Social engineering sits at the crossroads of cybersecurity and psychology, exploiting human behavior to achieve malicious goals. From Kevin Mitnick's legendary frauds to today's AI-driven threats, this blog post by Kyle Nielsen and Tom Barnea delves into real-world examples and uncovers sophisticated techniques discovered by our Managed Data Detection and Response (MDDR) team during recent investigations.
Continue reading to see how the threat landscape has evolved and how attackers are able to execute cyberattacks with specific examples.
The Nigerian Prince is dead, long live the Vishing!
First, let’s look at common types of social engineering tactics and how they’ve evolved.
The classic scam of the “Nigerian Prince”, also known as the “Nigerian Scam” or the “419 scam,” is classified as an Advance-Fee Scam. This scam involves a fraudster posing as a wealthy individual who needs help transferring a large sum of money out of their country, promising a share of the fortune in return. Once you agree, they ask for upfront fees or personal information, but you never receive any money.
According to the FBI, "an advance fee scheme occurs when the victim pays money to someone in anticipation of receiving something of greater value –– such as a loan, contract, investment, or gift –– and then receives little or nothing in return." In these types of scams, threat actors send thousands of emails, hoping to deceive as many people as possible.
Today, social engineering attacks have become more strategic and precise, with attackers shifting their focus from trying to extract small amounts of money from many to targeting individuals who have more authority within organizations, such as elevated permissions in their network, access to remote tools and sensitive data, and the ability to make significant financial transactions.
Phishing attacks have also evolved from broad, indiscriminate methods to more targeted approaches such as spear phishing and whaling. Spear phishing involves targeting specific individuals with personalized emails, while whaling focuses on high-profile targets like CFOs and CEOs.
With these changes, these attacks tend to be much quieter, and if the hacker succeeds, the payoff can be significantly greater. For example, imagine you observe 100 emails in your Exchange logs from an external sender to multiple users simultaneously versus a single email sent to the CFO or the IT director. What would raise more suspicion?
AI – Attacker intelligence
The rise of AI technologies has undoubtedly changed the landscape of social engineering. One technique that has seen significant advancements is Pretexting. Pretexting occurs when the victim feels compelled to follow the attacker’s instructions based on false pretenses. In this method the attacker impersonates a partner, client, or a high-ranking executive of the organization.
Our MDDR forensics experts assisted in an investigation with a large wealth management company. This company fell victim to a highly sophisticated social engineering attack. The attackers conducted extensive research and specifically focused on a high-level group manager in the finance department.
The attack began with a fake non-disclosure agreement (NDA) that looked like it came from DocuSign, pretending to be a legal third party the organization usually works with. The manager signed the document and was then told to call the phone number in the email. However, no one answered the call.
The following day, the attacker called the manager back with the “CEO”. On a conference call, the CEO confirmed the NDA was legitimate and a deposit was required to initiate the work. As a result, the group manager transferred a deposit of 1 million euros to the scammer.
During the investigation, it became apparent that the real CEO was never part of the call. The threat actor had cloned the CEO's voice, using his public profile to manipulate the group manager.
It’s raining (phishing) emails
What could make you feel more helpless and desperate than an IT issue on your busiest day at work? Unlike other attacks in the cybersecurity landscape, social engineering does not focus on exploiting code or network architecture flaws. Instead, it takes advantage of human behavior, which is often the weakest link in the security chain.
Recently, our forensics team investigated several cases and discovered a pattern that highlights how advanced and strategic social engineering attacks have become.
Step 1. Create a problem:
Attackers may create technical issues to make their stories more convincing. One common method is Email Bombing, or Graymail Flood, where the attacker signs up the victim's email to numerous services, resulting in an overwhelming number of emails. These emails are legitimate but can arrive in massive quantities quickly. For instance, one victim received 3,000 emails in under 2 hours.
Step 2. Impersonate the savior:
Who do we call if not the IT guy? The victim received a call from someone pretending to be a Help Desk Manager claiming they could help solve the problem and let them continue their workday as planned. This scenario involves two types of social engineering attacks:
- Vishing, which stands for Voice Phishing. In this tactic, the scammer attempts to trick the victim into providing their credentials or granting access to their desktop via phone call.
- Quid Pro Quo: In this method, the attacker offers a service in exchange for information or access, often by posing as a member of the IT department seeking to resolve a technical issue.
These tactics represent simple ways for an attacker to gain access to a user's device without delving into the complexities of developing sophisticated malware.
The snowball effect of social engineering
A great example of the snowball effect caused by a simple social engineering attack takes us back to September 2023.
MGM Resorts International, a leading hospitality and entertainment company, experienced a significant cyberattack that disrupted operations across its properties, including iconic Las Vegas venues like the Bellagio, Aria, and MGM Grand.
The breach was orchestrated by the hacking group Scattered Spider, also known as Starfraud, UNC3944, Scatter Swine, and Muddled Libra, known for their social engineering tactics.
They ran a complex vishing campaign by impersonating an MGM employee. The scammers got the employee’s details from LinkedIn and contacted MGM’s IT help desk. This allowed the attacker to obtain credentials granting access to MGM’s internal systems. MGM Resorts reported an estimated loss of $100 million due to the attack. The company chose not to pay the ransom demanded by the attackers. In the aftermath, multiple class-action lawsuits were filed against both MGM Resorts and Caesars Entertainment (which suffered a similar attack), alleging failure to protect customer data adequately.

Fool me once, shame on you; fool me twice, shame on me: Vishing in action
Since the MGM breach, Varonis Forensics has seen a large uptick in complex “vishing” attacks. In several cases, a threat actor, Black Basta, used legitimate “Microsoft Teams” tenants to gain the confidence of the victim via a Teams call from a user named “Helpdesk,” “Support Team,” or “Help Desk Manager.” The threat actor, posing as an internal IT member, socially engineers the victim into using a Windows native remote management tool called “Quick Assist.”
Using the “Quick Assist” tool lends credibility to a scammer's actions because it’s a legitimate Windows-native tool and doesn’t trigger any security alerts. The victim can be easily tricked by using the shortcut “ctrl + Windows key + Q” to open a window that generates a code. This code allows the threat access to the victim's computer. Once they have access, they can use whatever foothold they’ve gained to try to escalate their privileges and move laterally.
In the screenshot below, you can see a real chat on Teams between the threat actor and the victim.
Figure 1: A hacker impersonating an IT team member.
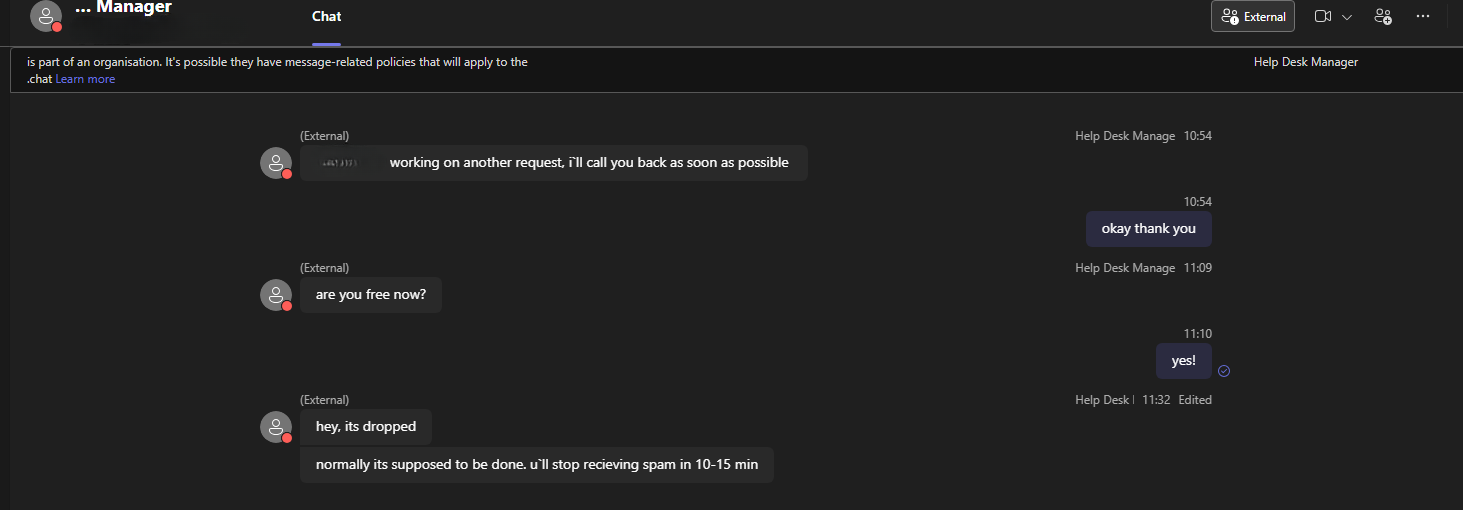
Figure 1: A hacker impersonating an IT team member.
The threat actor quickly moved from their initial foothold to the broader environment. Within just a few days, they managed to steal terabytes of files from across the entire environment.
How you can protect your organization
Preventing employees from falling victim to sophisticated social engineering traps can be complex and challenging. However, several technological and human strategies can help reduce the likelihood of attackers succeeding.
There are options in both Teams and Zoom to restrict communications solely to trusted domains and organizations.
While implementing and listing all trusted partners might take some time, we believe it is worth considering after discussing potential business disruptions internally.
Microsoft Teams plans to introduce a new phishing alert feature for all users. This feature will automatically check for phishing attempts in messages from external sources, prompting users with an "Accept or Block" option for potentially suspicious chats. This proactive measure aims to enhance security and protect users from phishing attacks.
Some threat actors exploit the built-in remote-control features of video chat applications. Both Zoom and Teams allow you to choose whether external participants can gain remote access to other participants' screens during a call. While there may be slight differences between the platforms regarding this option, we recommend reviewing the features of your chosen platform and configuring them to suit your organization's needs.
Implementing Conditional Access policies is a game changer in strengthening access controls in your organization. Conditional Access policies, at their simplest, are if-then statements; if a user wants to access a resource, then they must complete an action. For example: If a user wants to access an application or service like Microsoft 365, then they must perform multi-factor authentication to gain access.
You can implement Conditional Access policies to restrict access based on geo-location, user types, applications, and even a token protection policy. In today's security landscape, Multi-Factor Authentication (MFA) alone is insufficient, as attackers can conduct man-in-the-middle attacks using tools such as Evilginx or Mamba 2FA.
Data Access Governance
The principle of least privilege is one of the best ways to reduce the blast radius of a future attack. Varonis has your back and can help you visualize access to sensitive data across your environment and enhance access governance.
- User training: Keeping your organization's security awareness up to date can be challenging and frustrating. However, no matter how many technological barriers you put in place, one mistake by an unaware employee can cause significant damage. It is essential to continuously train your employees to prevent such incidents. Our recommendations are:
- Simulated phishing and vishing attacks: Regularly conduct simulated phishing and vishing attacks to test employees' responses. This helps identify vulnerabilities and provides real-world practice in recognizing and responding to social engineering attempts.
- Personalized Training: Tailor training sessions to different departments and roles within the organization. For example, finance teams might need more focused training on spear-phishing attempts around financial files, while customer service teams should be aware of vishing tactics.
- Incident reporting mechanisms: Establish clear and easy-to-use incident reporting mechanisms. Encourage employees to report suspicious activities without fear of repercussions, and ensure they know the proper channels to do so.
- Executive involvement: Ensure that executives and senior management are involved in training initiatives. Their participation underscores the importance of security awareness and sets a positive example for the rest of the organization.
Explore best practices guides by Zoom and Teams to their platforms that can help you make your next training much more precise to the platform you use.
Secure your cloud environment today
Don't leave your cloud security to chance. Implementing robust security measures is crucial to protecting your data, applications, and infrastructure from evolving threats.
With Varonis, you can enhance your SaaS and IaaS security posture through advanced visibility, automation, and threat detection solutions.
Learn how to reduce your risk with our free Data Risk Assessment. It takes minutes to set up and delivers immediate value. In less than 24 hours, you’ll have a clear, risk-based view of the data that matters most and a clear path to automated data security.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.