Ransomware is a form of malicious software that infiltrates a computer or network and limits or restricts access to critical data by encrypting files until a ransom is paid. The first use of ransomware dates back to 1989, when floppy disks were high-tech and the price of the ransom was a mere $189.
Ransomware attacks are on the rise and continue to be a disruptive force in the cybersecurity industry, affecting everything from financial institutions to higher education.
Read these top ransomware statistics you should know in 2024, plus tips on how to avoid becoming a victim and how to keep your organization protected.
- Top ransomware statistics
- Recent ransomware statistics
- Ransomware statistics by industry
- Mobile ransomware stats
- Ransomware in cryptocurrency
- The cost of ransomware attacks
- Ransomware trends
- How to prevent ransomware attacks
- Ransomware FAQ
Top ransomware statistics
Ransomware is an ever-growing threat to thousands of organizations and businesses worldwide. Here are the top ransomware statistics you need to be aware of:
- The average ransom in 2024 is $2.73 million, almost an increase of $1 million from 2023. (Sophos)
- 97 percent of organizations whose data had been encrypted got it back. (Sophos)
- Ransomware attacks have risen by 13 percent in the last five years, with an average cost of $1.85 million per incident in 2023. (Astra)
- The average downtime a company experiences after a ransomware attack is 24 days. (Statista)
- In 2021, the largest ransomware payout was made by an insurance company for $40 million, setting a world record (Business Insider). The highest ransomware payment demand ever is $70 million. (NetApp)
- In 2022, organizations around the world detected nearly half a billion ransomware attacks. (Statista, 2023)
- Organizations in the U.S. are the businesses most likely to be affected by ransomware, accounting for 47 percent of attacks in 2023. (AAG)
- 93 percent of ransomware is Windows-based executables. (AAG)
- The most common tactics hackers use to carry out ransomware attacks are email phishing campaigns, RDP vulnerabilities, and software vulnerabilities. (Cybersecurity & Infrastructure Security Agency)
- 59 percent of employers allow their employees to access company applications from unmanaged personal devices. (Bitglass, 2021)
- A survey conducted with 1,263 companies found 80 percent of victims who submitted a ransom payment experienced another attack soon after, and 46 percent got access to their data but most of it was corrupted. (Cybereason, 2021)
- Additionally, 60 percent of survey respondents experienced revenue loss and 53 percent stated their brands were damaged as a result. (Cybereason, 2021)
- 42 percent of companies with cyber insurance policies in place indicated that insurance only covered a small part of the damages resulting from a ransomware attack. (Cybereason, 2021)
- 27 percent of malware breaches involved ransomware in 2023. (Astra)
Recent ransomware statistics
There have been many ransomware attacks in recent years that affected organizations across the globe and their customers. Here are some notable recent ransomware attacks:
- Victims paid more than $1 billion to gangs after ransomware attacks in 2023. (WIRED)
- In 2023, the Clop ransomware group attacked MOVEit Transfer — a secure managed file transfer software — and robbed its customers’ sensitive data, impacting hundreds of organizations and impacting nearly 18 million individuals. (Kolide)
- The City of Oakland, California declared a local state of emergency in February 2023, as it had to shut its IT systems owing to a ransomware attack. (Astra)
- In January 2023, ION Cleared Derivatives suffered a ransomware attack that took its systems offline. These systems help automate the trading lifecycle of financial companies. As a result of the attack, finance companies using ION were forced to confirm trades manually. (AAG)
- Ransomware group BlackCat stole an estimated 1.6TB of sensitive data in 2022 from billion-dollar revenue firm, Swissport. (Astra)
- A series of ransomware attacks were launched against the Costa Rican government in 2022, forcing a national emergency to be declared as critical systems were crippled. (AAG)
- The REvil ransomware group accounted for around 37 percent of all ransomware attacks committed in 2021. (AAG, 2023)
- In May 2021, Colonial Pipelinewas the victim of a ransomware attack that affected the flow of oil across the eastern U.S. (TechTarget)
- In June 2021, meat processing vendor JBS USA was hit by a ransomware attack that reduced the company's ability to package meat products. The company is reported to have paid $11 million in ransom to REvil cyber criminals. (TechTarget)

Industry-specific ransomware stats
Ransomware attacks impact nearly all industries of all sectors and sizes.
- 66 percent of organizations were hit by ransomware in the last year. (Sophos, 2023)
- 13 percent of small and medium businesses experienced a ransomware attack in the past year, and 24 percent of respondents experienced a ransomware attack at least one time ever (Datto, 2023).
- Almost three-quarters of companies say that a ransomware attack would be a death blow, and about 60 percent of respondents felt their organization might be hit by a successful ransomware attack in the next 12 months. (Datto, 2023).
Check out more shocking statistics by industry below.
Healthcare
- From 2020 to 2025, healthcare will spend $125 billion to defend against breaches. (Chief Healthcare Executive, 2023)
- An average of 64.8 percent of healthcare data was restored after paying the ransom. (Health and Human Services, 2022)
- There were over 630 ransomware incidents impacting healthcare worldwide in 2023. (HHS)
- Ransomware attacks targeting healthcare delivery orgs doubled from 2016 to 2021. (Health and Human Services, 2022)
- For the 13th year in a row, the healthcare industry reported the most expensive data breaches, at an average cost of $10.93 million. (IBM)
- In 2020, 560 healthcare facilities were affected by ransomware attacks in 80 separate incidents. (Emsisoft)
Education
- Ransomware attacks targeted the education sector more than any other industry in the last year, with 79 percent of surveyed higher education institutions across the world reporting being hit. (Sophos)
- Of the higher-ed institutions that reported ransomware attacks, 59 percent said it resulted in them losing “a lot of” business and revenue. Around one-fourth, 28 percent, reported smaller losses. (Sophos)
- The average cost of a data breach in 2023 in the education sector was $3.65M. (IBM)
- The median recovery cost in lower education was $750K in 2023. (Sophos)
- Since 2020, 1,681 higher education facilities have been affected by 84 ransomware attacks. (Emsisoft)
- 66 percent of universities lack basic email security configurations. (BlueVoyant)
- 38 percent of analyzed universities in the Cybersecurity in Higher Education Report had unsecured or open database ports. (BlueVoyant)
- In higher education, exploited vulnerabilities (40 percent) were the most common root cause of ransomware attacks, with compromised credentials falling in second place at 37 percent. (Sophos, 2023)
Finance and insurance
- Banking ranks as the No. 1 industry for detected ransomware attacks in 2023. (Trend Micro)
- In 2023, the average cost of a data breach in the financial industry was $5.90 million. (IBM)
- The rate of ransomware attacks in financial services increased from 55 percent in 2022 to 64 percent. (Sophos)
- More than 204,000 people experienced a malicious login attempt to access their banking information in 2021. (HUB Security)
- Exploited vulnerabilities (40 percent) and compromised credentials (23 percent) were the two most common root causes of the most significant ransomware attacks in the financial services sector. (Sophos, 2023)
- Financial services reported the highest encryption level in three years: 81 percent of organizations stated that their data was encrypted. (Sophos, 2023)
- In 2020, 70 percent of the 52 percent of attacks that went after financial institutions came from the Kryptik Trojan malware. (HUB Security)
Government
- Over the past three years, 246 ransomware attacks have struck U.S. government organizations at an estimated cost of $52.88 billion. (Sungard AS, 2021)
- 58 percent of state and local government organizations were hit by ransomware in 2021. (Sophos)
- Between 2018 and October 2022, 330 individual ransomware attacks were carried out against U.S. government organizations, potentially impacting more than 230 million people and costing an estimated $70 billion in downtime alone. (Comparitech)
- State and local government reported one of the highest data encryption rates following ransomware attacks: 72 percent in state and local government vs. 65 percent across sectors. (Sophos)
- Cyber insurance is driving state and local government organizations to improve cyber defenses: 96 percent have upgraded their cyber defenses to secure coverage. (Sophos)
- In August 2022, theCity of Wheat Ridge was attacked by the ALPHV/Black Cat ransomware strain and was instructed to pay $5 million in ransom. (Comparitech)
- In March 2022, Plainfield Town received a ransom demand of $199,000 that officials refused to pay. They did, however, spend $350,000 on restoring systems, nearly double the ransom amount. (Comparitech)
Mobile ransomware statistics
With the increase in dependence on mobile phones, especially with the use of personal mobile devices in the workplace, comes a higher risk of ransomware attacks. Within the workplace, employees are able to access sensitive information from their mobile devices via corporate Wi-Fi and oftentimes unsecured networks.
This leaves the user and their organization with major vulnerabilities. Take a look at the statistics below, along with some Wi-Fi security tips to avoid falling victim to a hacker.
- More than 5.3 billion people use mobile phones worldwide, and over 90 percent of those individuals rely on smart or internet-enabled phones. (Cybertalk)
- In Q1 of 2023 alone, 4,948,522 mobile malware, adware, and riskware attacks were blocked. (Securelist)
- China tops the list as the No. 1 country for mobile malware attacks with 17.7 percent of the share. Other countries with significant shares of attacked users were Syria (15.61 percent) and Iran (14.53 percent). (Securelist)
- 2022 saw the emergence of almost 200,000 new mobile banking trojans, a 100 percent increase from the previous year, and represents the largest upswing in mobile malware development observed in the last six years. (Cyware Social)
- The most common threat to mobile devices was adware: 34.8 percent of all detected threats. (Securelist)
- In 2022, RiskTool accounted for 24.05 percent of mobile malware detected worldwide. Meanwhile, AdWare ranked second with a 24 percent share of all new threats that year. Trojan attacks constituted approximately 15.6 percent of all new mobile malware detected online in the examined period. (Statista)
- There are over 4,000 mobile threat variants and families within the McAfee sample database. (McAfee)
- There are 50 times more malware infections on Android devices than on iOS devices. Android is the mobile platform with the highest malware infection rate, accounting for 47.15 percent of all infected devices, while iOS accounts for under one percent of infections. (DataProt)
Ransomware cryptocurrency stats
Since the start of bitcoin, the world’s first cryptocurrency, transferring money and data has become increasingly efficient. Now, the size of the cryptocurrency space has grown exponentially, with innovations and a collective market capitalization of more than $1.2 trillion. But with this advancement in digital and financial technology, new threats in cybersecurity have come to the surface.
- Crypto payments to ransomware attackers hit $449.1 million in the first half of 2023, up $175.8 million from the same period last year. (Reuters)
- In 2022, the total cryptocurrency value received by illicit addresses was $20.6 billion — an all time high. (Chainalysis)
- Hackers who attacked an oil company earned over $90 million in Bitcoin. (Business Insider)
- Illegal activity comprised 2.1 percent of all cryptocurrency transaction volume, or about $21.4 billion worth of transfers in 2019. (Chainalysis)
The cost of ransomware attacks
Ransomware attacks can be costly, both financially and to your reputation — businesses around the globe that have been victims of ransomware attacks have spent around $144.2 million in resolving the effects of the attacks. Here are some statistics covering the costs that are caused by ransomware attacks.
- The average cost of a ransomware recovery is nearly $2 million. (Sophos)
- The share of breaches caused by ransomware grew 41 percent in the last year and took 49 days longer than average to identify and contain. (IBM)
- Last year, ransomware attacks increased by 93 percent year-over-year. (CyberTalk)
- 75 percent of respondents said they’ve experienced a significant increase in security incidents — most often due to credential theft, ransomware, DDoS, and lost or stolen devices. (Infosecurity)
- The value of ransom demands has gone up, with some demands exceeding over $1 million. (Cybersecurity & Infrastructure Security Agency)
- In 2021, the average payout by a mid-sized organization was $170,404. (Sophos)
- In May 2021, Colonial Pipeline paid hackers $4.4 million in bitcoin after receiving a ransom note. (The Wall Street Journal)
- The average cost to recover from a ransomware attack is $1.85 million. (Sophos)
- The hacker group behind an oil company attack allegedly acquired $90 million in ransom payments in only nine months from around 47 victims. (Fox Business)
Ransomware projections
Ransomware is an ever-growing issue in the cybersecurity space and continues to shape the world today. Looking ahead, here are some statistics that cover the projections and future trends of ransomware.
- In 2022, there will be more cooperation between countries to find, extradite and ultimately prosecute ransomware groups. (Forbes)
- Ransomware will become the top tactic used in software supply chain attacks and third-party data breaches in 2022. (SC Media)
- 30 percent of organizations will adopt Zero-Trustnetwork access (ZTNA) models by 2024. (Gartner)
- 60 percent of organizations, along with investors and venture capitalists, will use cybersecurity risk as a key factor in assessing new business opportunities by 2025. (Gartner)
Ransomware attack trends
2024 has already seen a steady rise in the number of cyberattacks and ransoms demanded by hackers. Below are some of the most visible trends in ransomware that have recently affected the cyber landscape.
Exploitation of IT outsourcing services
Ransomware groups have been shifting their focus to managed service providers (MSPs), a platform that serves many clients at once. This means that if a hacker gains access to one MSP, it could also reach the clients it’s serving as well. Most of the time, MSPs are hacked due to remote access tools that are poorly secured.
Attention shifting to vulnerable industries
Due to the ongoing economic, logistical, and financial implications of the pandemic, cyberattackers have been taking advantage of industries that have been hit the hardest, such as healthcare, municipalities, and educational facilities. Hackers also continue to see the pandemic as an opportunity to take advantage of employees who are now working remotely on their personal devices.
Evolving ransomware strains (and defenses)
In 2024, ransomware and the tactics that hackers use to carry out attacks are evolving — but luckily, so are the defenses. In recent years, new ransomware strains have been discovered, including:
- RedAlert/N13V: The ransomware, which focused on non-Windows platforms, supported the halting of VMs in an ESXi environment, clearly indicating what the attackers were after.
- A new ransomware gang known as Black Basta catapulted into operation in April of 2022, breaching at least 12 companies in just a few weeks.
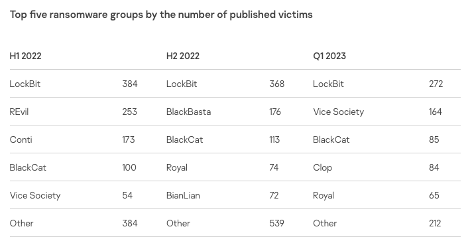
Source: SecureList
Because newer strains of ransomware behave differently today, there is now a need for alternate methods of detection. Defenses have recently begun to harden, including improved heuristics or behavioral analysis, and the use of canary or bait files for earlier detection.
Greater spread to mobile devices
Hackers have been taking advantage of mobile device features such as emergency alerts and relaxed permissions to spread malware. The majority of mobile ransomware variants have the ability to cover every browser window or app with a ransom note, rendering the mobile device unusable.
Prevalence of ransomware-as-a-service
Ransomware-as-a-service, or RaaS, is a subscription that allows affiliates to use ransomware tools that are already developed to carry out ransomware attacks and extend their reach. The decentralized nature of the attacks makes it difficult for authorities to shut down.
The creators of these tools take a percentage of each successful ransom payment; the average ransomware payout has increased dramatically, year to year – from $812,380 in 2022 to $1,542,333 in 2023.
Ransomware attack prevention
Ensure you take the necessary steps to prevent an attack and data loss within your organization. Here are a few effective ways to prevent ransomware from affecting your company.
Educate your employees
Use security training within your company to help your employees gain a better understanding of cybersecurity and its importance. Implementing this training will help ensure a working culture that is even more resilient.
Avoid clicking on suspicious links
Be wary of opening or clicking on attachments or links that come from spam or unsolicited emails. According to Astra, phishing email statistics suggest that nearly 1.2 percent of all emails sent are malicious, meaning for every 4,200 emails sent, one would certainly be a phishing scam email. To avoid this, it’s beneficial to know how to spot a phishing scam.
Use email and endpoint protection
Be sure to scan all emails, filter malicious attachments and links, and keep firewalls and endpoint detection software up to date with the latest malware signatures. You should also notify users of out-of-network emails and provide VPNs for employees to use outside of the network.
Implement a stronger password system
Password security is crucial when protecting the assets of a company. Use two-factor authentication within your organization to prevent password sharing and overuse of the same password. It may also be beneficial to use an SSO system for additional security.
Keep immutable, offsite backups
Make sure you have backups of any important or sensitive data and systems. Practice your restore motion in the event of a ransomware strike. Limit access to backups, as ransomware gangs often target backup files to cripple your ability to restore.
However, keep in mind that backups cannot help in cases where the ransomware actor has also exfiltrated the data to their own servers and threatened to release that data publicly unless the ransom is paid. To combat exfiltration, consider data loss prevention software.
Mitigating the impact of ransomware
Reduce your blast radius
Your blast radius is the amount of damage that can be caused by compromising a single random user or device. Reduce your blast radius by limiting access to critical data so that only those who require access have it.
Implement a Zero-Trust security model
Assume your perimeter defenses will fail and make sure everything within is still safe and secure. The Zero-Trust security model requires you to authenticate all users and devices that connect to your network every time they connect, not just once. You must also monitor activity in your environment and ensure users only have access to what they need and nothing else.
Use UEBA for threat detection and response
You should continually monitor for and alert to telltale signs of ransomware activity on your data. Use user and entity behavior analysis tools to detect and alert when users or devices behave abnormally and implement automatic responses to stop threats in their tracks.
Ransomware statistics FAQ
Below are a few of the most frequently asked ransomware questions, with answers supported by additional ransomware statistics and facts.
Q: What is the average length of impact after a ransomware attack?
A: As of the second quarter of 2022, the average length of interruption after ransomware attacks at businesses and organizations in the United States was 24 days. (Statista, 2023)
Q: How many industries are hit by ransomware attacks?
A: As of 2022, around 70 percent of businesses worldwide were affected by ransomware attacks. This represented an increase from the previous five years and was the highest figure reported. (Statista, 2023)
Q: What is the average payout for ransomware?
A: Ransomware payments have nearly doubled to $1.5 million over the past year, with the highest-earning organizations the most likely to pay attackers. (The Guardian, 2023)
Q: What is the average payout for small businesses?
A: Smaller businesses are impacted less than bigger companies. However, the average payout for a small business is around $5,900. (Datto)
Q: Do I have to pay for a ransomware attack?
A: The FBI does not support paying a ransom because it does not guarantee that you or your company will have the data returned to you. Paying ransoms can also encourage the attacker to go after additional victims.
Ransomware is not going away any time soon — as an organization, it’s important to stay ahead of cyber criminals and take the steps to become more cyber aware.
Learn how to protect your business and gauge your readiness for a potential ransomware attack with a free ransomware preparedness assessment.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.








