Featured Content

AI Security

Nolan Necoechea

Nolan Necoechea
Threat Research

Oren Bahar
Cloud Security

Yaki Faitelson
Data Security

Avia Navickas
-
 Data Security
Data SecurityJan 21, 2016
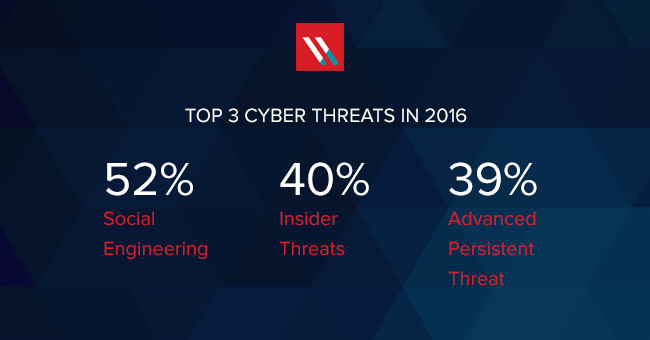
Social Engineering Remains a Top Cybersecurity Concern
In 2016, the top cyberthreat for IT pros, at least according to ISACA’s Cybersecurity Snapshot, is social engineering. It has always been a classic exploit amongst the hackerati. But in...

Michael Buckbee
3 min read
-
 Data Security
Data SecurityJan 18, 2016
Current Privacy Risks in Genetic Testing
The idea of taking a direct-to-consumer(DTC) genetic test is intriguing. What was once considered an expensive test that could only be performed in a medical environment can now be purchased...

Michael Buckbee
3 min read
-
 Data Security
Data SecurityJan 10, 2016
Varonis Seven Part Guide to Penetration Testing
Our sprawling pen-testing series has taken on a life of its own! For your convenience and blog reading pleasure, we’ve assembled all the links to this six seven part series below....

Michael Buckbee
1 min read
-
 Data Security
Data SecurityJan 06, 2016
Penetration Testing Explained, Part VI: Passing the Hash
We’re now at a point in this series where we’ve exhausted all our standard tricks to steal credentials — guessing passwords, or brute force attacks on the hash itself. What’s...

Michael Buckbee
2 min read
-
 Data Security
Data SecurityJan 05, 2016
Varonis and the Building Security in Maturity Model (BSIMM)
With major security threats and vulnerabilities making headlines daily, it’s good to hear there’s now a way for organizations to share experiences and strategically work together. Through the Building Security...

Michael Buckbee
6 min read
-
 Data Security
Data SecurityJan 04, 2016
Data Security’s Tower of Jenga
Over the holiday break, I had a chance to see “The Big Short”, the movie based on Michael Lewis’s book about the housing bubble. Or more accurately, about how a...

Michael Buckbee
3 min read
-
 Privacy & Compliance
Privacy & ComplianceDec 11, 2015
What is the EU General Data Protection Regulation?
Table of Contents DPD 2.0 GDPR Vocabulary Articulating the Articles More Articles: The New Stuff Focus Your GDPR Compliance Note: This post now reflects the final version of the EU...

Michael Buckbee
7 min read
-
 Data Security
Data SecurityDec 04, 2015
Design Thinking for your Data Strategy
A fact of life for many Chief Data Officers (CDOs) is that once you’ve achieved certain milestones in your data strategy, your focus will inevitably shift to a new milestone...

Michael Buckbee
2 min read
-
 Data Security
Data SecurityDec 02, 2015
Penetration Testing Explained, Part V: Hash Dumping and Cracking
In the previous post in this series, I guessed a local password and then tried various ways to move laterally within my mythical Acme network. But what happens if you can’t...

Michael Buckbee
3 min read
-
 Data Security
Data SecurityNov 10, 2015
A Brief History of Ransomware
Ransomware’s Early Days The first documented and purported example of ransomware was the 1989 AIDS Trojan, also known as PS Cyborg1. Harvard-trained evolutionary biologist Joseph L. Popp sent 20,000 infected...

Kieran Laffan
5 min read
-
 Data Security
Data SecurityNov 05, 2015
Introducing Varonis UBA Threat Models
If you’re a regular reader of our blog, you know that we feel that the perimeter is dead, and that the battle against insider (and outsider) threats is won with...

Michael Buckbee
2 min read
-
 Data Security
Data SecurityNov 03, 2015
Penetration Testing Explained, Part IV: Making the Lateral Move
You can think about the post-exploitation part of penetration testing as an army or rebel force living off the land. You’re scrounging around the victim’s website using what’s available —...

Michael Buckbee
5 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital