One of the lessons learned from the uptick in ransomware attacks is that it pays to keep your security patches up to date. A few months ago the SamSam/Samas malware was (and is still) having great success primarily against healthcare companies and hospitals.
The attack vector, though, was not based on phishing or social engineering. SamSam instead exploits a very old (and surprising) vulnerability in JBoss, Red Hat’s Java-based web server environment.
No Phishing
JMX is the administrative console web app for JBOSS — yes, everything starts with a J. Unfortunately, by default, the JMX home page is available externally without any authentication checks.
Like any good admin took, JMX gives you access to some basic functions including running Java code.
Are you thinking what I’m thinking?
Hackers discovering this JBoss vulnerability quickly realized that if they could upload a simple shell they were on their way to controlling the server.
And that’s the way this exploit works. If you want to read the technical details and the coding involved, you can google on “jboss vulnerability”.
This is a very well-known security hole – the CVE dates back to 2010—and it has since been patched.
But it has come back into the limelight because the SamsSam ransomware has very successfully used it against healthcare orgs, which for whatever reasons are more likely to have JBoss installations.
Once the cyber thieves gain entry through JMX, they upload the ransomware. And start collecting the fees. No phishing required.
How bad is the problem?
According to Cisco security researchers, there could be as many as 3.2 million installations at risk.
Remote Access Trojan by Any other Name
Attackers can find sites that have JBoss by Google dorking, which allows you to search for part of the telltale URL – in this case “jmx-console”—that indicates a JBoss server on an exposed site.
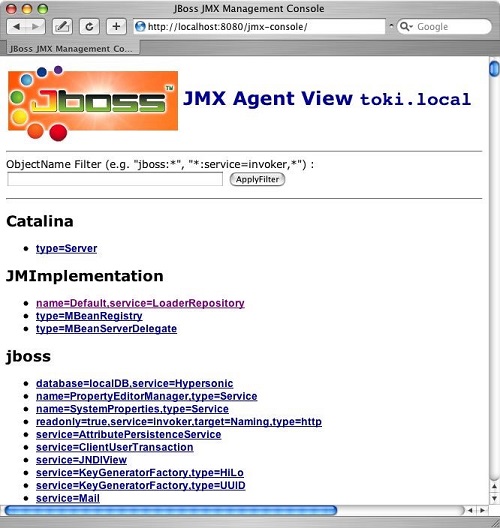
In looking at the JBoss attack techniques, I saw lots of code where the JMX interface acts as starting point to uploading and launching other software, say a reverse shell. So the vulnerability leaves open other attacks, not necessarily ransomware.
To put it bluntly, the JMX interface is an unintentional Remote Access Trojan or RAT, which we wrote about in our pen testing series.
Normally the attacker has to first install the RAT, but with these unpatched Red Hat installations it’s there — gasp!— waiting for them.
Maybe it’s a good time now to bring all your systems up to date with the latest security patches — I’m talking to you healthcare orgs!
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.





