Data Security Platforms (DSP) enable organizations to protect data from being stolen, improperly distributed, and accessed by the wrong parties. Many DSPs govern data security by controlling permissions and labels, and restricting who can access, modify, or distribute data.
These platforms identify unlabeled data and highlight users with excessive permissions, and while they help implement least-privilege principles, they usually lack a key aspect — identity.
Data and access events are tied intrinsically to identity. Security teams monitor data access and administration by focusing on the “who?” of an action, including non-human identities like machine and service accounts. That’s why an effective DSP solution must intrinsically incorporate the identity context.
Understanding the “Who?”
In Varonis’ latest identity threat report, “The Identity Crisis,” our team outlines the key themes and attack profiles from 2024. More than half (57%) of the cyberattacks examined started with an identity exploit, and most of those attacks ended with data exfiltration.
Some IT and security leaders may question why they still experience compromised accounts, despite implementing multifactor authentication. There are several overlapping reasons this can occur:
- User error or lack of education: Some users might approve authenticator challenges without discerning the request's origin, especially if they are overwhelmed by the number of MFA and OTP requests they receive.
- Phishing attacks: Attackers use phishing emails to trick users into providing their login information and other factors on fake login pages, allowing the attacker to bypass MFA.
- Token theft: Attackers steal authentication tokens, allowing them to bypass MFA entirely. They then use renewal tokens to keep renewing the stolen token.
- MITM attacks: Man-in-the-middle attacks capture login information and MFA tokens, allowing attackers to bypass conditional access policies.
Organizations can enhance security with phishing-resistant authentication and conditional access policies. However, identities continue to be compromised year after year. Neither identity security nor data security can protect critical resources alone.
Data security and identity protection belong together
Identity posture
Organizations aiming to prevent and limit the impact of breaches need visibility into their identity posture. Understanding the state of guest and internal user identities, the distribution of privileged roles and group memberships, and how they evolve over time is essential.
Understand roles and privileges spanning data systems with Varonis
Understand roles and privileges spanning data systems with Varonis
Some DSPs can identify if a site or file is labeled and what group(s) have access to those labeled files, but they have no visibility into changes in that group’s membership — or worse — the ownership. For example, many labels in Microsoft 365 are bound to a group of individuals managed by Microsoft Entra ID.
Bad actors who successfully join or add themselves to a particular group undetected will then gain access to sensitive files governed by that label policy. They may also instantly gain access to a Finance site, for instance, with “Full Control” permissions after joining the “Finance Owners” group.
Understanding how identities, entitlements, and groups change in your environment is crucial, as AI solutions like Microsoft 365 Copilot rely heavily on these factors to provide information.
Microsoft 365 Copilot generates responses based on organizational data accessible to each user and group, including their documents, emails, calendar, chats, meetings, and contacts. A bad actor who gains the right role or joins the right group can quickly access desired emails or documents using AI without triggering certain DLP policies.
It’s a case of the right user, right access, right prompt, wrong human.
Without integration with Entra ID, you might miss stale users' group memberships and admin roles or users without modern MFA methods. This crucial information needs to be available to data security teams without navigating multiple products and UIs. Gathering these insights shouldn’t require complex prompt engineering or multiple prompts in an AI security assistant.
Gain visibility into roles and privileged accounts without modern authentication methods and reduce identity risk
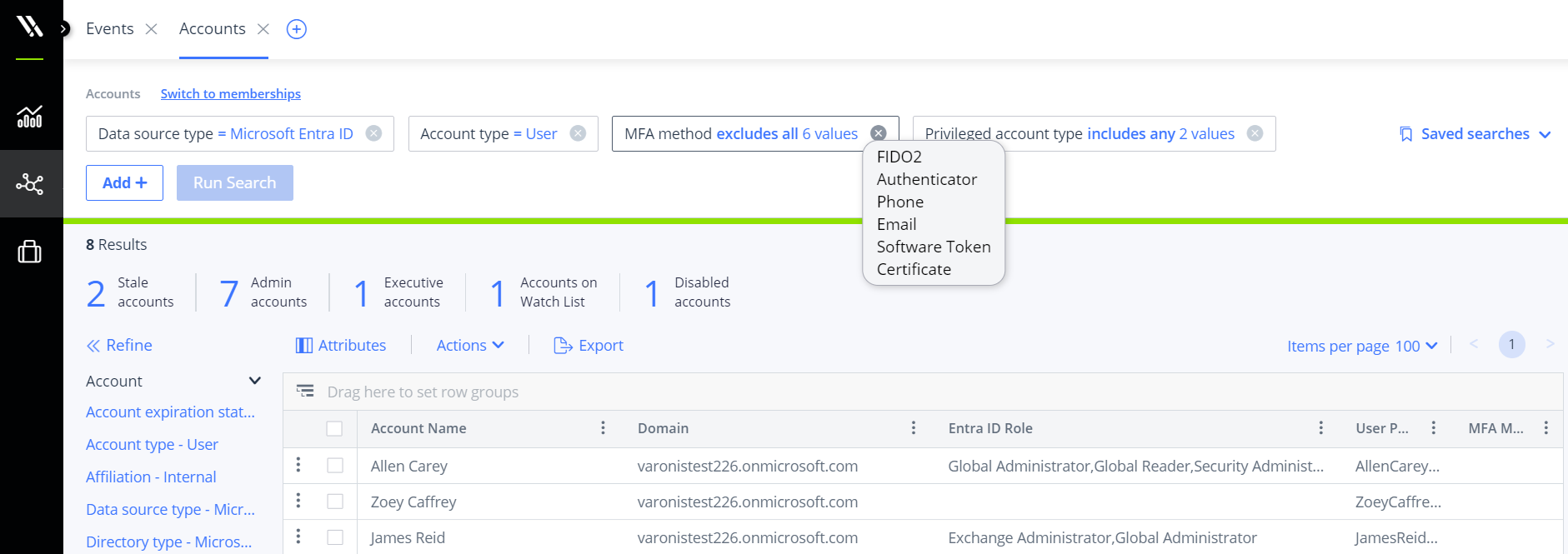
Gain visibility into roles and privileged accounts without modern authentication methods and reduce identity risk
Identity threat detection and response
Correlating identity events and alerts with data events is important for identifying when and where a breach occurs. The National Institute of Standards and Technology highlights this requirement within NIST CSF 2.0 and the Detect Function: “DE.AE-03: Information is correlated from multiple sources.”
Security teams should be able to easily discern threats within a DSP, such as when a user adjusts a data resource’s permissions while also logging in at odd times or resetting their password.
Alone, these events may seem insignificant, but combined, they highlight potential issues. This is why modern data security requires platforms remove the partition between data and identity security.
Identity resolution
Linking data events and alerts with identity is challenging, and resolving multiple identities and systems to a single user can seem impossible. This is because users often have multiple local identities in on-prem systems or cloud apps. Innovative DSPs help correlate these identities to detect attacks earlier in the attack chain.
Attackers consistently have long dwell times and often move laterally within systems to find sensitive data. Every move has a signature. Organizations must be able to quickly recognize these signatures without relying solely on SIEM solutions and SOCs to analyze large amounts of data before it’s too late.
Intelligently alert on identity and access threats with Varonis
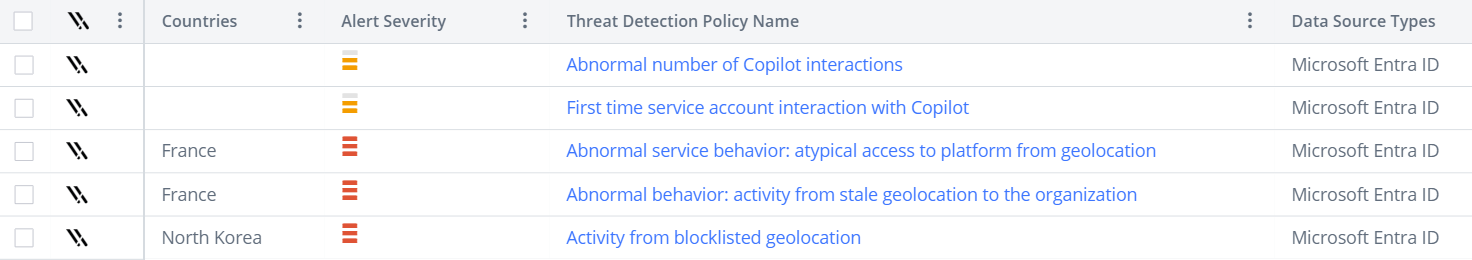
Intelligently alert on identity and access threats with Varonis
Additionally, more organizations are beginning their multi-AI journey, highlighting the need for DSPs to manage identities, prompts, and data access across many different AI solutions.
The purpose and future of DSP
Modern DSPs must integrate with identity management solutions for effective posture management, threat detection, and response.
By linking identity events with data actions, security teams can better identify threats and quickly address breaches. This integration simplifies configurations and provides ongoing insights while aligning with industry standards and addressing the growing complexity of AI deployments.
Ultimately, organizations must prioritize these innovations to protect their sensitive data from sophisticated cyber threats.
Explore Varonis Identity Protection or schedule a demo to see our Data Security Platform in action. We'll personalize the session to your org's identity and data security needs and give you a clear, risk-based view of the data that matters most.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Read about the recent Varonis report, "The Identity Crisis," highlighting trends from 2024 cyberattacks and how organizations can prevent catastrophic breaches in 2025.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.










