Malware has become one of the most pressing threats to organizations worldwide. Something as simple as opening a malicious email attachment can lead to data breaches, operational shutdowns, or millions of dollars in damages, especially if proper defenses aren’t in place.
Thankfully, there are a plethora of malware analysis tools to help curb these cyber threats. Today’s malware is not only more pervasive but also more advanced, often using artificial intelligence to evade traditional detection methods and adapt to dynamic environments.
To counter these evolving threats, security teams rely on a growing ecosystem of malware analysis tools designed to dissect, understand, and neutralize malicious code. During a typical incident response, digital forensics or research teams collect malware samples to reverse engineer their behavior and assess the scope of impact.
Fortunately, several powerful and entirely free open-source malware analysis tools are available to help analysts with this process.
In this article, I cover the top 12 malware analysis tools (in no particular order) on the market:
- PeStudio
- Process Hacker
- Process Monitor (ProcMon)
- ProcDot
- Autoruns
- Fiddler
- Wireshark
- X64dbg
- EMBER
- Ghidra
- MalConv
Malware analysis tools and techniques
Before running the malware to monitor its behavior, the first step is to perform some static analysis of the malware. The tools used for this type of analysis won’t execute the code, instead, they will attempt to pull out suspicious indicators such as hashes, strings, imports and attempt to identify if the malware is packed.
Once enough information has been pulled out from static tools and techniques, you can detonate the malware in a virtual machine specially built for running and analyzing malware.
While the malware is running you can use a number of tools to record its activity, also known as dynamic analysis. When dynamically analyzing a sample, you would look for any unique characteristics that can be attributed to this piece of malware. This may include looking for files created, changes to the registry which may be indicative of the malware building some persistence. or looking at network traffic to see what command and control (C2) infrastructure the malware calls out to.
Disclaimer: The tools in this article should be used in a sandboxed environment such as a virtual machine designed for analyzing malware. Do not attempt to analyze malware using these tools on your host operating system.1. PeStudio
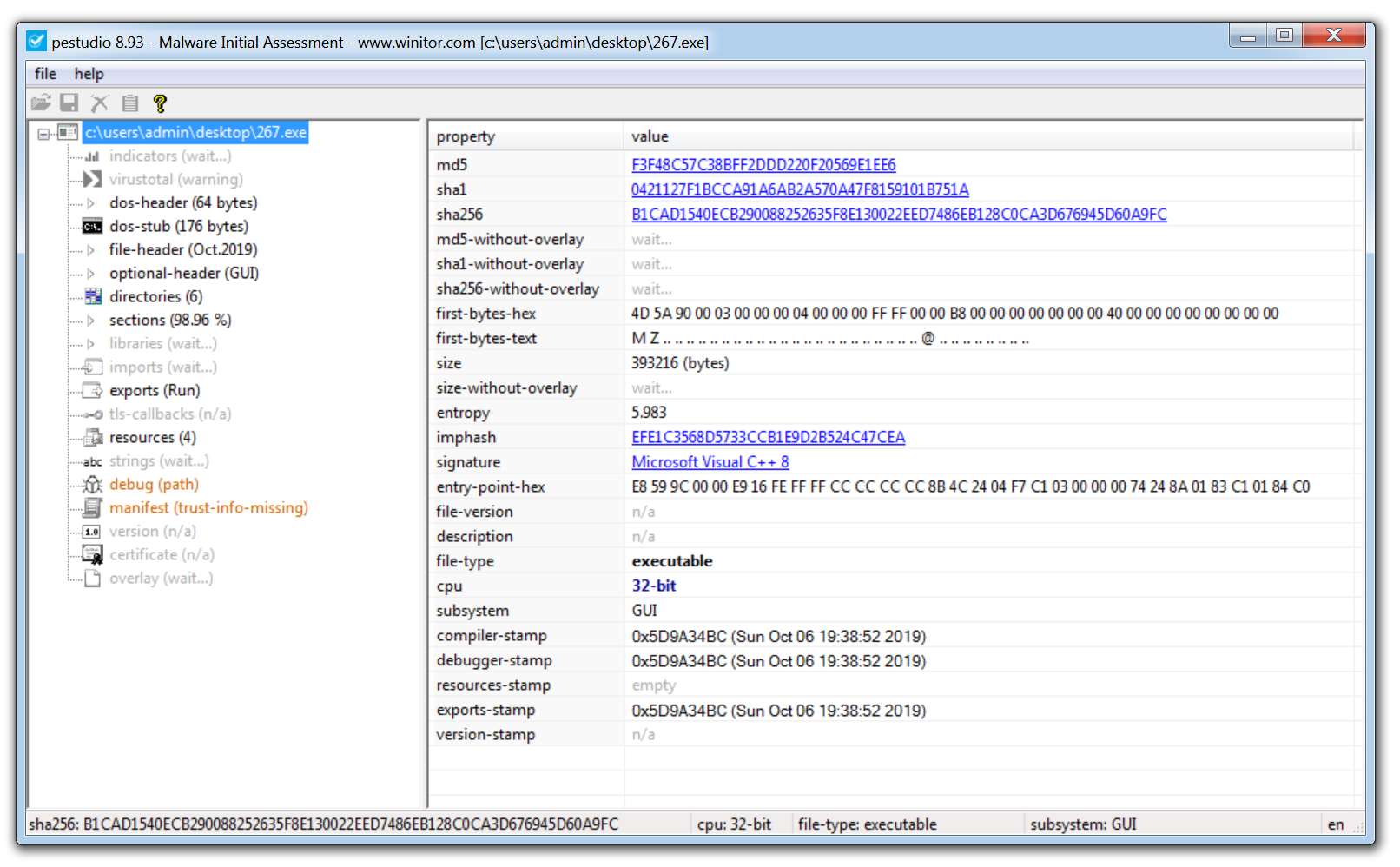
PeStudio is an excellent tool for conducting an initial triage of a malware sample and enables you to quickly pull out any suspicious artifacts.
Once a binary is loaded, the tool quickly generates hashes of the malware and checks them against VirusTotal for known detections. It also extracts a list of strings from the sample, which can offer valuable indicators of compromise (IOCs). However, if the binary is packed, the initial string analysis may yield limited results. In such cases, unpacking the sample first is recommended; this often reveals more meaningful data like malicious domains, IP addresses, and embedded commands.
The screenshot above also shows the ‘entropy’ of the malware. This helps identify whether the malware is packed or not. When a sample is packed, this means the malware author has effectively put a layer of code around the malware in order to obfuscate its true functionality and prevent analysis of the malware.
To assist with identifying packed malware, PeStudio displays the level of entropy of the file. Entropy is measured on a scale of 0-8, with 8 being the highest level of entropy. The higher the entropy the more likely that a piece of malware is packed.
Another useful section to examine is the Imports tab. This shows the external functions the malware relies on—typically pulled from Windows system libraries known as DLLs (Dynamic Link Libraries). These libraries contain Windows APIs, which are commonly used by legitimate software to perform routine operations like creating files, launching processes, or accessing network resources. For instance, the DLL Kernel32.dll includes the API CreateProcessW, which allows a program to start a new process.
Malware authors often use the same APIs to implement malicious functionality. Instead of writing custom code to, say, create a file on disk, the malware can simply import the CreateFileW API. By analyzing which functions are imported, a malware analyst can often infer the intended behavior of the sample—such as file creation, process injection, or network communication—before even executing it.
2. Process Hacker
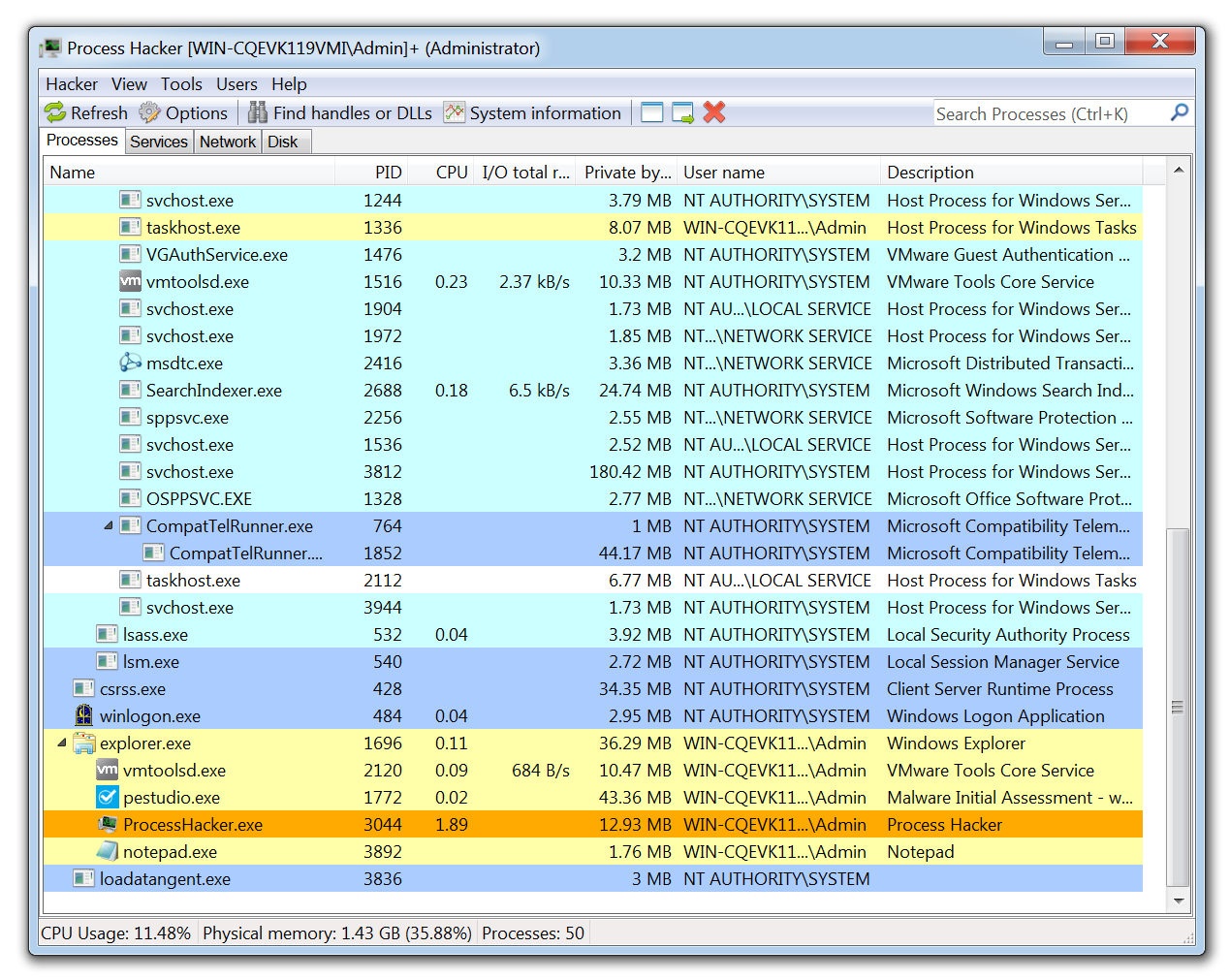
Process Hacker allows a malware analyst to see what processes are running on a device. This can be useful when detonating a piece of malware to see what new processes are created by the malware and where these are being run from on disk. Malware often attempts to evade detection by copying itself to a different location on the system and renaming the file. Tools like Process Hacker can reveal this behavior in real time, making it easier for analysts to spot how the malware is trying to conceal its presence.
This tool is also useful for pulling information from the memory of a process. This means that if a piece of malware is detonated then Process Hacker can be used to inspect the memory for strings, the strings found in memory will often return useful information such as IP addresses, domains, and user agents that are being used by the malware.
3. Process Monitor
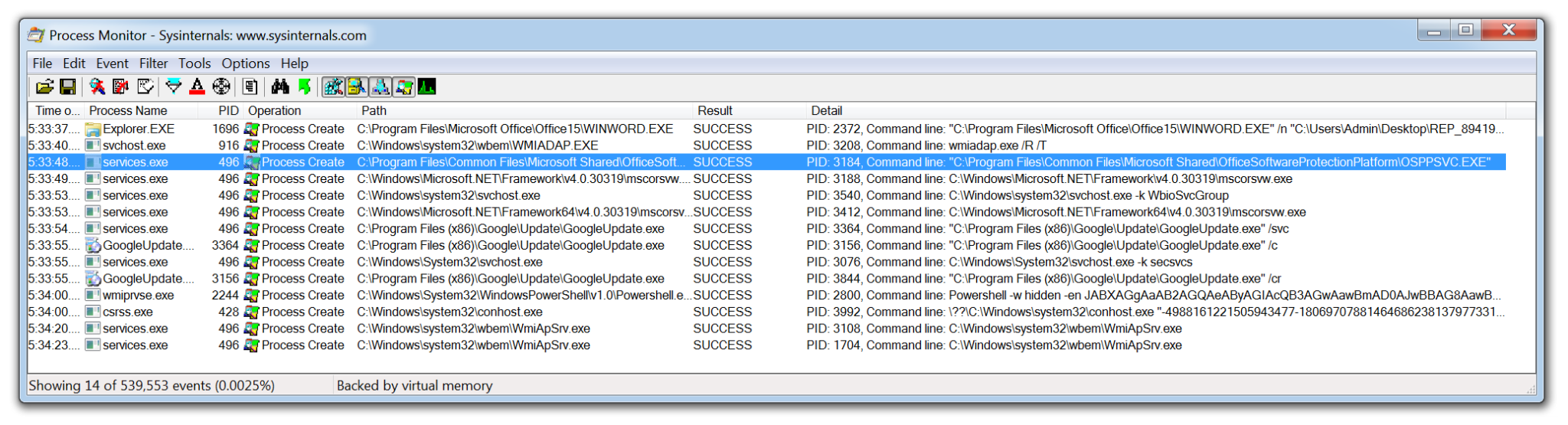
Process Monitor is a powerful tool from Microsoft which records live filesystem activity such as process creations and registry changes. This becomes especially useful when used alongside Process Hacker. For example, if a new process is created and then quickly terminated, it might be easy to miss, but ProcMon can still capture and log that activity. With built-in filters and the process tree view, analysts can quickly trace which processes were created, where the executables were run from, and how they relate to parent or child processes.
Process Monitor can be particularly useful when analyzing malicious documents. The threat actors behind Emotet often use malicious Word documents as an attack vector. The Word document will contain macros which when enabled will call out to the attackers C2 infrastructure and download the Emotet payload. None of this activity is visible to the user of the compromised device. By using Process Monitor, you are able to capture the Word document being opened, view the hidden PowerShell process being launched and the base64 encoded command being run.
One issue with this tool is that in a matter of seconds it can quickly record over 100,000 events. Although the filters are excellent, there is always a risk an event of interest could be missed. However, this data can be exported as a CSV and imported into the next tool on this list.
4. ProcDOT
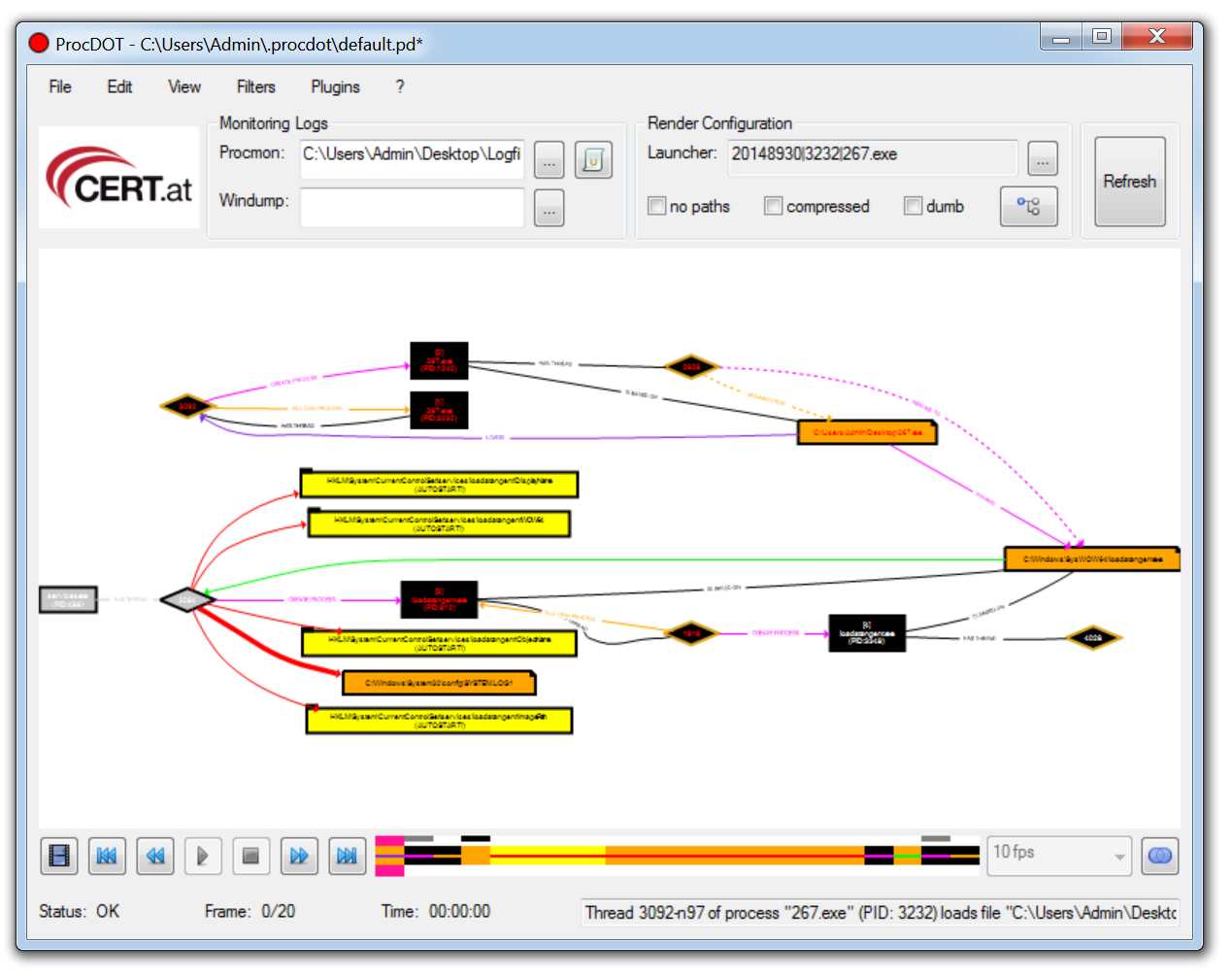
ProcDOT allows a malware analyst to ingest the output from Process Montior and automatically generate a graphical representation of the captured data. Simply upload the CSV into ProcDot and select the process name of the malware. Rather than creating filters and navigating hundreds of thousands of events, you are now able to navigate a visual diagram of what recorded malware activity.
Process Monitor data can also be enriched by ingesting a packet capture (PCAP) file, collected by a tool like Wireshark into ProcDOT.
5. Autoruns
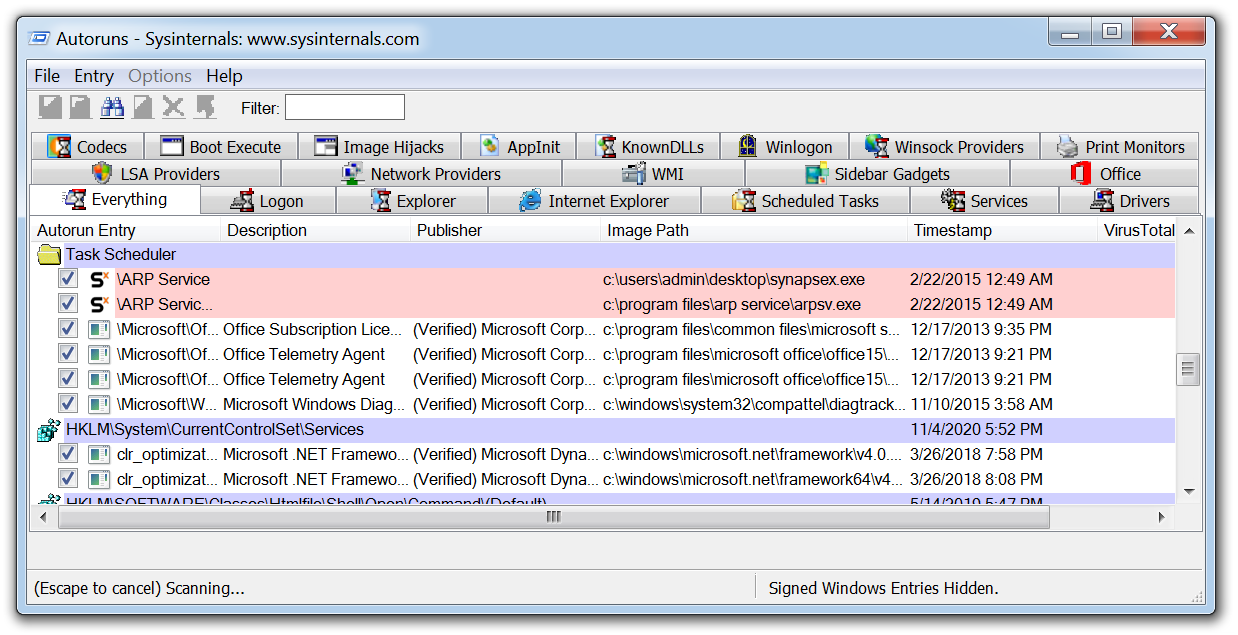
Autoruns is another Microsoft tool that will display any installed software on a device that is set to launch when a machine is powered on. Malware may try to hide, but eventually it has to execute. To survive a system reboot, it must establish some form of persistence mechanism.
Several techniques can be used by malware to achieve persistence, such as creating scheduled tasks or adding entries to specific registry run keys. After executing the malware in a virtual machine, tools like Autoruns can detect and highlight any newly added persistence mechanisms, making it a valuable resource for malware analysis.
6. Fiddler
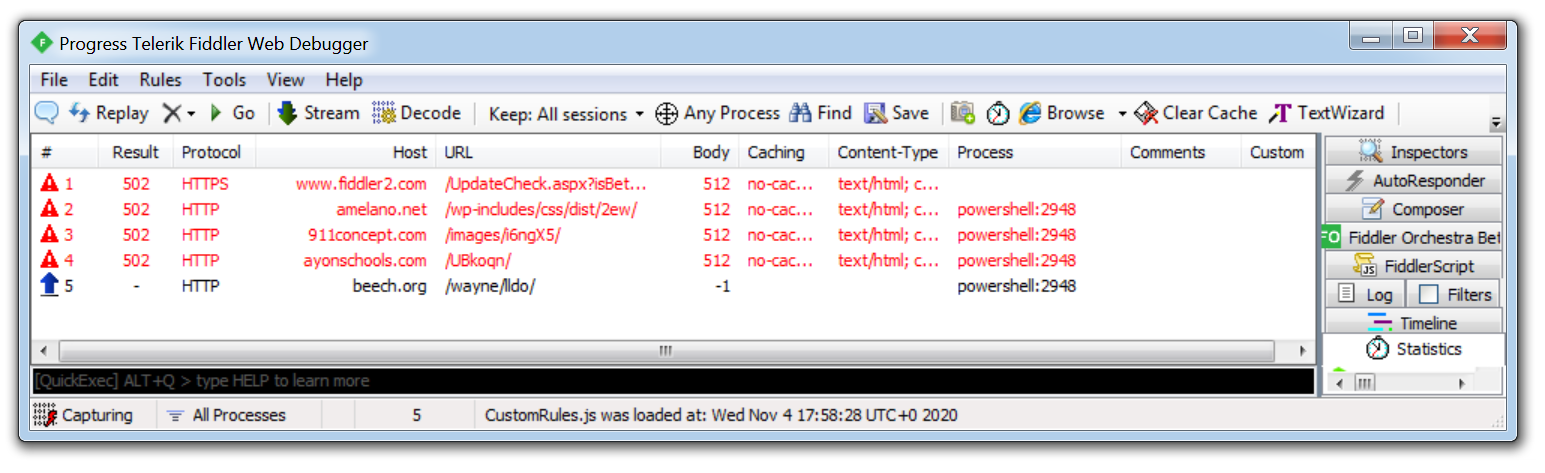
Malware will often use HTTP/HTTPS to contact its C2 servers and download additional malware or exfiltrate data. Using a tool such as Fiddler which acts as a web proxy allows this traffic to be captured and analyzed. This is especially useful when analyzing a malicious document that uses macros to download a payload. By running Fiddler, a malware analyst can identify the hardcoded domains embedded in the document revealing where the malware is being downloaded from.
In the example above, you can see how Fiddler was able to record a malicious Word document attempting to download Emotet from multiple websites hosting the malware, if the first attempt is unsuccessful it will move on to the next hardcoded domain.
7. Wireshark
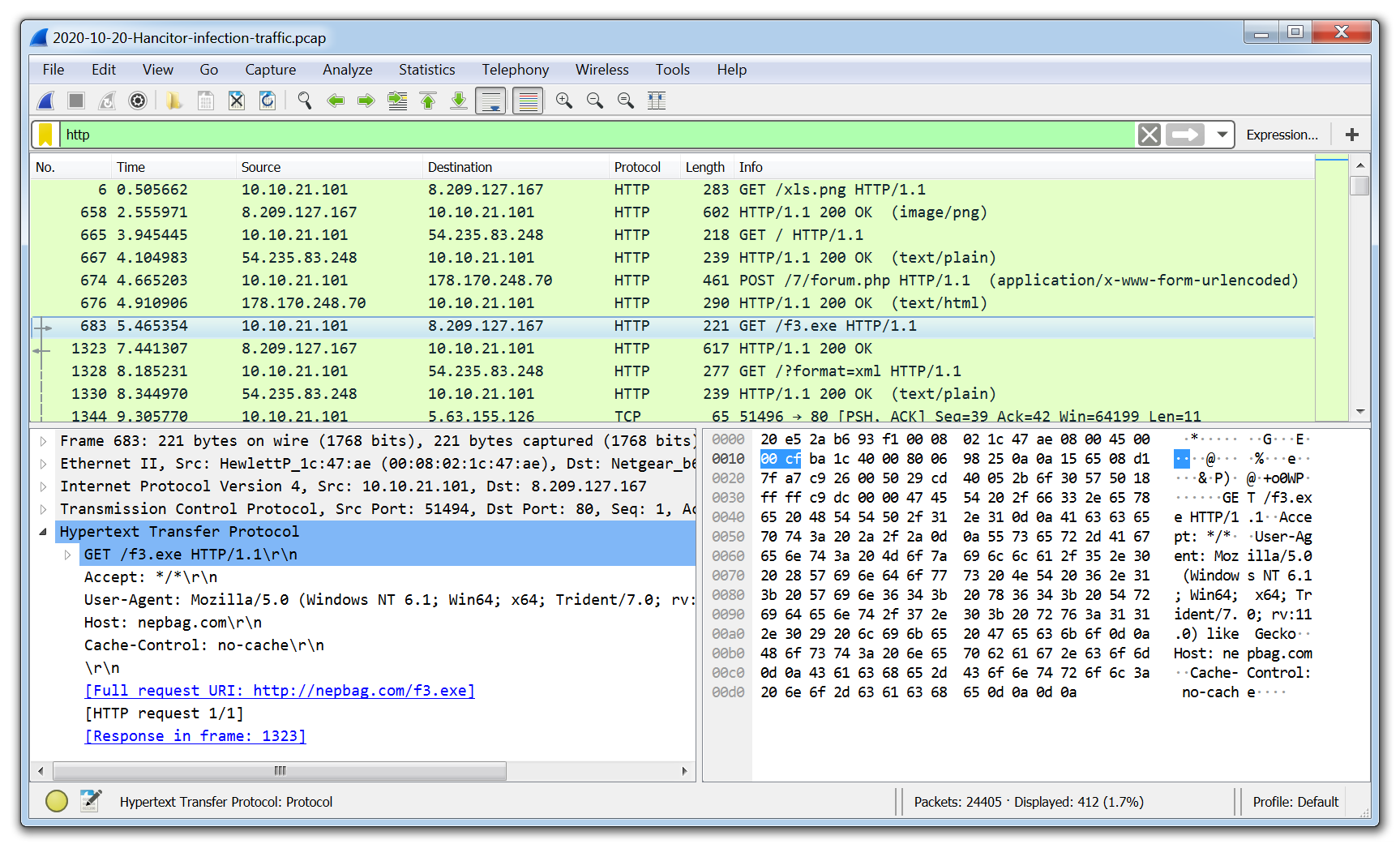
Wireshark is the go-to tool for capturing and analyzing network traffic. Unlike web proxies like Fiddler, which focus primarily on HTTP and HTTPS, Wireshark enables deep packet inspection across a wide range of protocols and network layers. When analyzing a packet capture, analysts can even extract files downloaded by the malware directly from the PCAP, offering valuable insight into the payload and its behavior.
8. x64dbg
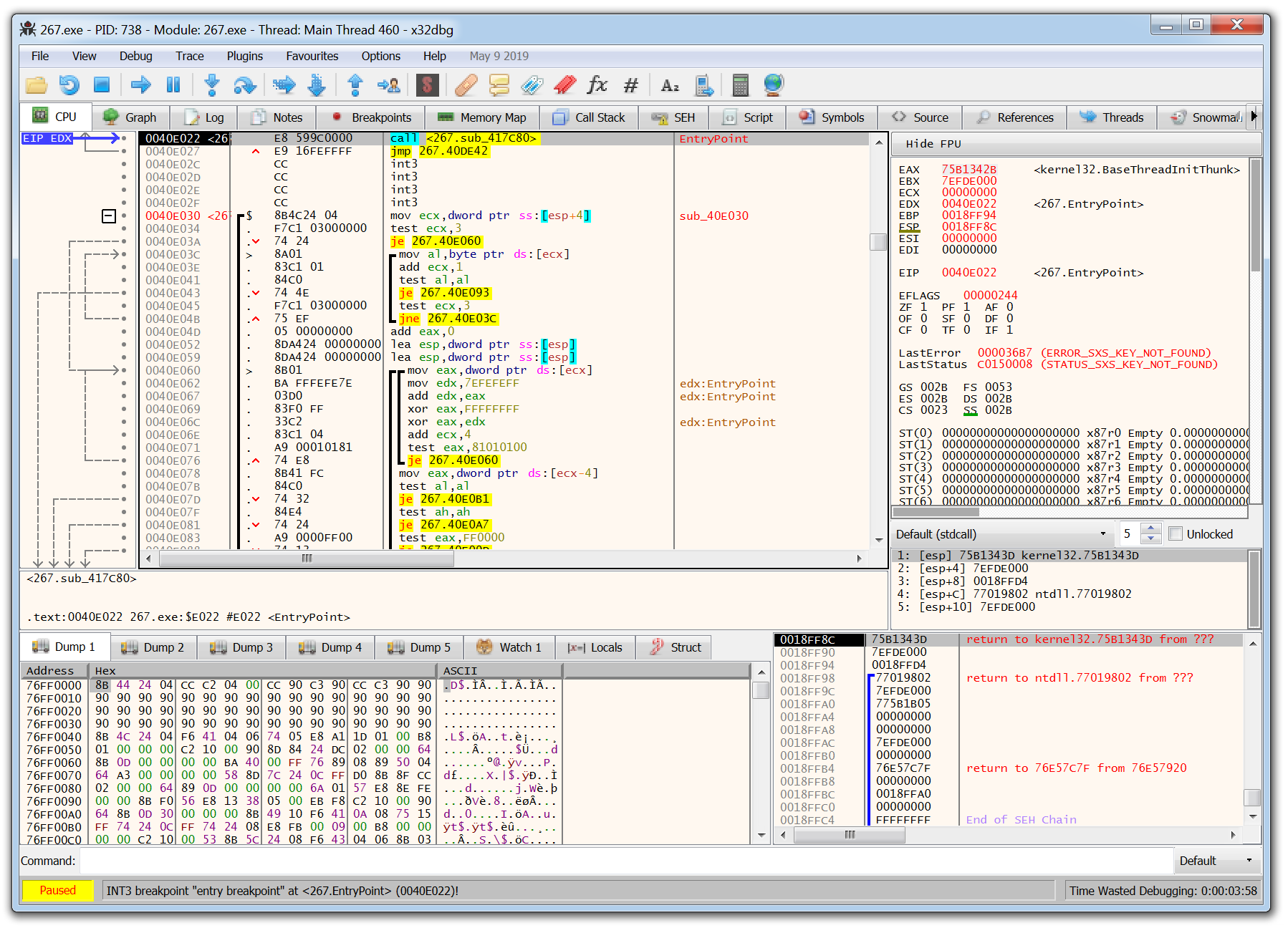
The tools covered so far are beginner-friendly and great for those just starting out in malware analysis. However, x64dbg marks a significant step up in complexity. Designed for manual debugging and reverse engineering, x64dbg requires a solid understanding of assembly language. While the learning curve is steep, mastering this tool gives analysts the precision to manually unpack and dissect malware with surgical accuracy. It allows you to zero in on specific functions and API calls, providing deep insight into how the malware truly operates.
9. Ember
EMBER (Endgame Malware BEnchmark for Research) is an open-source dataset and machine learning model designed for static malware detection. It provides a rich set of pre-extracted features from Windows PE files along with a baseline LightGBM classifier. While EMBER isn’t an interactive analysis tool like some others on this list, it’s widely used to train and evaluate machine learning models that classify malware at scale.
Security researchers and engineers can use EMBER to explore how AI can detect malware based on static attributes without needing to detonate or reverse engineer samples manually.
10. Ghidra
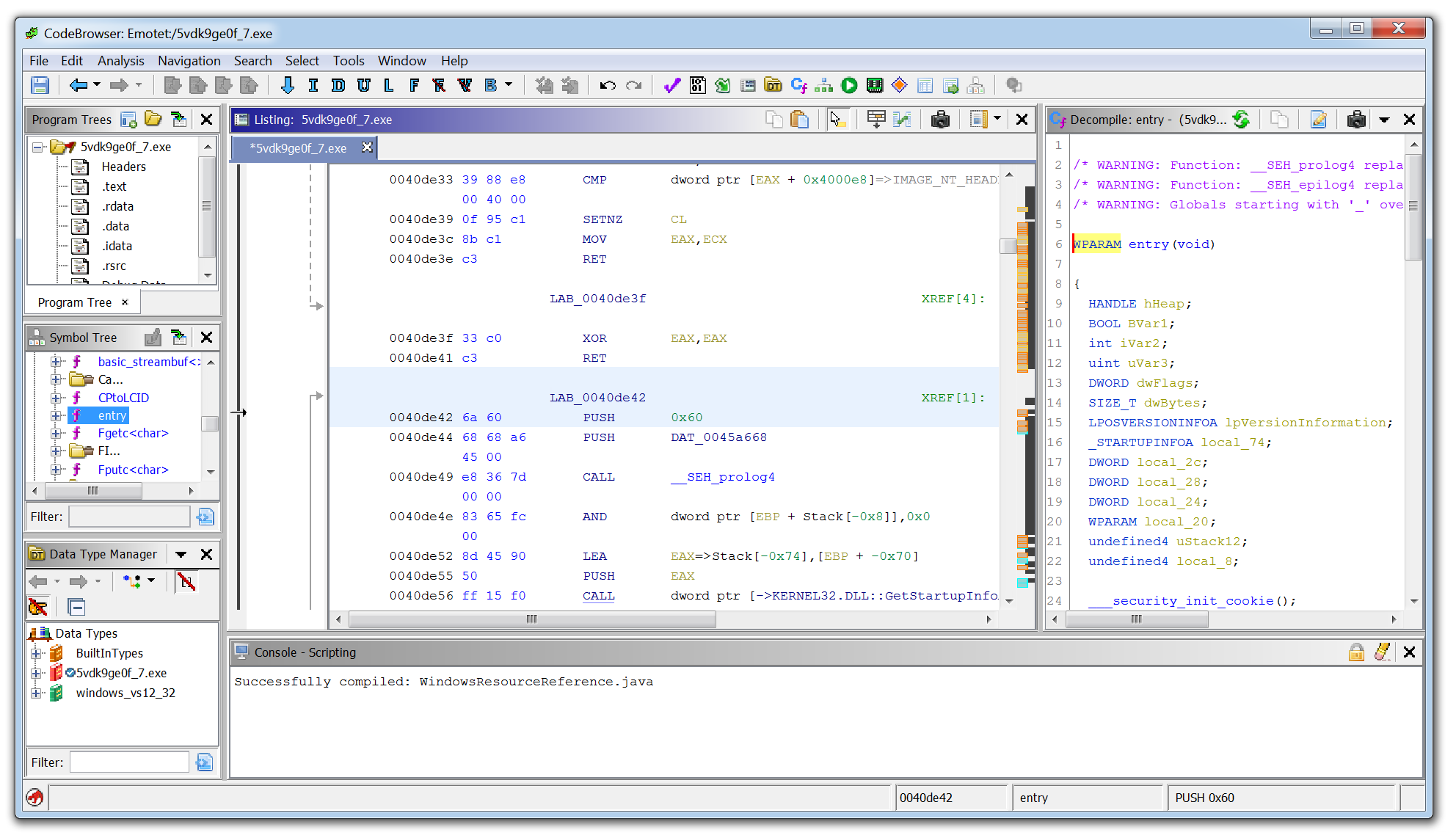
Ghidra developed by the National Security Agency (NSA), is a powerful reverse engineering tool known as a disassembler, as opposed to a debugger like x64dbg. With Ghidra, you can explore the structure and functions of assembly code without executing it, enabling static analysis of malware samples in a controlled, non-runtime environment.
One of Ghidra’s standout features is its decompiler, which attempts to translate low-level assembly into a high-level, human-readable format resembling the original source code. This makes it easier for analysts to understand the malware’s logic, variables, and control flow, offering a clearer picture of what the malware was designed to do—without needing to run it.
11. Malconv
Malconv is an open source deep learning model that classifies Windows executable files using raw byte sequences. Unlike traditional approaches that depend on predefined features or signatures, MalConv uses a convolutional neural network (CNN) to learn from the binary structure directly. This makes it a valuable tool for exploring how AI can detect malware in a more generalized and scalable way.
MalConv is especially useful for teams experimenting with AI-driven detection techniques or building custom malware classifiers that don’t rely on static indicators of compromise.
In closing, malware analysis is often complex, but with the right tools, it becomes more approachable and effective. The tools outlined in this article offer a solid starting point for building a malware analysis lab and understanding the techniques used to dissect malicious code.
FAQs about malware analysis tools
Why is network traffic analysis essential in malware investigation?
Network traffic analysis reveals communication patterns between malware and command and control servers. Tools like Fiddler capture HTTP/HTTPS traffic, allowing analysts to identify domains hardcoded in malicious documents. Wireshark provides deeper inspection across multiple protocols and can even extract files downloaded by malware. These capabilities help security teams understand how malware communicates and what data it might be exfiltrating.
How do tools like PeStudio help identify packed malware?
PeStudio helps identify packed malware by measuring the file's entropy on a scale of 0-8. Higher entropy levels (closer to 8) indicate a greater likelihood that the malware is packed. Packed malware has been obfuscated by its author, with a layer of code added to hide its true functionality and prevent analysis. PeStudio also shows imports that reveal potential malware functionality and checks for detections on VirusTotal, providing analysts with critical information before executing the suspicious file.
How do Process Hacker and Process Monitor work together for malware analysis?
Process Hacker shows running processes while Process Monitor captures filesystem activity, creating a powerful combination. Process Hacker can reveal new processes created by malware, even those that try to hide by renaming themselves. Meanwhile, ProcMon records events like process creations and registry changes in real-time. Together they provide a comprehensive view of malware behavior, particularly useful for analyzing threats like malicious Word documents with embedded macros.
How does Cuckoo Sandbox automate the malware analysis process?
Cuckoo Sandbox creates an automated environment for safely detonating and analyzing malware samples. It typically runs on a Linux host with a Windows VM containing a Cuckoo agent to record malware activity. The sandbox automatically documents behaviors like file creation, registry modifications, and network communications. This automation allows analysts to gather comprehensive information while simultaneously performing their own manual analysis on the same sample.
How is AI being used in modern malware and malware analysis tools?
Modern malware increasingly leverages AI to evade detection, automate its behavior, and adapt to different environments. This makes traditional signature-based detection less effective. In response, some malware analysis tools now incorporate AI and machine learning to detect subtle patterns, classify unknown binaries, and predict malware behavior. Tools like EMBER and MalConv apply machine learning to static file features or raw byte sequences, enabling more adaptive and scalable malware detection.
What are EMBER and MalConv, and how do they help analyze malware?
EMBER is an open source dataset and baseline machine learning model used to classify Windows PE files based on static features. MalConv, on the other hand, is a deep learning model that analyzes raw binary data using a convolutional neural network (CNN). Both tools represent how AI is being used to enhance malware detection, enabling analysts to go beyond manual triage and detect threats that might not yet be known or easily observable.
What is Varonis and what does it do?
Varonis is a data security platform that helps organizations find, protect, and monitor their sensitive data. It automatically discovers and classifies critical data, remedies exposure issues, and stops threats in both cloud and on-premises environments. Varonis provides capabilities such as data discovery, security posture management, user behavior analytics, and data access governance to keep organizations' data secure.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.







-1.png)

