December 1, 2025
Understanding Business Email Compromise (BEC): Threat Types and Defense Strategies-
 Ransomware
RansomwareJan 24, 2022
What Every CEO Should Know About Modern Ransomware Attacks
How To Make Yourself A Tougher Cybersecurity Target

Yaki Faitelson
3 min read
-
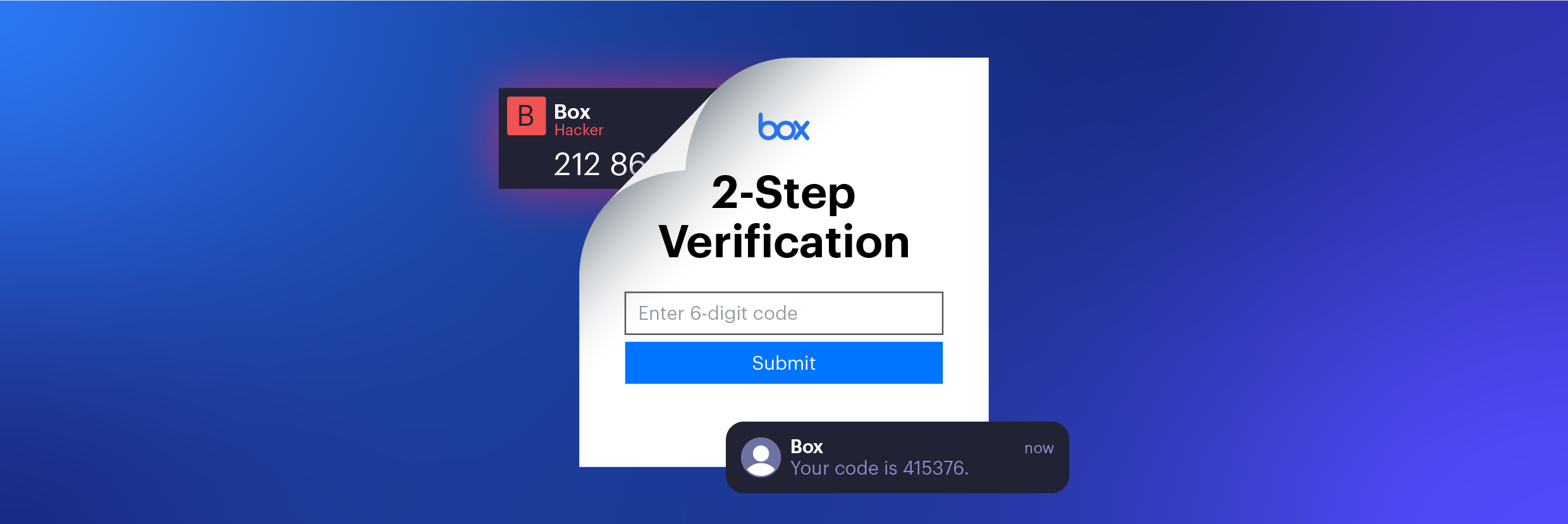 Threat Research
Threat ResearchJan 18, 2022
Mixed Messages: Busting Box’s MFA Methods
Varonis Threat Labs discovered a way to bypass multi-factor authentication (MFA) for Box accounts that use an SMS code for login verification.

Tal Peleg
3 min read
-
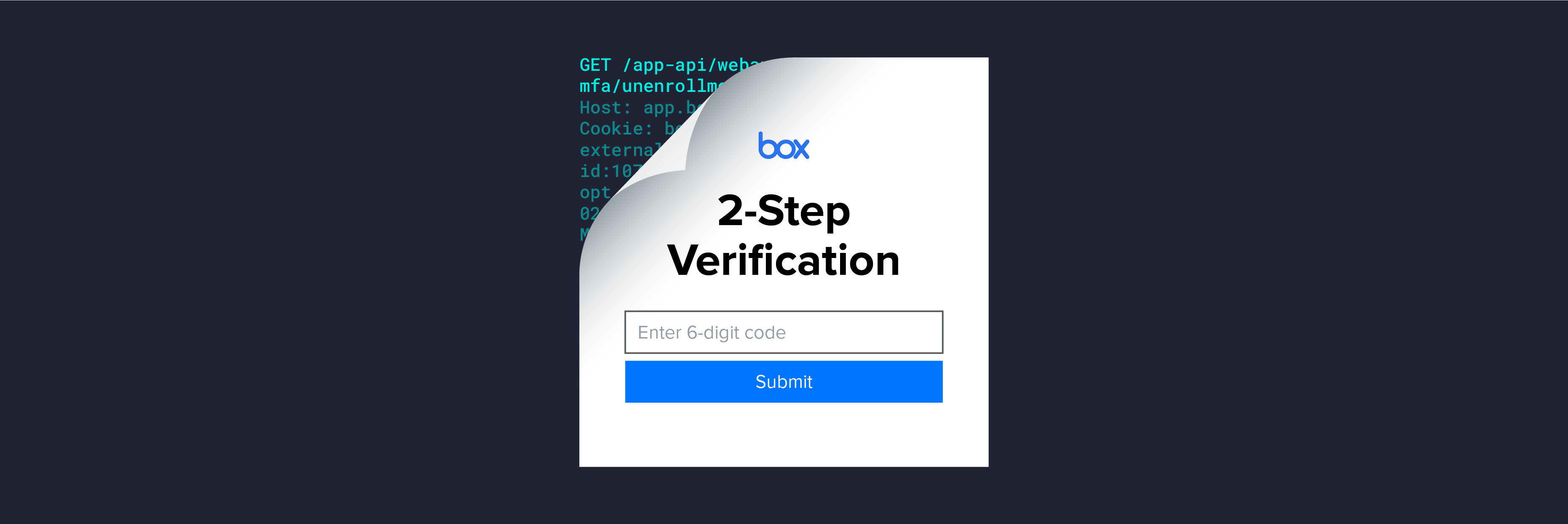 Threat Research
Threat ResearchDec 02, 2021
Bypassing Box's Time-based One-Time Password MFA
The Varonis research team discovered a way to bypass Box's Time-based One-Time Password MFA for Box accounts that use authenticator applications.

Tal Peleg
2 min read
-
 Data Security
Data SecurityNov 18, 2021
How to Monitor Network Traffic: Effective Steps & Tips
In this article, you will learn how to monitor network traffic using different tools and methods.

David Harrington
4 min read
-
 Threat Research
Threat ResearchNov 17, 2021
No Time to REST: Check Your Jira Permissions for Leaks
Varonis researchers enumerated a list of 812 subdomains and found 689 accessible Jira instances. We found 3,774 public dashboards, 244 projects, and 75,629 issues containing email addresses, URLs, and IP...

Omri Marom
4 min read
-
 Data Security
Data SecurityNov 17, 2021
What is Role-Based Access Control (RBAC)?
Role-Based Access Control (RBAC) is a security paradigm where users are granted access depending on their role in your organization. In this guide, we'll explain what RBAC is, and how to implement it.

Neeraj Kumar
6 min read
-
 Data Security
Data SecurityNov 17, 2021
What is a Security Operations Center (SOC)?
What is SOC security? In this article we'll dive into the functions of an SOC and why it's critical for the safety of your company's security and response to cybersecurity incidents.

David Harrington
8 min read
-
 PowerShell
PowerShellNov 03, 2021
How to Install and Import Active Directory PowerShell Module
The Active Directory PowerShell module is a powerful tool for managing Active Directory. Learn how to install and import the module in this detailed tutorial!

Jeff Brown
5 min read
-
 Threat Research
Threat ResearchNov 02, 2021
Einstein's Wormhole: Capturing Outlook & Google Calendars via Salesforce Guest User Bug
If your organization uses Salesforce Communities and Einstein Activity Capture, you might have unknowingly exposed your administrator's Outlook or Google calendar events to the internet due to a bug called...

Nitay Bachrach
3 min read
-
 Threat Research
Threat ResearchNov 02, 2021
BlackMatter Ransomware: In-Depth Analysis & Recommendations
CISA has issued a security bulletin regarding the BlackMatter 'big game hunter' ransomware group following a sharp increase in cases targeting U.S. businesses. To mitigate these attacks, it is recommended...

Dvir Sason
6 min read
-
 Data Security
Data SecurityOct 29, 2021
Update 62 - SaaS Authentication Monitoring Evasion
Businesses know they need to monitor their SaaS apps, but it's easy to get lulled into a false sense of security if you're relying on authentication monitoring as your only line of defense.

Kilian Englert
1 min read
-
 Data Security
Data SecurityOct 25, 2021
The MITRE ATT&CK Framework: A Comprehensive Guide
The MITRE ATT&CK framework helps businesses discover which hacker techniques, tactics, and behaviors they're most vulnerable to. Read about how to use ATT&CK for penetration testing within your organization today.

David Harrington
7 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital



