The Varonis Data Security Platform Remote Work Update is here! This update delivers the product enhancements you need right now to keep your data safe in a work-from-home world. In this video, we’ll give you a quick tour of what’s new and outline all the details in the post below.
Visibility and Threat Detection for a Remote Workforce
With more people working from home, cyberattacks are on the rise. Many of you have reached out to our Incident Response Team for help, and we’re going to continue to support you any way we can.
Meanwhile, these new features will help with some of the new threats you’re facing with increased VPN activity, Microsoft Teams / O365 usage, and a lot more. We’re including these features as part of the Data Security Platform version 8, however, many of these updates will be available as patches to version 7, so you can deploy them as quickly as possible.
Let’s get right to the highlights, shall we?
Get a Free Data Risk Assessment
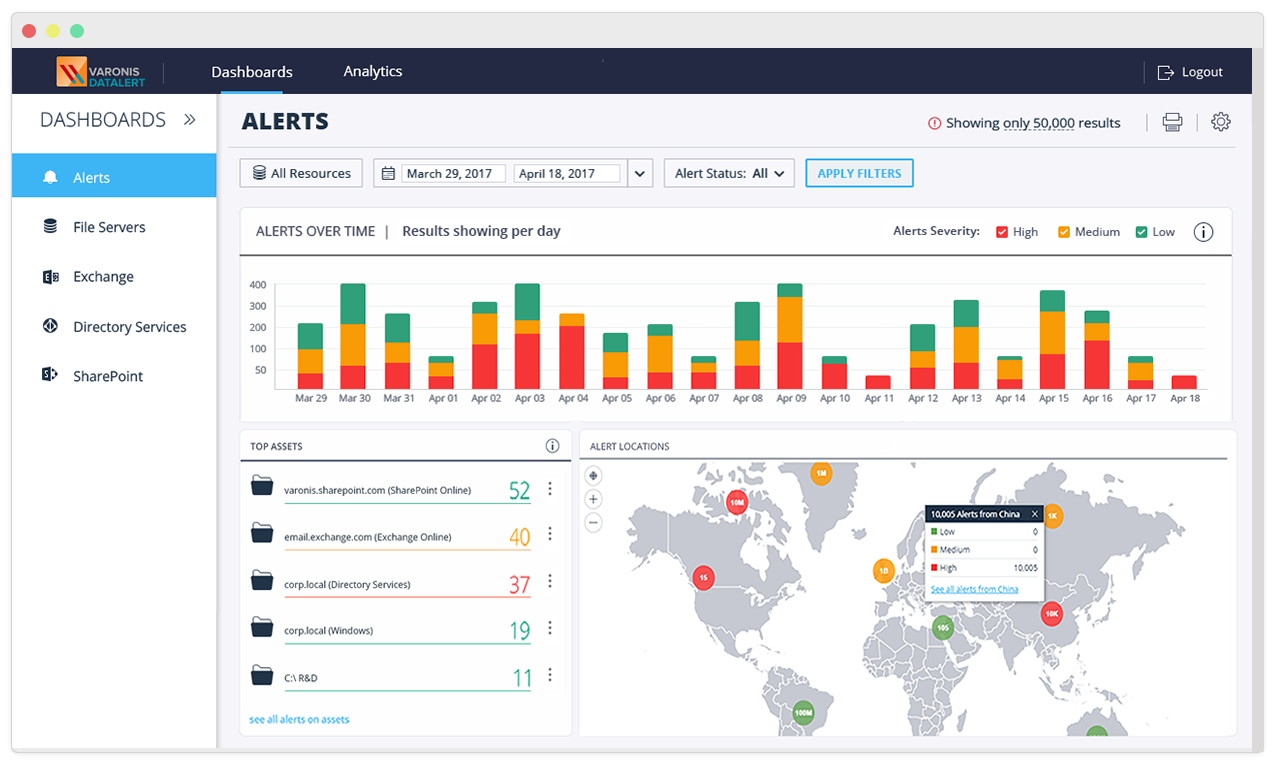
New Dashboard for Real-Time Awareness of Unusual VPN, DNS, and Web Activity
The new Edge dashboard highlights key risk indicators such as:
- Blacklisted Countries with Active VPN Connections
- Privileged Account Access to Low Reputation Domains
- Malicious Domains Accessed in the Past Week
- Service Accounts with Active VPN Connections
These customizable widgets highlight risks to your remote workforce and help security teams track and trend progress as they mitigate critical security gaps.
Built-In Threat Hunting Queries
Our Incident Response and Forensics teams investigated over 650 incidents last year. We’ve taken that real-world experience and made it available to you in the form of out-of-the-box queries to give you a head start on your own investigations.
Some of the new remote work-centric queries include:
- VPN Sessions from Dormant Accounts
- VPN Login from Blacklisted Countries
- Failed VPN logins from disabled accounts
- Successful DNS requests to known-malicious domain
These queries can highlight potential indicators of compromise that haven’t yet progressed to a full-blown alert. There are dozens of new queries available, and of course, you can build and save custom queries as well.
Comprehensive Microsoft Teams Visibility
Microsoft Teams usage has exploded during the 2020 pandemic, but rushed deployments with misconfigured permissions and limited threat monitoring are making hackers salivate. In fact, the U.S. Department of Homeland Security issued an alert about it.
There are countless ways to share data via Teams and answering a simple question like “Which sensitive files have are overexposed?” can be an archeology project with the built-in security tools.
Varonis de-mystifies Teams permissions and shows you how each user can access your Office 365 data. For example, Varonis identifies if a user exists in Azure or if the user is granted access via a sharing link, right in the interface. Clearly see the impact Teams has on your threat surface and get a granular view of who can access data shared through Teams—even if the users are outside of the organization.
Check out our webinar Complexity is the Enemy of Security: Protecting Data at Scale in Office 365 to learn more about how Teams permissions work under the hood and how users can inadvertently expose sensitive data.
Out-of-the-Box Reports that Highlight Exposed Cloud Data
Varonis makes it easy to see where sensitive data may be overexposed. The Remote Work Update adds new reports that show where data is shared with external users or even publicly on the internet so that you can remove excessive sharing links and protect your data.
More Threat Models for Office 365
The number of internet-facing systems increased by 30% since March, and Teams usage jumped 500%, so we added new threat models to detect more attacks against Office 365.
In response, we added new threat models that enable users to combat those new threats. For example, Varonis will detect if a compromised account creates a sharing link to sensitive data, or there is an active brute force attack directed at Azure.
In the Remote Work Update, we added threat models to detect:
- Brute-force attacks against Azure
- SQL injection against Azure
- Successful logins to Azure from blacklisted IP
- Successful authentication using a penetration testing tool
- And many more…
Additional features included in the Remote Work Update
New Platform Support
- New data store support: Nasuni, SharePoint & Exchange 2019, IBM AIX, Dell EMC Unity
- New Edge platform support (Infoblox DNS)
- Automation Engine support for Nasuni
- Data Transport Engine support for Nasuni
Architecture
- Support for 180-day log history in Solr, meaning you can conduct fast investigations on events that are older without taxing the SQL database
DatAlert
- View events in an easy-to-digest list, only showing attributes of the event that contain data (a nice alternative to the column-based view)
- Add/remove watch list users in the web UI
- Change privileged account designation in web UI
- Exclude accounts and devices from triggering certain alerts directly from the web UI
- Automatic updates of DatAlert Threat Dictionaries via Varonis VIPs
- New threat models, including:
- Successful authentication using a penetration tool—triggers when an account has been successfully authenticated using an unusual computer name
- Successful logins by a specific account from multiple IPs—could indicate that an account is compromised and is being used by several attackers
- Configure custom interval for pulling data from Splunk
Edge
- Edge filter for common domains to reduce noise stored in your logs
- Faster deployment time for DNS monitoring
DatAdvantage for Directory Services
- Directory Service metrics can now be added to reports 14d (not just dashboards) Such as No. Admin Accounts with SPN
- Expanded NTLM event collection for analysis and threat detection
DatAdvantage for O365
- Group Type and Group Source attributes in the Work Area UI to help you better understand permissions structure (e.g., is this an Azure AD group or a SPOL group?)
DataPrivilege
- All fields in DataPrivilege, including built-in fields, are customizable (name and description)
- Multi-factor authentication (MFA) support in DataPrivilege
- New “Activation Date” setting on permissions approvals to allow a permission to be granted in the future, not immediately
- Request origin filter for DataPrivilege requests to see if it came from the UI, an entitlement review, the API
Automation Engine
- Built-in token bloat prevention
- Global access group remediation and broken ACL remediation for Nasuni
- Scope detector reports allow users to see the full scope of what’s included in the Automation Engine rules
Data Classification Engine
- Option to skip OCR of PDF files to speed up scans
- Expanded OCR support to include new image file formats
- Error log shows archive files that failed to extract for scanning (e.g., due to anti-virus)
Data Classification Labels
- Labeling of PDF files now supported
- Uses the new Microsoft Information Protection API (vs. old Azure Information Protection API)
DatAnswers
- Ability to copy files for data subject access requests (DSARs) (without needing Data Transport Engine)
- Scale and sizing improvements—we can now hold 120 terabytes of indexed data and index those files 3x faster
Want a more in-depth tour? Sign up for Varonis Virtual Connect on June 3rd, 2020 to join our product team for an in-depth tour of the Remote Work Update.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.