The MITRE ATT&CK framework is a global knowledge base hub for documenting various tactics and techniques that hackers use throughout the different stages of a cyberattack. The MITRE company began developing the database in 2013, and over the years it's become a key resource for cyber defense teams in assessing the vulnerabilities and security protocols.
ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. The framework is a matrix of different cyberattack techniques sorted and organized by various tactics. Moreover, there are different matrices for Windows, Linux, Mac, and mobile systems. Using the MITRE ATT&CK matrix is an extremely useful tool in knowing what attack vectors that hackers might use against your company and how to optimize your incident response plan and penetration testing.
- MITRE ATT&CK Today
- MITRE ATT&CK Matrix: Top 5 Techniques
- MITRE ATT&CK Uses
- MITRE ATT&CK Challenges and Solutions
- Benefits of ATT&CK for Mitigating Threats
- Top ATT&CK Tools and Resources
MITRE ATT&CK Today
The ATT&CK matrix is one of the most complete and definitive resources of hacker techniques available today. Some of the latest evolutions and developments in the ATT&CK framework are:
- Improvement and expansion of Linux and Mac coverage
- Adding more data sources to help grow the matrix
- Consolidating cloud platforms and improving cloud data
- Refining and expanding mobile attack database
- Investigating container-based attack techniques
MITRE is extremely committed to keeping the ATT&CK matrix current and comprehensive, and you can expect them to make additions and changes as the nature of cyber threats evolve on a continual basis.
MITRE ATT&CK Matrix: Top 5 Techniques
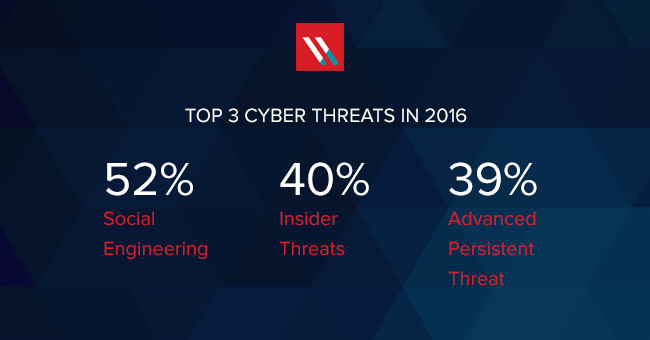
The primary goal of the ATT&CK framework is to enhance post-compromise detection of malicious actors that target enterprise networks, systems, and data. When utilizing ATT&CK, organizations gain insight into the actions an attacker might take. Things like how the attacker entered the system, how they're moving around, and what areas they're targeting become apparent.
The knowledgebase is designed to answer key questions about how hackers might target a specific company, as well as contribute to overall organizational security posture. Using ATT&CK helps identify holes and vulnerabilities, helping companies then prioritize them based upon overall risk.
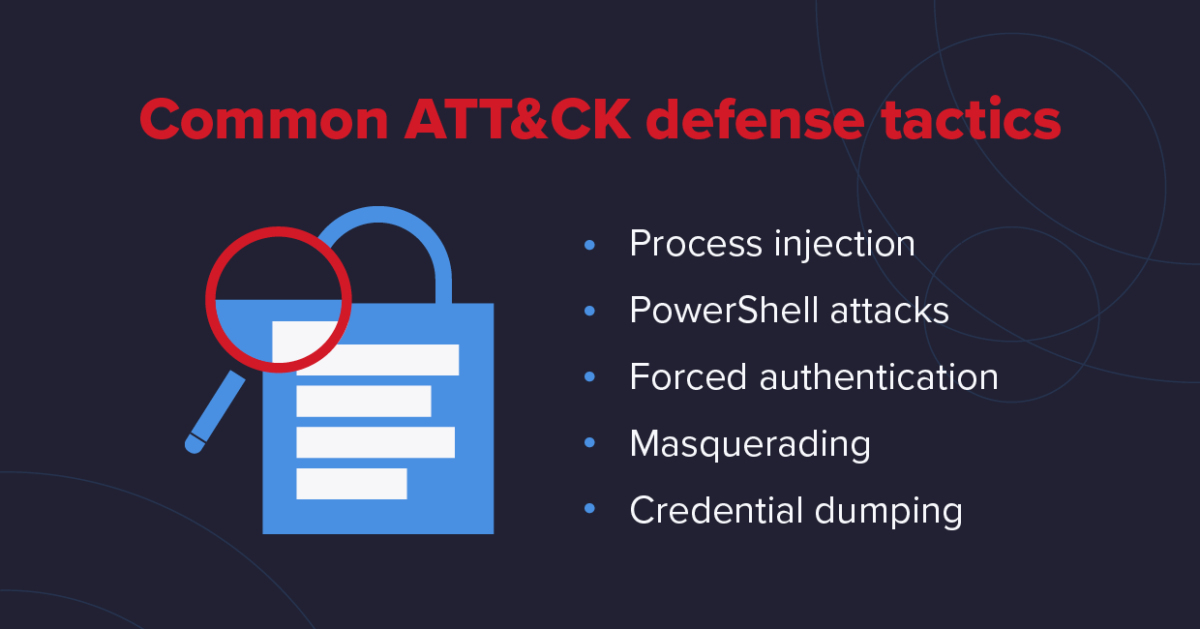
There are too many specific techniques to list here - over 290 in particular - but here are some of the top ATT&CK tactics that businesses can utilize to improve their overall cybersecurity posture.
1. Process Injection
One of the most common forms of malware attacks in the matrix, process injection involves inserting active code or applications into a system for malicious purposes. The code will then do several things, such as disable systems for ransomware purposes or automatically steal data. Simulating process injection is a great place to start for new ATT&CK users.
2. PowerShell Attacks
PowerShell attacks are extremely popular amongst hackers because it's the interface the system administrators use to manage and configure operating systems. PowerShell is a command-line shell and scripting language installed by default on Windows, so any company leaning on Windows should strongly consider using PowerShell exercises using MITRE ATT&CK.
3. Forced Authentication
Hackers today possess extremely powerful tools - such as Mimikatz - designed to either guess passwords or bypass login and authentication processes altogether. Hackers gather credential material by invoking or forcing a user to automatically provide authentication information through methods like phishing or social engineering.
4. Masquerading
Hackers often change the features of their malicious code or other artifacts so that they appear legitimate and trusted. Code signatures, names, and location of malware files, names of tasks, and services are just a few examples. Conducting MITRE ATT&CK exercises can help you discover how hackers might masquerade in your system and how to weed them out more effectively.
5. Credential Dumping
Once adversaries gain access to a system, one of their primary objectives is finding credentials to access other resources and systems in the environment. Credential dumping is a key mechanism to obtaining account login and password information, making it one of the top tactics to utilize in the ATT&CK matrix to guard against unauthorized access.
MITRE ATT&CK Uses
Once you decide which tactics, techniques, and vectors to test, you're ready to put the MITRE ATT&CK matrix into action. Here are the top ways you can utilize ATT&CK:
- Plan your cyber security strategy. Build your defense to counter the known techniques and equip your monitoring to detect evidence of ATT&CK techniques in your network.
- Reference your Incident Response (IR) teams. Your IR team can use ATT&CK to determine the nature of potential threats and methods needed to mitigate them.
- Future IR Planning Reference. Your IR team can use ATT&CK as a reference for new cybersecurity threats, and plan ahead.
- Overall Cyber Defense Assessment. ATT&CK can help you assess your overall cybersecurity strategy and close any gaps that you discover.
MITRE ATT&CK Challenges and Solutions
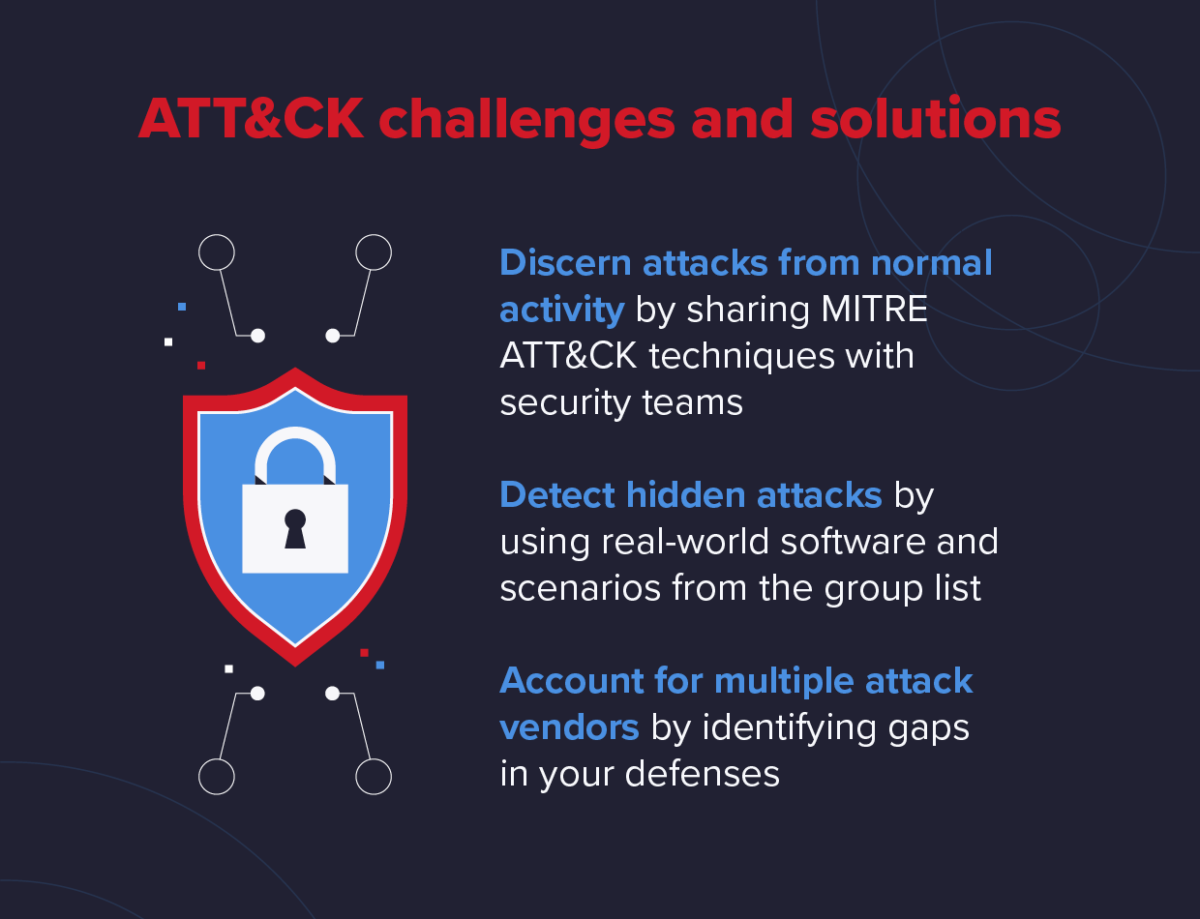
When using the ATT&CK framework, there are several unique challenges that you'll need to keep an eye out for. Thankfully, there are tactics and solutions to issues like differentiating attacks from normal activity or accounting for multiple vectors.
1. Discerning Attacks from Normal Activity
Not every behavior that matches a MITRE ATT&CK technique is malicious. File Deletion, for instance, is a listed technique under Defense Evasion -- which makes total sense. But how are you going to discern normal file deletes from an attacker's attempts to evade detection?
The first step is to Socialize and share MITRE ATT&CK techniques as a common language for your security teams. You should also work with an experienced cybersecurity partner well-versed in the ATT&CK framework to help you separate normal activities from malicious ones.
2. Detecting Difficult to Discover Attacks
Similarly, some ATT&CK techniques are difficult to detect even on a good day. Brute Force attacks are easy to detect if you know what to look for. Exfiltration over Alternative Protocol, like a DNS tunnel, can be quite difficult to detect even if you are looking for it.
The ability to discover difficult-to-find techniques is key to your long-term data security strategy. You'll want to use real-world software and scenarios from the Groups list. If you can't protect against the known threats, there is no way you can stop the unknown, hard-to-spot threats.
3. Accounting for Multiple Attack Vectors
Never assume that since you can defend against a technique in one way, you won't get dinged by a different implementation of that technique designed to attack the same targets. Just because your Anti-Virus catches "Mimikatz," don't assume it will also catch "tnykttns" -- or whatever variant of Mimikatz comes out next.
That's why it's critical to Identify gaps in your defenses with the MITRE ATT&CK matrices and implement solutions for those gaps. One of the biggest benefits of using MITRE ATT&CK is seeing how and where hacks might come from multiple angles, sources, and vectors.
Benefits of ATT&CK for Mitigating Threats
Using the ATT&CK framework helps organizations not only spot potential weaknesses but understand how hackers are likely to behave in the event of an attack. Moreover, you'll recognize the specific tactics and techniques they're likely to use and determine how best to guard against them.
Reconnaissance
- Active scanning
- Information phishing
- Gathering victim information
Initial access
- Supply chain compromise
- Exploit public facing apps
- Drive-by compromise
Privilege escalation
- Hijack execution flow
- Process injection
- Create or modify system process
Defense evasion
- Access token manipulation
- Impair overall defenses
- Masquerading
Lateral movement
- Remote session hijacking
- Internal spear phishing
- Use alternate authentication
Command and control
- Data encoding & obfuscation/li>
- Traffic signaling
- Protocol tunneling
Exfiltration
- Automated exfiltration
- Data transfer to cloud accounts
- Scheduled data transfer
Impact
- Data destruction or manipulation
- Network denial of service
- Disk wipe or defancement
Examples of some of the core techniques and tactics in the ATT&CK framework
MITRE ATT&CK vs. Cyber Kill Chain
The main difference between ATT&CK and the typical Cyber Kill Chain is that the Kill Chain focuses on a specific order of operations, while ATT&CK centers around techniques and tactics. However, the common thread is that they both seek to understand how hackers try to infiltrate and affect systems without getting caught.
The Cyber Kill Chain progresses in a well-defined sequence. The Red Team, or attackers during a penetration testing exercise, move from reconnaissance to intrusion and onto the next stages. Conversely, the Red Team uses ATT&CK techniques from different tactics at different times of the scenario depending on the situation.
An ATT&CK scenario could start with a Hardware Addition from the Initial Access tactic, then jump to Bypass User Account Control from the Privilege Escalation tactic and go back to the Execution tactic to run PowerShell.
ATT&CK defines the following tactics used in a cyberattack:
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Exfiltration
- Command and Control
The Cyber Kill Chain, on the other hand, is a sequential framework as follows:
- Reconnaissance
- Intrusion
- Exploitation
- Privilege Escalation
- Lateral Movement
- Obfuscation/ Anti-forensics
- Denial of Service
- Exfiltration
A successful cyber defense strategy will leverage both the Cyber Kill Chain and ATT&CK frameworks to determine vulnerabilities and how best to address them.
How to Use MITRE ATT&CK to Help Your Business
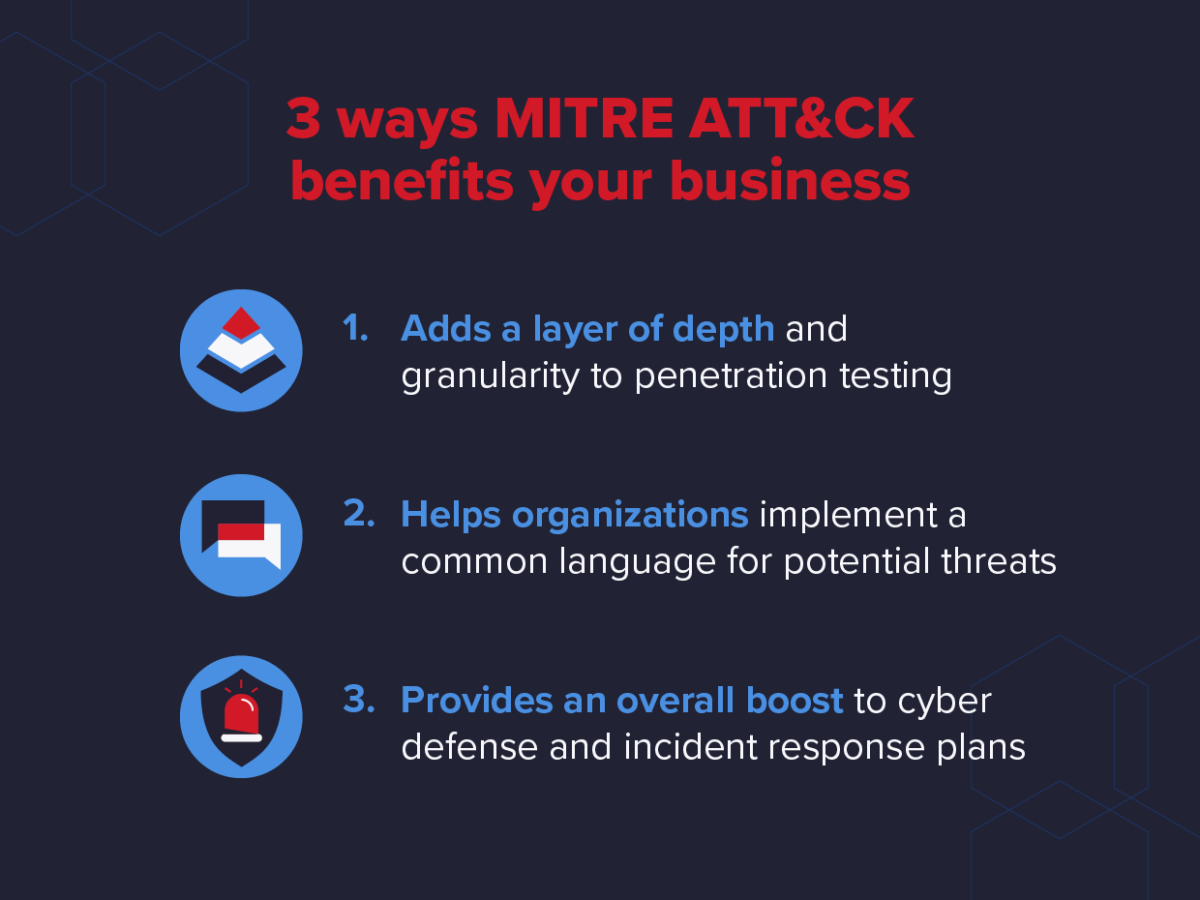
Using ATT&CK has several unique, core benefits to businesses. First, the framework adds a layer of depth and granularity to penetration testing. Red Teams can focus on various techniques, tactics, and vectors during different penetration testing exercises, covering a wide swath of potential attack surfaces.
ATT&CK also helps organizations implement a common language and understanding of potential cyber threats within an organization. Therefore, when teams are communicating about things like Exfiltration or Lateral Movement, members know specifically which tactics are covered under those umbrellas and can coordinate better for mitigation and prevention.
Finally, ATT&CK provides a huge boost to overall cyber defense and incident response plans. Knowing which specific tactics that your organization is most vulnerable to helps businesses put the right safeguards in place. If your penetration testing using ATT&CK finds that social engineering might be most prevalent, for instance, you can develop your plans around that specific vector.
Top ATT&CK Tools and Resources
The following list of helpful tools and resources when utilizing the ATT&CK framework:
- Caldera -- MITRE's automated attach technique emulation tool
- DatAlert -- Data-centric threat detection solution from Varonis
- Cascade -- This is MITRE's Blue Team automation toolset
- DatAdvantage -- Audit, and protection for hybrid environments
- Oilrig -- An adversary Playbook built on the ATT&CK model.
Closing Thoughts
One of the best ways to maximize the benefits you get from ATT&CK is by using it in tandem with a data protection platform and partner like Varonis. Conducting your penetration testing using the ATT&CK framework will also let you know which specific techniques and tactics that hackers are most likely to use, along with how they'll probably behave.
The MITRE ATT&CK framework is thorough, comprehensive, and ever-changing. So, if you're interested in learning more about how to improve your penetration testing, cybersecurity policy, or incident response plan using ATT&CK, connect with an expert at Varonis today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.