If you’re a regular reader of our blog, you know that we feel that the perimeter is dead, and that the battle against insider (and outsider) threats is won with User Behavior Analytics (UBA), which is why we’re so excited to announce the launch of Varonis UBA Threat Models in beta release of 6.2.5.
What are Threat Models?
Without any configuration on your part, our predictive threat models will automatically analyze behavior across multiple platforms and alert you to potential threats. From CryptoLocker infections to compromised service accounts to disgruntled employees, we’ll detect and alert you on all sorts of abnormal user behavior.
Get the Free Pen Testing Active Directory Environments EBook
Varonis has been doing UBA for the past decade, most notably to determine when users no longer need access to data based on their behavior and peer-group analysis. With our new threat models, you’re getting even more value out of the data we collect—the ability to use machine learning to detect and stop threats you might not have pre-configured an alert for.
Why does this matter?
Varonis UBA threat models uncover security issues quickly, and give context around metadata and what’s actually happening on your file and email servers, SharePoint, and Active Directory.
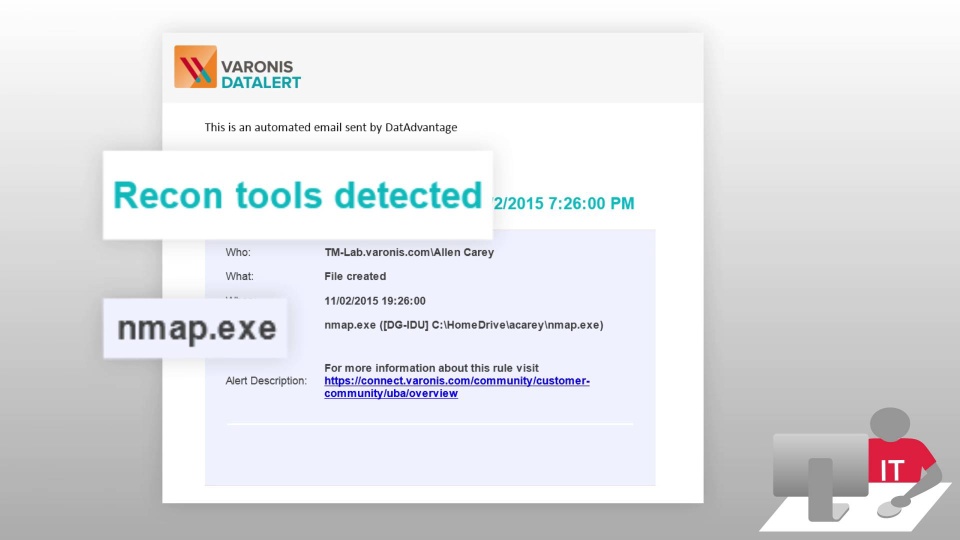
Our advanced behavioral alerts catch suspicious activity across every stage of a potential data breach: from initial reconnaissance to data exfiltration. Here’s a sample of some of our most sought-after threat models:
Abnormal behavior: access to sensitive data
Exfiltration: May indicate an unauthorized attempt to gain access to sensitive data assets. The user’s actions are compared to his behavioral profile, and an alert is created when a deviation is discovered.
Abnormal service behavior: access to atypical mailboxes
Exfiltration: May indicate an unauthorized attempt to exploit service privileges to gain access to data assets. The user’s actions are compared to his behavioral profile, and an alert is created when a deviation is discovered.
Crypto intrusion activity
Intrusion: May indicate presence of Ransomware.
Suspicious access activity: non-admin access to files containing credentials
Privilege Escalation: May indicate an unauthorized attempt to extract credentials, or deny access to systems.
Modification: Critical GPOs
Exploitation: May indicate unauthorized attempts to gain access by changing policies, or using privileged groups. May also indicate attempts to deny users access to systems, especially if performed without regard for established change control processes.
Suspicious access activity: non-admin access to files containing credentials
Privilege Escalation: May indicate an unauthorized attempt to extract credentials, or deny access to systems.
Exploitation tools detected
Exploitation: May indicate attempt to install or use known hacking tools.
Membership changes: admin groups
Exploitation: May indicate unauthorized attempt to gain access via privileged groups or prevent administrators from responding to the attack, especially if performed outside of established change control processes.
Administrative or service account disabled or deleted
Exploitation: May indicate an unauthorized attempt to damage the infrastructure, deny users access to systems, or to obfuscate, especially if performed outside of established change control processes.
Multiple open events on files likely to contain credentials
Privilege Escalation: May indicate an unauthorized attempt to extract credentials.
Recon tools detected
Reconnaissance: May indicate the unauthorized presence of reconnaissance tools that could be used to scan the corporate network or to search for vulnerabilities.
Curious to see what our threat models reveal about your systems? Let’s find out.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.









