Featured Content

Data Security

Avia Navickas

Avia Navickas
Cloud Security

Yaki Faitelson
Data Security

Varonis Threat Labs
Data Security
-1.png)
Lexi Croisdale
-
 Data Security
Data SecurityJun 07, 2018
What Does it Take to Be an Ethical Hacker?
A white hat hacker, or an ethical hacker, works with agencies and organizations to discover network vulnerabilities and security flaws. Learn what it takes to make hacking your profession with our guide!

Rob Sobers
3 min read
-
Data Security
Jun 04, 2018
The Malware Hiding in Your Windows System32 Folder: Mshta, HTA, and Ransomware
The LoL approach to hacking is a lot like the “travel light” philosophy for tourists. Don’t bring anything to your destination that you can’t find or inexpensively purchase once you’re…

Michael Buckbee
5 min read
-
 Data Security
Data SecurityJun 01, 2018
The State of CryptoWall in 2018
CryptoWall and its variants are still favorite toys of the cybercriminals that want your Bitcoin. Learn more about the state of CryptoWall in 2018, today!

Michael Buckbee
5 min read
-
 Data Security
Data SecurityMay 30, 2018
Australian Prudential Regulation Authority CPS 234
The Australian Prudential Regulation Authority (APRA) regulates Australia’s financial services industry, including banks, insurance companies, and investments firms. In December 2018, they published the final version of its security framework,...

Michael Buckbee
1 min read
-
 Data Security
Data SecurityMay 25, 2018
What's The Difference Between a Proxy and a VPN?
Comparing a proxy vs VPN? We're taking a look at each to help you understand the benefits, drawbacks and steps to deciding which is right for your company!

Michael Buckbee
4 min read
-
 Data Security
Data SecurityMay 24, 2018
The Malware Hiding in Your Windows System32 Folder: Intro to Regsvr32
In our epic series on Malware-Free Hacking, I wrote about techniques that let you use well-known Microsoft apps and tools to run evil custom scripts. This file-less hack-craft usually involves sneaking...

Michael Buckbee
5 min read
-
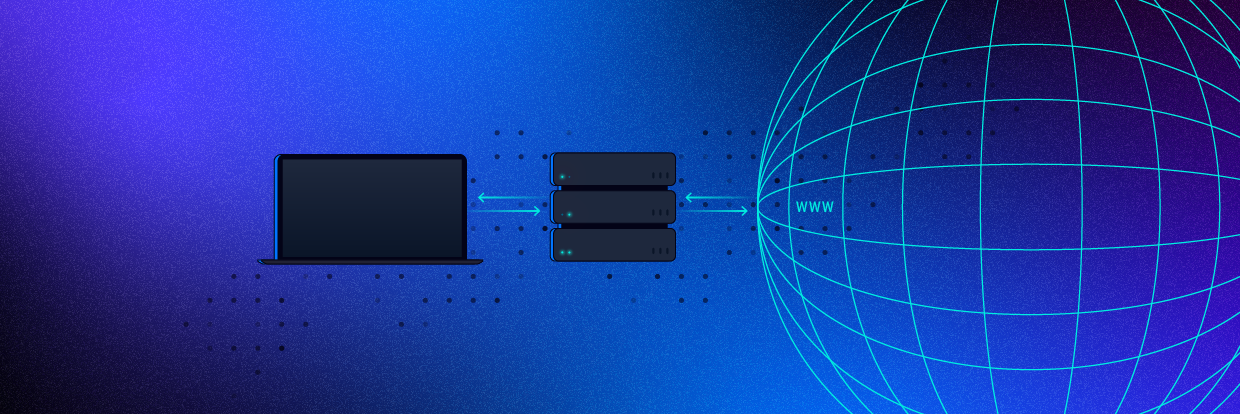 Data Security
Data SecurityMay 21, 2018
What is a Proxy Server and How Does it Work?
A proxy server acts as a gateway between you and the internet. Learn the basics about proxies with our complete, easy-to-follow guide.

Michael Buckbee
7 min read
-
 Data Security
Data SecurityMay 18, 2018
What is Spear Phishing?
You might be wondering what is spear phishing. Our guide includes all the information you'll need to know including examples and tips for avoiding an attack

Michael Buckbee
3 min read
-
 Data Security
Data SecurityMay 10, 2018
Australian Notifiable Data Breach Scheme, Explained
A third time is a charm, in life and in data breach notifications laws. On February 13, 2017, the Australian government, in its third attempt, passed the Notifiable Data Breaches...

Michael Buckbee
4 min read
-
 Data Security
Data SecurityMay 08, 2018
The Anatomy of a Phishing Email
Have you been hooked by a phishing email? We’ve broken out the most common components of a phishing email. Check out our full guide to test your knowledge!

Rob Sobers
3 min read
-
 Privacy & Compliance
Privacy & ComplianceMay 02, 2018
Canada’s PIPEDA Breach Notification Regulations Are Finalized!
While the US — post-Target, post-Sony, post-OPM, post-Equifax — still doesn’t have a national data security law, things are different north of the border. Canada, like the rest of the...

Michael Buckbee
2 min read
-
 Active Directory
Active DirectoryApr 23, 2018
5 FSMO Roles in Active Directory
FSMO roles give you confidence that your domain will be able to perform the primary functions of authenticating users and permissions. Learn more today.

Michael Buckbee
2 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital