Featured Content

Data Security

Avia Navickas

Avia Navickas
Cloud Security

Yaki Faitelson
Data Security

Varonis Threat Labs
Data Security
-1.png)
Lexi Croisdale
-
 Data Security
Data SecurityMay 23, 2016
How has Ransomware Impacted the US Government?
Ransomware crimes have been soaring this year. It has stalled the operations of not only hospitals and businesses, but also the US government – federal, state and local governments, law enforcement...

Michael Buckbee
3 min read
-
 Data Security
Data SecurityMay 16, 2016
Ransomware That Deletes Your Files
Organizations with legal obligations to prevent data from improper alteration or destruction—I’m talking to you healthcare orgs that fall under HIPAA– really need to pay close attention to a new...

Michael Buckbee
1 min read
-
 Data Security
Data SecurityMay 06, 2016
CyptMix Ransomware Claims to Donate Your Ransom Payment to Charity
Unlike traditional ransomware notes that rely on fear-based tactics, a new ransomware strain called CyptMix preys on your generosity. Part of the ransom note reads: “Your money will be spent...

Michael Buckbee
1 min read
-
 Data Security
Data SecurityMay 05, 2016
Lessons From the Goldcorp Extortion
Unfortunately, another breach has made the headlines and it’s déjà vu all over again. The narrative surrounding the Goldcorp breach is similar to other doxing attacks: Attackers appear to have...

Michael Buckbee
1 min read
-
 Data Security
Data SecurityMay 03, 2016
Interesting Deloitte Research on Insider Threats
We’re excited that Deloitte, the international auditing and consulting firm, has been raising the alarms on insider threats. They have some content in the CIO section of the Wall Street...

Michael Buckbee
1 min read
-
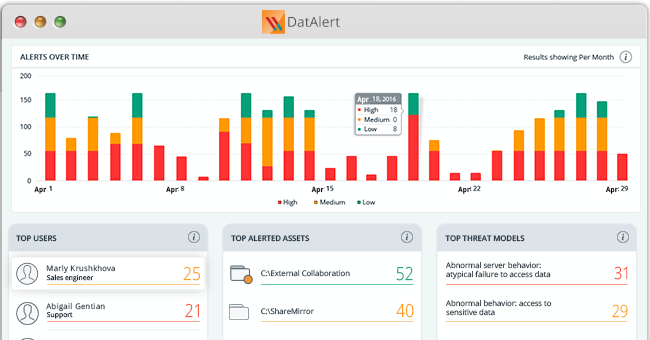 Data Security
Data SecurityMay 02, 2016
Visualize your risk with the DatAlert dashboard
Last week, we introduced over 20 new threat models to help defend your data against insider threats, ransomware attacks and threats to your most sensitive data. But with all this...

Michael Buckbee
1 min read
-
 Data Security
Data SecurityApr 29, 2016
Football player hacked live during NFL draft
Experts had Laremy Tunsil flagged as one of the top prospects in Thursday night’s NFL draft. But shortly before the opening pick, something disturbing happened. An incriminating video tweeted from...

Rob Sobers
2 min read
-
 Data Security
Data SecurityApr 28, 2016
Cryptolocker, lockouts and mass deletes, oh my!
DatAlert Analytics just got some new threat models. Our research laboratory is tracking new ransomware, finding vulnerabilities in common security practices, and setting up new threat models to keep your...

Michael Buckbee
1 min read
-
 Data Security
Data SecurityApr 22, 2016
New Varonis eBook Helps IT Kickstart Their Pen Testing Program
Hackers are able to break into systems and move around easily without being detected. How is this possible with so much invested in firewalls, malware scanners, and other intrusion detection...

Michael Buckbee
1 min read
-
 Data Security
Data SecurityApr 15, 2016
CEO Phishing: Hackers Target High-Value Data
Humans like to click on links. Some of us are better at resisting the urge, some worse. In any case, you’d also expect that people in the higher reaches of...

Michael Buckbee
2 min read
-
 Data Security
Data SecurityApr 14, 2016
Ransomware Guide for Healthcare Providers
Table of Contents Ransomware strains that have been targeting hospitals Should your hospital pay? Reasons not to pay Would a ransomware infection be considered a breach, according to HIPAA? Are...

Michael Buckbee
4 min read
-
 Data Security
Data SecurityApr 13, 2016
Learning to Write Fully Undetected Malware - Lessons For IT
I really believe that an IT security person should master some of the programming concepts that go into malware. File that under “know your enemy”.
Oded Awaskar
7 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital