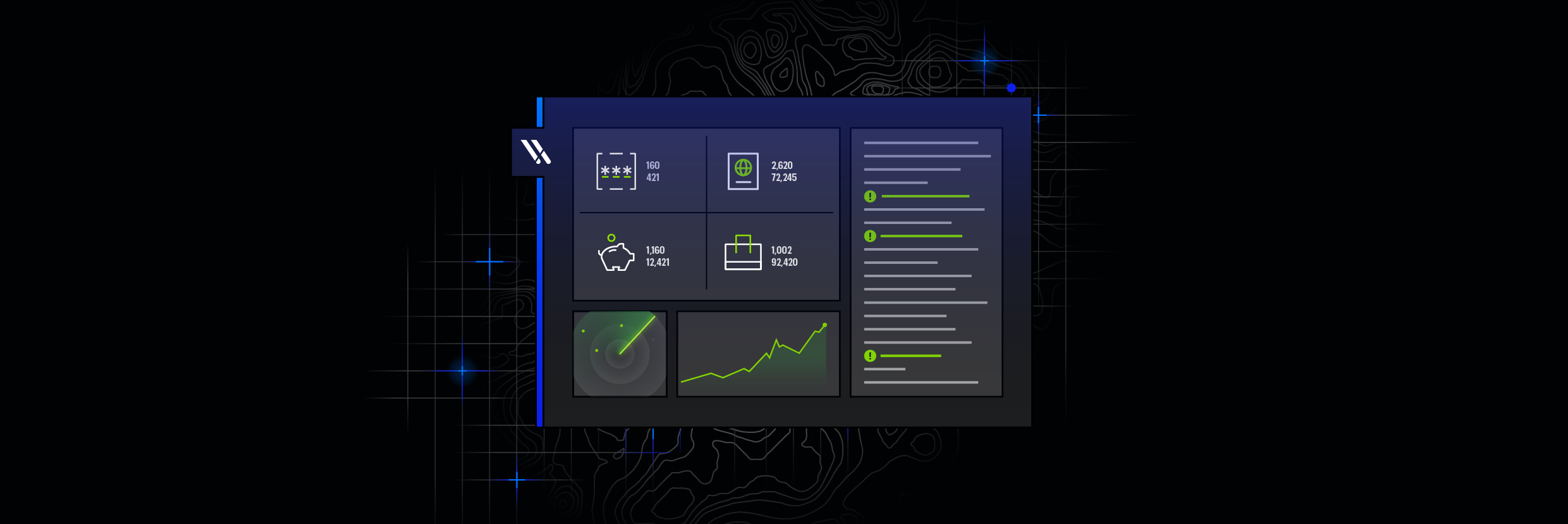
Most companies don’t have a clear picture of where their sensitive data lives, nor do they know where to begin to establish a better security posture.
That’s where a Data Risk Assessment (DRA) comes in.
What is a Data Risk Assessment?
A DRA is a comprehensive review of your data assets that can help your organization discover, classify, and label critical data that is created, stored, and moving around your cloud and on-prem environments.
Essentially, we can look at DRAs and cloud security solutions like pizza (because who doesn't like pizza?). Most people have access to the basic ingredients needed to create the Italian staple (like flour, salt, and water) and an oven to bake in, but it’s what you do with the ingredients and their quality that makes a difference between a slice available in an elementary school cafeteria to a pizza you’d find at a four-star restaurant.
This same analogy works with your cloud security and conducting a Data Risk Assessment. What matters is the quality of the assessment, the preparation, and the presentation.
Varonis’ risk assessment brings together different ingredients, like the accouterments of private information and the zest of Zero-Trust principles, in an accurate and appetizing way. A Varonis DRA positions the sensitivity of the data alongside the exposure. It’s the most advanced Data Risk Assessment in the industry — and we offer it for free.
In less than 24 hours, you’ll have a risk-based view of the data that matters most and a clear path to automated remediation. Plus, your team is assigned a dedicated incident response analyst and will be given full access to the Varonis SaaS platform during the process, no strings attached.
In this blog post, we’ll dive into the details of how Varonis’ DRA works to show you how we discover where your data is most at risk and how we are able to provide actionable recommendations for a clear path to remediation. Follow along with a sample of our DRA.
Addressing the challenges and pain points that warrant a DRA
If you wait until a data breach occurs to undergo a risk assessment, you’ll put yourself behind the eight ball.
In fact, there are many challenges companies already face when it comes to creating a strong security program. Some of them include:
- Struggling to classify and label sensitive data and fix exposure that could lead to a breach
- Data remediation efforts, which are difficult with a small team
- Efficiently monitoring data usage and alerts on abnormal activity
- Quantifying data security posture and showing progress to the board
- Sub-units that operate independently — there is a need to build a unified data security program
- Manual and incomplete compliance audits
Manually discovering, classifying, and labeling your sensitive data in-house is laborious. Varonis takes your pain points and turns them into automated outcomes. We assess your systems with a focus on the sensitivity, permissions, and activity in your systems, allowing us to:
- Provide real-time visibility.
- Reduce your blast radius.
- Offer proactive threat detection and response.
- Simplify your compliance.
Varonis automatically eliminated nearly 100% of external and org-wide data exposure in a customer's first 90 days of using our Data Security Platform.
Varonis automatically eliminated nearly 100% of external and org-wide data exposure in a customer's first 90 days of using our Data Security Platform.
Another challenge many organizations come to realize in the assessment process is how many places their data lives, including third-party apps, CRMs such as Salesforce, and more. With Varonis’ DRA, we can connect to dozens of additional data sources, and setup only takes minutes.
A look at Varonis’ DRA critical findings
Once we’ve conducted your assessment and reviewed your organization's data security, we’ll highlight the most critical findings that could potentially lead to a data breach, providing concrete, specific examples upfront.
In our example report, we assessed a portion of a fictional company’s overall environment which includes Microsoft 365, Active Directory, Entra ID (Azure AD), Salesforce, Windows File Share, and Google Workspace.
The top four risks we found in our sample report were:
- HR compensation reports were shared publicly via “anyone” links.
- 332 Salesforce users had unnecessary report export privileges.
- An external user was a super admin in Google Workspace.
- A marketing assistant triggered an abnormal data access alert.
For each risk, Varonis provides a detailed overview of the affected system, risk type, NIST control, a detailed overview of our observation, and a recommendation on how to minimize the risk further.
Let's look deeper at the external user who has super admin access in Google Workspace, which is one of the critical findings in our sample report. During Varonis’ observation, we found that an external contractor used a personal Gmail account to access Umbrella Corp’s Google Workspace account. This user has super admin rights and does not have multifactor identification (MFA) enabled. His activity spiked on July 4, which triggered an alert, and this account is considered extremely high risk.

Our recommendation included immediately enforcing MFA on this account and adding him to a watch list in Varonis. We also recommended reviewing the user’s past 30 days of activity, entitlements, and related identities to decide whether this external user truly needs super admin rights.
Other Data Risk Assessment providers will tell you where a problem is, but unlike Varonis, they fail to provide actionable recommendations to rectify risks upfront. Our assessment process doesn’t stop with surfacing risks alone — we also provide detailed summaries of your data security posture, cloud environments, collaboration risk, threat detection, and more.
Data security posture
To minimize the risk of a data breach, it’s crucial for your org to have real-time visibility and control over its rapidly changing data estate — with unified classification, threat detection, and policy enforcement.
The Varonis Data Risk Assessment includes an overview of your sensitive data spread across multiple cloud services and on-prem data stores. Post-assessment, you’ll receive a complimentary report and chart that shows where you have the most exposure.
We dedicate part of the assessment to data discovery and classification — which conveys the top sensitive patterns and different sensitive data types found in the environment — and break down exposure across your data stores. This also highlights the differentiators of our engine, its accuracy, its scale, and all the built-in policies that we have across different categories like PII, credentials, secrets, federal patterns, and policies.
The power of Varonis’ data classification includes:
- Attention to the top four data types by volume: PCI-DDS, passwords, U.S. PII, and matter numbers
- True incremental scanning for efficient and scalable discovery on massive data sets
- Unified classification policies across all supported data stores
- Being battle-tested in multi-petabyte environments
- 400+ expert-built and tested rules (and growing) available out of the box
- Customizable scanning scopes and sampling
For organizations needing to comply with government policies such as HIPAA, GDPR, and more, our classification efforts also include locating misplaced data and identifying compliance risks. In our sample risk assessment for Umbrella Corp, we found private EU citizen records on a U.S.-hosted Microsoft 365 tenant.
The path to remediation with Varonis
Once we’ve shown you all the action of where and what the risk is in your organization, it’s time to show you specifically how Varonis can help.
Threat detection and response
Varonis' real-time monitoring and behavior-based threat detection are enabled across each in-scope system during the assessment period. Our AI models are trained on 800M+ events to learn the unique behavior of users and devices in your company's environment.
Your org will benefit from threat modeling we’ve developed across our entire SaaS customer base, and with our Data Security Platform, your team can drill down into high-fidelity alerts and incidents involving compromised service accounts, files modified by backup services, rogue user accounts, and more.
 Events are enriched with data-centric context.
Events are enriched with data-centric context.
Configuration risk
Varonis continuously scans system configurations in your company’s SaaS and IaaS platforms to identify risky settings or determine if any configurations have drifted from their desired state. Your team will be provided with a summary of the five highest-severity misconfigurations discovered during the assessment, and full details and recommendations for each one can be found in the Varonis UI.
See critical SaaS and IaaS misconfigurations instantly.
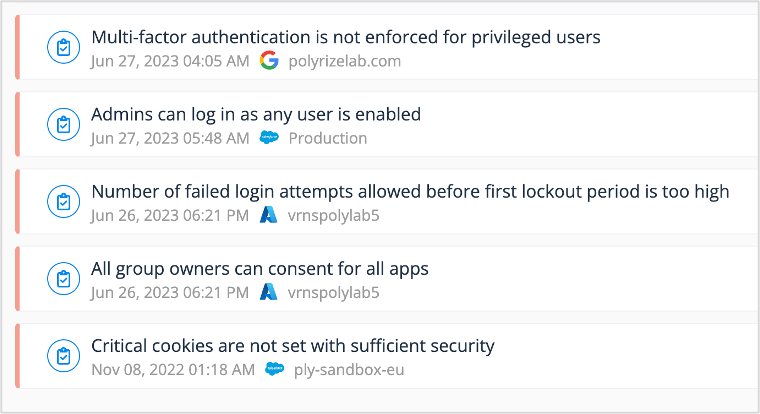
See critical SaaS and IaaS misconfigurations instantly.
Third-party app risk
Our third-party risk page of the assessment shows the apps plugged into the important systems we analyzed. Specifically, this section shows you how many third-party apps are installed and which ones are risky, inactive, or unverified. We may recommend revoking inactive app assignments depending on their usage and the level of risk.
Identity risk
Understanding identity risk for your users and organization is another top priority during your risk assessment. Varonis analyzes your security posture for multiple systems to give you concrete examples of where risk is most prevalent. Those include:
Active Directory security posture and monitoring: Varonis scans your company’s cloud and on-prem directory services and detects weak configurations that can provide pathways for attackers. These risks are updated in real time on your Varonis dashboards and will help prioritize AD hardening efforts.
We monitor events in directory services and correlate those actions to the data-centric events collected from collaboration platforms and data stores. In your assessment, we’ll highlight what changes were performed outside of the change control window.
Entra ID security posture: Entra ID posture is continuously monitored and scored by Varonis. Risky misconfigurations are surfaced in your dashboards and reports, where you can review unverified app permission and data access.
Risky external users and personal accounts: Varonis automatically identifies related accounts using a proprietary algorithm. In the example below, Guy Incognito is an admin user in Google Workspace using a personal Gmail account without MFA. He is connected to several identities across Umbrella Corp’s environments. Guy has several aliases — a mixture of corporate and personal accounts.

Our DRA will also bring to light excessive admin account permissions and offboarding gaps, such as inactive user accounts that still have access to data, as a part of our identity risk analysis.
Salesforce risk
Because Salesforce is such a unique platform with unique risks, we dedicated an entire section of our risk assessment to the CRM tool. We also offer a specific Data Risk Assessment for Salesforce for any customers and prospects seeking to evaluate this platform.
In our sample Salesforce report, we focus on data exposure, external sharing in Salesforce, misconfigurations, and feature significant discoveries by the Varonis Threat Labs team that relate to the CRM platform. Discover how our Salesforce Data Risk Assessment works and download the sample report today.
What others have to say about Varonis’ DRA
To date, Varonis has conducted countless DRAs and is trusted by thousands of organizations. Here’s what some of our customers have said:
"Get the Data Risk Assessment. It gives you the depth of view to confirm where you’re at risk in your environment. It also gives you a visible, tangible asset to justify the solution to management, so you can say, 'This is where we are... and this is where we need to be.'" — CISO in the events industry. Read the full case study.
"We knew there were issues, but we didn’t have the hard numbers to show the higher-ups what we were talking about. Varonis’ Data Risk Assessment gave us the ammunition we needed to show our management board the actual risks we had in our environment." — Information Security Manager in the manufacturing industry. Read the full case study.
Get the Data Risk Assessment. You’ll see how much you stand to benefit from having Varonis in your security stack. We thought we were covering everything, but the assessment showed us areas where we were still at risk and helped us take the steps needed to mitigate that risk.
Information Security Analyst in the U.S. state government. Read the full case study.
"We were trying to get a handle on all of the data in our servers. We thought we knew where it was, but a Data Risk Assessment revealed a lot of data that we didn’t know about. We didn’t realize we had so many folders with open permissions." — Information Security Analyst in the U.S. state government. Read the full case study.
"Varonis flagged all this data that was almost a decade old and alerted us to at-risk areas. The risk assessment made us aware of just how much PII and other data we were holding." — Security System Administrator in the education industry. Read the full case study.
Beyond the assessment
Your Data Risk Assessment is completely free and lets you experience several SaaS Data Security Platform features unique to Varonis.
Varonis' Managed Data Detection and Response (MDDR) offering is the world’s first managed service for monitoring and protecting critical data 24x7x365. Varonis MDDR combines our industry-leading threat detection technology with our world-class team of elite threat hunters, forensics analysts, and incident responders who triage, investigate, and respond to alerts, so you don’t have to.
Varonis also provides ongoing risk assessments for ransomware readiness, pre-audit support, and attack surface testing for our customers, in addition to quarterly business reviews.
As a Varonis customer, you’ll have a dedicated customer success team that will meet with you to review your goals, quantify the value, and discuss your roadmap to constantly strengthen your data security posture. We’ll also monitor proactively to stop threats and perform routine system health checks.
Additionally, Varonis offers online training for unlimited users and Varonis certification courses, CPE credits, and we will welcome you to a community of 40,000+ Varonis users.
Varonis is a top choice for organizations prioritizing deep data visibility, classification capabilities, and automated remediation for data access.
Forrester Wave™: Data Security Platforms, Q1 2023
By completing your Data Risk Assessment with Varonis, you gain so much more than a document of where risks might live. We’re the only data security vendor willing to share our assessment sample because we’re confident that any other assessments available in today’s market won’t stack up against ours.
So, reduce your risk without taking any and get started with our free risk assessment today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.
-1.png)