December 1, 2025
Understanding Business Email Compromise (BEC): Threat Types and Defense Strategies-
Jun 02, 2022
How to Prepare for a Salesforce Permissions Audit
In this post, I'll walk you through what a Salesforce audit is, how permissions work, and provide tips on how you can prepare.

Mike Mason
5 min read
-
 Data Security
Data SecurityMay 20, 2022
Data Breach Statistics & Trends [updated 2025]
These data breach statistics cover risk, cost, prevention and more — assess and analyze these stats to help prevent a data security incident.

Rob Sobers
12 min read
-
 Ransomware
RansomwareMay 16, 2022
Why Every Cybersecurity Leader Should ‘Assume Breach’
Any system, account or person at any time can be a potential attack vector. With such a vast attack surface, you need to assume attackers will breach at least one vector.

Yaki Faitelson
3 min read
-
 Threat Research
Threat ResearchMay 11, 2022
Spoofing SaaS Vanity URLs for Social Engineering Attacks
SaaS vanity URLs can be spoofed and used for phishing campaigns and other attacks. In this article, we’ll showcase two Box link types, two Zoom link types, and two Google Docs link type that we were able to spoof.

Tal Peleg
6 min read
-
 Ransomware
RansomwareMay 06, 2022
Bad Rabbit Ransomware
Bad Rabbit is a ransomware strain that spread via hacked websites, infected systems via a fake Adobe installer and held encrypted files for Bitcoin.

Michael Raymond
3 min read
-
 Threat Research
Threat ResearchApr 19, 2022
Hive Ransomware Analysis
Learn how Hive ransomware exploits public servers, spreads through your network, encrypts sensitive files, and exports victims for cryptocurrency.

Nadav Ovadia
7 min read
-
 Data Security
Data SecurityApr 12, 2022
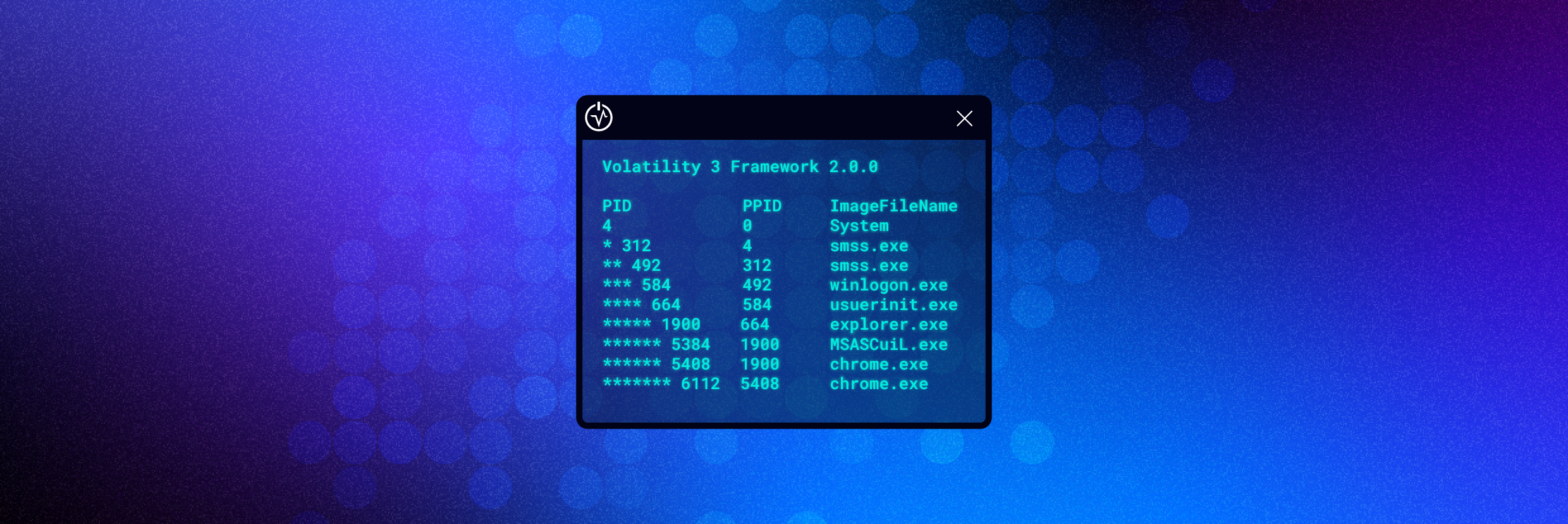
How to Use Volatility for Memory Forensics and Analysis
This article will cover what Volatility is, how to install Volatility, and most importantly how to use Volatility.

Neil Fox
8 min read
-
 Data Security
Data SecurityApr 07, 2022
CCSP vs. CISSP: Which One Should You Take?
Get an overview of the CCSP and CISSP exams and learn which certification is best for you and your career.

Josue Ledesma
5 min read
-
 Data Security
Data SecurityApr 06, 2022
Unpacking NIST Cybersecurity Framework 2.0
Learn how you can implement the NIST Cybersecurity Framework (CSF) 2.0 within your own organization and how Varonis helps.

Shawn Hays
8 min read
-
 Active Directory
Active DirectoryApr 04, 2022
12 Group Policy Best Practices: Settings and Tips for Admins
Group Policy configures settings, behavior, and privileges for user and computers. In this article, you’ll learn best practices when working with Group Policy.

Jeff Brown
5 min read
-
 Data Security
Data SecurityMar 31, 2022
Your Guide to Simulated Cyberattacks: What is Penetration Testing?
Penetration testing simulates a real-world cyber-attack on your critical data and systems. Here’s what penetration testing is, the processes and tools behind it, and how pen testing helps spot vulnerabilities before hackers do.

David Harrington
7 min read
-
 Data Security
Data SecurityMar 30, 2022
What is Terraform: Everything You Need to Know
Terraform is an infrastructure-as-code (IaC) solution that helps DevOps teams manage multi-cloud deployments. Learn about what is Terraform, the benefits of IaC, and how to get started.

David Harrington
5 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital