Featured Content

Data Security

Avia Navickas

Avia Navickas
Cloud Security

Yaki Faitelson
Data Security

Varonis Threat Labs
Data Security
-1.png)
Lexi Croisdale
-
 Data Security
Data SecurityMay 17, 2017
Adylkuzz: How WannaCry Ransomware Attack Alerted The World To Even Worse Threats
Your garden variety ransomware, like Cerber, is the canary in the coal mine that rudely, but thankfully announces bigger security issues: insider threats and cyberattacks that take advantage of too...

Rachel Hunt
2 min read
-
 PowerShell
PowerShellMay 16, 2017
How to use PowerShell for WannaCry / WannaCrypt cleanup and prevention
Use PowerShell to help test and resolve issues from WannaCry / WannaCrypt variants and other ransomware attacks.

Michael Buckbee
2 min read
-
 Data Security
Data SecurityMay 15, 2017
Why did last Friday's ransomware infection spread globally so fast?
Ransomware is a type of malware that encrypts your data and asks for you to pay a ransom to restore access to your files. Cyber criminals usually request that the...

Kieran Laffan
3 min read
-
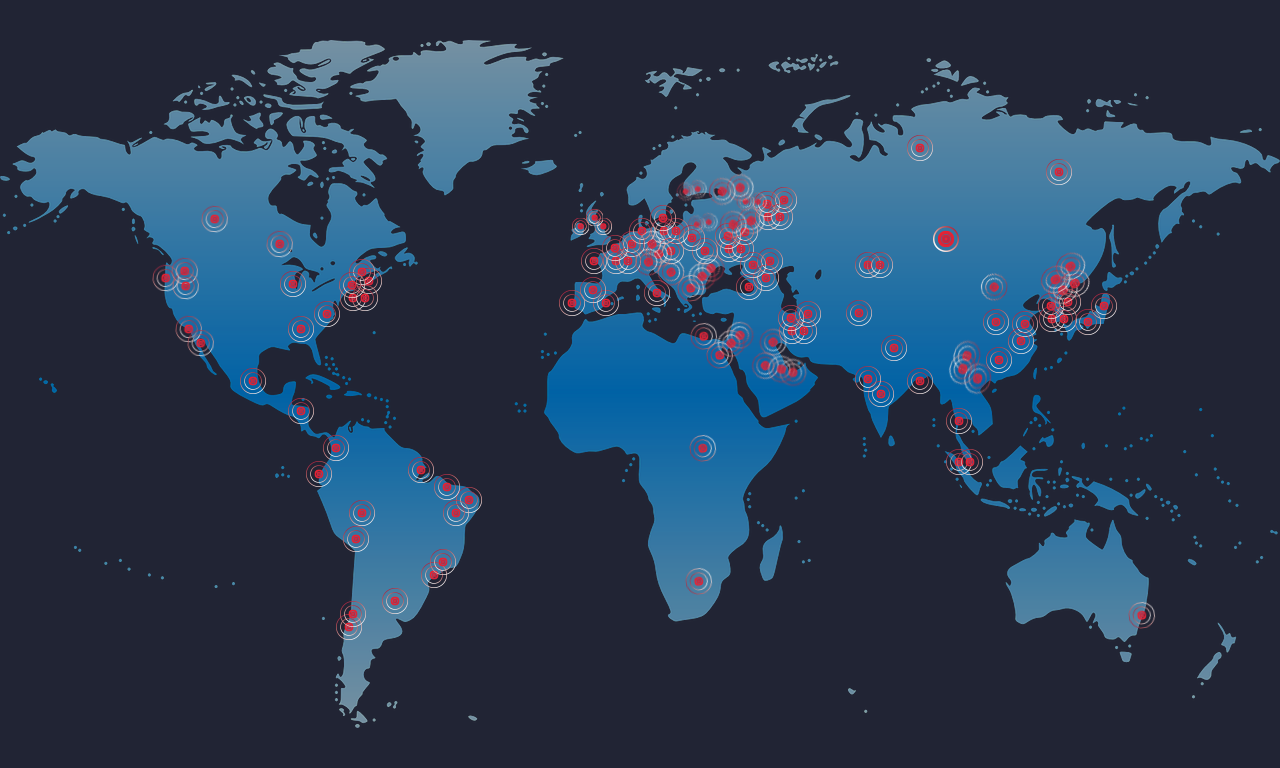 Data Security
Data SecurityMay 12, 2017
🚨 Massive Ransomware Outbreak: What You Need To Know
Remember those NSA exploits that got leaked a few months back? A new variant of ransomware using those exploits is spreading quickly across the world – affecting everyone from the...

Michael Buckbee
2 min read
-
 Data Security
Data SecurityMay 12, 2017
Planet Ransomware
If you were expecting a quiet Friday in terms of cyberattacks, this ain’t it. There are reports of a massive ransomware attack affecting computers on a global scale: in the...

Michael Buckbee
1 min read
-
 PowerShell
PowerShellMay 10, 2017
Practical PowerShell for IT Security, Part IV: Security Scripting Platform (SSP)
In the previous post in this series, I suggested that it may be possible to unify my separate scripts — one for event handling, the other for classification — into...

Michael Buckbee
10 min read
-
 Security Bulletins
Security BulletinsMay 05, 2017
Introducing the Automation Engine, DatAlert Analytics Rewind, and more
Getting to least privilege can be a nightmare. The first steps – tracking down inconsistent ACLs and remediating global access groups can turn even the most basic file share clean-up...

Michael Buckbee
1 min read
-
 Security Bulletins
Security BulletinsApr 26, 2017
Varonis + Splunk: Epic Threat Detection and Investigations
We’re bringing our powerful DatAlert functionality to Splunk® Enterprise to give you comprehensive visibility into data security with our new Varonis App fo

Michael Buckbee
1 min read
-
 Privacy & Compliance
Privacy & ComplianceApr 20, 2017
Data Security Compliance and DatAdvantage, Part III: Protect and Monitor
At the end of the previous post, we took up the nuts-and-bolts issues of protecting sensitive data in an organization’s file system. One popular approach, least-privileged access model, is often...

Michael Buckbee
5 min read
-
 Privacy & Compliance
Privacy & ComplianceApr 14, 2017
Data Security Compliance and DatAdvantage, Part II: More on Risk Assessment
I can’t really overstate the importance of risk assessments in data security standards. It’s really at the core of everything you subsequently do in a security program. In this post...

Michael Buckbee
5 min read
-
 Data Security
Data SecurityApr 12, 2017
What is a Data Security Portfolio?
A Data Security Platform (DSP) is a category of security products that replaces traditionally disparate security tools to reduce risk and prevent threats.

Rob Sobers
6 min read
-
 Data Security
Data SecurityApr 11, 2017
Varonis Data Security Platform Listed in Gartner 2017 Market Guide for Data-Centric Audit and Protection
In 2005, our founders had a vision to build a solution focused on protecting the data organizations have the most of and yet know the least about – files and...

Rachel Hunt
1 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital