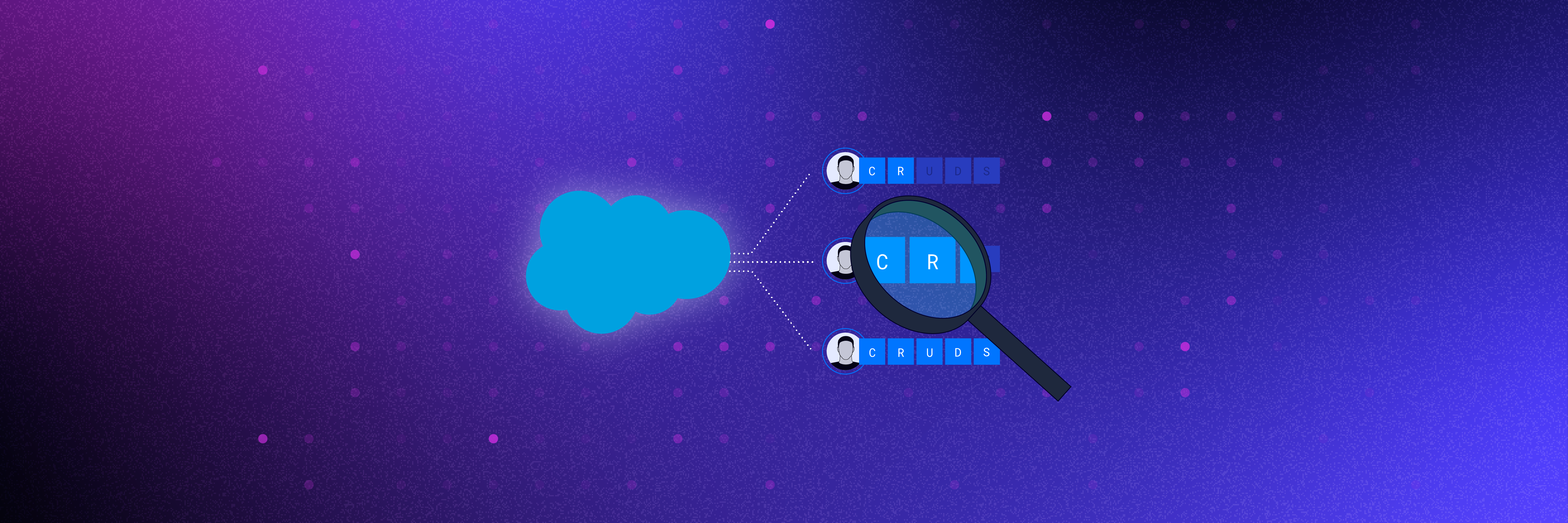
One of Salesforce’s greatest strengths—like many SaaS apps— is its customizability. As organizations adopt these solutions, they often fail to consider the complexity customization can inadvertently introduce into their environments. Most IT and security teams are already stretched thin with many competing priorities. That, combined with the lack of end-to-end visibility and the complexity of the Salesforce permission configurations, could leave your data at risk to potential threats. Native Salesforce security solutions can help organizations start to get a handle on what’s happening with their Salesforce data, but security teams need to be able to do lots of correlation in order to get meaningful insights. Data security solutions, like Varonis, can help security teams answer critical questions about their data.
Varonis DatAdvantage Cloud helps organizations defend their mission-critical Salesforce data. We automatically correlate cross-cloud identities with privileges and activities, helping organizations simplify the complexity of Salesforce permissions and easily visualize where their data is exposed. We monitor for policy violations—like accessing an excessive number of Salesforce records—and other suspicious activity to help you defend against threats.
Want to learn more? Schedule a time to speak with our team.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.