Phishing attacks. They’re ubiquitous, easy to carry out, and at the root of some of the most devastating cyberattacks in history. Phishing is a type of social engineering attack, employing deceit and coercion to trick a user into revealing sensitive information or downloading malware. Those pesky fake emails pretending to be from your bank might seem like a mere annoyance, but phishing has very real implications for companies, governments, and other types of organizations. In fact, Verizon’s 2021 Data Breach Investigation Report (DBIR) lists phishing as the most common tactic seen in confirmed breaches. According to Symantec, one in 2,000 emails are phishing attacks, which means there are 135 million phishing attacks every day [1].
Discover your weak points and strengthen your resilience: Run a Free Ransomware Readiness Test
In this post, we’ll take a deeper look at phishing, explore why it’s remained a popular attack method, and learn about some ways to protect ourselves.
What is Phishing?
Phishing is a type of social engineering attack, which means it targets the weaknesses of human psychology rather than technical vulnerabilities. The attacker will masquerade as a legitimate individual or organization and then send the victim a phony message using this assumed moniker. Many people expect to receive emails from official sources such as expert organizations, insurance companies, government entities, etc., leaving ample opportunity for scammers to sneak their “real enough” emails into the fray. These seemingly innocuous emails aimis to convince the user to take some specific action, often downloading a file laced with malicious code or logging into a fake sign-in page designed to capture credentials.
Email phishing attacks are by far the most common, but the same tactic can be applied to instant messaging, text, or even a good old-fashioned phone call. Many phishing attacks will bait their targets with a sense of urgency: an account that’s been accessed by an unknown party, an impending draft out of a victim’s bank account, or an action that needs to be taken to maintain employment. Preying on the emotional humans in front of a computer rather than unfeeling bits of 1’s and 0’s can often thwart some of the most advanced technical defenses. Phishing is often used to gain an initial foothold in an organization as part of a broader campaign that may include other types of hacking.
While phishing attacks are nothing new, the scale and complexity have increased dramatically over the last several years. The height of the global CoVID-19 pandemic saw an unprecedented surge in phishing emails, demonstrating how attackers capitalize on fear, confusion, and chaos. Phishing has been used in everything from simple financial scams to highly sophisticated cyber espionage and ransomware campaigns.
How Does Phishing Work?
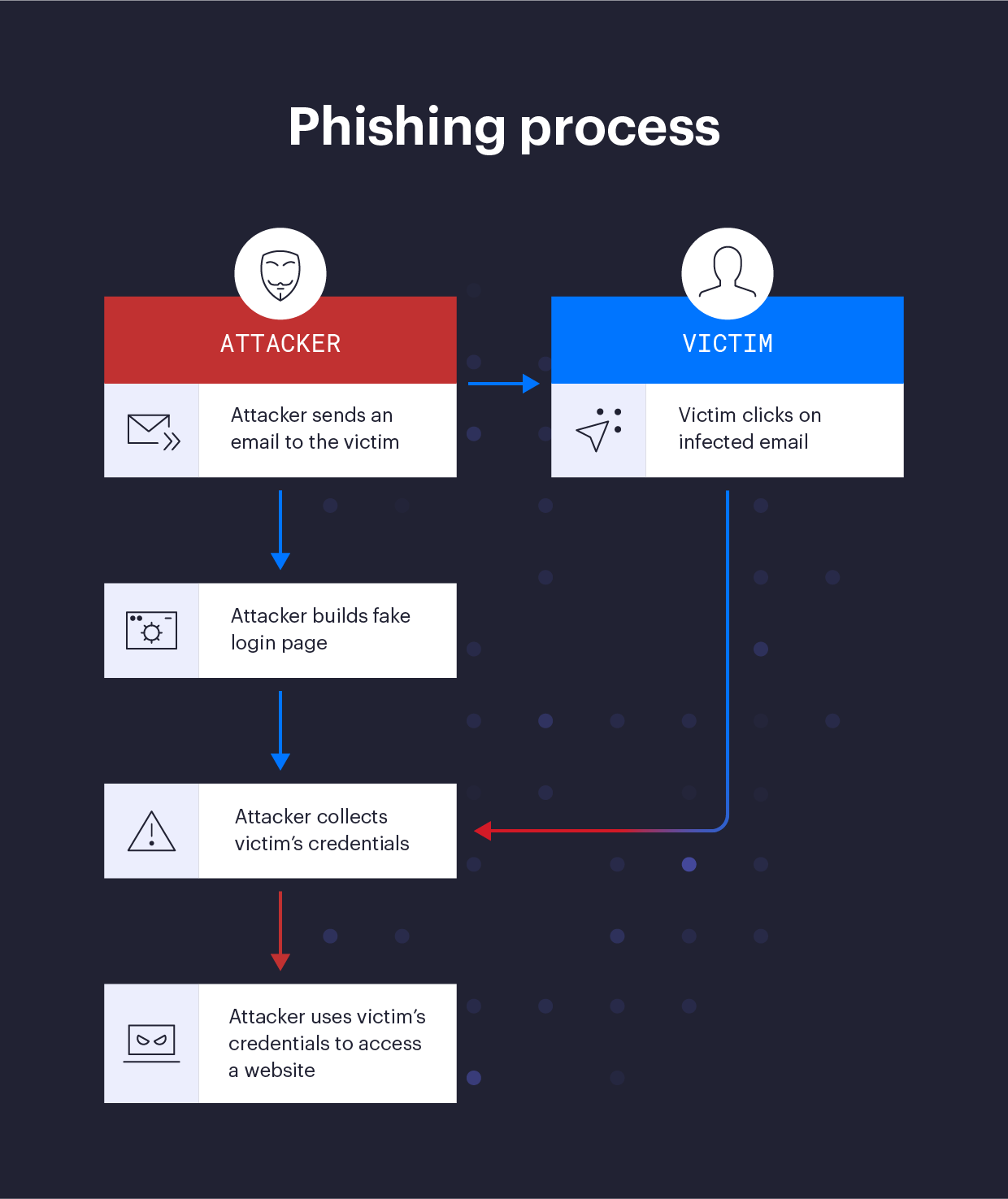
Individual phishing campaigns will vary in their complexity, scale, and motivation, but most types of phishing attacks follow a predictable pattern:
- Selection of a Target: Target selection is a key step in a phishing campaign, as it directly impacts many of the other phases. Targets can be as specific as a single individual, or as broad as all of the users of a video streaming service. Some phishers are opportunists and target users en masse in the hopes of gobbling up as many credentials as possible, perhaps to resell in bulk on underground hacker forums. On the other hand, cyberespionage campaigns might use phishing to target people with access to privileged information.
- Registration of Domains: Phishing attacks frequently make use of domain names that are visually similar to a real well-known domain. Automated tools make finding and registering such domains a relatively simple process. If an attacker wanted to spoof “example.com” for instance, they could register domains like “ex.ample.com”, “exarrple.com”, or “exa-mple.com” - all of which were available at the time of writing. (Note that the real “example.com” is a specially reserved domain, and should never really be the source of an email in any case). Another frequently used technique is the use of URL shortening services like bit.ly. These can not only mask the true destination to human eyes but complicate technical efforts to thwart attacks as well.
- Craft a Campaign: The “meat” of a phishing attack - the actual message designed to trick a user - can be as simple as a few lines of text or as complex as an officially branded message from a well-known source like a bank. Both have proven effective. If they’re willing to invest a little more time, attackers can leverage a bit of Open Source Intelligence (OSINT) to increase the believability of their phony messages.
- Weaponize It: If capturing credentials is the aim, an attacker will likely build a fake login page to complement their phony emails. Tools like HTTrack can rapidly clone an entire website, and the fake domain registered in step 2 adds a sense of legitimacy. To directly infect a target machine, an attacker might add malware to a file that’s either included as an attachment in the email or delivered as a link, sometimes even through legitimate sites like Box or GitHub. Office documents and PDFs are a frequent target as users are conditioned into receiving them daily, and don’t always realize they can contain malicious code.
- Post-exploitation: There are many possibilities following a successful phishing attack. Some attackers might sell stolen credentials on hacker forums. Others might co-opt infected computers to build large botnets in order to send spam or launch Denial of Service attacks. More advanced phishing campaigns may take additional action inside the victim’s network, such as stealing data or detonating a ransomware payload.
4 Types of Phishing Attacks
Bulk Phishing
Bulk phishing is the classic phishing attack, employing a wide net to ensnare as many victims as possible - think bottom trawling in cyberspace. The bulk phisher may have a low overall success rate but relies on the fact that out of thousands or even millions of potential victims, a few will always take the bait. Bulk phishing campaigns are often low in complexity, and may be carried out using an easily available “phishing kit”. Here’s an example of a rudimentary bulk phishing scam:

Spear Phishing and Whaling
Like general phishing attacks, spear-phishing and whaling use emails from what appear to be trusted sources to trick their victims. Rather than casting a broad net, however, spear phishing targets specific individuals or personas. IT administrators and HR professionals are frequent targets because of the level of access they may have within the broader organization.
Like spear phishing, whaling creates campaigns around a specific target but with a bigger fish in mind. Rather than target a broad group like a department or team, these attackers channel their inner Captain Ahab by aiming their spear at high-level targets like executives or influencers with hopes to spear their white whale. Whale hunters may seek to impersonate senior management like CEOs, CFOs, the head of HR, etc., to convince members of an organization to reveal sensitive information that would be of value to the attackers. For a whaling excursion to be successful, the attackers must perform more in-depth research than usual, with the hope of impersonating their whale accurately. Attackers are looking to use the whale’s authority to convince employees or other whales not to look into or question their requests.
Clone Phishing
Clone phishing attacks are less creative than spear and whale fishing, but still highly effective. This attack style has all of the core tenants of a phishing scam. However, the difference here is that rather than posing as a user or organization with a specific request, attackers copy a legitimate email that has previously been sent by a trusted organization [4]. The hackers then employ link manipulation to replace the real link included in the original email to redirect the victim to a fraudulent site to deceive users into entering the credentials they would use on the actual site.
Smishing, Vishing, and More
Most phishing attacks still take place over email, but a number of spin-off attacks using other mediums have also been observed. Smishing refers to phishing attacks sent via text message (SMS). Voice phishing or “vishing” swaps the bogus text for an audio scam, either live or recorded. The July 2020 takeover of dozens of high-profile Twitter accounts was possible because of a sophisticated vishing campaign targeting Twitter employees.
Email Phishing Scam Examples
Recent phishing attacks have capitalized on trends that took shape during the CoVID-19 pandemic, such as an increase in online shopping. It is common for scammers to spoof official-looking emails from retailers like Amazon or Walmart, claiming that you need to enter your credentials or payment information to ensure they can complete your order. Links embedded in the email will take you to a genuine-looking landing page to enter your sensitive information.
An example of a phishing scam that saw an uptick during the 2020 holiday season is a spoofed email from Amazon informing customers that they need to log in to update their payment and shipping information to complete their order [5].

(Source)
How to Prevent Phishing Attacks
Phishing attacks are notoriously difficult to prevent - some experts even consider them the hardest cyberthreat to defend against. Basic cyber hygiene practices are important, but won’t prevent all phishing attacks. Even with advanced filtering, it’s likely you or your users will end up with a phishing attempt in their inbox at some point. It may be more helpful to focus on how to mitigate phishing attacks in your organization and ensure that the bogus emails, texts, and other messages that do get through don’t have the chance to cause lasting damage. Here are some general tips that may help from both a prevention and mitigation angle:
- Security Awareness Training
As mentioned earlier, phishing attacks are all about human psychology and not technical weaknesses. As such, it’s critical that your defenses also start with the “human layer”. Security Awareness training should be mandatory for all employees, including senior executives and board members. Simulated phishing campaigns can be helpful in building employee understanding, but keep in mind that the goal is to educate users and not reprimand them. Between formal training, things like memos and awareness posters can help reinforce a culture of pervasive security in your organization.
- Two-factor Authentication (2FA)
Enabling (and enforcing) two-factor authentication on user accounts can be one of the most powerful mitigations against phishing attacks. A 2019 study commissioned by Google found that 2FA could prevent 96 to 99% of “bulk” phishing attacks. The more determined attackers launching spear-phishing and whaling campaigns may expend more effort in trying to thwart 2FA protections, but a lower-tier cybercriminal looking for an easy target of opportunity will likely just move onto an easier catch. Still, some phishing attacks are designed specifically to circumvent 2FA, which is all the more reason to ensure your workforce is well educated in using appropriate cyber hygiene.
- Password Managers
Password managers don’t directly prevent phishing attacks but can mitigate the threat of credential harvesting. That’s because a password manager saves login information for a specific domain, and can’t be fooled by a lookalike or shortened URL. A password saved for “example.com” will not be used on “ex.ample.com”, even if it looks the same to the human using the password manager. A password manager can’t protect against phishing attacks that use malicious attachments, however
- Sandboxing, URL rewriting, and domain-based filtering
Various schemes exist to monitor, rewrite, or block the external links that phishers often use in their campaigns. URL rewriting integrates directly with an organization’s email infrastructure and modifies the links that may be found within emails. Links that are found to be malicious can then be blocked, even if emails containing the link have already made it to user inboxes. Web proxies and DNS filtering can be used to similar effect, although these protections are only as good as the data behind them.
- Account Monitoring and Anomaly Detection
Cyber espionage and Ransomware campaigns may use phishing attacks to harvest credentials or slip malware through your perimeter defenses. Monitoring user accounts in your organization won’t stop that, but can alert you to the attack before serious damage has been done. Solutions like Varonis DatAlert can integrate with popular email products like Exchange to provide advanced detection capabilities that can help to mitigate a phishing attack.
Like other types of cyberattacks, phishing is a constantly evolving phenomenon. It can be difficult for both humans and machines to spot the signs of a phishing attack, but many campaigns share similar anatomy that can yield clues:
The Anatomy of a Phishing Email
We’ve broken out the most common components of a phishing email. Check out our full infographic to test your knowledge.

- Subject line: Phishing campaigns typically aim to create a sense of urgency using intense language and scare tactics, starting with the email’s subject line.
- “From” field: The email will appear to come from a legitimate entity within a recognized company, such as customer support. However, upon closer look, you can see that both the sender’s name and email address is a spoofed on a known brand, not a real vendor.
- “To” field: Phishing emails are often impersonal, addressing the recipient as a “user” or “customer.”
- Body copy: As with the subject line, the body copy of a phishing email typically employs urgent language to encourage the reader to act without thinking. Phishing emails are also often riddled with both grammar and punctuation mistakes.
- Malicious link: A suspicious link is one of the main giveaways of a phishing email. These links are often shortened (through bit.ly or a similar service) or are formatted to look like a legitimate link that corresponds with the company and message of the fake email.
- Scare tactics: In addition to urgent language, phishing emails often employ scare tactics in hopes that readers will click malicious links out of alarm or confusion
- Email sign-off: As with the email’s greeting, the sign-off is often impersonal — typically a generic customer service title, rather than a person’s name and corresponding contact information.
- Footer: A phishing email’s footer often includes tell-tale signs of a fake, including an incorrect copyright date or a location that doesn’t correspond with that of the company.
- Malicious landing page: If you click on a phishing link, you’ll often be taken to a malicious landing page.
Phishing FAQs
Who do phishing attacks target?
Phishing attacks target both individual users and large organizations. Scams targeting individual users are often carried out by less sophisticated attackers, while advanced persistent threat (APT) and organized crime groups might use phishing as the first stage of a complicated attack.
What should I do if I think I’ve been phished?
Report the incident to your IT or security team promptly. Larger organizations often have an email alias dedicated to receiving suspected phishing messages, and some may even support a plugin to report phishing attacks right from your email client. If you believe you’ve inadvertently given your credentials to an attacker, change your password immediately and enable 2FA.
Who can I report Phishing Attacks to?
The FBI’s Internet Crime Complaint Center (IC3) accepts reports of phishing attacks against U.S. citizens and corporations. Organizations like banks, the IRS, online retailers, etc. are often interested in scams that may be impersonating them, and many have dedicated reporting channels. The Anti-Phishing Workgroup (APWG) is a global non-profit coalition that tracks broad trends in phishing in order to build new defenses.
What are some famous phishing attacks?
Phishing has been at the root of some of history’s most notable cybersecurity incidents. A spear-phishing attack on an HVAC vendor is believed to have led to the 2013 Target data breach. The 2016 leak of emails from Hilary Clinton’s presidential campaign began with a phishing attack on campaign chair John Podesta. Twitter’s 2020 account takeover incident began with several vishing attacks on employees. And by some metrics, phishing is the first action in as many as a quarter of all ransomware campaigns.
Conclusion
Though it may not truly warrant being called a hack in its own right, phishing is a favored tool of malicious hackers because of the low cost and high potential. As a social engineering attack, phishing is difficult to defend against, but the risks can be mitigated through a well-designed information security program. Varonis Edge and Varonis DatAlert are both well-suited to detect and mitigate phishing threats throughout their entire lifecycle. Contact us for a 1-on-1 demo today!
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.