Featured Content

Data Security

Avia Navickas

Avia Navickas
Cloud Security

Yaki Faitelson
Data Security

Varonis Threat Labs
Data Security
-1.png)
Lexi Croisdale
-
 Data Security
Data SecurityMar 29, 2020
10 Secure File Sharing Options, Tips and Solutions
When moving digital data across networks, there is a number of different tools and solutions that will fit various business needs at the enterprise level.

Michael Buckbee
8 min read
-
 Data Security
Data SecurityMar 29, 2020
5 Cybersecurity Concerns of Industry Insiders
We asked professionals attending two of the world’s biggest cybersecurity conferences – RSA in San Francisco and Infosecurity in London – five questions to gauge their opinions and attitudes about current cybersecurity concerns and issues. Read on to discover what we found!

Rachel Hunt
3 min read
-
 Data Security
Data SecurityMar 29, 2020
Zero-Day Vulnerability Explained
Find out how zero-day vulnerabilities become zero-day exploits and zero-day attacks, and how to defend your network from zero-day attacks and exploits.

Michael Buckbee
3 min read
-
 Data Security
Data SecurityMar 29, 2020
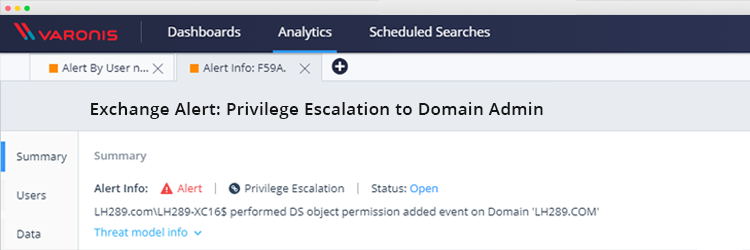
Exchange Vulnerability: How to Detect Domain Admin Privilege Escalation
Researchers recently uncovered a vulnerability in Exchange that allows any domain user to obtain Domain admin privileges that allow them to compromise AD and connected hosts. Here’s how the attack...

Michael Buckbee
1 min read
-
 Privacy & Compliance
Privacy & ComplianceMar 29, 2020
Beyond Privacy and DSARs: Public Data Requests (FOI) Are the Law in 50 States
Happy 2020! The New Year brings Californians under the California Consumer Privacy Act (CCPA). CA consumers can ask state-based companies for all relevant data, and to request that companies delete...

Michael Buckbee
4 min read
-
 Privacy & Compliance
Privacy & ComplianceMar 29, 2020
What the H**L Does Reasonable Data Security Really Mean?
For anyone who’s spent time looking at data security laws and regulations, you can’t help but come across the words “reasonable security”, or its close cousin “appropriate security”. You can...

Michael Buckbee
3 min read
-
 Privacy & Compliance
Privacy & ComplianceMar 29, 2020
Post-Davos Thoughts on the EU NIS Directive
I’ve been meaning to read the 80-page report published by the World Economic Forum (WEF) on the global risks humankind now faces. They’re the same folks who bring you the once...

Michael Buckbee
3 min read
-
 Data Security
Data SecurityMar 29, 2020
Spotlighting Unstructured Data Access
At Varonis, we sometimes highlight external articles, especially when they provide independent insight into our solution. Dr. Edward G. Amoroso, former Senior Vice President and Chief Security Officer of AT&T,...

Rob Sobers
1 min read
-
 Data Security
Data SecurityMar 29, 2020
What Working in Cybersecurity is Really Like: A Day in the Life
Learn what working in cybersecurity is like from Q&A with experts across various job roles — including which skills you need, resources and expert advice

Rob Sobers
18 min read
-
 Active Directory
Active DirectoryMar 29, 2020
Active Directory Domain Controller (AD DC) Could Not Be Contacted [SOLVED]
Sometimes clients report an error “An Active Directory Domain Controller (AD DC) for the domain could not be contacted.” Read on to learn how to troubleshoot and resolve this issue.

Michael Buckbee
2 min read
-
 Data Security
Data SecurityMar 29, 2020
What Certifications Should I Get for IT?
Elevate your IT knowledge and credentials by using our IT certification flowcharts to find the right certification for your experience level and interests.

Rob Sobers
2 min read
-
 Data Security
Data SecurityMar 29, 2020
Maximize your ROI: Maintaining a Least Privilege Model
TL;DR: Managing permissions can be expensive. For a 1,000 employee company, the overhead of permissions request tickets can cost up to $180K/year. Automating access control with DataPrivilege can save $105K/year...

Michael Buckbee
5 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital