On the heels of last month’s massive WannaCry outbreak, a major ransomware incident is currently underway by a new variant (now) dubbed “NotPetya.” For most of the morning, researchers believed the ransomware to be a variant of Petya, but Kaspersky Labs and others are reporting that, though it has similarities, it’s actually #NotPetya. Regardless of its name, here’s what you should know.
This malware doesn’t just encrypt data for a ransom, but instead hijacks computers and renders them completely inaccessible by encrypting their Master Boot Record (MBR).
Get the Free Pen Testing Active Directory Environments EBook
Petya is another fast-spreading attack which, like WannaCry, uses the NSA exploit EternalBlue. Unlike WannaCry, Petya can also spread via remote WMI and PsExec (more on that in minute). A few scary things about this new malware:
- It doesn’t have a remote kill switch like WannaCry
- It is far more sophisticated — it has a variety of automated ways to spread
- It renders machines completely unusable
A number of prominent organizations and companies have already been badly hit, including the Ukranian government, which has quite the sense of humor:
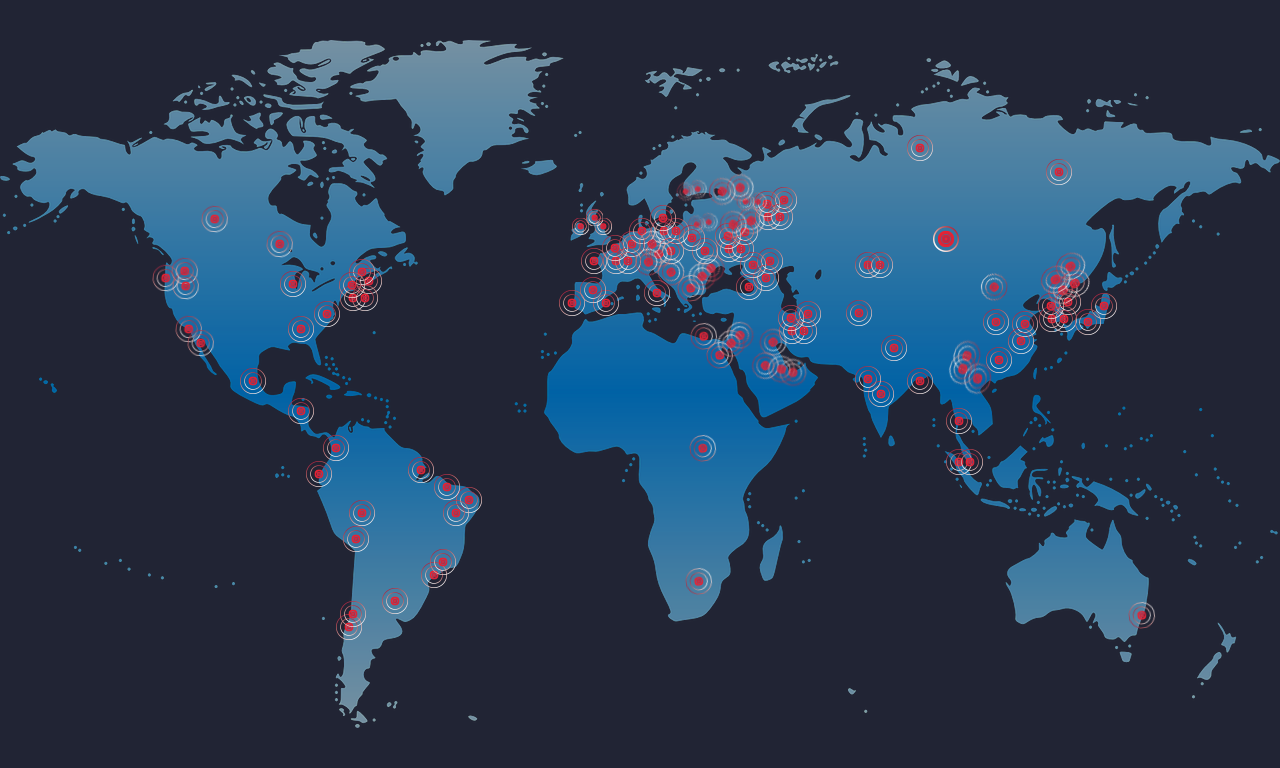
Infections have been reported across the globe: affecting metro systems, national utilities, banks and international enterprises: the scope is not yet known, but reports continue to come in of infected computers and stalled IT systems across industries and throughout the world.
How is Petya spreading?
Petya was initially thought to have gotten a toehold in corporate networks via emails with infected Word document attachments which exploit CVE-2017-0199. (If you’ve patched Microsoft Office, you should be protected from this attack vector.)
While phishing is a viable attack vector, one of the primary vectors is MeDoc, a financial software firm based in the Ukraine. MeDoc’s software update feature was hacked and attackers used it to distribute the Petya ransomware (source). This explains why the Ukraine has been hit hardest.
Once a single machine is infected, Petya spreads peer-to-peer to other Windows-based endpoints and servers that are vulnerable to MS17-010 — the SMB vulnerability that everyone was instructed to patch during WannaCry. It can also spread via PsExec to admin$ shares, even on patched machines. We’ve written a detailed guide about PsExec and how to disable PowerShell recently. That’ll come in handy here.
A silver lining, at least at this juncture, is that the peer-to-peer infection doesn’t seem to leap beyond the local network. Petya can buzz through an entire LAN rather efficiently, but is unlikely to hop to other networks. As @MalwareTechBlog, the pizza-loving surfer dude who famously hit the WannaCry kill switch points out:
The Current Petya attack is different in the sense that the exploits it uses are only used to spread across a local network rather than the internet (i.e. you are extremely unlikely to be infected if you’re not on the same network as someone who was already infected). Due to the fact networks are of limited size and fairly quick to scan, the malware would cease spreading once it has finished scanning the local network and therefore is not anywhere near as infectious as WannaCry, which still continues to spread (though is prevented from activating via the “kill switch”).
How to Detect PsExec with DatAlert
If you’re a DatAlert customer on the version 6.3.150 or later you can do the following to detect PsExec.exe dropped on Windows file servers:
1. Select Tools –> DatAlert –> DatAlert
2. Search for “system admin”
3. For each of the selected rules (expand the groups to see them), press “Edit Rule” and tick “Enabled”
If PsExec is detected, DatAlert will generate sysadmin tools alerts in the “Reconnaissance” alert category such as “System administration tool created or modified” or “An operation on a tool commonly used by system administrators failed.”
This should help you detect if Petya is using PsExec to spread across your file servers. Keep reading because there is more you can do to prevent initial infection and stop Petya from spreading on your endpoints.
What does Petya do?
Once on a machine, NotPetya waits for a hour and a half before performing any attack, likely to give time for more machines to be affected, and to obfuscate the point of entry.
After waiting:
- It encrypts the Master File Table (MFT) of locally attached NTFS drives
- Copies itself into the Master Boot Record (MBR) for the infected workstation/server
- Forces a reboot of the machine so that users are locked out
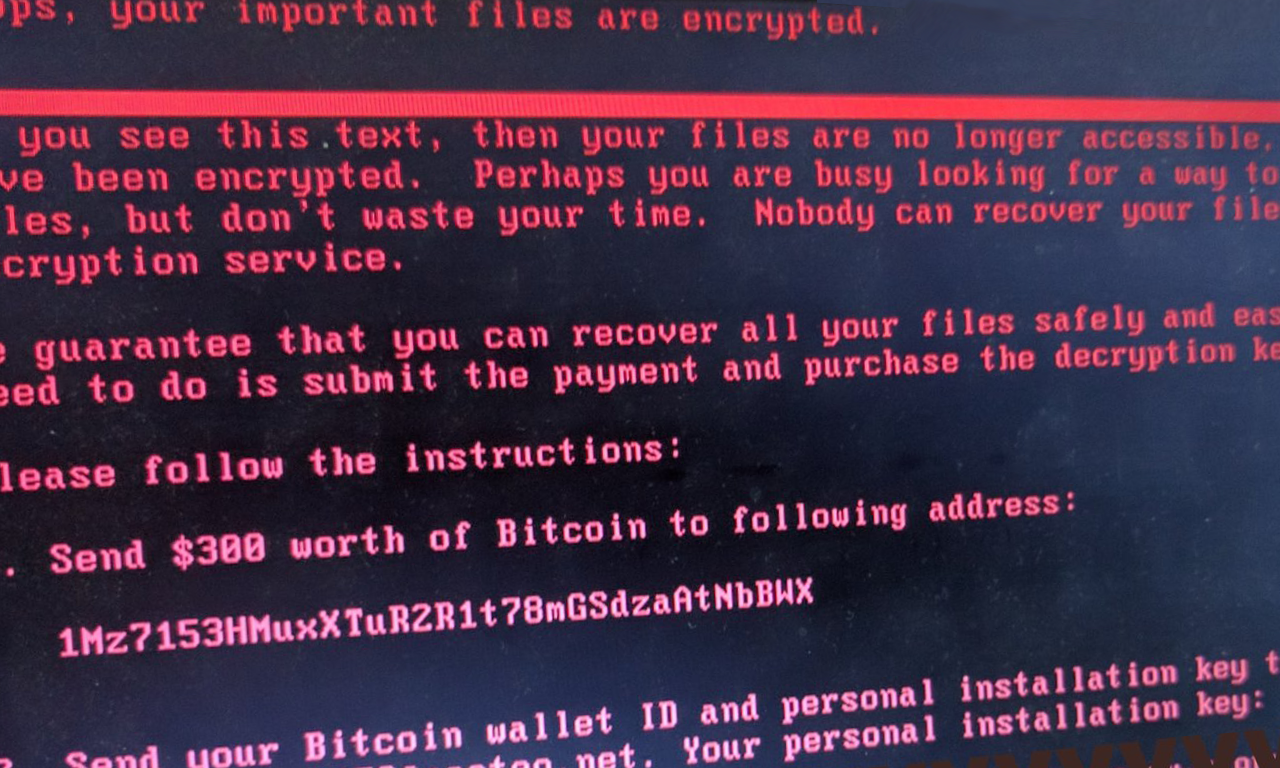
- Displays the ransom demand lock screen on boot (shown below)
All computers in our office are down. Global #Ransomware attack. I’ve heard few other companies affected too. Backup and stay safe, guys. pic.twitter.com/YNctmvdW2I
— Mihir (@mihirmodi) June 27, 2017
By encrypting the MFT, the individual workstation or server is taken offline until the ransom is paid. This has the potential to disrupt an organization to a much greater degree than if some files on a server are encrypted. In many cases, IT may need to individually address each machine; the standard ransomware response of “We’ll just restore those files from backup” is rendered ineffective.
If remote boot / imaging processes aren’t in place to restore infected machines, it may be necessary to put hands on the workstations to fix them. While possible in most cases, for companies with many remote installations it can be extremely challenging and time consuming. If you’re a shipping company with 600+ cargo ships on the move at any moment nearly impossible.
As Microsoft notes, “Only if the malware is running with highest privilege (i.e., with SeDebugPrivilege enabled), it tries to overwrite the MBR code” — if the infected user does not have admin privileges on the machine, it will try to encrypt user data matching the following extensions:
It does not add a unique extension to the encrypted files (such as .locky) — it encrypts the contents and preserves the original filename and extension.
What To Do?
Preventing Petya closely mirrors the steps that you may have previously taken for WannaCry:
- Disable SMBv1 while you patch
- Block TCP port 445 from outside (or between segments if possible)
- Apply the patch!
Local Kill Switch
There is also somewhat of a local kill switch. On any given machine, if the file %WINDIR%\perfc exists (no extension) the ransomware will not execute. You can get creative with ways to deploy that file to all workstations in your environment.
Additionally, you can see which endpoint AV products are able to detect Petya by looking at the VirusTotal results.
A sample of Petya acquired by researchers was compiled on June 18:
Should You Pay?
A Posteo (an email service provider) account was included in the Ransomware message. The abuse and security team at Posteo have posted an update at:
They have:
- Blocked the account
- Confirmed that no decrypt keys were sent from the account
- Contacted the authorities to offer what assistance they can
All of which adds up to the fact that you shouldn’t pay the ransom as you won’t receive the necessary decryption keys.
This is a developing story and we’ll keep this post updated as we learn more.
Other Helpful Links
- Microsoft’s extremely thorough recap (probably the most informative resource to date)
- Ransomware spreads across Europe with firms in Ukraine, Britain and Spain shut down
- WannaCry Déjà Vu: Petya Ransomware Outbreak Wreaking Havoc Across the Globe
- PetrWrap: the new Petya-based ransomware used in targeted attacks
- Ukraine cyber attack: Chaos as national bank, state power provider and airport hit by hackers
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.