Featured Content

Data Security

Avia Navickas

Avia Navickas
Cloud Security

Yaki Faitelson
Data Security

Varonis Threat Labs
Data Security
-1.png)
Lexi Croisdale
-
 Data Security
Data SecurityMar 10, 2023
A Step-By-Step Guide to California Consumer Privacy Act (CCPA) Compliance
CCPA Compliance: Everything you need to know about protecting user data under the California Consumer Privacy Act.

David Harrington
10 min read
-
 Data Security Privacy & Compliance
Data Security Privacy & ComplianceMar 10, 2023
HIPAA Compliance: Your Complete 2025 Checklist
Is your organization ready to comply with 2025 HIPAA updates and changes? Ensure HIPAA compliance with our comprehensive checklist.

Daniel Miller
12 min read
-
 Varonis Products
Varonis ProductsMar 08, 2023
How Varonis Saves Salesforce Admins Hours in Their Day
Varonis provides industry leading Salesforce management and permission implications capabilities to help save Salesforce admins hours in their day.

Nathan Coppinger
7 min read
-
 Threat Research
Threat ResearchFeb 20, 2023
HardBit 2.0 Ransomware
HardBit is a ransomware threat that targets organizations to extort cryptocurrency payments for the decryption of their data. Seemingly improving upon their initial release, HardBit version 2.0 was introduced toward the end of November 2022, with samples seen throughout the end of 2022 and into 2023.

Jason Hill
8 min read
-
 Threat Research
Threat ResearchFeb 08, 2023
Neo4jection: Secrets, Data, and Cloud Exploits
With the continuous rise of graph databases, especially Neo4j, we're seeing increased discussions among security researchers about issues found in those databases. However, given our experience with graph databases ― from designing complex and scalable solutions with graph databases to attacking them ― we've noticed a gap between public conversations and our security researchers' knowledge of those systems.

Nitay Bachrach
15 min read
-
 Threat Research
Threat ResearchFeb 07, 2023
VMware ESXi in the Line of Ransomware Fire
Servers running the popular virtualization hypervisor VMware ESXi have come under attack from at least one ransomware group over the past week, likely following scanning activity to identify hosts with Open Service Location Protocol (OpenSLP) vulnerabilities.

Jason Hill
10 min read
-
 Varonis Products
Varonis ProductsFeb 07, 2023
Varonis Enhances GitHub Security Offering With Secrets Discovery and Data Classification
Varonis is extending our world-class data classification capabilities to discover secrets, keys, and other sensitive data embedded in your GitHub repositories and source code.

Nathan Coppinger
3 min read
-
 Varonis Products
Varonis ProductsJan 31, 2023
Varonis Announces Proactive Incident Response for SaaS Customers
Varonis offers the brightest minds in offensive and defensive security, watching your data for threats.

Yumna Moazzam
3 min read
-
 Varonis Products
Varonis ProductsJan 26, 2023
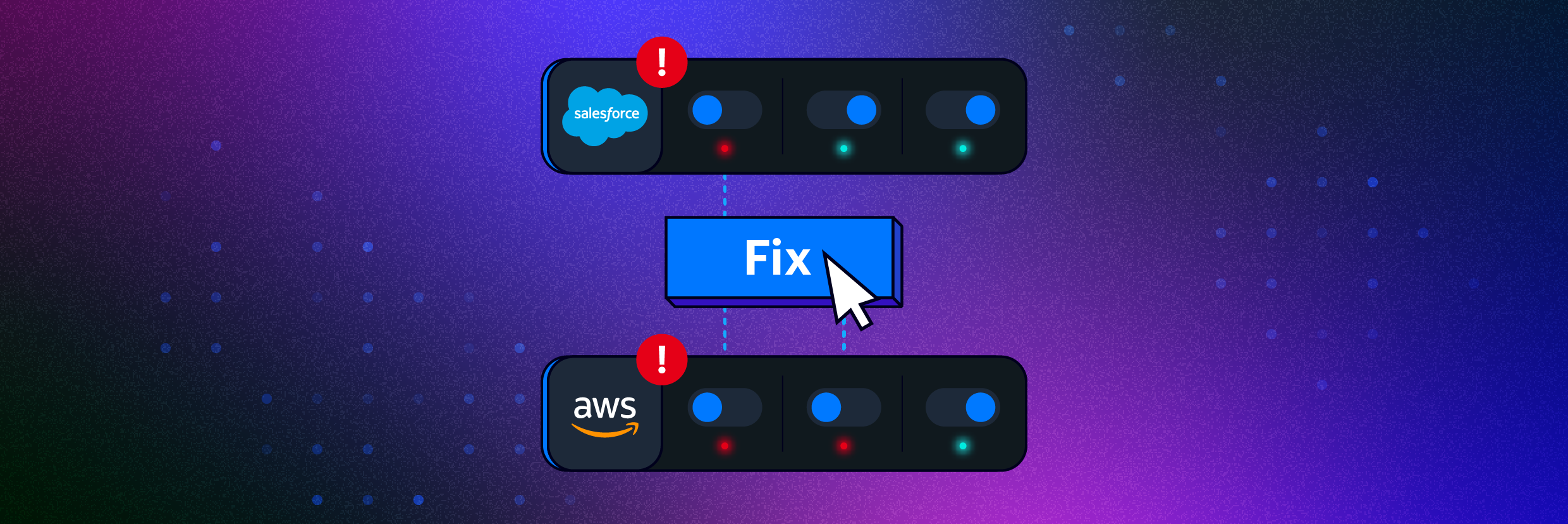
Introducing Automated Posture Management: Fix Cloud Security Risks with One-Click
Varonis launches Automated Posture Management to effortlessly fix cloud Security risks with a simple click of a button

Nathan Coppinger
3 min read
-
 Threat Research
Threat ResearchJan 23, 2023
CrossTalk and Secret Agent: Two Attack Vectors on Okta's Identity Suite
Varonis Threat Labs discovered and disclosed two attack vectors on Okta's identity suite: CrossTalk and Secret Agent.

Tal Peleg and Nitay Bachrach
7 min read
-
 Varonis Products
Varonis ProductsJan 17, 2023
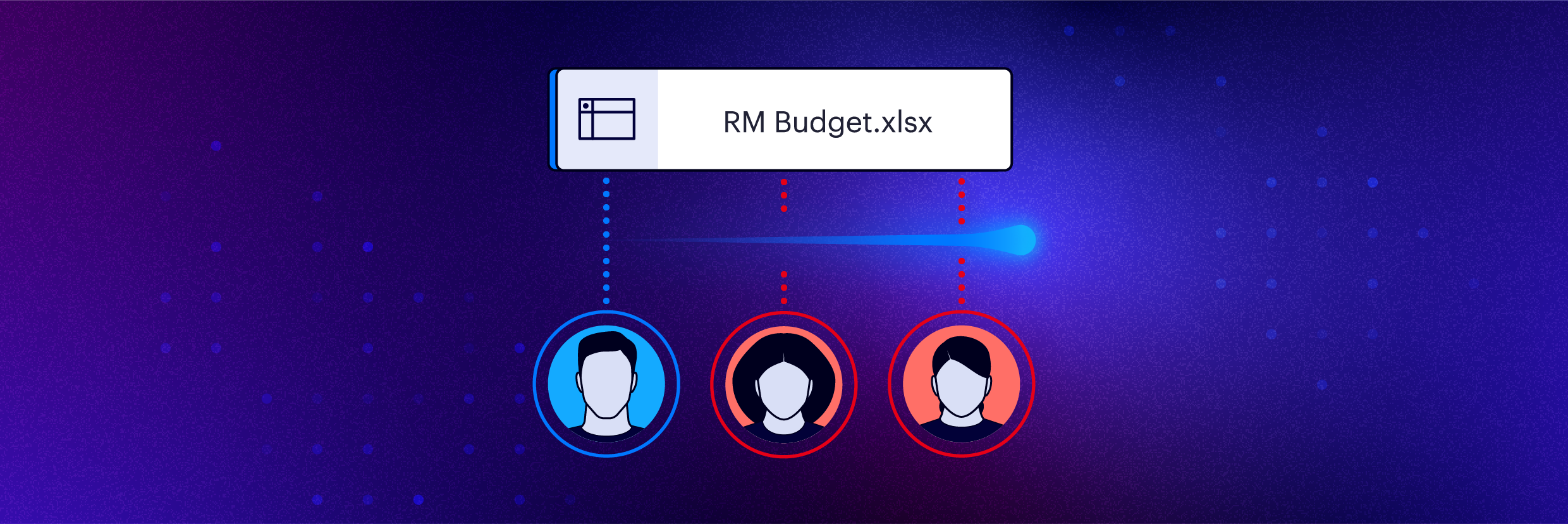
Introducing Least Privilege Automation for Microsoft 365, Windows, Google Drive, and Box
Varonis announces least privilege automation for Microsoft 365, Google Drive, and Box.

Yumna Moazzam
4 min read
-
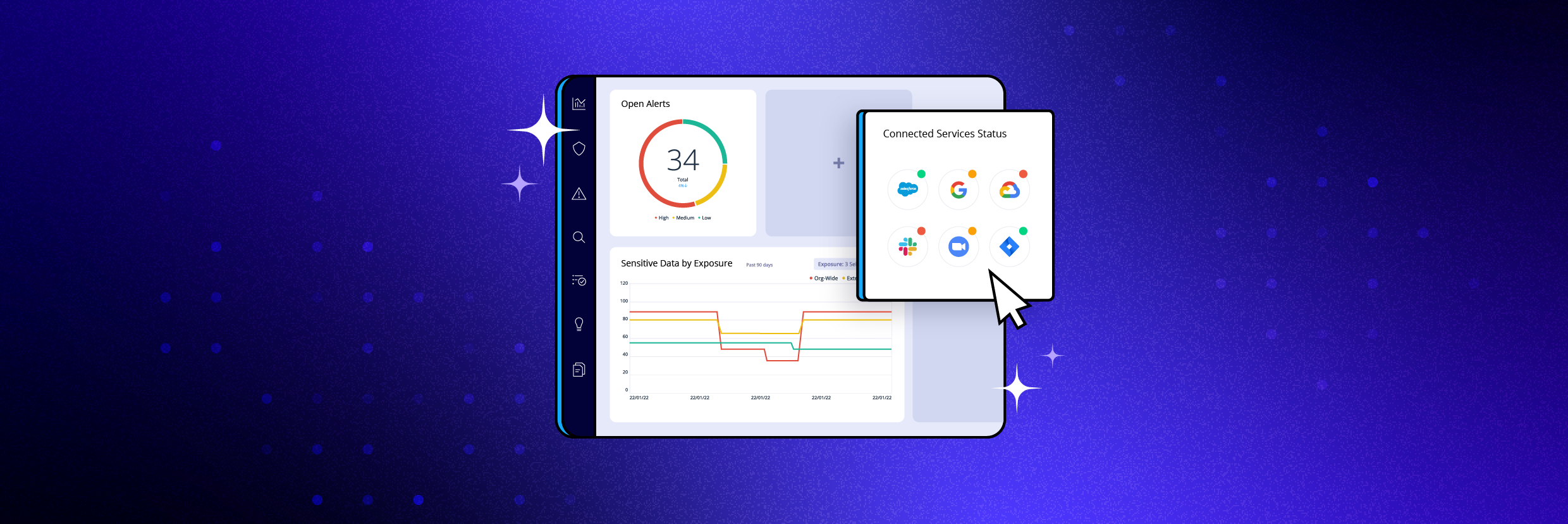 DSPM Varonis Products
DSPM Varonis ProductsJan 03, 2023
Varonis Launches Customizable Data Security Posture Management (DSPM) Dashboard
Varonis introduces a new customizable DSPM dashboard to help improve data security posture management

Nathan Coppinger
3 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital