One of the most critical security concepts is permissions management: ensuring that proper permissions are set with users – and that usually means knowing the difference between share and NTFS permissions.
Share and NTFS permissions function completely separately from each other, but ultimately serve the same purpose: to prevent unauthorized access.
Get the Free Pen Testing Active Directory Environments EBook
However, when NTFS and share permissions interact or when a shared folder is in a separate shared folder with different share permissions, users might not be able to access their data or they can get higher levels of access than security admins intend.
Here are key differences between share and NTFS permissions so you’ll know what to do.
What is NTFS?
A file system is a way of organizing a drive, indicating how data is stored on the drive and what types of information can be attached to files, such as permissions and file names.
NTFS (NT File System) stands for New Technology File System (NTFS). NTFS is the latest file system that the Windows NT operating system uses for storing and retrieving files. Prior to NTFS, the file allocation table (FAT) file system was the primary file system in Microsoft’s older operating systems, and was designed for small disks and simple folder structures.
NTFS file system supports larger file sizes and hard drives and is more secure than FAT. Microsoft first introduced NTFS in 1993 with the release of Windows NT 3.1. It is the file system used in Microsoft’s Windows 10, Windows 8, Windows 7, Windows Vista, Windows XP, Windows 2000, and Windows NT operating systems.
NTFS Permissions
NTFS permissions are used to manage access to the files and folders that are stored in NTFS file systems.
To see what kind of permissions you will be extending when you share a file or folder:
- Right click on the file/folder
- Go to “Properties”
- Click on the “Security” tab
All then you’ll navigate this window:
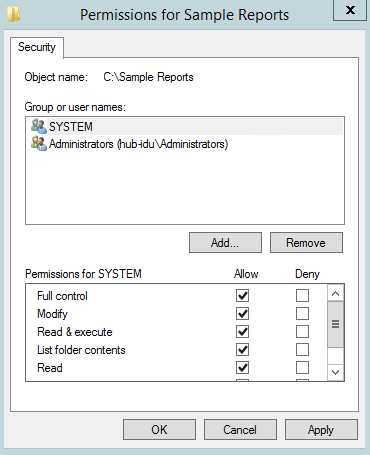
Besides Full Control, Change, and Read that can be set for groups or individually, NTFS offer a few more permission options:
- Full control: Allows users to read, write, change, and delete files and subfolders. In addition, users can change permissions settings for all files and subdirectories.
- Modify: Allows users to read and write of files and subfolders; also allows deletion of the folder.
- Read & execute: Allows users to view and run executable files, including scripts.
- List folder contents: Permits viewing and listing of files and subfolders as well as executing of files; inherited by folders only.
- Read: Allows users to view the folder and subfolder contents.
- Write: Allows users to add files and subfolders, allows you to write to a file.
If you’ve ever involved in permissions management within your organization, you’ll eventually encounter ‘broken’ permissions. Rest assured, they’re repairable.
Share Permissions
When you share a folder and want to set the permissions for that folder – that’s a share. Essentially, share permissions determine the type of access others have to the shared folder across the network.
To see what kind of permissions you will be extending when you share a folder:
- Right click on the folder
- Go to “Properties”
- Click on the “Sharing” tab
- Click on “Advanced Sharing…”
- Click on “Permissions”
And you’ll navigate to this window:
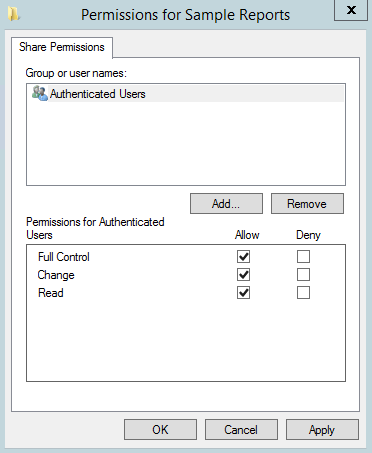
There are three types of share permissions: Full Control, Change, and Read.
- Full Control: Enables users to “read,” “change,” as well as edit permissions and take ownership of files.
- Change: Change means that user can read/execute/write/delete folders/files within share.
- Read: Read allows users to view the folder’s contents.
A Caveat on Share Permissions
Sometimes, when you have multiple shares on a server which are nested beneath each other, permissions can get complicated and messy.
For instance, if you have a “Read” folder in a subfolder share permission but then someone creates a “Modify” share permission above it at a higher root, you may have people getting higher levels of access then you intend.
There’s a way around this, which I’ll get to below.
How to Use Share and NTFS Permissions Together
One of the common questions that comes up when you’re configuring security is “what happens when share and NTFS permissions interact with each other?”
When you are using share and NTFS permissions together, the most restrictive permission wins.
Consider the following examples:
If the share permissions are “Read”, NTFS permissions are “Full control”, when a user accesses the file on the share, they will be given “Read” permission.
If the share permissions are “Full Control”, NTFS permissions are “Read”, when a user accesses the file on the share, they will still be given a “Read” permission.
Managing NTFS Permissions and Share Permissions
If you find working with two separate sets of permissions to be too complicated or time consuming to manage, you can switch to using only NTFS permissions.
When you look at the examples above, with just three types of permissions setting, shared folder permissions provide limited security for your folders. Therefore, you gain the greatest flexibility by using NTFS permissions to control access to shared folders.
Moreover, NTFS permissions apply whether the resource is accessed locally or over the network.
To do this, change the share permissions for the folder to “Full Control.”
You can then make whatever changes you want to the NTFS permissions without having to worry about the share permissions interfering with your changes.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.







-1.png)



